To understand the concept of VEC attacks (Vendor Email Compromise), it is important to first understand Business Email Compromise (BEC) attacks. So, let’s start off by getting a general idea about BEC attacks.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Business Email Compromise (BEC) Attacks
In a BEC attack, a cybercriminal impersonates an employee, colleague, or executive to send an email to another employee. This email usually contains a request for a fund transfer. The cybercriminal may also ask for personally identifiable information (PII) from employees. In this case, it can further lead to fraud or identity theft.
The emails used in BEC attacks typically carry instructions related to payment approvals or client data sharing. Employees can easily fall into this trap as the criminals usually impersonate a senior employee within an organization.
BEC attacks can lead to huge financial losses. A report by the FBI suggested that BEC attacks cost organizations $26 bn in total over 3 years from June 2016 to July 2019.
Between July 2019 and December 2021, the FBI reported a 65% increase in losses from Business Email Compromise attacks (BEC attacks).
What Exactly is a Vendor Email Compromise (VEC) Attack?
A Vendor Email Compromise (VEC attack) is slightly different from a BEC attack. In a VEC attack, a threat actor compromises and uses the email account of an organization’s legitimate vendor. Equipped with a legitimate email identity, the cybercriminal has now become more powerful than ever
Book a Free Demo Call with Our People Security Expert
Enter your details
Once the target is picked, the attacker designs an email template that suits the setting of the target organization. This makes the email more believable. They send these realistic-looking emails to the employees in charge of handling payments. They attach fake invoices and change the payment information from the vendor’s side to redirect the payment to an account controlled by the miscreant.
This example will give you a better understanding of the spread of a VEC attack:
“A” company has 20,000 suppliers. So practically, there are 20,000 vendor companies whose email domains can be compromised. VEC attacks on “A” company can be launched using these compromised email domains. Therefore, from the point of view of “A” company, a VEC attack can come from 20,000 different sources.
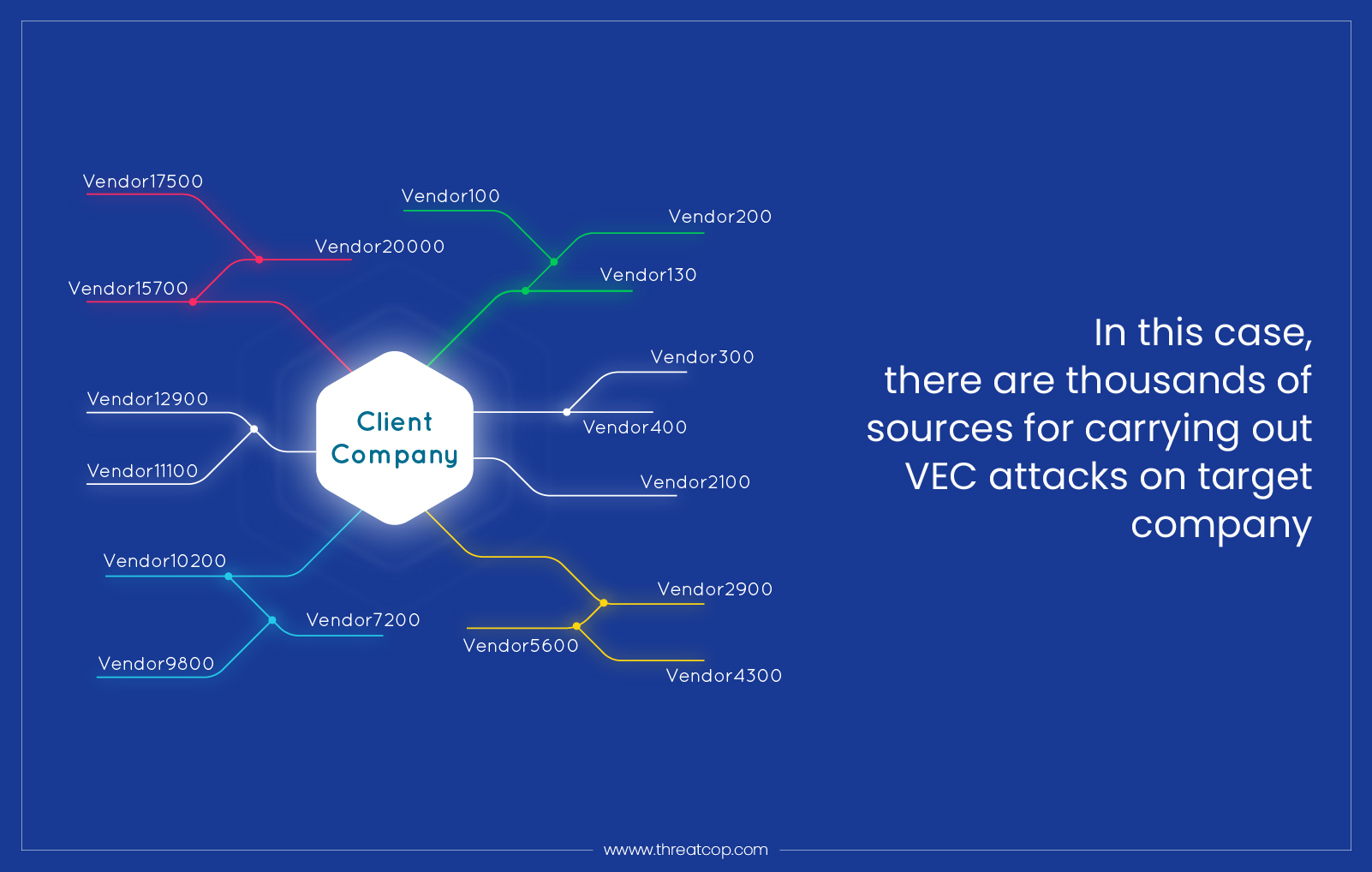
The damage potential of a VEC attack is huge. This is majorly due to the fact that the attacker gets hold of the legitimate vendor identity to launch it. A VEC attack leverages the usual communication between vendors and organizations. This is one major difference between a BEC attack and a VEC attack.
How does Vendor Email Compromise (VEC Attack) Work?
A BEC or a VEC attack relies on social engineering attack. However, it is set apart as in the VEC attack, the targets are supplier’s customers. A payment request is sent to those customers for a service they expect to pay for. There are different phases of VEC attack.
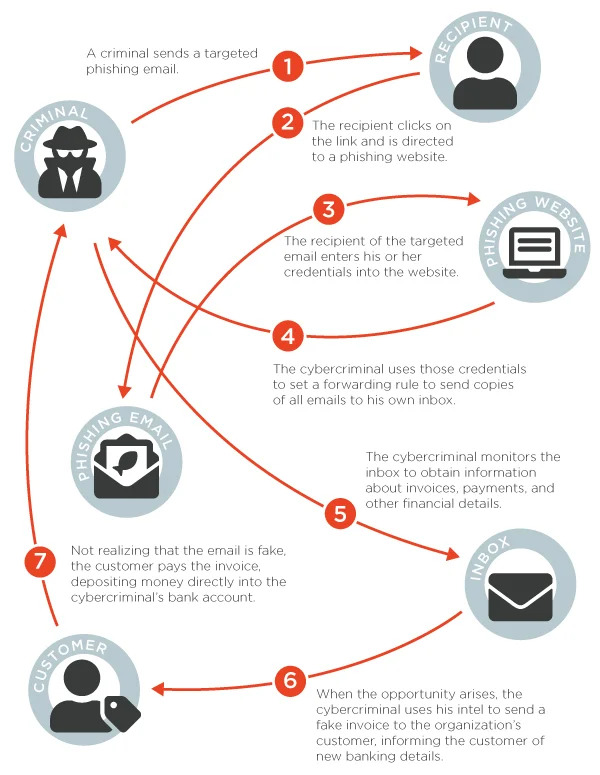
Phase 1: Stealing Credentials Through Phishing
For VEC attackers, the foremost step is to get into the vendor’s email account. To achieve this they run several phishing campaigns. They research those organizations that sell products and services. Then, they send emails containing malicious links to the employees of the targeted company. Many employees think that these links or landing pages are legitimate and may open or provide essential credentials without checking. Those credentials allow attackers to enter and compromise vendors’ email accounts.
Phase 2: Compromised Account’s Takeover
After getting all the details, the attackers can then enter into their email inboxes. After this, they take over the accounts and trail communications. They would create email rules to guide copies of all incoming emails from the relevant vendors to the hackers’ inboxes. After all the rules are implemented, victims are not likely to notice that someone is spying on their email accounts. Therefore, hackers can spy for a long time.
Phase 3: Monitoring the Inbox
In a VEC attack, once an attacker enters a vendor’s email account, they watch the day-to-day activities and interactions closely. These threat actors spend months observing the victim’s behavior. The email exchange between the vendor company’s employees and their customer company’s point of contact is closely monitored to figure out the pattern of raising invoices and payment methods. After noticing these activities between them, they will start the final phase of the scam.
Phase 4: Start Sending Spear Phishing Emails to the Vendor’s Customers
The attacker then proceeds to send spear phishing emails containing fake invoices that look like the usual real ones. The vendor typically sends these emails at the same time the client is billed. The cybercriminal will ask the vendor’s customers to transfer payments to a new bank account under their control by sending these fraudulent emails. These spear phishing emails are expertly designed so as to not cause any suspicion even while departing from the status quo. The VEC attack becomes successful when the customer falls for these emails with fake invoices and sends the money to the new bank account controlled by the attacker.
Two Cases of Vendor Email Compromise (VEC Attacks)
In 2019, an article published by Security Intelligence revealed that the Silent Starling cybercriminal group was conducting VEC attacks. The group launched phishing emails to trick the employees of the vendor companies into giving up the credentials of their official email accounts.
They used these email accounts to watch the email flow pattern between the vendor companies and the client companies. The group waited and watched for a very long period before hitting the target client companies at an opportune time.
They used the compromised email accounts of the vendor companies to send fake invoices to the client companies. The payment information included the banking details of a bank account controlled by the attacker.
In another event, SolarWinds, an American software company, suffered a huge VEC attack. Suspicious activity was observed in its Office365 environment, the company revealed.
Hackers used a compromised email account to gain access to the credentials of SolarWinds’ personnel in business and technical roles. This allowed the hackers to gain access to the SolarWinds Orion Development environment.
A Russian hacking group exploited the vulnerabilities in its software. Around 18,000 of its customers downloaded the compromised version of this software.
Wait, there’s more! As per a 2021 article published by Business Wire, organizations face an 82% increase in the chances of being attacked through a SolarWinds-style VEC attack in a given week. This article also mentioned that the average potential loss from VEC attacks is 144% more than the loss caused by standard BEC attacks.
Protection Against Vendor Email Compromise (VEC Attacks)
Protection against vendor email compromise (VEC Attacks) requires proactivity at every step, i.e., before, during, and after an attack. Firstly, possession of knowledge about these attacks is a prerequisite for organizations to set up a strong defense against them.
Therefore, making sure that everyone on the staff knows what these attacks are and how they work is essential for organizations. Along with this, knowing the correct way of requesting and providing payment details, funds, or sensitive information is also important for the employees.
Furthermore, the employees are less likely to fall for a VEC attack if they are aware of the regular flow of emails in the organization. Any irregularity in this email flow will be enough cause for creating suspicion.
Even if an email doesn’t raise any suspicion due to the pattern of its flow, there will always be something about the content that is odd. It might be the sender’s name, signature, or body of the email.
However, changes in payment information raise immediate red flags. Any email regarding a change in payment information must be immediately verified using methods like video calling the vendor or sending the vendor some codes to revert to.

In an event where the damage has already been done, i.e., if the money has been transferred or the information has been stolen, mitigation measures should be put in place right away. In case of wrongful transfer of money, the insurer, the bank, and the authorities should be informed immediately.
If any sensitive information of the organization has been compromised, mitigation measures should be directed towards minimizing damage to the reputation of the company and preventing the misuse of that information.
Being Vigilant: Vendor’s Duty and Need
As mentioned above, attackers use phishing emails to trick employees of vendor companies into giving up their email account credentials. Therefore, cybersecurity awareness for employees using tools like TSAT becomes essential for an organization. It uses simulation through five different attack vectors to sensitize employees with respect to cyber attacks.
For vendor companies, the implementation of email domain security tools is very important. This minimizes the risk of misuse of their email domain in VEC attacks. An article by Threat Post reported that standard email authentication protection is nonexistent in 80% of company web domains! Isn’t that mind-boggling?
Email authentication tools are game-changers when it comes to preventing email domain misuse. TDMARC is counted among the best email authentication and anti-spoofing tools. It detects and defends email domain forgery.
This tool can identify all the sources that are abusing your email domain and prevent anyone from sending fraudulent emails on your behalf. Consequently, it also increases the email deliverability rate and email engagement rate.
VEC attack is a threat on the rise and it is imperative for both vendor companies and client companies to be on the lookout for them. Vigil and alertness can thwart VEC attacks right at their onset.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
