A threat actor has been found to leverage two of the most popular remote access trojans (RAT attack), including RevengeRAT and Orcus RAT. Organizations belonging to a variety of domains are being attacked by these trojans. In addition to financial services and government entities, remote access trojans are used by attackers to target consultancies and IT service providers.
The infection process has many variations that are linked with the distribution of malware. Most of these attacks are carried out through phishing attacks emails. Several campaigns were discovered after they began embedding their payloads in malicious attachments instead of redirecting the targets to their malware distribution servers. It was discovered that the RevengeRAT and Orcus RAT were being used to backdoor their victims’ computers.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is a RevengeRAT attack?
A dangerous remote access trojan called RevengeRAT or Revetrat allows cybercriminals to remotely access the infected machine and exploit the victim’s system. In most cases, RATs leave no traces on the device. They can infect users for as long as they cannot be traced and spy for a long period. This infection is spread by cybercriminals via spam email campaigns that contain harmful MS Office attachments. A trojan-type infection like RevengeRAT can install itself on your computer and result in some problems.
By using this malware, cybercriminals can access the infected machine and exploit the victims remotely. Viruses spread through spam emails containing MS Office attachments created by cybercriminals. A trojan-type infection like RevengeRAT can cause many problems on your computer. Through RevengeRAT attack, attackers can:
- Manage system processes
- Change the Windows Registry entries
- hosts files
- The account information has been stolen.
- Log keystrokes
- Access Hardware
- Execute shell commands
Modifications to a system can affect its performance, and recovering it can be difficult. Cybercriminals can cause serious privacy issues by logging keystrokes and stealing account credentials. Their main goal is to generate revenue as much as possible. They have several ways to misuse users’ stolen data, such as direct transfer of funds to their accounts.
Additionally, RevengeRAT permits the execution of shell commands that can result in various forms of system control. Injecting malware into the system through shell commands causes chain infections. Typically, RATs like RevengeRAT are used for proliferating infections that have different capabilities. This RAT attack poses a substantial threat to the safety of your computer and should be stopped immediately.
What is an Orcus RAT attack?
Orcus RAT is a remote access trojan that is used to remotely control or access computers and it is installed by spear phishing emails. Cyber attackers trick users into installing these programs and then use them to steal information. It can disable webcam activity lights, password retrieval from applications as well as retrieve browser cookies. It can also use a microphone for recording sound, performing keylogging, etc. This Orcus RAT attack is being promoted on the hacking forums where people can purchase as well as sell malicious programs, hacks, exploits, etc.
To lure people into installing this tool, cyber attackers use spam emails. These emails include attachments that, when opened and downloaded, install Orcus.
Once the tool is installed, it steals passwords and further sensitive details. Some plugins can download files, including computer malware like ransomware attacks. Installing this tool creates a few issues with privacy, financial loss, computer infections, and some serious issues.
How does the RAT Attack Work?
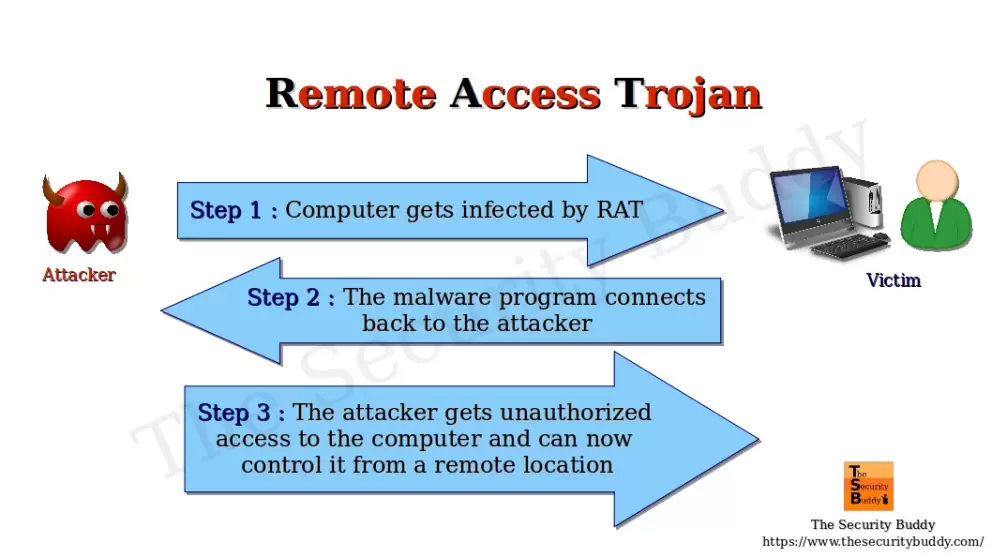
A RAT attack attempts to get backdoor access to a device so that its operators can remotely copy files, perform commands, and observe the target undetected. Like any other virus or malware, it can infect computers. They could be linked to an email, featured on a malicious link, or use an unpatched machine to exploit a vulnerability.
A RAT attack is intended to allow an attacker to remotely control a computer like RDP (Remote Desktop Protocol) and TeamViewer are used for remote access or system administration. Through a command and control channel (C2) established with the attacker’s server, the RAT can receive commands and data. RATs typically include a set of built-in commands as well as methods for concealing their C2 traffic.
The functionality of RATs may be bundled or modularized to provide additional capabilities as needed. For example, when an attacker obtains a foothold using a RAT, he or she might then install a keylogger on the infected system after exploring it. RATs may include this functionality, or users may download and add keylogger modules as required, or launch independent keyloggers.
To gain persistence on targeted systems and evade detection, threat actor groups use email threat attack techniques. The attackers are using the SendGrid email delivery service to redirect victims to the malware distribution server, which is controlled by the attacker. These emails come from various authorities, including the Better Business Bureau (BBB), Ministry of Business Innovation & Employees (MBIE), Australian Competition & Consumer Commission (ACCC), as well as other regional agencies.
What can be done to Evade Such a RAT Attack?

It is important to keep an eye on the latest technologies and emerging cyber threats; however, attackers will always figure out a way to deploy attacks.
Store and analyze logs for tracking where an infection starts and how far the organization went to remediate the infection.
Domain Protection like TDMARC helps in preventing phishing attacks through automated use of email authentication and it can also protect against fraud. It maintains email governance through the analysis, updating, and auctioning against the misuse of domains to send malicious emails.
Organizations should ensure that employee security awareness training, as well as security best practices, are carried out regularly. Cybersecurity training helps employees in building up the capability such as not clicking on links or downloading files that appear to be suspicious.
Organizations can improve employee alertness to defend against cyber attacks with the help of attack simulators and awareness tools. There are many simulators and awareness tools in the market. You need to choose the best for your organization, like phishing awareness and simulation, smishing awareness and simulation, ransomware awareness and simulation, vishing awareness and simulation, and so on.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
