Do you use Net Banking or send your personal information on chat or email? Now imagine if someone is capturing or grabbing your data, just because you are not aware of cybersecurity. We are in the 21st century and are in an exponentially growing world, where we are surrounded by technology. In this era, being aware of information security is not only an important thing but also, a need. Although just being aware will not exempt and resolve all your security issues, it will surely help you to mitigate them. So, it is especially important for you to have security awareness training.
Table of Contents
ToggleIf you are still negligent enough and are planning to overlook being aware, then probably you are ready to negotiate with your data privacy. The latest trends show that social engineering has been one of the prominent attack vectors.
What is Information Security?
We generally confuse, between information security and cybersecurity. There is a basic difference between the two, as Cybersecurity gives us the wide aspect of the security included in the digital front, while information security is more focused on the data security part.
When we are talking about information security, we should be focusing more on CIA (Confidentiality, Integrity, Availability) triads. Now let us know, what is a security triad?
Book a Free Demo Call with Our People Security Expert
Enter your details
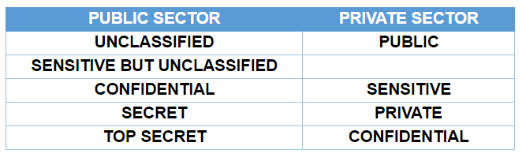
1. Confidentiality:
It keeps the privacy and secrecy of the data. The confidentiality categories of the data are based on the Public and Private sectors according to their respective privileges.
2. Integrity:
In this type of data security, there is no form of alteration in data while it travels from source to destination. It is set up with the help of various hashing techniques so that there are zero discrepancies in data.

3. Availability:
This ensures that users have the proper availability of their data based on their allotted and allowed privileges. According to availability, a user should never lack access to the data he is authorized to view.
Major Attacks Based on Lack of Information Security Awareness
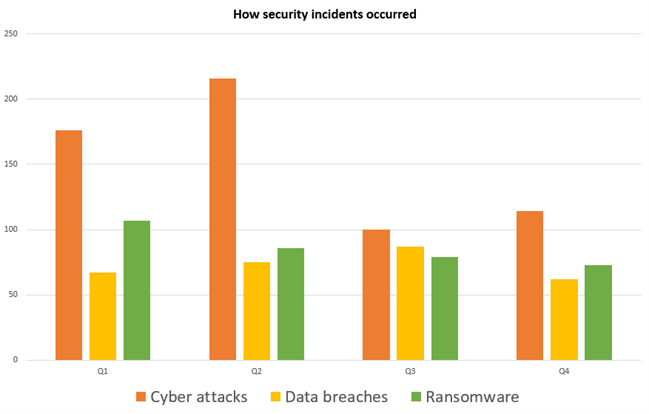
We have mentioned above that in the past few years, most cyber attacks have been tried using Social Engineering.

These are some of the major types of Social Engineering attack that are done by the attacker, and that is the reason we suggest you have security awareness training and education. Employers should also provide employees security awareness training. There are security awareness and management software that help employers to assess and train employees in cybersecurity.
Many auditors say that the organizations and systems with users who are unaware of basic system security are like “low-hanging fruit” and are the weaklings in the process. Organizations can use a solution that will help their employees to be aware of information security.
Some of the social engineering techniques that attackers use are:
1. Pretexting:
In Pretexting attack, the perpetrator tries to impersonate a legitimate authority on call or also tries to text and send a spoofed email, which looks like it is sent from someone known or mutual.
E.g.: Someone befriends you on social media and after some time, he convinces you to reveal/ the information. The link will redirect the victim to an illegitimate website that will look identical to the real one.
2. Phishing:
In this type of attack, the miscreant tries to send a link via mail, or message that creates fear, curiosity, or a sense of urgency in the victim. We call these phishing attacks.
E.g.: For suppose, you receive an e-mail from your bank with an unknown link attached to it. As you click on it, you are redirected to a look-alike webpage of your bank’s official site.
3. Spear Phishing:
There is a difference between spear phishing and phishing. In a spear phishing attack, the attacker tries to impersonate someone from the organization or a higher authority, and then, tries to create an urgent situation and manipulate the victim to give out the details.
E.g.: Suppose the attacker sends the email to the grade one employee impersonating his/her boss asking for information. As the mail is from the high in command the employee without any further confirmation responds unknowingly to the attacker with the data, thus landing the employee into big trouble of falling victim to the spear-phishing attack.
4. Scareware:
A Scareware attack is considered one of the most dramatic attacks compared to all social engineering attacks. The attacker will try to create a false alarm by using a bombarding technique. The false alarm will scare the victim to spill out all the necessary information, which should have been kept private.
E.g.: Suppose you get an Antivirus pop-up with a link, telling your computer is infected, and you need to install this software to remove the threat.
5. Baiting:
In the Baiting attack, the victim is promised larger-than-life things, that get the victim in awe of the bait. This acts as bait for the attacker. As soon as the victim takes a small wrong step, the game is over. Also in this attack, the attacker plants hardware intentionally that has malware in it.
E.g.: Someone conspires to plant a Pen Drive with malware so that someone picks it up and uses it in its system. As soon as the victim plugs in the Pen Drive the malware gets transferred to his system and infects it.
Now, you must decide, who do you want to be?
Top 10 Things to Keep in Mind and be Cyber Aware
- You should never click on unwanted, jazzy, and lucrative links, they may end up infecting you.
- Always keep your PC’s operating system updated.
- Do not go to any link unless provided by a trusted source.
- Use complex passwords (including all numbers, alphabets, and signs with upper and lower cases).
- Change your passwords in the necessary interim intervals.
- You should not open emails and attachments from an unknown resource.
- We should not share any of your private and personal information on a public forum.
- Check if someone is not doing shoulder surfing (trying to peep into your password) while typing passwords.
- Avoid throwing your important old documents in the trash, they can be picked up and be used as information.
- Read the basics of being a secure user.
These are the ways that a user should follow to be safe and cyber aware.
