Email is the primary means of business communication, which makes its protection a major concern for organizations today. Email security involves the implementation of practices and solutions meant to protect email channels and servers against cyber attacks.
Table of Contents
ToggleThreat actors carry out email-based attacks in different forms like phishing, spoofing, business email compromise, etc. The majority of these attacks rely on manipulating employees and are called “social engineering attacks.”
What Does Email Security Mean?
Email security refers to the implementation of a set of techniques and procedures to protect email accounts and prevent email-based cyber attacks. These techniques are meant to empower email service providers and employees to make sure that organizations don’t get attacked.
There are multiple mechanisms for implementing email security including:
- Email Authentication Protocols
- Email Security Policies
- Email Security Awareness and Training
- Secure Email Gateways
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Why is Email Security Important?
Email security involves enhancing security on a technological level as well as an individual level. The purpose of email security is to ensure that threat actors don’t get past the first line of defense. It also saves employees time by filtering out irrelevant emails.
Book a Free Demo Call with Our People Security Expert
Enter your details
There are some email authentication standards like SPF, DKIM, and DMARC that help you protect your outbound email channels. This helps in increasing the reputation of the domain and enhances the email deliverability rate.
Read more about Sender Policy Framework (SPF): Email Authentication Protocol
Read more about DomainKeys Identified Mail (DKIM): An Email Security Protocol
Types of Email Threats
There are several different types of email-based threats. Some of the most popular and commonly used include:
1. Phishing Emails for Credential Theft
Phishing emails are the most common method to lure targets into revealing confidential or sensitive information. The contents of phishing emails are specifically designed to manipulate the target into clicking on a malicious link or downloading a malicious attachment.
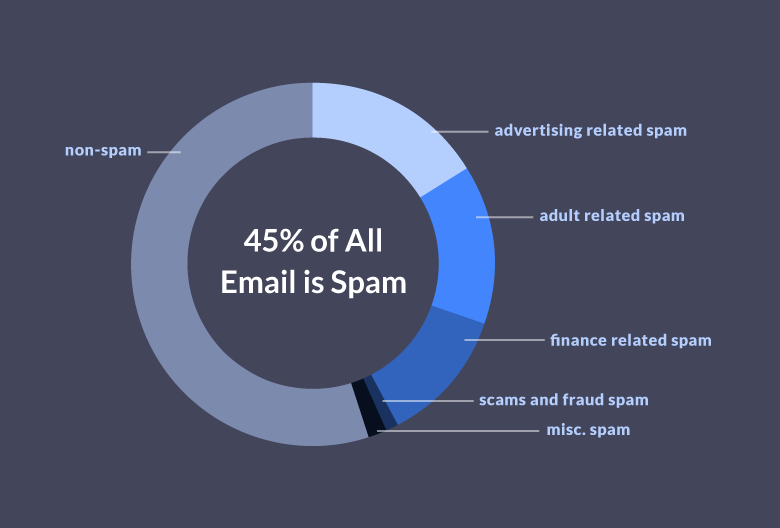
45% of all the emails are spam. (Source: Propeller)
The major portion of spam emails sent daily is generated from the United States, followed by Korea. Usually, the major objective of phishing emails is to steal credentials, but sometimes they lure users to download attachments that contain malware.
2. Business Email Compromise
A BEC attack is a type of highly sophisticated spear-phishing attack. The targets of BEC attacks are mostly C-level executives. That’s why it is popularly also known as “CEO fraud”. In this attack, threat actors invest a certain amount of time in studying the victim to know their whereabouts.
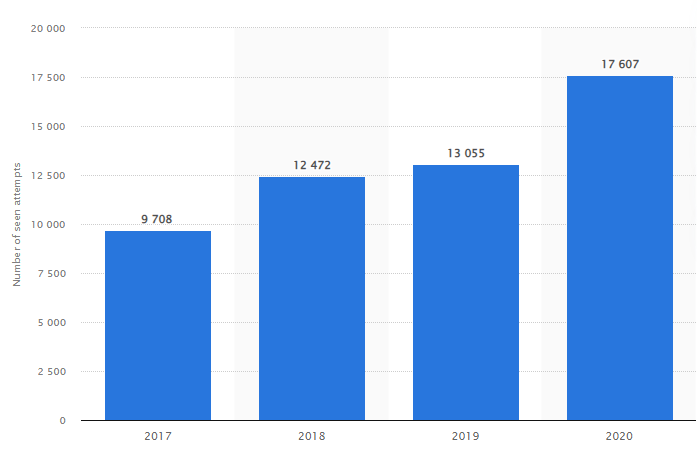
According to FBI IC3, there were 19,369 BEC attacks in 2019 that incurred a financial loss of $1.8 billion.
BEC attacks are carried out mainly through email spoofing. The impact of BEC attacks is enormous because they not only cause data breaches but also disrupt the reputation of the company.
3. Malware Attacks through Spam
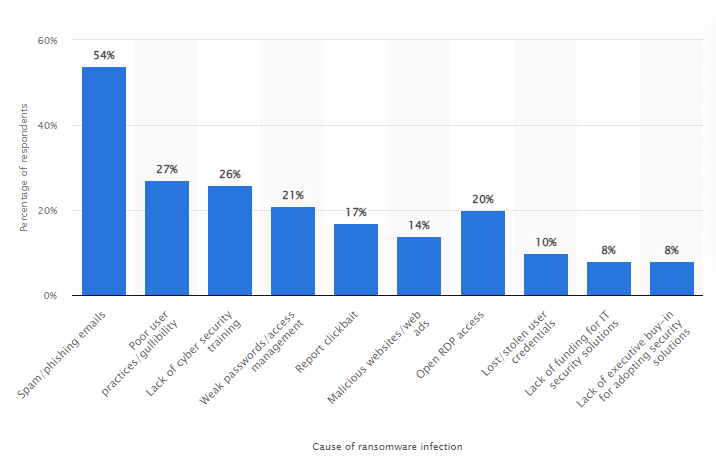
Many cybercriminals attempt to send malware through emails, either as an attachment or through a link to a phishing website. Such malware leads to major cyber attacks such as ransomware attacks or data breaches.
According to Statista, there were 10.5 billion and 9.9 billion malware attacks in 2018 and 2019, respectively.
According to an article by Information Age, the Information Commissioner’s Office (ICO) suffered a steep rise of 2650% in email attacks in 2021. This increase occurred over the course of a year (from January to December), during which phishing emails increased by 20% and malware increased by 423%.
4. Authentication Attacks
Authentication attacks are the types of cyber attacks that are carried out by using a predictive method of guessing a target’s credentials or card details. There are some specific types of authentication attacks such as brute force attacks, insufficient authentication (hackers getting access to websites containing confidential information that lacks enough security), and weak password recovery validation.
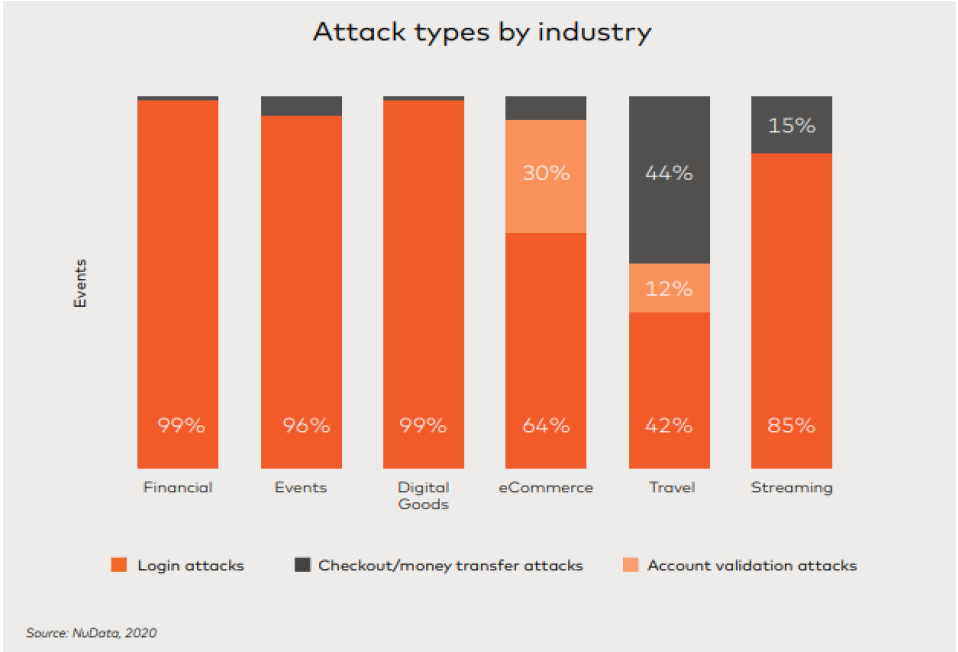
According to NuData, 99% of authentication attacks in the financial sector were carried out through login attacks, and 39% of authentication attacks in the e-commerce sector were carried out through account validation attacks.
In a recent attack on Solarwind Corporation, threat actors carried out breaches of private networks through authentication attacks. Cybercriminals found a loophole in Microsoft source code, which led to a breach of 18,000 networks.
Read more about Nobelium: Russian Hacking Group That Attacked SolarWinds
5. Email Server Vulnerability
Every system has some vulnerabilities. It is only a matter of time before cybercriminals identify them. Threat actors have been known to use some common exploitable weaknesses of email servers like weak authentication protocols, data leakage, outdated plugins, etc.
Email Security Policies for Organizations
Every organization must create a set of policies to protect its mail service. These policies are documented and implemented to ensure secure email service and usage within the organization.
Use a Highly Trusted Email Service Provider
Every organization should employ email services that are known for their security. Some of the popular email services are Gmail and Outlook. The purpose of using a trusted service is to make sure that it provides all the security tools and services such as phishing filters, multi-factor authentication, etc.
Multi-factor Authentication
All organizations must make it mandatory for every employee to enable multi-factor authentication on their email accounts. MFA allows you to add an extra layer of security to your email account like a fingerprint or an OTP in addition to the password.
Implement Spam Filters
Most email service providers have in-built features to filter out certain emails such as categorizing all the promotional emails in one section. But some service providers are better than others at filtering out spam emails using artificial intelligence. They use whitelisting tactics and sometimes they provide additional antivirus to facilitate additional security.
Treat External Emails Differently
Some email service providers formulate a policy that treats all external communication with special emphasis or marks. Thus, it gives employees a first-hand indication of treating the particular email with caution.
Awareness of Phishing Mail
Every employee must be trained to identify phishing emails or links to phishing websites. The employees should know what a phishing email looks like and how to differentiate between real offers and fake offers.
Email Security Gateway
A secure email gateway is a comprehensive framework of technology that provides robust protection against email-based attacks. It can be comprehended as a firewall of emails. The purpose of a secure email gateway is to scan inbound and outbound emails to check whether or not they contain suspicious or malicious content.
A secure email gateway provides four prime features- spam filtering, malicious content identification, malware blocking, and email archiving. Each of these features defines a definite segment of email security and enhances it. An email security gateway is regarded as one of the best protection against malicious emails and attachments.
Threat Scanning Email Attachments
Organizations should employ some tools or additional features that scan all email attachments before downloading. These tools can be anti-malware or antivirus software that scans the emails regularly, especially during the download of the attachments.
Email Security: Best Practices for Employees
Email security is a pressing concern for both employees as well as organizations as well. Below are some practices that should be followed by every employee to ensure email security.
1. Strong Password
One must choose a strong password for their email accounts. There are some key practices to keep your password safe from hackers that every employee must follow.
2. Monitoring Your Habits
It’s a simple yet effective practice to keep track of what you are doing with your email accounts or where you are sharing the details. For example, subscribing to newsletters, sharing email addresses on public forums, reviewing sent or received emails from time to time, etc.
3. Avoiding Public Wi-Fi
One must avoid using email services or opening email accounts while being connected to a public Wi-Fi. Public Wi-Fi is considered one of the most insecure communication methods. Piggybacking attacks are directly and easily carried out through public Wi-Fi.
4. Careful About Links and Attachments
There should be a set guideline that educates employees about ways to identify links that can be suspicious. These employee-centric guidelines should be implemented in the form of a policy of employee awareness. Along with that, the organization should employ a policy that prevents or warns users of suspicious links or attachments. They should double-check with the sender before downloading the attachments and scan the email for suspicious links.
5. Changing Password Frequently
An employee should change their passwords regularly. They can choose the frequency according to their convenience. But, one must be in the habit of changing passwords on email accounts after a certain period.
6. Cautious About Devices
Everyone must be careful about the devices they use. An employee should not log in to their email account on an unknown or unsolicited device. They should avoid logging into business email on personal devices.
7. Secure Email Address
Many times employees mention their work email addresses at unofficial places such as social media, or public forums. So, a policy should be incorporated for all the employees to prohibit them from posting their email addresses on public or social platforms. Thus, employees should only contact vendors, suppliers, business partners, or business associates with their official email addresses.
8. Employ DMARC
Every organization must employ DMARC policies to secure its email domain. The DMARC policies are custom settings that allow the domain owners to identify and treat spoofed emails differently.
Best Practices for Email Attachment
Emails are a major form of business communication and also essential for inter-employee communication within an organization. There may be exchanges of files and attachments. In such cases, some practices must be followed while sending or receiving attachments in emails. They are:
- An employee should avoid sending large attachments in emails. They should also avoid downloading large files or multiples files unless specifically stated during personal communication with the sender.
- While sending a large number of files, an employee should compress them into a ‘zip’ to make sure that the receiver’s size quota is optimally used.
- While sharing documents and files, an employee should save them on a drive and share the access link with the receiver.
- While sharing sensitive or private files, an employee can choose to protect them with a password or encryption and share them with the receiver.
- An employee should mention certain things in the email regarding the attachment, such as the contents and the purpose.
Secure Emails Result in Safe Organizations
Every organization must give the utmost attention to their email domain and mail server security as it is often the first point of attack. Email security is the prime subject of an organization’s cybersecurity. That’s why organizations need to focus on securing emails as a prioritized activity.
Employees are the heart of the organization and at the same time, they are its biggest vulnerability. That’s why employees’ phishing awareness training is essential to educate employees by carrying out simulated phishing campaigns. This will transform the employees into a strong line of defense against social engineering attacks.
TDMARC is the most effective solution for the implementation of email authentication standards. It allows organizations to set security protocols and measures to prevent the domain of organization from any kind of cyber attacks.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
