“Among all the email impersonation attacks in 2020, 50% were phishing, 36% were scamming, 12% were BEC, and 2% were extortion”
Table of Contents
Toggle(Source: Statista)
The word ‘impersonation’ refers to the act of pretending to be another person for a purpose or fraud. Impersonation attacks are a form of cyber-attack where attackers send emails that attempt to impersonate an individual or company to gain access to sensitive and confidential information. One of the most popular forms of impersonation attacks is CEO fraud, or business email compromise (BEC).
Over one-third of the organizations saw an increase in the number of attackers trying to gain access to sensitive and confidential information. This includes the theft of sensitive intellectual property or login credentials via email spoofing.
Globally, BEC attacks caused $1.8 billion of financial loss in 2020, resulting in businesses losing valuable data, customers, and money in the process. In 2021, 94% of organizations have experienced phishing attacks. Additionally as per the Business Wire, 45% of organizations witnessing a visible increase in spear-phishing attacks with malicious URLs.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is an Impersonation Attack?
Impersonation attacks are a form of social engineering attack where attackers use manipulation to access information. The impersonation attack involves cybercriminals imitating a trusted individual or an organization to steal sensitive data or money from the targeted organization.
Email spoofing is the primary mechanism for carrying out impersonation attacks. The primary objective of these attacks is to get private data or monetary benefits by faking emails or individuals. These attacks are highly dependent on social engineering tactics.
Emails are the prime medium for carrying out impersonation attacks. Most of the time, cybercriminals impersonate CEOs or C-suite executives. This includes the email ID as well the content of the email body. The email impersonation attack is done via one of the following.
- Free email account for spoofing
- Cousin domain spoofing
- Sender’s Forged Envelope
- Sender’s Forged Header
- Compromised Email Account
How Email Impersonation Attack is Carried Out?
Targeting the victim
The most important step in deploying a successful impersonation attack is doing background research on the target victim. In this era of technology, finding someone’s personal information is a pretty easy task. Social networking platforms such as Facebook, Instagram, Twitter, etc., are some of the media that can provide victims’ personal information.
Book a Free Demo Call with Our People Security Expert
Enter your details
Building Trust
Once the attacker gets his hands on the required information, the next step is to build a relationship of trust with the victim. The attacker will impersonate someone who knows the victim.
Deploying the attack
Once the attacker builds up a relationship of trust with the victim, attacks are deployed by majorly using three tactics. They are-
By Registering a look-alike Email Domain: The threat actor registers an email domain that is similar to the actual email domain and creates a new email ID using a name that is similar to the name of the person who is being impersonated.
Manipulating the Display Name: The majority of mobile email clients only display the name of the sender, thus making it very easy for the attacker to edit the display name and manipulate the victim. However, in desktop email clients, both the display name and email ID of the receiver are shown, and thus, this attack methodology is not very successful.
Using a Free Email Account: Attackers send messages through free email accounts such as Gmail, Yahoo, etc. The sender indicates that the victim has been locked out of their official account and needs immediate help to get the task done.
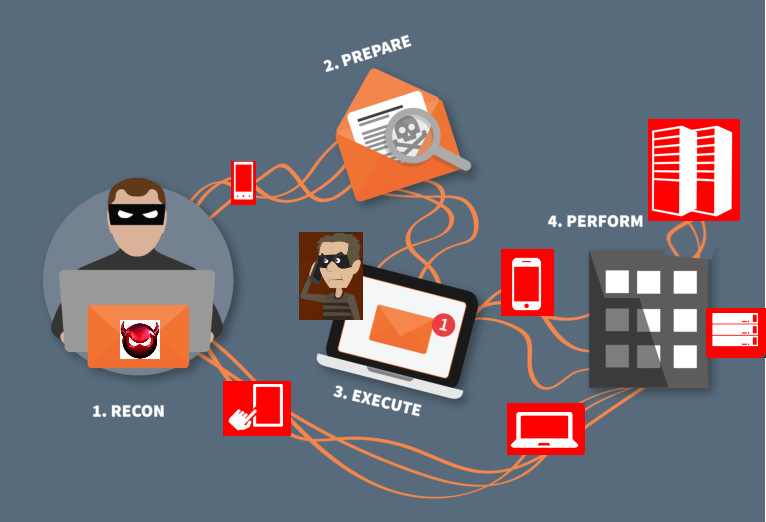
Types of Email Impersonation Attacks
CEO Fraud
In this type of attack, the cybercriminals impersonate the executives of the organization, namely the CEO. They target a CEO, carry out research on them, and then create a spoofed email that contains a command/request for their employees. Thus, employees carry out the designated tasks which would cause a loss of data or money for the organization.
Business Email Compromise
In this type of cyber attack, the cybercriminals target C-level employees or a business altogether. The threat actors defraud the target companies by luring them to make wire transfer payments. The email accounts of these targets are usually publicly available which makes it easy for cybercriminals.
Whaling
This type of attack is highly dependent on social engineering tactics to gather personal or organizational information. The attack vectors for whaling are email spoofing and content impersonation. The whaling attack involves the use of a malicious website, where threat actors record the credentials of the targeted individuals.
Why is Impersonation Attacks Hard to Detect?
The nature of impersonation attacks is that either the email domain is spoofed or the content of the email is spoofed. The only distinction between all kinds of email-based attacks is that it doesn’t contain malware.
Cybercriminals are social engineering experts, who have excellent manipulating skills to gain the trust of targeted employees of an organization. Along with that, cybercriminals often conduct extensive research on the targeted individuals to get to know everything and find ‘pressure points’. These pressure points are kind of triggers that lure users into revealing information.
Thus, they use all the information to create a fake email account with a message that seems authentic. They create the message in such a way that the targeted user is compelled to share sensitive information or make monetary transactions.

How to Prevent Impersonation Attacks?
Providing Cybersecurity Awareness and Training to Employees
Organizations should take the initiative to provide proactive cyber security awareness training to their employees. Cyber security awareness and training tools such as TSAT, enable employees to learn about cyber-attack methodologies and the different ways in which these attacks can be deployed on them.
Building a Cyber Resilience Strategy
It is important to build a cyber resilience strategy that can help in enhancing the cyber security of the organization including email domain security, web security, network security, endpoint security, as well as data backup and recovery.
Business Contingency Plan
Each business must formulate a business contingency plan in case your organization suffers from an unexpected event or situation. The purpose of a business contingency plan is to establish a strategic framework and response mechanism to recover from a cyber attack.
Cybersecurity Awareness and Resilience are the Resolutions
Awareness is a key element to strengthening the first line of defense that are humans. The purpose of employee awareness training is to educate employees to defend themselves against impersonation attacks. Cybercriminals can manipulate targeted employees if they are not well-informed about the attack vectors through which cyber attacks could take place. They must also learn the necessary actions that should be taken to increase the cyber resilience of an organization.
When you procure a domain for your company, you must also employ an email security tool. There are various aspects of email security tools. One can be the “Threat Alert Button”, which empowers employees to report suspicious emails. Another prominent and technical solution is to employ email authentication standards such as “DMARC”, which adds another layer of security in the form of SPF and DKIM protocols. You need to cyber aware your employees using TSAT and secure your email domain by using TDMARC.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
