Make the change this Cybersecurity October Awareness Month with the Cybersecurity Olympics. – Know More
Video conferencing applications like Zoom became a popular medium for daily meetings to discuss plans of action and everyday work developments. Nowadays, zoom phishing attacks became a new source for scammers to steal data.
The popularity of Zoom has also turned into one of the cyber criminals’ most lucrative tools for exploiting innocent individuals. Scammers have been using emails to trap their victims using the name of this app to launch phishing attacks on unsuspecting users.
Zoom Phishing Attacks Use its Name
The victims receive emails saying that Zoom has undergone a server upgrade, prompting them to verify their account if they want to continue making or receiving calls through this app.
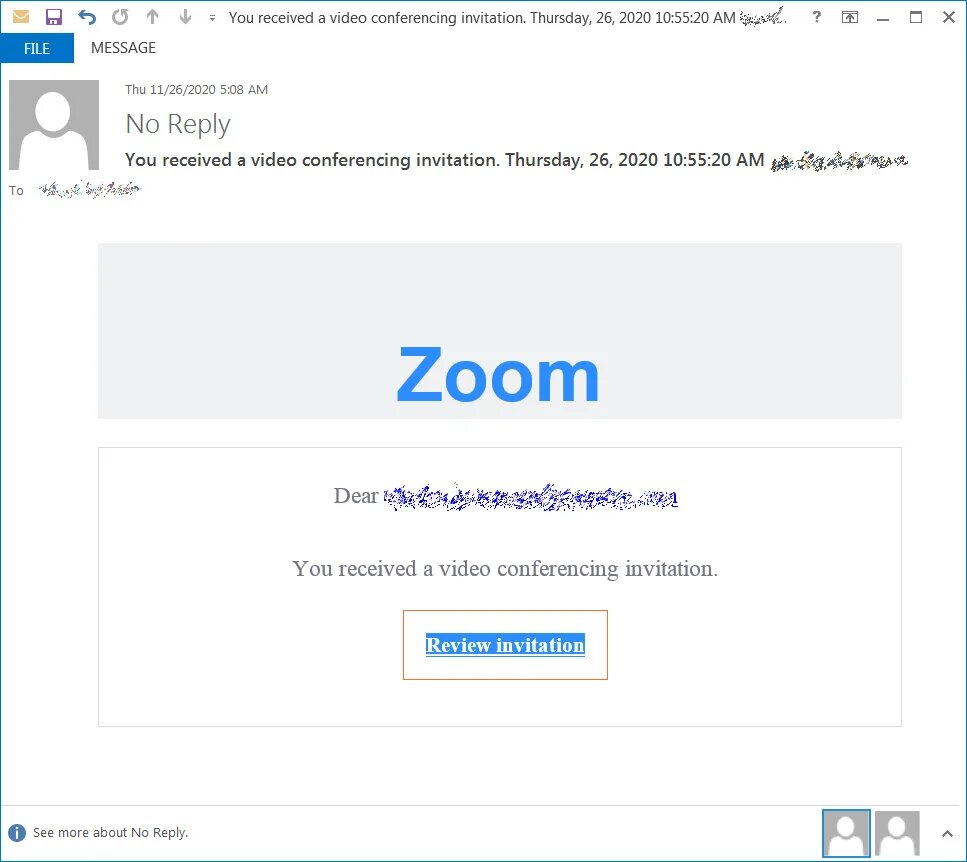
The display name in the email headers shows “Zoom – no-reply@zoom[.]us”. This makes it appear as if it is genuinely from Zoom.
Along with this, most of the email domains used came from legitimate but compromised accounts. Additionally, some phishing emails also used new email domain names such as zoomcommunications[.]com or zoomvideoconference[.]com. It is very difficult for Secure Email Gateways (SEGs) to catch them due to the legitimacy attached to the domain names used by these threat actors.
Book a Free Demo Call with Our People Security Expert
Enter your details
Credential Harvesting is Their Aim in Zoom Phishing Attacks
These zoom phishing attacks aim to steal credentials from services like Outlook and Office 365 by directing the user to spoofed login pages. Moreover, the attackers are even using techniques like obfuscation to make it very difficult for security systems to detect phishing pages.
Hackers use a fake attachment that leads to a login page that is locally hosted on the recipient’s computer and not on the internet. Further, the HTML, JavaScript, and PHP code is encoded. This is unreadable to humans and automated security tools. This is done to bypass URL reputation checkers and remain undetected.
Similarly, hackers use a malicious link to redirect the victims to a fake login page that is hosted on a compromised server. The spoofed websites or email spoofing look very identical to the legitimate pages of Outlook and Microsoft Office 365. Therefore, it’s very easy for the victim to fall prey to it.
In a Tom’s Guide article, they have researched and mentioned the problems Zoom has been experiencing in past. An expert review of its security and privacy practices revealed some concerning findings. Like Zoom’s end-to-end encryption was not quite that. Other Zoom meeting participants could learn a lot about you. Pranksters and bored teenagers could, and occasionally still do, “Zoom bomb” public meetings with shocking or rude content.
Since the early summer of 2020, most of those imperfections have now been fixed or mitigated, but newer issues have arisen on occasion.
Recent Zoom Phishing Attack
Researchers revealed a zoom phishing attack on a major North American online brokerage company on 25 August 2022, in which a victim begins a legitimate Zoom session only to have their Microsoft credentials hijacked after landing on a fake Microsoft Outlook log-in screen.
A study found that email attacks clone workflows that are used by most people every day. In most organizations, Zoom has been used all the time. It’s like a daily routine for employees to click on start meeting. Especially since Zoom’s emails all have similar content and most users are used to them.
Phishing attacks rose 220 percent during the height of the Covid-19 pandemic compared to the yearly average
– Gulf Business
How Can You Identify a Zoom Phishing Attacks
Phishing attacks have evolved and have become even more complex to differentiate from legitimate emails. The cost of recovery from a successful phishing attack that results in credential harvesting can be huge. Some measures to detect zoom phishing attacks are mentioned below:
Check the email domain name
You should check the name and email address of the sender very carefully. The domain name of a legitimate sender would look like abc@company[.]com. However, a phishing email would contain a sender id which would say abc@commpany[.]com or abc@companny[.]com.
Be wary of requests for sensitive information
The purpose of zoom phishing attacks is to harvest sensitive information from the victims. A legitimate email would never ask you to send such information through email. Therefore, this is a major red flag when it comes to detecting phishing emails.
Check the content of the email
Typically, a phishing email would contain numerous spelling mistakes and grammatical errors. Legitimate emails from companies will never contain such mistakes as they have dedicated teams of employees who write emails on their behalf. It’s better to check for the genuineness of the sender if the email body contains any spelling mistakes or grammatical errors.
Check for suspicious links
Zoom phishing emails come with a gateway. It can be in the form of redirection to a fake website or an attachment that needs to be downloaded. Genuine companies never ask you to download any such attachments or click any such links.
Check for free offers or coupons
Phishing emails usually contain offers that sound very attractive. The objective is to make the victim click on the link for availing of the offer. This starts the process of redirecting the victims to a bogus website or getting them to download a malicious attachment.
To mark Cybersecurity Awareness Month, Threatcop collaborated with 31 respected CISOs and CTOs from prominent organizations. Together, we’re working towards a safer digital future.
Explore Here: 31 Cybersecurity Awareness Ideas from Security Leaders
Measures to Prevent Zoom Phishing Attacks
Threat actors have found ways to evade the barriers of spam filters and land their phishing emails in the inboxes of recipients. Some ways to prevent zoom phishing attacks are mentioned below:
- Use awareness training tools like TSAT for creating employee security awareness training. Moreover, this tool can provide the organization with handy information about the status of their employees in terms of cyber vulnerability. Along with this, it also provides employees with useful awareness training at the end of the campaign.
- Use Multi-Factor Authentication (MFA) to add an extra layer of protection. This can enhance the security of sensitive information. Moreover, MFA is a very user-friendly defense mechanism for the end-user. Along with this, MFA comes with Single-Sign-On (SSO) solution. It helps in the prevention of losing data due to password misplacement.
- Use Phishing Incident Response Tools like TPIR to secure the organization from emails from suspicious domains in the future. You can report the email, and it will send it to the trash. It removes reported malicious emails directly from the user’s inbox.
- Encrypt all the sensitive information possessed by the organization about clients and their systems.
- Implement DMARC like TDMARC to secure your domain against forgery and misuse. Limiting phishing attacks that use your organization’s domain can save the organization’s reputation and client relationships.
- Conduct VAPT to test the organization for vulnerabilities and upgrade the systems accordingly to satisfy the standard of cyber security required.
“If you’re proactive, you focus on preparing. If you’re reactive, you end up focusing on repairing.”
– John C Maxwell
Malicious actors are now equipped with newer technology and methods to carry out zoom phishing attacks. However, if people are careful and smart enough to spot such emails, the damage from these attacks can be prevented.
Security Compliance Executive
Department: Compliance, Threatcop
Sanjana is a Security Compliance Executive working on best-of-the-industry-level compliances relevant from a cybersecurity perspective, their implementation, learning and outcomes in various business domains.
Security Compliance Executive Department: Compliance, Threatcop Sanjana is a Security Compliance Executive working on best-of-the-industry-level compliances relevant from a cybersecurity perspective, their implementation, learning and outcomes in various business domains.
