Are there any differences between cybersecurity and information security? Both terms are used for security purposes and to protect computer systems from threats. Cybersecurity and information security are so closely linked that they may seem synonymous, and they are also used synonymously. If we talk about data security, we secure our data from malicious users and threats.
Table of Contents
ToggleThere are differences between data and information. Information is a group of processed data that, collectively, gives meaning. For those who use the terms “cybersecurity” and “information security” interchangeably, their definitions and understandings vary a lot. Cybersecurity deals with the protection of data from outside the resources on the Internet, whereas information security deals with the protection of information from unauthorized users.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is Cybersecurity?
Cybersecurity is the activity of protecting data that is found on computers, servers, network devices, mobiles, or any other electronic form from being attacked. It deals with the threats that may or may not exist in your cyber realm, such as protecting your social media account, personal information, etc. Cybersecurity can be further classified into five types, critical infrastructure security, network security, application security, cloud security, and information of things (IoT) security.
Cybersecurity usually considers a target against the threats like Social Engineering, Phishing Smishing, Man-in-the-Middle Phish Kits, Pretexting, Email Attacks, Baiting, etc.
According to the reports, cyber threats have significantly increased in India in the last few years. It has been reported that a total of 14,02,809 in 2021 and 6,74,021 in 2022 (till June).
Book a Free Demo Call with Our People Security Expert
Enter your details
What is Information Security?
Information security is the set of procedures and processes that any organization uses to protect its data. The data can be any combination of business records, personal data, or intellectual property. In this, there is a policy setting that will prevent unauthorized people from accessing their company data.
Since now everything is digital, so much important data of the companies are kept electronically on servers, desktops, and laptops. Before the data are transferred into digital forms, they were kept in files and till now some of the confidential data are.
So, information security is concerned with making the data secure in whatever form it is. It protects sensitive data from unauthorized acts (modification, recording, destruction, etc.). It deals with data confidentiality and integrity. Confidentiality refers to protecting the data from unauthorized people. The information can only be viewed by authorized people.
Integrity refers to the act of maintaining and ensuring the accuracy of the data over its entire life cycle. And, availability refers to maintaining the ability to access and use data when needed. The data can be viewed only when it is necessary.
Information security includes processes and technology like anti-malware technology, an information security policy, access control, staff awareness training, etc., which are needed to protect the confidentiality, integrity, and availability of information.
Cybersecurity Vs Information Security
Up until now, we have discussed the meaning of cybersecurity and information security. And now you can understand why people get confused over this. Now let’s see the differences between the two in detail.
| Basis | Cybersecurity | Information security |
|---|---|---|
| Definition | Cybersecurity is the practice of protecting data found in computers, servers, network devices, mobiles, or any other electric form from being attacked. | Information security is the set of procedures and processes used to provide data confidentiality, integrity, and availability. |
| Protect | It is meant to protect the use of cyberspace from cyber attacks. Mainly protects digital data from external threats like viruses, hackers, and others malicious activities that can take place on the Internet. | It is meant to protect the data, whether it is offline or digital, from any form of threat. Protects all types of data from unauthorized access, destruction, modification, etc. to provide data protection to the respective company. |
| Attacks | It attacks against Cyber crimes, Cyber frauds, and law enforcement. | It attacks unauthorized access to the company, data modification, and its disruption. |
| Professionals | The professionals in cybersecurity deal with the prevention of active threats or advanced persistent threats (APT). | The professionals of information security are the foundation of data security, and the security professionals associated with it are responsible for the policies, processes, and responsibilities that assure data confidentiality, organizational roles, data integrity, and availability. |
| Threat | Cybersecurity helps in protecting against various dangers in cyberspace. | Information Systems Security helps with securing data from any form of threat. |
Both information systems security and cybersecurity deal with protecting the data of IT companies from cybercriminals.
IT companies need to protect their data because the information they store is very confidential, and if it gets hacked by hackers or attackers, then the IT companies will incur a huge amount of loss.
That’s why IT companies implement information systems security to protect their company from unauthorized access, data modifications, and disruption.
Many IT companies implement cybersecurity to keep themselves protected from cybercrime, cyberattacks, fraud, and much more.
Cybersecurity Threats and Attacks
Malware Attacks
Malware, or malicious software, is a program inserted into any system to infect or steal information. It can affect the data or operating system. Examples of malware are spyware, viruses, worms, adware, ransomware, Trojan viruses, etc. Malware gets activated when we click on any link or any attachment that contains viruses.
Phishing
Phishing is the most common technique of social engineering that hackers perform. In this type of social engineering technique, hackers use email or other communications and pretend to be from a legitimate source. In those emails, they mention the instructions to send your credit card number, username, password, etc.
Man-in-the-Middle (MITM)
Man-in-the-middle (MITM) attacks are a kind of eavesdropping attack where the attacker detects communication between two parties and listens in on or modifies the data.
Denial of Service (DoS)
Denial of Service (DoS) is an attack that floods a computer, a network, or a server so that it can’t respond to the request. In simple words, the attack shut downs the system and the user is not able to use it.
Major Information Security Threats and Attacks
Insider Threats
Insider threats occur when an individual within an organization has authorized access to its network and misuses it either intentionally or unintentionally to harm the organization’s data. Some employees intentionally break the organization’s rules and policies. These malicious insiders delete data and steal and sell the data that harm the organization.
Virus and Worms
Viruses and worms are types of malware. These perform malware activities that harm the organization’s data and information. Computer viruses are malicious software that spreads between computers and destroys data and software. It doesn’t work until and unless someone activates it. After the activation, the malicious code runs and infects the system without the user’s knowledge.
Drive-By Download Attacks
A drive-by download is another type of information security attack. It’s a malicious code that gets downloaded from any browser, any application, or through the operating system. It gets activated automatically, without any human activity. It is not downloaded intentionally, but when you click on any website, it gets automatically downloaded. The attackers use this threat to get your personal information, harm your entire network with malware, or spy on you.
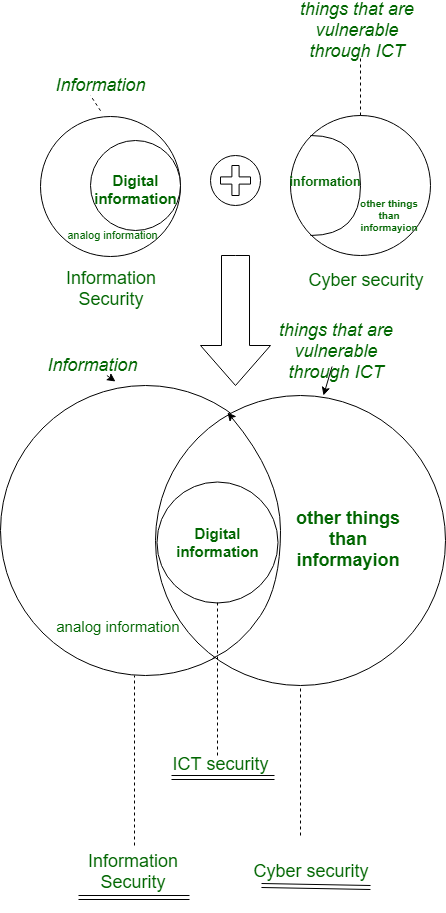
Cybersecurity Vs Information Security: Overlap
Information security and cybersecurity overlap somewhat, which may cause some confusion between the two terms. The majority of the data is kept in digital form. These details are accessible to cybercriminals, who can use them to their advantage.
The main concern that both security types have is the value of the data. For information security, the main concerns are confidentiality, integrity, and availability. Cybersecurity, the main concern is protecting against unauthorized access to the data.
In both situations, it’s critical to recognize the data that, if accessed without a permit, would cause the organization the most harm. Then can a security framework with the appropriate controls be established to guard against unauthorized access.
Final Thoughts: Cybersecurity Vs Information Security
Cybercrime and unauthorized access are not new terms for IT companies. A lot of companies have faced huge data loss due to it. That’s why they must guide their employees about information security or cybersecurity threats and attacks and how to prevent them. Both terms have security in them, but they have a slight difference between them, and the security team of an organization should keep these terms in mind.
FAQs: Cybersecurity Vs Information Security
Here are the major elements of information security:
1. Integrity
2. Confidentiality
3. Availability
Cybercrimes are increasing day by day because of a lack of knowledge about cybersecurity practices.
Hackers’ main motive to attack any company is to make money. There is no particular type they target. However, they would target blockchain as it can make more money.
