The Middle East has become the global hub for major science and technology events. With the rising level of research and development, the region is hosting major gatherings of tech communities from across the world. Amidst such a global environment, the region is becoming a fresh target of email-based attacks. Recently, Khaleej Times reported that over 3.4 million email phishing attacks had taken place in the second quarter of 2022 alone in the region. That’s why email security in the Middle East is a major concern for organizations these days.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
You can never know whether your personal information has been illegally accessed by a hacker. These hackers use sophisticated hacking methods to get unauthorized access to your email account and phone numbers. Upon getting access, they promptly install malware on your computer or even collect keystroke data while you are chatting over social media. These methods, where threat actors target people to lure them into revealing confidential information, are collectively known as “social engineering attacks.”
As far as one can tell, social engineering attacks are becoming more rampant and dangerous. Email phishing is one of the most prominent types of social engineering attacks that causes the biggest havoc to email security. In a world of cybercrime, it is necessary to be prepared and aware for repelling and preventing these damaging cyber-attacks. Every organization must take precautionary actions by implementing proper security measures and protocols to safeguard their data and email domain as well.
Book a Free Demo Call with Our People Security Expert
Enter your details
What is Email Security?
Email security can be defined as the framework and proactive measures to ensure the safety and security of emails and their contents, exchanged between employees or other organizations. All these things are achieved by implementing strategies like strong encryption, domain authentication, multi-factor authentication, sophisticated passwords, etc., that protect emails from external attacks.
Email security helps you protect your company’s data and assets from cyber threats. The measures involved in implementing solutions and proactive measures are meant to empower employees to avoid various kinds of email attacks, such as phishing. Once you carry out phishing simulation campaigns, you will know the scope of improvement in your email security.
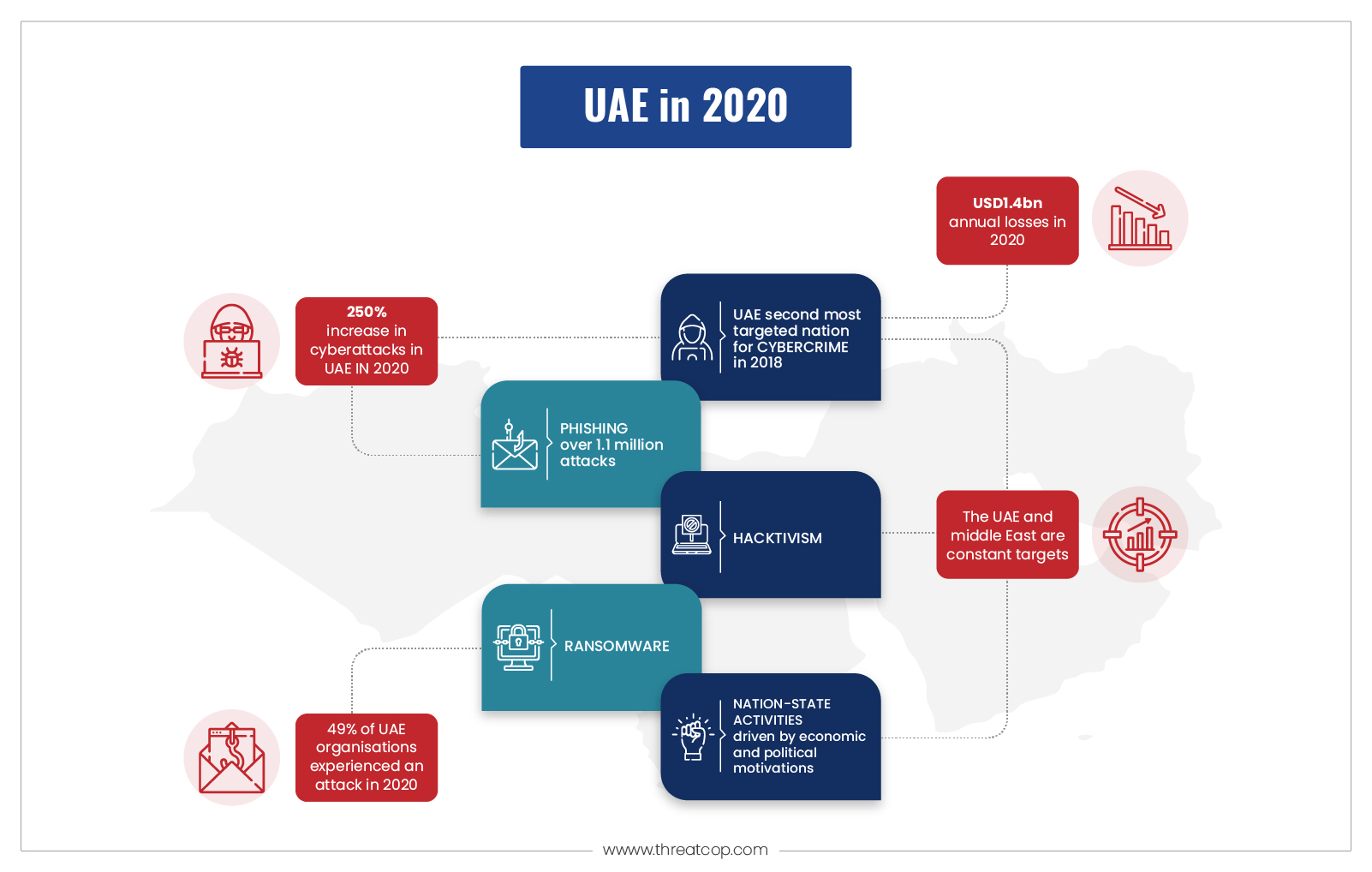
Types of Email Attacks
Phishing
Emails may seem harmless in disguise, but if you can’t distinguish between the two, there’s a chance that it could lead to a phishing attack. Phishing emails are designed to trick targets into revealing confidential or sensitive information to gain access to your online accounts or online assets for exploitation and financial gain.
A recent report by The National News highlighted the dangers of email phishing scams. Roughly 94% of businesses in the UAE experienced these attacks in 2020, compared to the global average of 73%. In another report by a magazine, Q2 2022, there was an immense increase of 230% compared to the previous quarter in the UAE.
Email Spoofing
Email spoofing is a sophisticated and technical way for cybercriminals to steal information from organizations. Many people are still unaware that email domains need to be verified through authentication protocols. In the absence of such protocols, it becomes extremely difficult for anyone to identify whether it is fake or not. 22% of all data breaches in 2019 were due to email spoofing. In addition, 77% of email spoofing victims in the UAE had their money and valuable data stolen, as compared to the global average of 73%.
BEC Attack
A BEC attack is a type of highly sophisticated spear phishing attack that targets executives, business leaders, and others who are expected to have access to sensitive information. Attackers target executives who have access to sensitive information and can pose a real threat. A BEC attack can be a particularly effective form of spamming. According to the IC3 annual report, there was 19,954 Business Email Compromise (BEC) complaints in 2021 that incurred a loss of over $2.4 billion to organizations.
For more details on email attacks, read: Types of Email Attacks
Some Infamous Email-based Attacks in the Middle East
The methods mentioned above are some of the most common and widely used for carrying out email-based attacks. Let’s talk about these notable attacks that happened in the Middle East in recent years.
A Dubai exhibition falls victim to a phishing attack, losing $53,000.
The phishing attack on Dubai Cheers Exhibition made headlines as the company had been prominent in conducting exhibitions for 11 years. The threat actors sent phishing emails to the customers from where they might get their hands illegally on the credentials. They used the data and hacked into the server of the exhibition, and they managed to make fraudulent transactions of $53,000 overseas.
Data Breach at Emirates Airline: Leaking Customers’ Sensitive Data
One of the largest airline companies in the Middle East is Emirates. Every week, they operate over 2,500 flights to 122 cities across 74 nations. It turned out that the company was giving a lot of information to outside businesses like Facebook, Google, Crazy Egg, and others. Sharing information like customer name, email, phone number, passport number, etc., after a reservation, the airline sends customers an email with the subject “Manage Preferences,” and the URL inside is not protected protocol. All data can be accessed through it.
This information was shared by a data security engineer, Konark Modi, who was booking a flight for his family. However, Emirates Airlines denied all the allegations, but other experts backed up Modi.
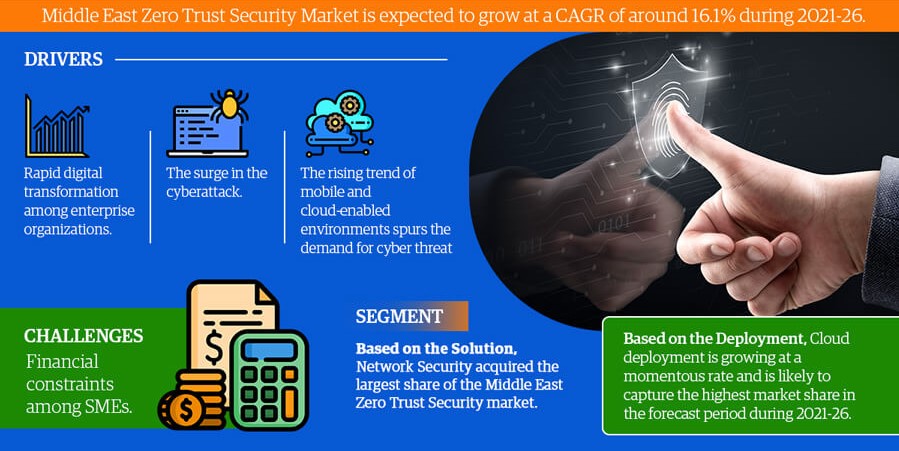
These types of email attacks are quite prominent in the Middle East, let’s understand what benefits one could get with the implementation of email security measures.
Benefits of Email Security
Access to Control Devices
Managed email security can enable full access to emails on secure devices while preventing full access to unmanaged email attachments. It ensures that an email account’s content access is restricted, protecting the information shared in email message exchanges. Additionally, one must implement multi-factor authentication to ensure security.
Recognize Suspicious Behavior
Email security helps secure outbound email policies for detecting threats. By controlling outbound emails, it might be possible to detect account compromises or other suspicious behaviors. Identifying and banning users who send or receive bulk emails can be made easier by implementing proper email security measures. Such activities might point to a compromised situation.
Improve Protection
In defending an organization, they need to imply powerful protection solutions against evolving social engineering attacks. Powerful email security measures allow customers to protect themselves from unwanted emails by helping them identify spam and threat emails.
Sustaining Communication Confidentiality
Email security measures like email encryption programs or software keep email messaging confidential. Enabling email encryption is essential, especially when important communications or confidential information is sent to your company. Therefore, investing in a good email security solution can save your organization from losing its data.
Security Against Zero-Day Attacks
Given that malicious links and rogue attachments are frequently used to launch attacks, email security is essential for protecting an organization from zero-day attacks. These attacks are typically started by malicious attachments or links. There must be multiple layers of defense against zero-day attacks against malware, viruses, APM, and targeted attacks like phishing, spear phishing, or whaling attacks. Secure email gateways provide malware and spam protection that prevents a zero-day attack.
Real-time Threat Safety
With email security, you can prevent advanced threats such as ransomware attacks by using an innovative blend of detection technologies, such as machine learning, sandboxing, and predictive analytics. Implementing real-time threat protection tools like TDMARC from Threatcop can help to prevent email spoofing, increase email deliverability, provide full visibility into outbound emails, and enable effortless monitoring of multiple email domains.
Best Practices for Email Security
To prevent email-based attacks, organizations can use an online end-to-end encryption service. Keep the information of employees secured in an encrypted environment. The modern workplace is a challenging one. With the ever-changing and evolving nature of technology, organizations must maintain a competitive advantage by implementing stringent security measures.
Implement Multi-factor Authentication
Multi-factor authentication (MFA) is the combination of more than one layer of security to verify your identity while accessing your account. It adds an extra layer of security to your email authentication.
Your password is encrypted with a unique fingerprint or OTP (one-time password), which reduces the risk of fraud or misuse. If you don’t have multi-factor authentication on your email account, it’s time to start using it! I suggest using 2FA (2-Factor Authentication) for the vast majority of services that offer it.
Create Strong Passwords
To keep your password safe, make sure it is extremely complex, strong, and impossible to guess. Having a strong password protects you not only from hackers but also from the temptation of using easy-to-guess passwords such as 1, 2, 3, etc.
When hackers gain access to your email account, they will try different combinations of letters and numbers until they find something that works. Having a password like this makes it easier for them to gain access to your account and compromise its security.
Monitoring Your Habits
Security training for employees might sound simple, but it is a good habit in the long run. Communication through email is very common in an organization, so your email activity should be tracked. A few practices you need to adapt to are:
- Prevent multiple login attempts.
- Remember to log out
- Avoid using public wifi
Phishing Simulation to Comprehend Vulnerability
Phishing emails are ones that attackers send to trick your employees. Commonly, an attacker uses email impersonation to fool your employees into downloading malware. Your organization needs specialized training programs to teach your employees how to recognize and respond to phishing emails. Having phishing simulation awareness training in the organization helps employees understand better how to respond to phishing emails.
Email Security Policies
Email Authentication Protocols
The three main email authentication protocols are DMARC, SPF, and DKIM. These protocols help secure the email domain against attacks such as spoofing and spam. DMARC is one such authentication mechanism that can reduce the chances of your email addresses being spoofed by unknown threats.
These email authentication protocols are implemented using a comprehensive suite such as TDMARC, which provides an interactive medium to implement protocols.
Email Encryption
Email encryption is a way for you to keep your online communications safe and private. Encryption uses a digital key to prevent unauthorized people from reading your messages, so you can send secret information without worry. Encrypted emails are fully encrypted end-to-end—so the recipient can’t read your messages. It’s also an extra layer of protection against hackers and government surveillance.
Employ a Trusted Email Service Provider
Email security should be one of your top priorities. Trusted email services will provide you with the services and tools that you need to guard your business against phishing, malware, and other cyber threats. As an email service, Gmail is known for its security. It provides you with emails forwarded to your organization’s accounts from Gmail that have been protected against phishing, as well as anti-spam and anti-virus protection. In addition, it also offers the option to manage multiple devices through a single account.
Spam Filters
Most email service providers have in-built features to filter out certain emails, such as categorizing all the promotional emails into one section. For example, some email service providers, such as Gmail, Outlook, and Yahoo!, use pattern-matching techniques to prevent spam from reaching their users. Some use whitelisting tactics and sometimes provide additional antivirus software to facilitate additional security.
Phishing Incident Response
Some email service providers treat all external communication with special emphasis and mark or tag them as spam, making it difficult for employees to check for these emails. Employees should be trained about phishing emails or links to phishing websites so that they can identify what a phishing email looks like and how to differentiate between real offers and fake offers. However, this leads to an action that must be taken by employees to report phishing emails through a phishing incident response tool.
Cybersecurity Awareness
Cybersecurity awareness training is an effective way of educating employees about cyber threats. It enlightens them on how they can protect themselves from cyber attacks so that they can be proactive in their response. The concept is to make employees aware of various security measures and threats that must be followed. Employees are often at risk of infection because of the extensions that are used for accessing devices and the applications they use.
The employees might fall victim to phishing attacks wherein threat actors lure them to download malicious files or fake executables that can be installed on their devices. Credentials are also involved in such threats, as they might allow crucial data theft or manipulation. Hence, it is necessary to ensure that security solutions are implemented at every level.

Email Security: An Imperative for Securing Cyberspace
You must have understood that email security is among the most important elements of secure cyberspace. Organizations must give the utmost attention to their email domain and email server security as it is often the first point of attack. Email security is the prime subject of an organization’s cybersecurity. Any company that wants to protect itself from cybercriminals should take steps to secure its domain name as well as its server infrastructure by upgrading its software and hardware. This can only be achieved by reaching out to a cybersecurity providers like Threatcop. It provides your organization with different security tools that help you secure your sensitive data.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
