“Fishing or phishing” & “Farming or pharming” – confused about them. Let’s clear it up.
According to FINSMES, there were 241,342 victims of pharming and phishing in 2020 in the United States. It comprised 32.96% of all cyber attacks. Google’s Gmail has also stated that they block 100 million phishing emails every day.
Table of Contents
TogglePhishing and pharming are the types of social engineering attacks. With passing time and increasing modernity, social engineering attacks are getting more sophisticated which is making them difficult to detect. The attacks which are activated by humans are the toughest threat because human exploitation has possible and depends on negligence and unawareness.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Today, cyber thieves are honing their cybertheft skills to beat the latest technology and innovative security systems to create havoc in the cyber world. Both phishing and pharming, the two major types of cyber attacks are being infamously used to trick users into providing their personal information. Cybercriminals use both of these tactics to obtain the sensitive information of users, however, both of these tactics work with different methods. Let’s move further to find out how.
Many fraudsters carry out these two types of cyber attacks by impersonating anyone, be it health or technical representatives, or government officials. According to ChannelLife, a 75% increase in phishing attacks was reported in 2020. According to IBM, 1 in every 5 companies have observed a malicious data breach in the same year.
Book a Free Demo Call with Our People Security Expert
Enter your details
What is Phishing?
Phishing is the type of social engineering attack which uses email as a medium of carrying out fraudulent communication. The purpose of phishing attacks is to target users with the aim to con them into revealing their personal and confidential information. In this technique, hackers send spoofed emails in the name of a legitimate source to victims and trick them into clicking on a malicious link or attachment to acquire their personal information.
In many instances, these phishing scams use software or security vulnerabilities to install malicious software on the targeted user’s device. In any case, the human factor remains the key element in the successful phishing attempts of these cyber crooks.

Phishing Examples
The scary part is, that cybercriminals don’t limit themselves to using emails for launching phishing attacks. They can also phish over a website and sometimes go with SMS (smishing) or voice calls/messages (vishing) to trick users. According to a report published by Security Boulevard, 97% of the users are unable to recognize a sophisticated phishing email.
In another report by The National News, 94% of businesses in the UAE experienced phishing attacks in the year 2020. The same report also highlighted that 77% of email spoofing attack victims in the UAE had their money and valuable data stolen, as compared to the global average of 73%.
What is Pharming?
Pharming is one of the social engineering attacks that involve acquiring credentials of the target user by luring them into a landing page which is usually a lookalike. The target can be an internet user who is given a link to a spoofed website to get access to their log-in credentials or capture personally identifiable information (PII). This personally identifiable information can be bank account numbers, passwords, etc. They are more likely to manipulate them and install the malware on the target’s digital device.
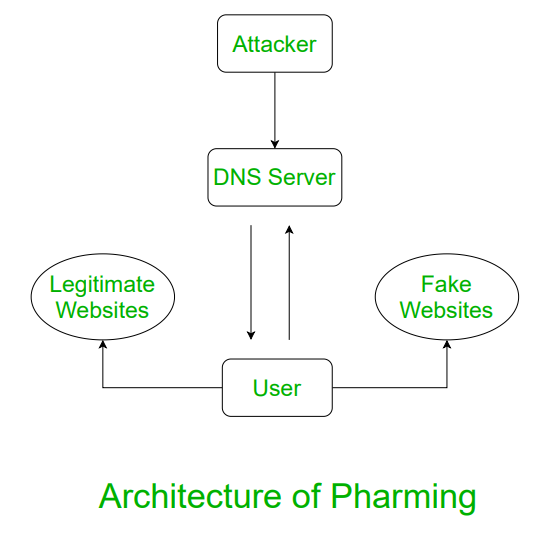
In other ways, a user can still get hacked through an authentic link if the DNS (Domain Name System) is hacked or hijacked. Pharming can result in a serious attack on the targeted user and the biggest reason is that the user won’t be able to comprehend that a particular website is hacked.
Pharming Examples
An employee routinely logging into a payroll account may be redirected to a forged website instead. And, if the fraudulent website looks legitimate enough, the victim may end up getting tricked.
According to a blog by Computerworld, there was a pharming attack on 50 financial institutions in Europe, the USA, and the Asia-Pacific region.
Difference between Phishing and Pharming
- During phishing, the attackers seek crucial information by legal electronic communication whereas, in pharming, a more technical and advanced method is used to acquire credentials.
- During the process of phishing, one person is scammed at a time through a test or email whereas, in pharming, a link is forged which redirects the user from one website to another which is fake and looks like.
- Phishing is social engineering attack whereas, pharming is a special kind of email phishing.
- In phishing, the victims are tricked by providing personal mail or message while in pharming, private or personal information is acquired by domain spoofing.
- The process of pharming is more tricky than phishing because it involves manipulating DNS while phishing is the more common attack and it misdirects the user to submit credentials or sensitive information.
- Phishing can be easily carried out and also identified. On the other hand, pharming is tough to identify as well as carry out.
Similarities between Phishing and Pharming
Phishing and Pharming, both are types of social engineering attacks. The notion of these attacks is that they are carried out by the manipulation or persuasion skills of attackers. These skills can be attributed to technicality or not, but the manner of delivery is to convince the target about the authenticity of the frauds.
How to prevent Phishing and Pharming?
The best way to prevent a phishing attack is by getting aware of different kinds of cyber attacks and being cautious about emails. Both phishing and pharming are serious cyber threats to any organization today. Regardless of their differences, these cyber scams lead to the same consequence i.e. loss of confidential data. In order to secure your organization from these cyber attacks, follow these effective guidelines as cybersecurity measures:
Lookout for HTTPS in URLs
DNS spoofing doesn’t generally work on HTTPS websites. Even if the hacker manages to spoof a legitimate website with an HTTPS extension and redirect a server under its control, it will not be of any use.
Check for Suspicious-looking Emails
Phishing emails more than often consist of grammatical errors and suspicious-looking content. Also, the source of the email address in most cases is unknown, so it is always better to cross-check any unfamiliar or unexpected email.
Cybersecurity Awareness Training
We can’t ignore the fact that employees are the most vulnerable link in the chain of cybersecurity. In order to strengthen this link, it is important to provide employees with proper security awareness training to guide them to identify the potential cyber risks.
Brand Monitoring
Always keep track of how your brand is being represented online. Anti-phishing and fraud monitoring tools help in identifying if there is any online copyright infringement activity going on against your organization’s website or application.
Avoid Clicking on Links
Emails are the successful carriers of malicious attachments like links, document files, images, etc. Try to avoid clicking suspicious or unexpected email attachments or links as they redirect users to fraudulent web pages and request personal information. Make sure to verify such emails on an incident response tool so as to avoid becoming a target of a cyber attack.
Email Authentication Protocols
Why pay for recovering damages of cyberattacks when you can easily avoid them? Secure your email domain from unauthorized access with email authentication protocols such as DMARC, dynamic SPF, and dynamic DKIM.
Recap
Pharming and phishing, both are serious threats to the cyber domain. Irrespective of their differences and distinctions, they are intended to steal confidential information. In common terms, the procedure of pharming requires the installation of a malicious code on the target user’s device to redirect the user to a fraudulent or spoofed website. And phishing involves sending enticing emails to target users to acquire their sensitive information.
A cyber attack can be expensive and financially damaging for organizations. There are cybersecurity tools such as TSAT that provide security awareness training for employees and assist the enterprise to educate their employees and make them aware of the cyber security domain. To prevent and safeguard from phishing, there is a tool named TPIR (Threatcop Phishing Incident Response), which can be used to report and take necessary action regarding malicious and suspicious emails.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
