Around the world, cyber attacks are spreading like spider webs across the internet to create havoc in the security systems of various sectors. There are multiple different ways to breach data, and the smishing (SMS phishing) technique is one of the ways scammers use it.
According to CPO Magazine, there were more than one million phishing attacks in the first quarter of 2022, a record high. According to a report, the number of scam attempts has tripled since 2020, when the APWG registered between 68,000 and 94,000 attacks each month. In addition to monitoring phishing, social engineering, and other identity theft techniques, the APWG also collects data from its members, researchers, and the general public.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Usually, we think that phishing attacks only happen through emails. Well, now we need to change this point of view as scammers are becoming more sophisticated. One of the new ways is through text messages.
What is Smishing Attack?
Smishing is a blended word, made with the combination of SMS and phishing. Smishing attacks are a part of phishing attacks. It is infamously trending and carries advanced techniques to obtain victims’ data.

Just as cyber-criminals use emails to phish people into opening malware-laden attachments, smishing attacks are carried out using text messages.
SMS phishing, or Smishing, is the unethical practice of sending fraudulent cellular texts to users to trick them into downloading the attached file or making them click on a link. These attached links take users to malware-loaded websites on their mobile phones.
A smishing attack on your cellular device can be launched in any form of attention-seeking text. These nefarious text messages could claim to be from your bank, asking for your financial information. It could also ask in a tricky way for your ATM number or account details to get access to your bank balance.
SMS Phishing Attack Example:
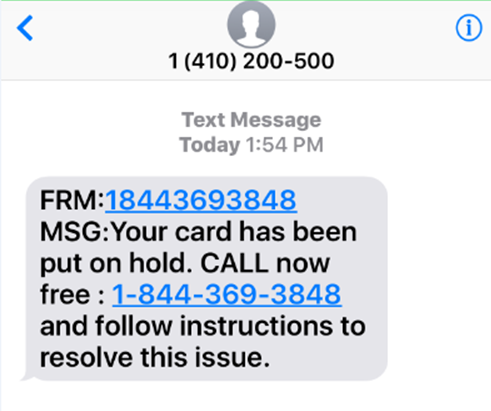
Every day, over 3.5 billion cell phone users worldwide receive phishing text messages from any number.
In an article by Cyware, a smishing campaign, “Lucky Draw Campaign,” was targeted at Indian Nokia owners. In February 2019, Nokia owners received a text message claiming they had won a lucky draw. The message was impersonated to have come from ‘Nokia.com online shopping Pvt Ltd. Co’, claiming that the recipient had won a Tata Safari or Rs. 12, 60,000. However, it urged recipients to pay up to 6,500 Indian rupees to claim their prize.
General SMS Phishing Attack Statistics (2022):
In April 2022, around 378,509,197 spam messages were sent and received per day. An average of 2,649,564,381 text messages were sent per week. Just under 35% of people are aware of when they are the victims of attacks. Smishing operations increased by more than 700% in the first six months of 2021. Smishing attacks have cost victims millions of dollars.
Smishing attackers use phony 2FA (two-factor authentication) messages to steal a victim’s private information. The majority of the time, cyberpunks utilize neighbor spoofing to lure victims. One of the most popular types of smishing attacks is tax fraud. Smishing is the current standard for mobile-based phishing assaults.
How Does Smishing Circulate?
As previously mentioned, smishing attacks can be sent using both SMS and non-text messaging. However, the deceptive nature of SMS phishing attacks enables them to propagate undetected and unnoticed. Users’ false perception of trust in the security of text messages makes smishing deception more effective.
People are less cautious when using their phones. There is a belief among many people that smartphones are safer than desktop computers. However, smartphone security has its limitations and often cannot provide immediate knowledge about smishing. A recent warning from the FBI’s Internet Crime Complaint Center warns that smishing attacks are effective.
How to Prevent Smishing Attacks?
- Never click on any links in text messages that come from unknown resources.
- Refrain from responding to personal text messages that ask for your personal details.
- Verify the legitimacy of the source before responding to any text message that looks like an alert or shows any urgency.
- Look out for messages that are not sent via phone number. Scammers often mask their identity so that their location or identity can not be tracked.
- Never give away your bank details or financial information to any text message asking for your credentials or verification.
- Cybersecurity researchers highly recommend organizations, as well as individuals, use good security awareness tools as a preventive measure.
- Change your account PINs and passwords whenever possible, it helps in keeping your password safe.
- Keep an eye out for odd login sites and other actions when checking various websites or applications.
How can Threatcop help in Smishing Awareness?

An organization could be at risk of losing data to cyber attackers because of its highly vulnerable employees. This tool checks the employee vulnerability level and helps employees become more empowered and proactive against smishing attacks and various other attack vectors.
To avoid SMS phishing, it is highly recommended to implement a cybersecurity awareness tool like TSAT from Threatcop. Train your employees to defend against smishing attacks through smishing awareness training. TSAT by Threatcop is an innovative cybersecurity awareness and personal risk assessment tool.
Threatcop provides SaaS private cloud features for users to freely manage their tools and gives an analysis of hacking records of employees. The most exciting part of this innovative tool is that you can compare the security status of your company at the industry level. There is a wide list of beneficial features when it comes to Threatcop, and you can customize some of its features according to your choice.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
