Along with the evolution of technology, a rapid and dramatic shift has been experienced in the occurrence of cyber attacks. The new targeted email-based phishing attacks have replaced the old extensive spam attacks. These phishing campaigns are causing major financial, brand, and operational harm to organizations across the world. The most notorious crime that is affecting major banks, corporates, media companies, and even security firms is a phishing email attack.
Table of Contents
ToggleAmong the types of social engineering attack, phishing and spear phishing are a few. Malware such as ransomware is spread through malicious links and downloads through both regular phishing and spear phishing attacks. However, there is a difference between spear phishing and phishing.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is Spear Phishing?
Spear phishing is an email scam that is targeted toward a particular individual, an organization, or a business. Attackers install malware on the targeted user’s computer system besides stealing the user’s data.
Follow the image to understand how a spear phishing attack works:
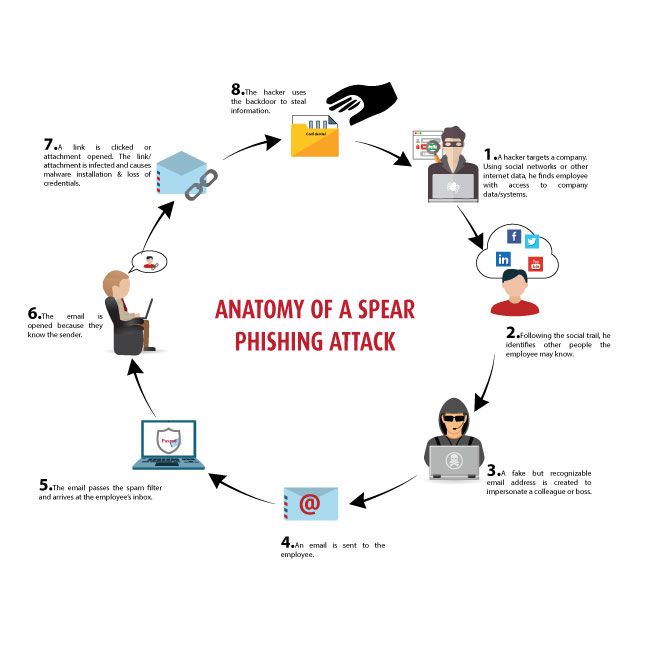
Spear phishing attack example:
Spear phishing and phishing attacks are deployed with similar forms of email attacks which include a typical malicious link or an attachment. The primary difference between them is the way of targeting individuals.
For instance, you have posted a social media update about traveling to a different state or country. You might receive an email from a colleague saying, “Hey, while you are in New York, make sure to try the famous Joe’s Pizza. Click Here, *link* to check out their menu list!” While you click on the link to browse their menu, a malware is quickly installed in your system. Such emails are sent to target individuals by tricking them with a spoofed email address of someone they know or are well acquainted with.
Book a Free Demo Call with Our People Security Expert
Enter your details
How Can We Define a Phishing Attack?
While spear phishing emails are sent to target a single recipient, phishing emails are sent to a large number of recipients. It is an unethical use of electronic communication to deceive users by taking advantage of their vulnerability in cyber security.
These attacks are carried out to obtain sensitive and confidential information like the credentials of users. Cybercriminals use social engineering to trick victims into performing certain actions such as clicking on a malicious link or opening an attached file.
Phishing attacks are wide-spreading cyber threats every year. If you are not yet aware of this ever-growing cyber scam then one wrong click can easily flip your world upside down.
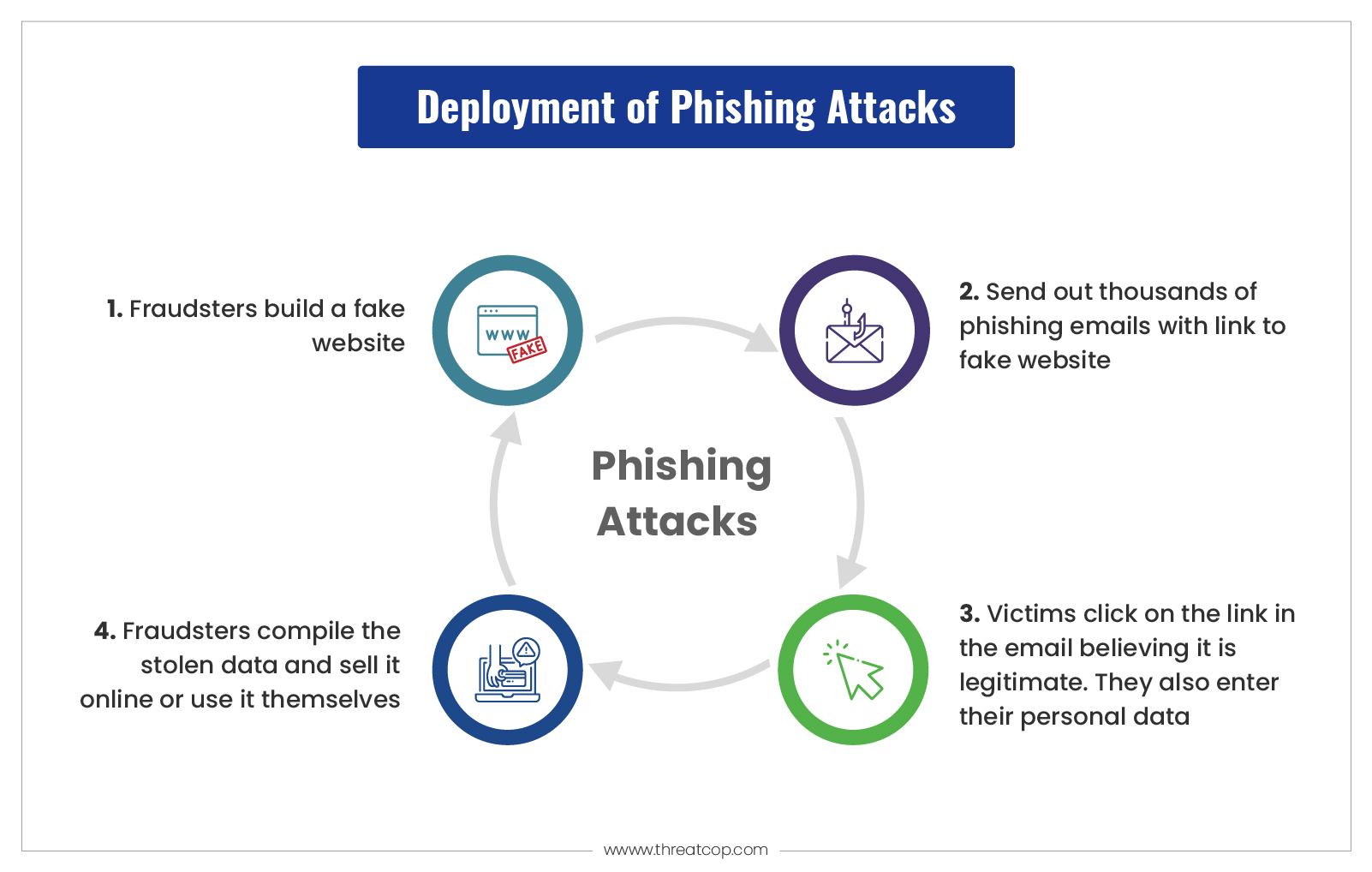
Phishing attack example:
Here is a real-life phishing attack example of Facebook and Google. Both the companies were together scammed out of $100 million+ between the years 2013 and 2015 through a fake invoice scam. A Lithuanian hacker accomplished this feat by sending a series of fake invoices to each company. It impersonated a large Asian-based manufacturer that they used as their vendor.
Such phishing attacks have been exploiting the data of various organizations and have led to a huge loss in revenue for many organizations. Be it phishing or a spear phishing attack, it is vital to take preventive measures to decrease the occurrences of these cyber attacks.
What is the Difference Between Spear Phishing and Phishing?
The main distinction is that phishing requires little effort and is not tailored to each victim. Spear phishing requires significantly more effort but is considerably more rewarding when successful, so spear phishing prevention is critical. There are only a few victims in a spear phishing attack, whereas there are many victims in phishing.
Spear phishing is directed at a particular individual, team, or organization. Regular phishing emails, on the other hand, take a broad approach that includes sending bulk emails to larger datasets of unsuspecting contacts. These spear phishing attacks are quickly crafted and usually don’t include confidential info about the recipient.
Spear phishing may be even scarier than traditional phishing because of its hyper-targeted nature. In addition to being more difficult to detect, spear phishing messages have a familiar tone and content, making them more dangerous.
How to Avoid Spear Phishing attacks?
The following steps can be taken to avoid phishing attacks:
Spelling & Grammatical Errors:
Usually, genuine emails are error-free because of the professionalism and image reputation they hold. On the other hand, spear phishing emails have spelling and grammatical errors that are oblivious to the recipient’s eyes.
General Greeting:
If you are in contact with any individual or an organization, they would certainly use your name in the email greeting. But if an email says anything unusual like “Hello email user or attn: user”, then it’s a red alert.
URLs & Attachments:
Cyber crooks make sure to convince users into clicking on the link or on the attachment that comes along with the email. Never click any of the attachment that comes with suspicious-looking email.
Cybersecurity Awareness for employees:
Every employee and individual in an organization should be provided with proper employee security awareness training. A simulation on spear phishing attacks can be performed on the employees in order to make them proactive towards the latest attack vectors.
How Does an Employee Security Awareness Training?

Cybersecurity awareness and training programs can be used for training employees and individuals in the organization regarding cybersecurity practices.
A security awareness tool like TSAT from Threatcop is a security attack simulator and awareness tool that assesses the real-time cyber security threat posture of an organization and reduces their cyber risks up to 90% from the people’s perspective.
This tool happens to be the most effective product for employee cyber awareness training it comes with highly beneficial features. It offers LMS (learning management system) and a large number of security attack simulation cycles to help employees in becoming proactive against the latest cyber risks. Along with the above-mentioned tips and cyber awareness training products one can have the benefit of a worry-free online experience.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
