REvil Group (Ransomware Evil), also known as Sodinokibi, is an infamous private ransomware-as-a-service attack group (RaaS) held responsible for several vicious ransomware attacks on organizations worldwide. According to an article by Dark Reading, REvil ransomware scams were the most common ransomware variant responsible for 25% of ransomware attacks from January 2021 to July 2021.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Who is REvil Group?
REvil’s name stands for “Ransomware Evil” and is enlightened by the Resident Evil movie series. Previously, security researchers dubbed the organization’s malware family REvil or Sodinokibi. The REvil group is a hacking organization based in Russia.
The REvil first showed up in April 2019 and became well-known after GandCrab, another RaaS gang that shut down its service. Investigators and security firms initially identified REvil as a strain of GandCrab or established various connections between the two. In a recent interview, an accused member of the REvil confirmed that the ransomware was not a new creation. It was built on top of an old codebase that the group acquired.
How REvil Group Works?
REvil group is one of the ransomware programs used in human-operated ransomware campaigns. Following a successful break-in, hackers perform lateral movement. It obtains domain administrator privileges and deploys ransomware across a network to maximize the impact.
REvil differs from other ransomware attacks in that it encrypts files using Elliptic-curve Diffie-Hellman key exchange rather than RSA and Salsa20 rather than AES. The cryptographic algorithms are highly efficient, utilize shorter keys, and are uncrackable if implemented correctly.
As a consequence of the ransomware, some processes on the infected machine are killed, including email clients and database servers, browsers, Office programs, and other programs that may keep important files locked or backed up. To prevent file recovery, it then deletes windows shadow copies and other backups.
Few Attacks Done by REvil Group
This Russian-speaking cybercriminal group issues the threat of publishing stolen information on its page. If targeted organizations do not pay the ransom after falling victim to launched cyber attacks. Here is a list of some of the most notorious ransomware attacks by the REvil ransomware group:
#1 Renewable Energy Company Invenergy
The Chicago-based clean energy company suffered REvil ransomware attacks in June 2021. The multinational company launched an investigation as soon as unauthorized activity was detected on its systems.
On its dark website, the REvil ransomware group declared that it had successfully carried out a cyber attack on Invenergy and compromised its computer systems, exfiltrating four terabytes of data. The stolen data allegedly included project data and contracts.
What’s even more curious about this attack is that the REvil ransomware group further claimed to have obtained some very personal information about Michael Polsky, Invenergy’s chief executive officer. The gang revealed that it had accessed Michael Polsky’s personal emails, compromising photographs, and sensitive details about his divorce from Maya, his first wife.
#2 Tech Giant Acer
The renowned Taiwanese electronics and computer maker, Acer was hit by a major ransomware attack by REvil in March 2021. The hacking group demanded a ransom of a whopping $50 million!
The ransomware group REvil announced the breach on their data leak site by posting some images of the stolen files as proof. The leaked images consisted of some sensitive documents like financial spreadsheets, bank balances, and bank communications.
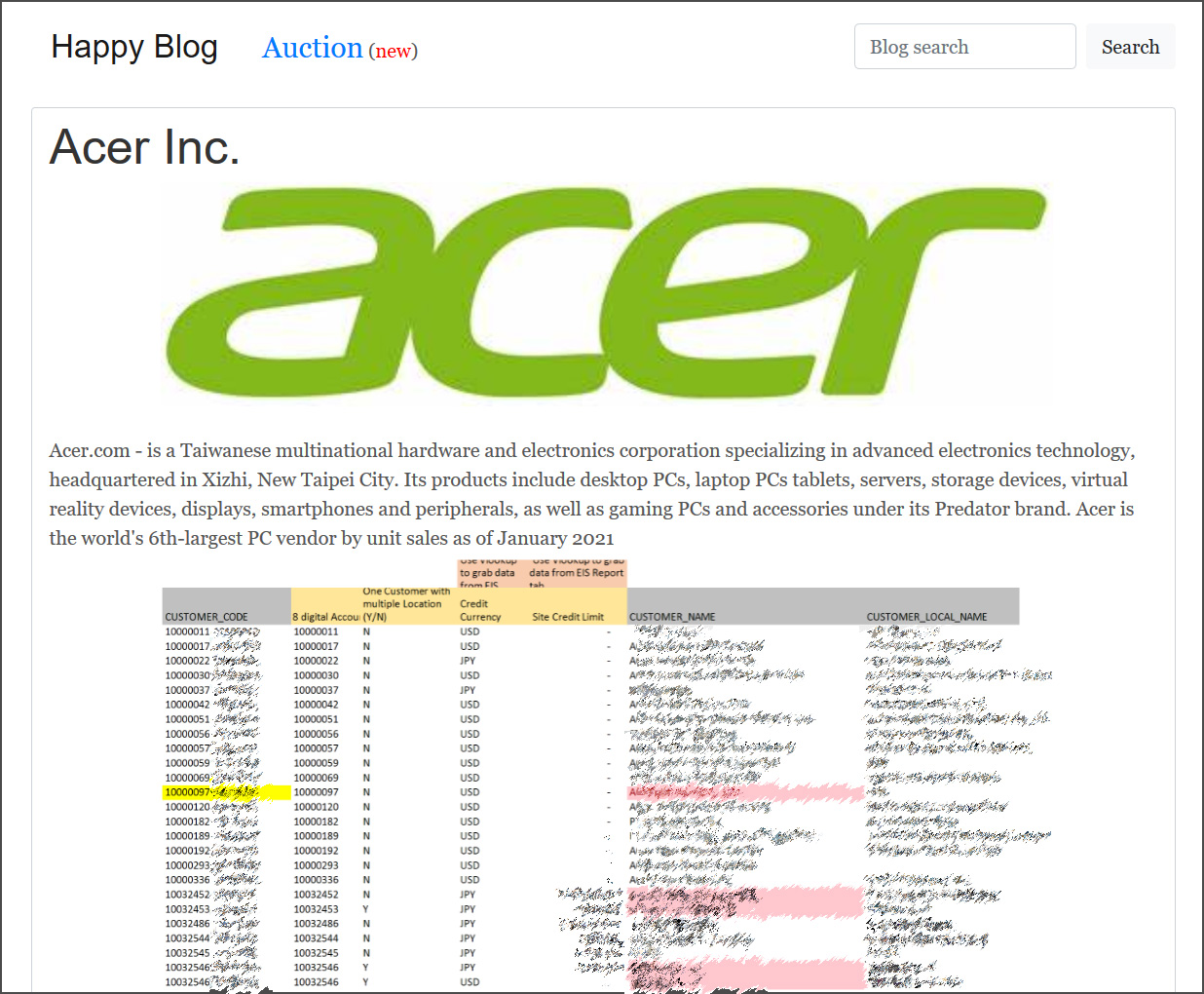
The hackers also offered a 20% discount if Acer made the payment before the deadline provided by the REvil ransomware group. The REvil group had promised to provide the company with a decryptor, the deletion of stolen files, and a vulnerability report in return for the payment.
Acer never admitted to paying the ransom. However, in a statement, the organization said that companies like theirs are constantly attacked. Acer stated that they had reported any abnormal situations to the required data protection and law enforcement authorities.
#3 Software Provider Kaseya
In July 2021, the US-based software provider Kaseya suffered a disastrous ransomware attack by REvil. To launch the REvil ransomware attacks, targeted a vulnerability (CVE-2021-30116) in one of Kaseya’s remote computer management tools called Kaseya VSA.
This infamous attack affected up to 2,000 organizations globally and its fallout lasted for weeks. After the attack, REvil operators boasted about it on the group’s “Happy Blog”, saying that over a million devices were infected. They also stated that they would provide Kaseya with a universal decryption key for a ransom of $70 million in Bitcoin.
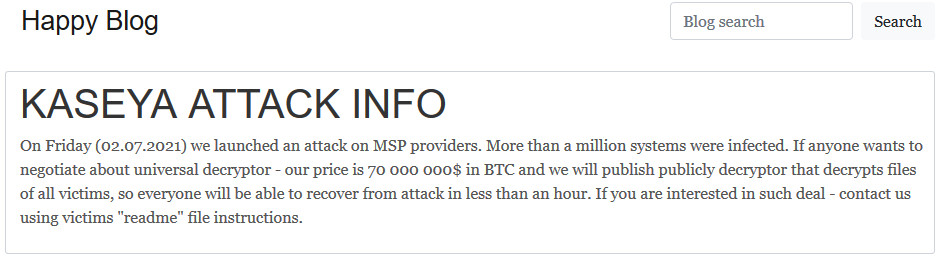
Counted amongst the farthest-reaching REvil attacks to date, the Kaseya ransomware attack created problems for a broad array of public agencies and businesses.
The Swedish grocery chain Coop had to keep most of its 800 stores closed for an entire day since their cash register software supplier was out of service. Two big Dutch IT services companies- Hoppenbrouwer Techniek and VelzArt were also affected among many others.
#4 Meat Supplier JBS
JBS, the world’s largest meat processing company, was hit by a huge REvil ransomware attack in June 2021. The attack disrupted the company’s Australian and North American operations. The company was forced to halt cattle slaughtering at all of the US plants for an entire day, contributing to the inflation in food prices. JBS paid the cybercriminal group a ransom of $11 million in Bitcoin.
JBS was able to restore the majority of its systems with the help of its own backups. It managed to fully restore global operations within a day, which helped in avoiding a prolonged shutdown. In a statement about paying the ransom, Andre Nogueira, CEO, of JBS USA said:
“This was a very difficult decision to make for our company and for me personally. However, we felt this decision had to be made to prevent any potential risk for our customers.”
#5 Apple Supplier Quanta Computer Inc
Quanta Computer Inc, one of Apple’s primary suppliers, was hit by a major REvil ransomware attack in April 2021. The REvil group announced the attack on its dark website, claiming to have infiltrated the company’s computer network.
The hacking group demanded a ransom of $50 million in return for the decryption key. The stolen data included manufacturing and engineering schematics of Apple’s current and future products.
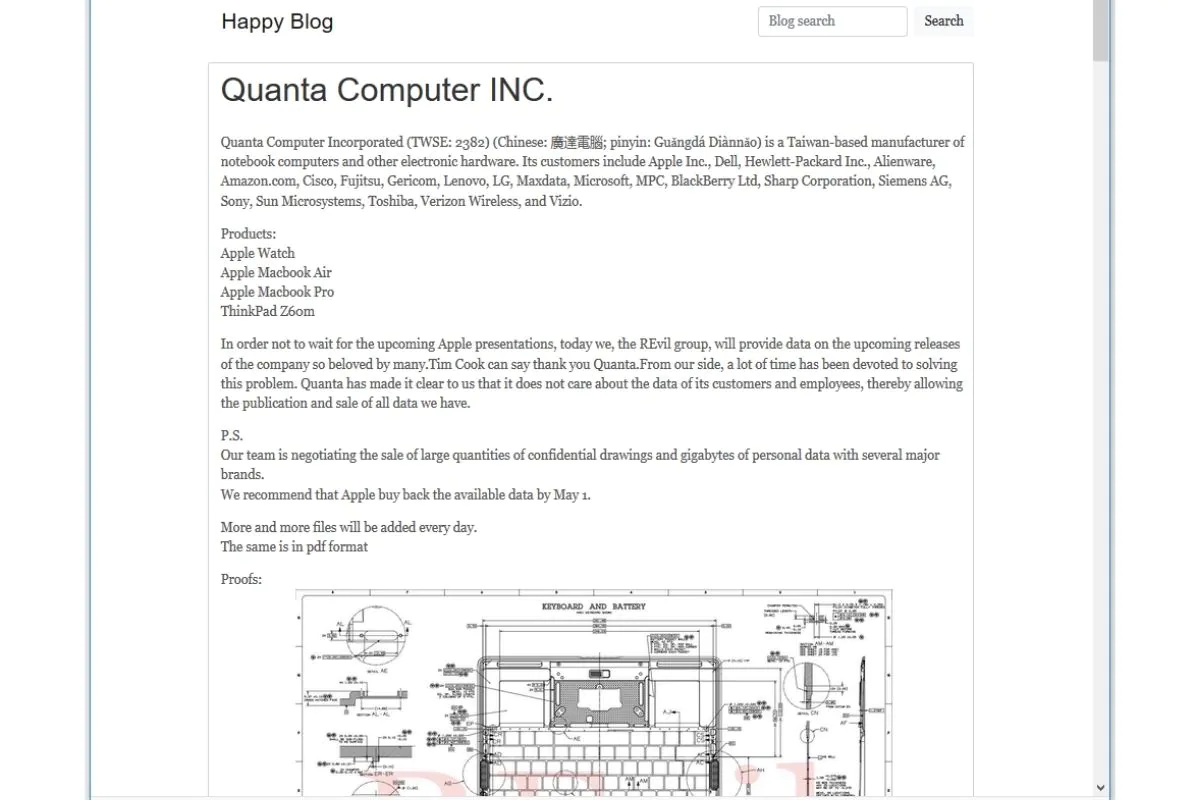
The announcement by the REvil group came on the same day when Apple was set to announce an array of new products at the Spring Loaded event. The cybercriminal group had already posted schematics and designs of new laptops and Macbooks by the time Apple’s product launch was over.
When Quanta Computer Inc refused to pay the ransom, the REvil ransomware group instead asked Apple to pay the ransom by 1st May 2021 if they want to avoid the leak of new files every day.
With several high-profile ransomware attacks under its belt, REvil ransomware attacks have become a menace for every organization around the globe. The growing threat of ransomware can only be contained with the proper application of suitable security controls topped with effective employee security awareness training in your organization.
So, stay vigilant and keep your eyes peeled. After all, prevention is better than cure, right?

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
