Cyberattacks are becoming increasingly sophisticated and email impersonation is one of the most common forms of phishing attack. Cybercriminals are always looking for new ways to infiltrate big networks and steal sensitive information. Brands are frequently imitated in a variety of services, including illegal streaming sites, retail websites, social media, finance, and more. Microsoft, a reputed IT company, topped the list of hackers’ favorite impersonation brands in 2022. And Microsoft impersonation is a major concern for CISOs (Chief Information Security Officers) around the world.
Table of Contents
ToggleMicrosoft, Meta, Yahoo, and PayPal are among the most impersonated brands by hackers. According to a report by a cybersecurity organization, Microsoft edged out Facebook for the top spot among the 25 businesses that phishers most frequently impersonated in the first half of 2022, with a total of 11,041 distinct phishing URLs. The Indian Express reported in 2021 that 36.6% of phishing attacks were orchestrated by impersonating the product pages of Microsoft.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Why is Microsoft a Hacker’s Favorite Brand to Impersonate?

Microsoft and Google top the list of most impersonated brands with 42,226 phishing pages, surpassing all combined cloud brands at 38,893. Today 70% of businesses universally depend on Microsoft’s cloud services which makes it a lucrative target for impersonation to steal exclusive data from Microsoft 365 applications. Intruding into a Microsoft 365 account also enables hackers to carry out inside attacks. The attacks include, malware distribution, ransomware attacks, and user manipulation for business email compromise.
Book a Free Demo Call with Our People Security Expert
Enter your details
Hackers pose as Microsoft by making false login pages, phishing emails, and social engineering assaults, hackers pose as Microsoft. These attacks can infect the victim’s system with malware or steal sensitive data like login passwords. Microsoft 365 is the #1 most popular productivity suite in the world. With more than 240 million corporate members, Microsoft’s hugely successful 365 platforms have made the company an appealing target, leading to a 266% quarter-over-quarter increase in phishing attempts impersonating the company this year. According to the report, productivity suites have grown to be a desirable target for phishers. As it provides additional chances to take advantage of users both before and after a first intrusion.
Read More– Email Impersonation Attack are on the Rise
How do Threat Actors Implement the Email Phishing Attacks?
Phishing emails mimic authenticity but are designed to extract personal information or money, posing a major global concern for individuals and businesses. Phishers will create malicious domain names claiming that they belong to these well-known trusted brands to hack your data. The sender will be tagged as unverified to alert the recipient that the sender might not be who they seem to be if the message is suspicious but not malicious.
“Hackers play on our faith to carry out phishing attacks as they target the companies we use every day. It is becoming harder for even the most technologically adept individual to recognize. Our bank accounts, passwords, and sanity shouldn’t be jeopardized because we overlooked the ‘from’ field or unintentionally clicked on a tricky URL,” according to Matthew Prince, co-founder and CEO of Cloudflare.
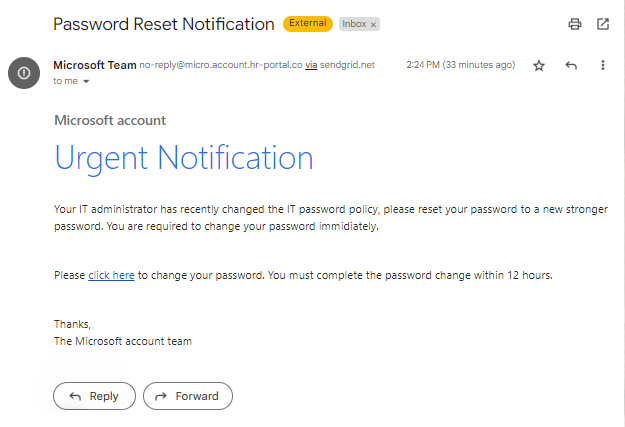
Phishing attacks are carried out by threat actors against businesses that store a lot of sensitive customer data. Cybercriminals search for potential victims by sending out emails and setting up phony websites using social engineering techniques. Phishing attacks against the retail and wholesale sector increased by 436% in 2021 compared to 2020. As the pandemic drove increased online shopping, threat actors capitalized on the opportunity. As the pandemic drove increased online shopping, threat actors capitalized on the opportunity. However, it is the consumer confidence and brand reputation that suffer the most when retailers are targeted by phishing attempts.
Methods Used by Attackers to Impersonate Microsoft
Hackers Abused Microsoft’s “Verified Publisher” OAuth App
Last year, through the Microsoft Cloud Partner Programme (MCPP), commonly known as the Microsoft Partner Network (MPN), a collection of threat actors successfully attained “verified publisher” status. According to Microsoft, the attackers registered fake versions of apps with plausible names like “Single Sign On (SSO)” and “Meeting” that were disguised with convincing visual cues like Zoom’s older video symbol and Zoom-like URLs. In order to join the MCCP, the attackers first pretended to be legal businesses. Then they used these identities to add a verified publisher to “OAuth app registrations” that they had made in Azure Active Directory (AD).
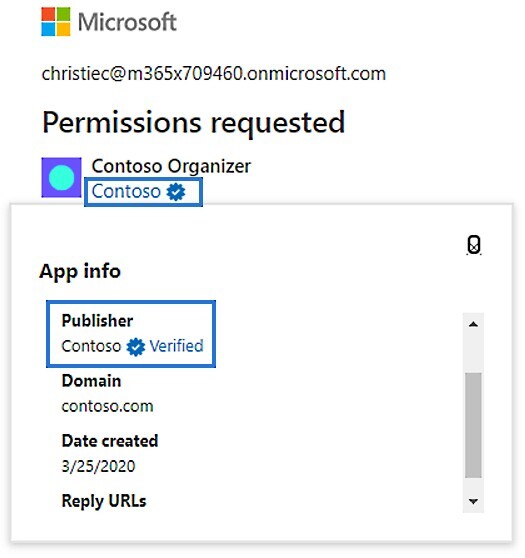
To become a “verified publisher,” the software publisher must confirm their identity using their Microsoft Partner Network (MPN) account and link it to their app registration. According to Microsoft’s guidelines, a blue verified badge is displayed on the Azure AD consent prompt and other web pages once the app publisher’s verification is complete. It’s important to note that Microsoft refers to third-party OAuth apps created by external companies as “publishers.”
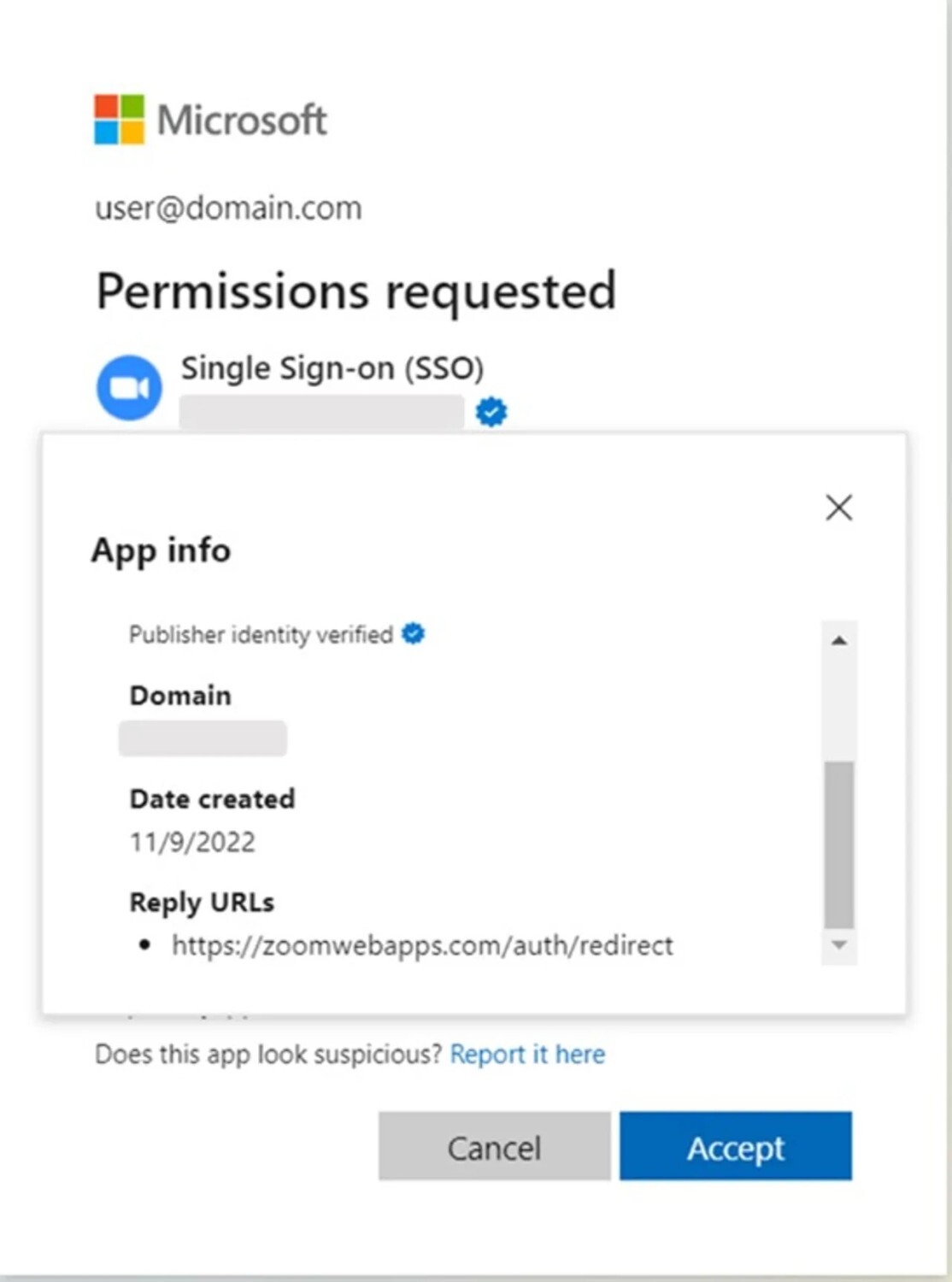
Consent Phishing
Microsoft calls it “consent phishing” as attackers trick users into granting access to fake apps, potentially compromising sensitive data for an extended period. In consent phishing, users unknowingly grant permissions to malicious cloud apps, allowing access to their data and legitimate cloud services.
The attackers specifically targeted managers, executives, as well as marketing and finance staff using deceptive software solutions. Through malicious software, the fake solutions partners targeted managers and executives as well as staff in marketing and finance. Users who click on the fake badge put themselves at risk of data exfiltration, and brand impersonation for their companies.
The manufacturer of Windows claimed that on December 15, 2022, it learned about the threat. The impacted customers were subsequently notified through email, and the business noted that the threat actors had exploited the permission to exfiltrate mailboxes. On December 6, Proofpoint discovered the fraudulent third-party OAuth apps, and on December 20, it notified Microsoft. It mentioned that the phishing effort was over on December 27. On December 15, Microsoft learned about the consent-phishing campaign. Microsoft says that the hackers targeted UK and Ireland-based customers.
Microsoft has bolstered security measures for the Microsoft Cloud Partner Program to enhance vetting processes and mitigate future fraud. They have taken ownership of the fraudulent apps and alerted impacted customers. The hackers employed remarkable sophistication to evade Microsoft’s security mechanisms, making this phishing attack exceptionally well-executed.
Also Read: Implement DMARC to Ensure Email Security
Microsoft Bing and Cortana Source Codes Compromised
In March 2023, a group of threat actors known as “Lapsus$“- which is also labeled as a “large-scale social engineering and extortion campaign” by Microsoft had carried out a data breach and obtained a file containing partial source code from Bing, Bing Maps and Cortana. The software giant revealed that a breach occurred in an employee’s account, leading to the theft of the company’s source code.
The notorious group of hackers released its most recent update, which included uploading a 9GB archive containing the source code for 250 Microsoft projects. The organization asserts ownership of 45% of the source codes for Bing Maps. Whereas, Cortana and 90% of the source codes for Bing itself. The complete collection of stolen information consisted of 37GB of Microsoft source code, with the mentioned portion being just a fraction.
The company confirmed viewing the source code does not lead to an elevation of risk. The hackers had “limited access” to the source code as they had control of a single account and just after this, the cybersecurity team responded quickly to prevent further activities. Microsoft provided the Lapsus$ group’s tactics, techniques, and procedures observed by its Threat Intelligence Center, known as MSTIC.
MSTIC has observed multiple attacks and reported that these attacks targeted organizations in South America and the U.K. Lapsus$ has its new global targets, including governments and companies in the technology, telecom, media, retail, and healthcare sectors. The hacker organization LAPSUS$ is unusual.
Why is Microsoft Impersonation a Major Concern for CISOs?
CISOs worldwide express significant concern about Microsoft impersonation, given that many organizations utilize its email and cloud services. Which makes it a potential target for sophisticated cyberattacks and enables unauthorized access to sensitive information.
Prevalence of Microsoft Products
Microsoft’s software and services, such as Windows operating systems, Office Suite, and cloud-based solutions like Azure and Office 365, are widely adopted by individuals and organizations worldwide. This ubiquity makes Microsoft an attractive target for cybercriminals seeking to exploit its brand recognition and trusted reputation.
Phishing and Social Engineering Attacks
Microsoft impersonation often involves phishing attacks that trick users into divulging their login credentials or installing malicious software. Cybercriminals may impersonate Microsoft emails, websites, or login prompts to deceive users into providing sensitive information.
Business Email Compromise (BEC)
Adversaries frequently leverage Microsoft impersonation in BEC attacks, posing as high-ranking executives or trusted partners. By spoofing Microsoft email addresses, attackers deceive employees into initiating fraudulent wire transfers, sharing confidential data, or compromising internal systems.
Read More: Top Real-life Examples of BEC Attacks
Will Human-Centric Cybersecurity Help?
Do you have enough confidence in your employees’ intellect that they can safeguard your business from such breaches? Or maybe the right question would be have you empowered them enough? Let’s see what the latest data disclosed about both the stakeholder. According to the “2022 State of Email Security Report” by Mimecast, 90% of businesses had been the target of impersonation attacks in the preceding year. The number of new domains suspected of imitating popular brands increased by 366%.
Additionally, the Mimecast “2021 State of Brand Protection Report” discovered that impersonation attempts for the “BrandZ Top 100 Most Valuable Global Brands 2020” list brands have increased by 381% during the months of May and June 2020 in comparison to the months prior to the pandemic.
According to Gartner’s latest report, 90% of employees knowingly engage in unsecured actions that compromise company security and privacy. And following this, the Gartner report also mentioned that 50% percent of CISOs globally will adopt the human-centric design to reduce cybersecurity operational activities. Large enterprises will focus on implementing zero-trust programs.
A report named Cyberthreat Defense also cited that low-security awareness among employees is the most significant weak point of these impersonation attacks. CISOs are concerned about these factors and shifting their focus to People Security Management. People Security Management focuses on individuals, not technology or threats, to minimize friction and improve control implementation.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Actions CISOs Can Take to Implement People Security Management
CEOs should actively seek information and participate in building a strategic risk framework, aligning cybersecurity with business demands. They should also ensure routine evaluation of cybersecurity issues, IT strategies, and cloud services. The following are the top security measures a CEO should take:
Educate Partners, Customers, and Employees
Regular consumer education reduces brand impersonation scams by distinguishing between fake and genuine articles. Which lowers the likelihood of falling for popular scams. Make cyber security training for all staff a requirement
Regular cyber training for employees
Training ensures that each employee is aware of the company-specific cybersecurity risks. The purpose of these sessions is to clearly outline staff roles and responsibilities in preventing threats and breaches and responding to them. By teaching your team about cyber security issues and their roles and responsibilities in protecting networks, systems, and IT assets, you may lower the risk to your business. To create awareness, You can use tools like Threatcop Security Awareness Training (TSAT). This will make your employees resistant to social engineering attacks.
Consider BYOD policy
BYOD (bring your own device) is a policy that allows employees to use their personally owned devices. It is not a bad practice but there must be safeguards in place. You can restrict your employees from accessing exclusive data from their personal devices.
Mobile devices are vulnerable to hacking, with a study revealing that around 50% of IT executives reported significant financial losses, exceeding $250,000, due to security incidents involving personal mobile devices. Nonetheless, there are security measures you can adopt to safeguard mobile apps against threats. Mobile app security testing tools (MAST) play a crucial role in enhancing app security by conducting testing and detecting potential vulnerabilities.
Restricted data access
Your organization should provide cybersecurity education to every employee. However, not every employee should have access to all of the data gathered. For this reason, the CEO must ensure the arrangement of every piece of data gathered from clients.
Limited data on client information promotes responsibility and reduces the possibility of data breaches on by human error or carelessness. Using password protection for various employee hierarchies is one technique to restrict access. Moreover, the adoption of two-factor authentication reduces the likelihood of unauthorized individuals using compromised passwords to access data.
As a CISO, you’re the gatekeeper of the company’s exclusive information. Given the ubiquity and sophistication of cyberattacks, it is imperative to be cautious and proactive in defending against such threats. You may reduce the dangers connected with Microsoft impersonation and fortify your organization’s defenses by implementing a thorough cybersecurity strategy. Are you doing everything you can to prevent your company from becoming the next victim of a cyberattack?
FAQs: Microsoft Impersonation Attack
Brand Impersonation is a phishing tactic by hackers wherein they pretend to be a legitimate website to win the trust of the target. You saw those emails in your junk mail box where the sender ask you to click a link? The idea behind it is to get you to click the URL and give sensitive information by logging in along with your username and password.
Threat actors use look-alike or cousin domains with near-identical names, but with minor differences to confuse the target. This technique is often used to trick users into thinking they are legit.
The goal of an email impersonation attack, a sort of phishing assault, is to fool the receiver into clicking a malicious link or attachment by pretending to be a legitimate sender. Obtaining the account and password to access the restricted data is the goal. For instance, the username for “[email protected]” is “bill. gates”. Although username impersonation is the least complex type of email impersonation, it nevertheless has the potential to fool an unwary victim.
Impersonation is one of several social engineering tools used to gain access to a system or network in order to commit fraud, industrial espionage, or identity theft. Impersonation is a form of social engineering because it uses psychological manipulations to make people do a security mistake by clicking on a link.
Impersonation attacks are a type of cyber attack where the attacker tries to deceive a targeted individual by posing as someone else, usually through email. These attacks don’t rely on malware but rather exploit social engineering techniques to gain the victim’s trust.
The main targets of impersonation attacks are employees who have the authority to initiate financial transactions or access sensitive data. The employee receives an urgent email that seems to be from a trusted source demanding immediate action such as wiring money to a specific account or sharing confidential information.
Security Compliance Executive
Department: Compliance, Threatcop
Sanjana is a Security Compliance Executive working on best-of-the-industry-level compliances relevant from a cybersecurity perspective, their implementation, learning and outcomes in various business domains.
Security Compliance Executive Department: Compliance, Threatcop Sanjana is a Security Compliance Executive working on best-of-the-industry-level compliances relevant from a cybersecurity perspective, their implementation, learning and outcomes in various business domains.
