Nowadays, BEC attacks have become one of the most remunerative lines of business for malicious actors. Every day new BEC attack groups are being discovered. These attackers are targeting various firms across the globe to scam them out of massive sums of money. Currently, cybercriminals are making loads of money by actively using BEC attacks as their prime attack vector. Among all the cyber crimes reported, they are the costliest ones for organizations.
Table of Contents
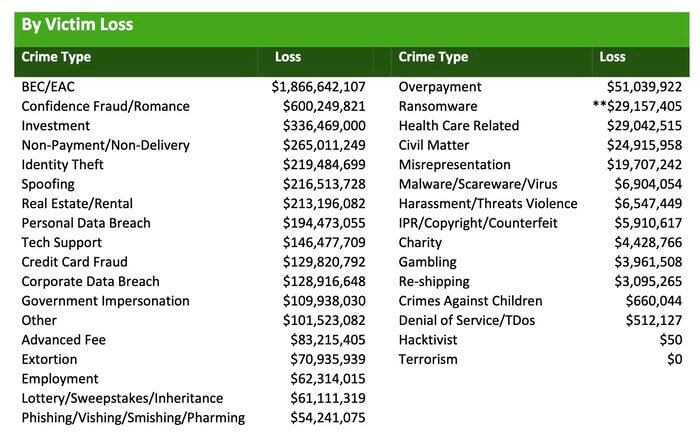
ToggleAccording to the FBI’s IC3, BEC attacks have incurred losses of $1.8 billion in 2020.
What is BEC Attack?
BEC attacks typically involve email spoofing, spear phishing, or impersonation of business email addresses. In business email compromises, cybercriminals use those forged email addresses to trick employees into making payments or financial transactions to the threat actors’ accounts. The BEC attackers are known for being master manipulators and fraudsters who employ social engineering tactics to gather intelligence about targets. Then, they use this intelligence to launch successful attacks.

The primary objective of business email compromise is to extort money from the organizations. Malicious actors gather intelligence about the target organization and utilize reconnaissance strategies to comprehend how it carries out everyday business operations.
Fraudsters study the market and keep a close eye on technological developments, constantly looking for ways to improve their attack tactics. The transition to work from home culture has created a favorable ecosystem for threat actors, allowing them to land attacks more easily. For example, during the pandemic, cybercriminals often curated covid-themed phishing templates to trick unsuspecting employees.
Book a Free Demo Call with Our People Security Expert
Enter your details
Different Types of BEC Attacks
BEC attacks involve a myriad of tactics, based on which they can be classified into multiple categories. The most common types of BEC attacks include:
False Invoice Scam
Cyber attackers often impersonate an organization’s suppliers or collaborators to send false/fake invoices. This tricks the target organization into making certain transactions or payments for scammed invoices.
CEO Fraud
It is the most common way of landing business email compromise attacks. In these attacks, cybercriminals impersonate the CEO or other higher-level executives of an organization to trick employees of the accounting or finance department into transferring them a certain amount of money.
Account Compromise
In these attacks, the official email accounts of one or more employees are hacked through stolen credentials or other ways. Attackers then use these accounts to send emails to stakeholders or vendors to request payments.
Attorney Impersonation
Many organizations hire legal representatives and lawyers to carry out their legal activities. Sometimes, attackers impersonate attorneys and target low-level employees for accessing vendors’ information or the organization’s intelligence.
Data Theft
In this type of BEC attack, the human resources department is directly targeted. The attackers attempt to gather employee information by impersonating the target organization’s executives and asking the HR department for certain details related to the employees. The data collected by cybercriminals can be used as leverage while carrying out CEO fraud.
Real-life Examples of BEC Attacks
Currently, BEC attacks are one of the most dangerous threats for organizations and the most lucrative attack vector for threat actors. There are numerous real-life examples of BEC attacks, where organizations suffered a massive loss of resources and severe damage to reputation. Two of the most infamous examples are mentioned below.
Puerto Rico Government Lost $3.8 Million
The government of Puerto Rico suffered a loss of $3.8 million in 2019 and 2020 due to a well-executed BEC attack. In this attack, a government-owned corporation, which was involved in the economic development of an island, was tricked into making changes in the banking account to which they were supposed to make payments.
Anthony Dwayne King Ripped off $250,000
Anthony Dwayne King was sentenced to two and half years for conducting a BEC scam, which caused losses of $250,000 for companies across four states. He, along with some accomplices, carried out BEC attacks through vishing (phishing through phone) by establishing fake companies and fraudulent bank accounts. They targeted home movers and law firms but were caught by the Cyber Fraud Task Force of Georgia.

What is C-Suite? How is it under Threat?
C-Suite refers to the executive-level members of an organization. C-suite is commonly known as C-level. The notion of C in C-suite is for the first letter of Chief. They are usually a cluster of important senior executives with an array of designations like ‘Chief Executive Officer (CEO)’, ‘Chief Operating Officer (COO)’, ‘Chief Financial Officer (CFO)’, ‘Chief Technical Officer (CTO)’, ‘Chief Information Officer (CIO)’, etc.
Often, cybercriminals gather information about an organization’s C-level executives and spoof their email accounts to carry out BEC attacks. When employees, especially from the finance and HR departments, receive spoofed emails from an executive’s accounts, they usually respond as the emails instruct them to, leading to business email compromise attacks. Among all the BEC attacks, the ones that target C-suite are the most damaging. Since the important individuals of the organization are involved, the damage is both reputational and financial.
How Are These Attacks Carried Out?
The basis of BEC attacks is that they are people-centric. It is quite dependent on compromising the email accounts of targets. The procedure of carrying out this attack involves tricking people. A traditional method employed by fraudsters is either phishing or credential stuffing. It starts with the collection of details of the employees. The collected details are used to trick employees into making fraudulent transactions. The following tactics are majorly used in these attacks:
Domain Spoofing
This is a method of forging an email domain to fool/trick the targets. The purpose of this method is to gain the trust of the targets by tricking them into thinking that the emails they receive are genuine. SMTP (Simple Mail Transfer Protocol) doesn’t have email address verification by default. That’s why cyber attackers can fake the sender’s address and display the name of the email account to create an impression of authenticity.
Lookalike Domains
Also known as cousin domains, lookalike domains have domain names pretty similar to those of the target organizations. These domains are slightly altered or modified which makes it easy to deceive target individuals. For example, netflix.com can be used as netffix.com. The success of this methodology is dependent on the lack of awareness in employees or target individuals.
Compromised Accounts
Sometimes, cybercriminals can get hold of the actual email account of someone who has a higher position in the organization. This allows them to carry BEC attacks easily as it facilitates a level of authenticity.
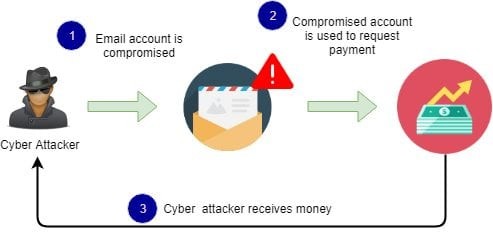
Group Mailboxes: Favourite Target for BEC Attacks
Group mailboxes or shared mailboxes are a point of email contact for a whole group or team. It is used by a large number of individuals, which makes it an excellent target for cybercriminals to send spoofed or phishing emails. Due to a large number of people in a group or shared mailboxes, the probability of at least one employee opening a link containing malicious attachments or links becomes very high. During remote working, the rate of success of attacks using malicious emails has increased tenfold.
Statistics on BEC Attack
- According to data from the FBI’s IC3 (Internet Crime Complaint Centre), BEC scams have increased by 61% in 2020 in comparison to 2016.
- An article by Helpnet Security mentions that 34% of the employees from the finance sector become victims of spear-phishing attacks.
- According to this article, 50% of the BEC attacks are carried out through spoofing by misusing the identity of individuals by displaying their names. Among all the spear-phishing emails, the company’s name was used 69% times, the individual target’s name was used 66% times, and senior management’s name was used 53% times.
- As per an article by TechRepublic, 71% of BEC attacks are carried out by spoofed email accounts and 69% by spear-phishing attacks. Apart from them, 24% of the attacks are carried out by malware.
- Surprisingly, IC3’s data also reports that BEC attacks are 64 times more expensive than ransomware attacks.
How to Detect Business Email Compromise Attacks?
Business email compromise attacks can have devastating consequences for organizations. It has become essential to detect these attacks before they can cause any damage. Here are the two major ways for detecting BEC attacks and stopping them in their tracks.
Anti-phishing Tools: An effective anti-phishing tool can act as the first line of defense against BEC attacks. It carries out authentication of the sender’s addresses and possesses additional capabilities to identify any discrepancies. Additionally, a tag can be used to mark external emails, which could alert the employees to be careful with non-organizational emails.
Employee Vigilance: A cautious employee can identify spelling mistakes or grammatical errors in emails, which are highly probable in such attacks. In organizations, there are some sets of procedures for dealing with financial transactions or crucial data. Thus, one must be careful to identify the requests for bypassing such procedures. The employees must be educated about the intricacies of business email compromise attacks so that they can identify addresses for their authenticity. In case of sensitive or finance-related requests made through emails, employees should be instructed to confirm them by contacting the sender through any other medium such as phone calls.
How to Protect Your Organization from BEC Attacks?
As cybercriminals are getting increasingly active and creative every day, it has become essential for organizations to take certain security measures against BEC attacks. So, here are some of the most effective ways to reduce the risk of BEC attacks and keep your organization safe:
- Multi-factor Authentication: Instruct the employees to enable multi-factor authentication (at least 2FA) on their email accounts. This will make it difficult for cybercriminals to compromise their accounts for launching a BEC attack.
- DMARC-based Protection: Use standard email authentication protocols like DMARC, DKIM, and SPF to protect your organization against domain forgery. TDMARC monitors all three of these email authentication protocols to complement the Simple Mail Transfer Protocol (SMTP).
- Be Proactive: Instruct your employees to avoid opening any emails from suspicious or unknown parties. Ask them to never click on any unsolicited attachments or links under any circumstances.
- Enable Fraud Reporting: Companies can employ phishing incident response tools like TPIR to enable employees to report malicious emails as soon as they are identified.
- Authoritative Control: Use the company domain name to create company email accounts instead of using free, web-based accounts.
- Anti-Phishing Awareness: Employees as well as organizations must be aware of spear phishing attacks and know how to avoid them. The employees must be provided phishing awareness training to prevent such attacks.
- Employee Awareness Training: The organization must carry out systematic cybersecurity awareness training for their employees so that they can become aware of various attack vectors and safeguard themselves against them. Instruct employees to verify any email requests for confidential information or wire transfers.
How can TDMARC Help?
KDMARC is an anti-spoofing and DMARC deployment tool that helps you properly implement and configure your email domain’s SPF, DKIM and DMARC records to prevent email spoofing. Loaded with an array of useful features, this email authentication tool prevents malicious actors from misusing your email domain to send malicious emails. Doing this significantly reduces the chances of BEC attacks like CEO fraud and data theft.
“TDMARC is listed on top technology review platforms like SourceForge, Gartner, and many more for its quality service”
Summing Up
Business email compromise attacks are more prevalent and financially destructive than any other attacks. This attack is based on targeting the C-suite or senior executives of the organizations. BEC attacks have led to the loss of millions of dollars and damaged the reputation of hundreds of organizations worldwide.
Organizations need to become smarter to prevent such attacks. The objective of every organization should be to empower their employees and senior executives to safeguard themselves against these kinds of threats. Companies should also focus on strengthening their email security framework to prevent email-based attacks.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
