Many businesses around the world lose millions of dollars due to phishing attacks. The primary reasons behind the success of phishing attacks are employee unawareness and negligence. Phishing is a type of social engineering attack in which threat actors manipulate or lure target users. The frequency and sophistication level of these attacks is increasing with every passing year. However, the number can be significantly reduced by knowing what these attacks are, how they work, and how they are delivered. This blog will discuss the types and techniques of phishing attacks and how to address them.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
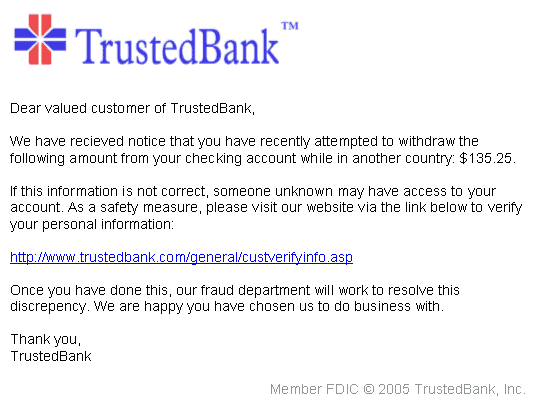
Email Phishing
Email phishing is the most widely-used phishing technique in cyber attacks. When any threat actor sends phishing emails, they target multiple people at a time, luring the target user to fall into a trap and reveal crucial information. Cybercriminals mostly use common tactics like inducing panic, creating a sense of urgency, or offering something the victim can’t resist. Usually, phished emails contain malicious links and attachments that lure users into revealing their credentials and confidential information.
How Does Email Phishing Work?
Cybercriminals either impersonate someone the user trusts or manipulate the contents of emails sent by legitimate senders. This lures and manipulates the target into revealing sensitive information. They will frame the email in such a way that will tempt the user to click on the malicious link or download the attachment that comes with the email. Most of the time, the malicious actors create urgency so that the user doesn’t take time to think carefully about clicking or downloading the link or attachment.
Spear-phishing
Spear-phishing is a more sophisticated form of phishing attacks. In these attacks, cybercriminals conduct extensive research on the target victim before carrying out the attack. The research enables threat actors to lay traps after knowing the whereabouts of the targets so they can manipulate them easily. It also helps cybercriminals create more personalized templates, which makes this attack vector more effective and dangerous than other phishing attacks.

How Does Spear-phishing Work?
In spear-phishing, cybercriminals customize the email templates based on the impersonated user’s position and company. This helps the threat actors trick the target victim into believing the email. However, the motive is the same as email phishing. They will trick the user into clicking or downloading the link or attachment and handing over their sensitive information or installing malware on their system.
Book a Free Demo Call with Our People Security Expert
Enter your details
Whaling
A whaling attack is a type of phishing attack that targets high-profile executives. Basically, in this campaign, cybercriminals target the people that have access to highly valuable information. The attack vector is also known as a whaling or whaling phishing attack. Cybercriminals launch a campaign based on spear-phishing techniques to go after high-profile targets such as C-suite executives.
How Does Whaling Attack Works?
In a whaling attack, cybercriminals often impersonate legitimate C-level executives to lure subordinate employees into clicking on a malicious link that either redirects them to phishing websites or enables malware to be automatically downloaded into their systems. The prime motive is to manipulate the target victim to make a fraudulent transaction or share sensitive information.
Smishing
Smishing is a type of phishing attack in which cyber attackers use text messages to target users. In smishing attacks, malicious links are embedded in SMS/text messages that are delivered via mobile phones. The motive behind the attack is the same as other phishing attacks. I.e., to lure users into clicking malicious links to a phishing website and carry out credential harvesting.
How Does Smishing Attack Work?
Cybercriminals impersonate a bank or other trusted organizations to send out text messages with a sense of urgency, asking users to click on the link and secure their accounts. The links often redirect the victims to a fake website, prompting them to give up credentials or confidential information.

In late 2021, OCBC Bank in Singapore was hit by a series of SMS phishing attacks in which over 800 users lost a total of $13.7 million. The threat actors sent text messages to account holders asking them to secure their accounts.
Vishing
Vishing is a term for “Voice Phishing”. A vishing attack is completely different from other phishing attacks when it comes to delivery methods. In vishing, cybercriminals make a telephone call to the target user and lure them to reveal confidential information. They often impersonate a technical assistant or bank representative, asking users for details of their debit/credit card, employee ID, password, etc.
How Does Vishing Attacks Work?
Vishing is based on social engineering tactics and lures target victims by manipulating them. A vishing attack employs a straightforward method: calling the user and telling them something that will either create a panic situation or excite them about an offer. During the call, the threat actor will try to get a hold of confidential information. Sometimes, in a targeted attack, they can call the target user and ask for an OTP to make fraudulent transactions.
Business Email Compromise
Business email compromise is a type of phishing attack in which cybercriminals target companies that make financial transactions and are in business with several vendors. BEC attacks are infamous for incurring huge financial and reputational damage to the organization. BEC attacks leverage the use of email as a communication medium by impersonating senior officials in an organization.
How Does Business Email Compromise Work?
To carry out a BEC attack campaign, the cybercriminals collect publicly available email accounts of senior employees of the organization. These email accounts of corporate executives or high-level employees are related to those that control wire transfer payments for the company or vendors. Then cybercriminals send them emails that are convincing and well designed to lure them. The targeted victim makes a transfer into a fraudulent bank account, resulting in financial damage to the company.
How to Prevent Phishing Attacks?
There are several ways to prevent phishing. However, the most crucial way to protect an organization against a phishing attack is to train its employees. A trained employee will know how to identify the methods and tactics used by cybercriminals to deliver phishing attacks. Moreover, they will also know how to defend against it and make smart security decisions if they come across phishing emails, messages, calls, etc.
To achieve a good level of cyber resilience and defense, organizations need to employ security awareness training for employees to strengthen the first line of defense, which is humans. Organizations need to incorporate security policies that enforce standard practices making everyone vigilant and the whole organization cyber secure.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
