The world had a toppling experience in the year 2021 with Covid-19 raising the concerns about the second wave. Apart from the pandemic, cyber attacks have continued to haunt the digital world. The year is ending with the identification of a severe vulnerability in Java library log4j, named as Log4Shell, but threats will continue to keep occurring.
Table of Contents
ToggleBelow listed are some of the most notorious cyber attacks that have taken place in the past. These attacks have created a necessity for the cyber security domain to become more resilient and stronger than ever. With an increasing number of attacks and kinds of threats, various defense mechanisms and tools have been incorporated to make the cyber world more secure and protected.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Major Cyber Attacks Witnessed Globally in 2021
JBS Meat Cyber Attack
JBS Meat is the largest company in the meat industry. The computer and network infrastructure of JBS Meat were cyber attacked. The company faced a ransomware attack and they had to pay an $11 million ransom through Bitcoins to attackers. The attack raised concern regarding the increasing sophistication of cyber attacks. The attack disrupted the operations of the whole meat industry in Australia.
Colonial Pipeline
On 7th May, the largest American oil pipeline company Colonial Pipeline became the victim of a cyber attack. They were targeted by a ransomware attack. This attack was the largest on any oil infrastructure, which forced the company to shut down for a long period of time. The pipeline was responsible for supplying oil which comprised 45% of fuel consumption on the East Coast. It was a smart move from the company to proactively take specific systems offline to contain the threat. The company also immediately engaged third-party cyber security experts to investigate the incident and mitigate the threat.
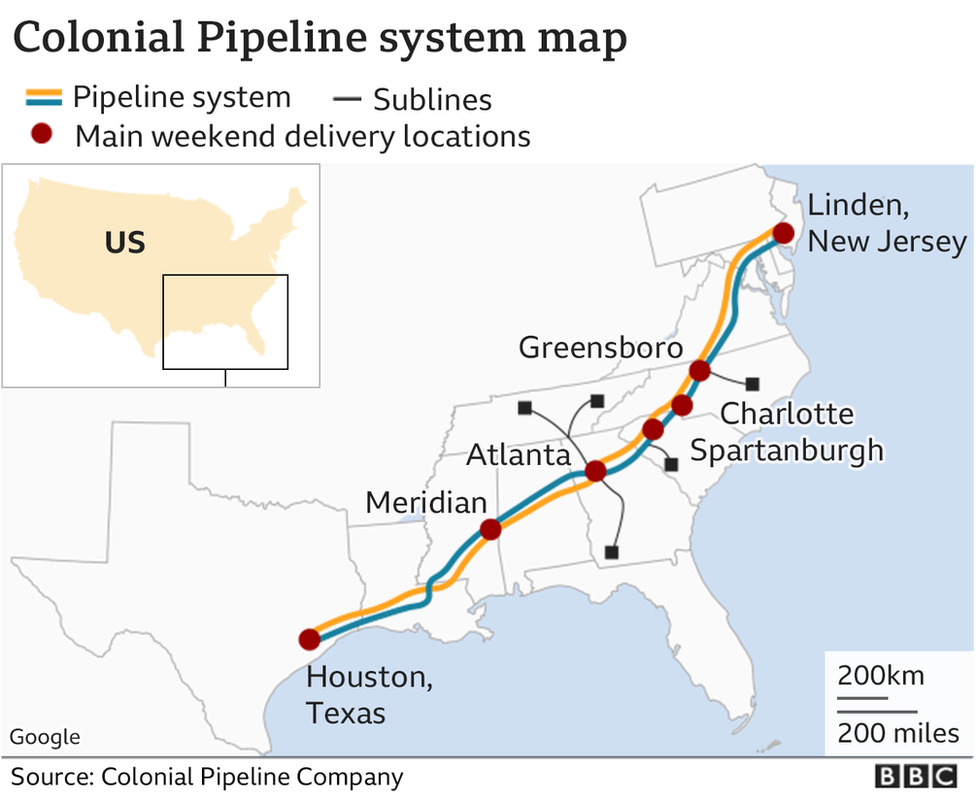
The attack was so severe and alarming that U.S. President Biden had to declare a state of emergency. In total, 100 GBs of data was stolen. The responsibility for the attack was taken by the ‘DarkSide’ group, who took $4.4 million (in the form of Bitcoin) ransom. Unfortunately, even though the company handled the matter wisely and controlled the damage within a short span, it also had to pay a huge chunk of money as ransom to gain back access to its systems.
Book a Free Demo Call with Our People Security Expert
Enter your details
Florida Water System
A cybercriminal attempted to poison the water treatment plant in Florida and increased the amount of sodium hydroxide to a potentially dangerous level. The cybercriminal was able to breach Oldsmar’s computer system and briefly increased the amount of sodium hydroxide from 100 parts per million to 11,100 parts per million. This attack became a major concern for public health but it was stated by the officials that no individual was affected. This brought attention to adopting cyber security measures for water treatment and supply systems.
Channel Nine, Australia
Australian broadcaster Channel Nine was hit by a Ransomware Attack using malware on 28th March 2021, which rendered the channel unable to air its Sunday news bulletin and several other shows. With the unavailability of internet access at its Sydney headquarters, the attack also interrupted operations at the network’s publishing business as some of the publishing tools were also down. Although the channel first claimed that the inconvenience was just due to “technical difficulties”, it later confirmed the cyber attack. The learning of attacks was proposed in the form of updates to the Security of Critical Infrastructure Act, 2018.

Microsoft Exchange Server Breach
A mass cyber attack affected millions of Microsoft clients around the globe, wherein threat actors actively exploited four zero-day vulnerabilities in Microsoft’s Exchange Server. The four vulnerabilities were ‘Server Side Request Forgery’, ‘Insecure Deserialization’, and twice ‘Post-Authentication Arbitrary File’. It is believed that nine government agencies, as well as over 60,000 private companies in the US alone, were affected by the attack. The mass cyber attack on Microsoft Exchange Server has significantly added to the increasing sophistication of cyber attacks. Microsoft found that a group named Hafnium was responsible for zero-day attacks.
Another set of attacks landed on Microsoft Server in December 2021 where the ‘BlackByte Ransomware’ group exploited the Exchange servers using the ProxyShell vulnerabilities. These vulnerabilities were ‘Elevation of Privilege on Exchange PowerShell Backend’, ‘Pre-authentication Path Confusion leads to ACL Bypass’ and ‘Post-authentication Arbitrary-File-Write leads to Remote Code Execution.
CNA Insurance
One of the biggest cyber insurance firms in the US CNA Financial suffered a ransomware attack on 21st March 2021. The cyber attack disrupted the organization’s customer and employee services for three days as CNA was forced to shut down to prevent further compromise. The cyber attack utilized a new version of the Phoenix CryptoLocker malware, which is a form of ransomware. This attack was the largest in terms of ransom demand, which led CNA to pay off the attackers with $40 million (Source: Bloomberg).

Data Breach at Bombardier
A popular Canadian plane manufacturer, Bombardier, suffered a data breach in February 2021. The breach resulted in the compromise of the confidential data of suppliers, customers, and around 130 employees located in Costa Rica. The investigation revealed that an unauthorized party had gained access to the data by exploiting a vulnerability in a third-party file-transfer application (Accellion File Transfer Appliance Software). Also, the stolen data was leaked on the site operated by the Clop ransomware gang.
Ransomware Attacks on Acer
The globally renowned computer giant Acer suffered a ransomware attack and was asked to pay a ransom of $50 million, which made the record for the largest known ransom to date. It is believed that a cybercriminal group called REvil was responsible for the attack. The threat actors also announced the breach on their site and leaked some images of the stolen data. They also committed to providing vulnerability reports and a decryptor to safeguard Acer from further attacks from cybercriminals.
Accellion Breach
Security software provider Accellion fell victim to a breach targeting its file transfer system FTA. Many of its clients were affected by the breach. Some high-profile organizations that got caught in the crossfire include grocery giant Kroger, telecom industry leader Singtel, the University of Colorado, cyber security firm Qualys, and the Australian Securities and Investments Commission (ASIC). The Accellion FTA suffered four zero-day vulnerabilities, which allowed threat actors to install a web shell, known as DEWMODE, which was undetectable. A lot of confidential and sensitive data stolen from various companies by exploiting the vulnerabilities in Accellion’s FTA tool was leaked online. The healthcare industry was most severely affected among all the targets of this attack.
Domino’s Data Leak
Domino’s India, the popular pizza brand, suffered a massive data leak. Customers’ personal data related to 18 crore orders were made available online. The worst part is that this information was made available to the public. Exposed data includes customers’ names, email ids, mobile numbers, and locations. However, the company assured customers that no payment details such as credit card information were leaked in the incident.
Pegasus Spyware
Pegasus spyware attack is considered one of the worst cyber attacks on humans and this ranks among the most sophisticated ones. The spyware was created by the Israeli company NSO Group for government agencies to monitor criminals and terrorists. A leaked list that consisted of more than 50,000 phone numbers, believed to be belonging to the persons of interest for NSO’s clients, made the shocking revelation.

University of the Highlands and Islands
A cyber attack targeted the University of the Highlands and Islands (UHI), forcing the university to close all its 13 colleges and research institutions to students for a day. Security professionals uncovered that the attack was launched using Cobalt Strike, a penetration testing toolkit commonly used by security researchers for legitimate purposes. This incident is just another in a series of cyber attacks targeting the education sector.
Major Cyber Attacks Witnessed Globally in 2020
In 2020, the world was struck by the Covid-19 pandemic. Fresh cases around the world were coming up and people were scared. The time was opportunistic for cybercriminals who exploited the global panic and lockdown to land their attacks in multiple ways. Below are listed some well-known attacks in 2020.
Facebook Data Leak
In April, during the time of the pandemic, when guidelines and rules were taking over the world for global lockdown, around 267 million profiles on Facebook were brought up for sale on Dark Web. Later, many pirated profiles were made using that data, which was later used to trace back the leaked data. The compromised data allowed cybercriminals to carry out spear-phishing attacks on various Facebook accounts.
Read more about Facebook Data Breach Created Havoc Worldwide

Cognizant Ransomware Attacks
One of the largest IT companies, Cognizant, underwent a cyber attack in June 2020. The ransomware attack on Cognizant Technology Solutions (CTS) was carried out by the Maze group. The attack led to the disruption of the services for the clients of the company. The attack compromised customer data which included social security numbers, financial account information, name, tax identification number, passport information, and driver’s license. Later, Cognizant informed the world that they paid a ransom of about $50-70 million to the Maze group.
Microsoft Misconfiguration Leak
Microsoft suffered a data breach in which up to 250 million records were exposed online. The information including email addresses, IP addresses, and support case details, were held on leaky Elasticsearch servers. Microsoft posted a blog notifying the exposure of databases that were unprotected. After investigation, it was found that the exposure was due to misconfigured security rules of the Azure application.
Magellan Health Phishing Scam
The cyber attack on Magellan Health was dual-layered. It was a ransomware cum phishing scam that affected the medical records of 365,000 patients. It was quite a sophisticated attack that began with a phishing scam, which imitated clients’ data and gave access to a server to cybercriminals. They deployed malware on the server which yielded sensitive data of patients. These data were used to carry out ransomware attacks that yielded large amounts of money. Magellan stated that after discovering the attack, they immediately reported the case to law enforcement.
Zoom Credential Breach
Due to the global lockdown, people were forced to remain indoors and the use of Zoom increased significantly. Zoom became popular in a very short span of time to become the most widely used platform for audio and video conferencing. There were multiple miniature incidents and overall user account data of 500,000 users were posted online for sale on the dark web. The credential stuffing is said to be the availability of User IDs and passwords. Additionally, zoom codes were quite easy to guess which allowed users to join meetings anonymously without invitation. They could interfere with the meeting and share inappropriate things. This was known as zoom bombing.
Twitter Spear – Phishing Attack
In 2020, the Twitter accounts of many celebrities were compromised through spear-phishing attacks. In total 130 accounts were hacked including Bill Gates, Kayne West, Barack Obama, Elon Musk, etc. The threat actors used the hacked account to create a bitcoin scam and they also got access to their personal messages. They used the accounts to post a bitcoin scam that offered to double the amount of money. Within 30 minutes, it reached over 350 million people. Finally, it was concluded that more than 130,000 public figures were lured and attackers made $121,000 through bitcoin donations.
Estee Lauder
Cosmetic company Estée Lauder suffered a massive data breach, resulting in the exposure of 440 million records. As soon as the company learned about the breach, they took the necessary action in securing the data and also notified the appropriate parties. Jeremiah Fowler was a researcher who found the unsecured database. However, no information on payment and bank account details were exposed. On the other hand, unprotected IP addresses, email addresses, access ports, etc were exposed.

Experian Breach
There was a major breach in Experian credit card agency which exposed 24 million consumer data of South Africa and 793,749 business entities. The investigation found that there was a client that requested certain services from the company which exploited the database. The company also gave a statement that fraudulent use of data was found. They also specified that the IT infrastructure of the company and customer database were not compromised. The attack raised the concern about enhancing the organization’s security policy.
World Health Organization
The world was already suffering from the pandemic of covid – 19 and at that time WHO was providing guidelines and instructions globally for precautions and safety. But cybercriminals exposed some 25000 email IDs with their passwords and leaked them online. The other organizations who were fighting against Covid were also impacted such as NH, Gates, Foundation, etc.
Whisper
Whisper, a secret-sharing app where you can post anonymous messages, failed to keep messages or profiles private, which resulted in millions of information being exposed for the world to see. The attackers posted all the information of 900 million posts to social media sites anonymously. However, the exposed data didn’t reveal names, but it did expose demographic data such as age, location, gender, ethnicity, etc.
Nintendo
Nintendo informed in April that they have been attacked through mass account hijacking. Around 160,000 users were affected due to vulnerabilities in the legacy login system. This hijacking allowed attackers to have access to payment services to these accounts which are Paypal accounts or credit card information allowing them to make unsolicited digital payments. After the hack was confirmed, the company shut down all their NNID logins and asked the owners to lock their accounts. After an initial investigation, it was found that weak passwords for login were the primary reason for the attack.
/cdn.vox-cdn.com/uploads/chorus_asset/file/10329935/jbareham_180301_2346_nintendo_switch_0034_mario.jpg)
CAM4 Data Breach
In the CAM4 data leak, almost 11 billion records were exposed. It is an adult entertainment company whose names, payment records, and email addresses of the users were exposed. In response to the attack, the parent company took down the database. It was anticipated that this data will be used by cyber attackers to carry out spear-phishing attacks and extort money from it.
