What is WhatsApp Phishing?
Needless to say, WhatsApp is a very popular and widely used social media platform among users. With over 2 billion people worldwide using and trusting the platform, cybercriminals highly target WhatsApp to commit theft, just like email.
Table of Contents
ToggleNearly 8% of social media cyberattacks are through phishing.
The reason cybercriminals prefer WhatsApp is its wide usage and ease of finding data. Scammers can effortlessly find billions of phone numbers with other personal information and create fake identities, resulting in tricking other people into specific scams. They often pretend to be someone from family, friends, gifts, lottery winners, etc.
Spam messages on WhatsApp cost a fortune to companies, not only the public and individuals but also companies if they are successful. They often get the organization’s login details, leading to substantial financial loss and brand image damage in the market.
Book a Free Demo Call with Our People Security Expert
Enter your details
What is WhatsApp Phishing Simulation?
WhatsApp phishing simulation is a proactive measure in cybersecurity that focuses on replicating highly realistic scam scenarios involving text-based attacks on the WhatsApp platform. With the simulation, organizations can check their vulnerability to such spam messages on WhatsApp and increase WhatsApp phishing awareness.
To generate a successful WhatsApp phishing simulation, it’s critical to explore common phishing tactics on the platform.
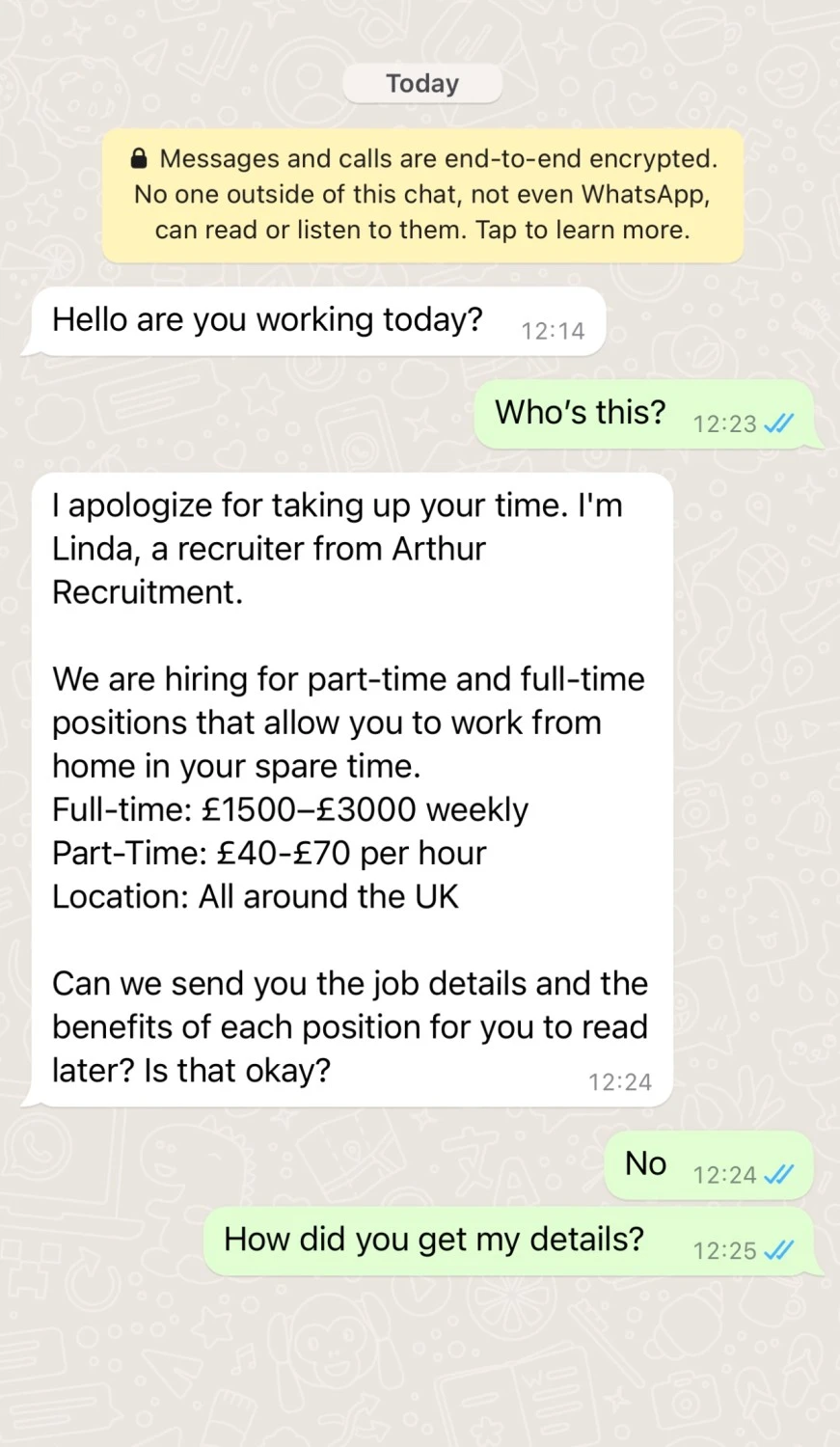
1. Imitation
Attackers often pretend to be from an authentic source, like a bank or institute, to make users trust them and share confidential information. By mimicking the source, they often ask users to change their passwords, click on a link, share other information, etc.
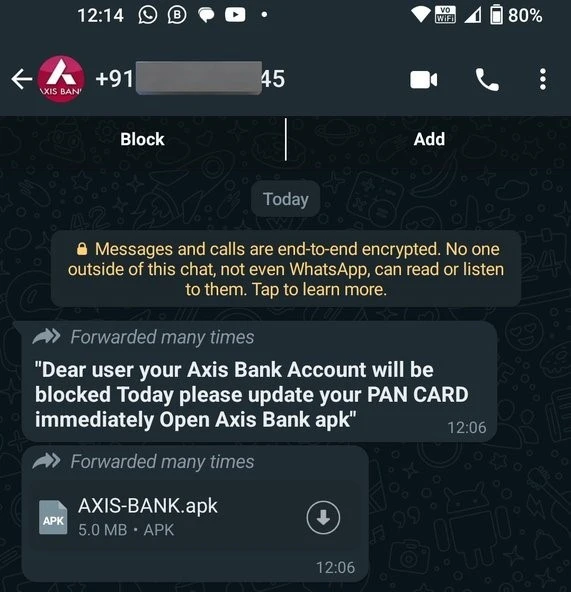
2. Infected Attachment
Cybercriminals often share WhatsApp scam messages to random numbers with faulty attachments of a group, inviting you to join. If clicked, the attacker gets access to your device, and the critical information is stolen from there.
The messages with the attachments are big clickbait like gifts, job offers, and so on.
Related: How PDFs Can Deliver Malware and How to Stay Safe
3. Wrong Numbers & Missed Calls
By giving a missed call, attackers send messages posing as a known person or expressing an urgent matter. They often keep you busy on a phone call, asking about whereabouts and making them curious. While building the situation, they ask for code and personal details, hoping they will share them unknowingly without giving the situation a second thought.
Process of Conducting Whatsapp Phishing Simulation?
The main aim of the simulation is to notice how many employees fall for scams and click on malicious links. With the results, organizations can develop training programs for employees who seek help in this area.
Here’s a detailed process that an organization can follow to conduct a WhatsApp Phishing Simulation on their employees.
Step 1: Select a Simulation Provider
There is a wide range of platforms that provide services for such simulations. Based on your goal and requirements, select a simulation provider that matches your needs.
Threatcop’s WhatsApp Phishing Simulation and Awareness Training is your best bet to reduce your company’s risk by 10% within only six months of duration.
Step 2: Customize the Simulation
Once the selection decision is made, it’s time to design and customize the campaign. Each organization is different, and therefore, employees are prone to fall for different modes of scams. Based on your company’s nature of work, design the fake messages and links to test the employees better.
Step 3: Analyze the Results
Once the simulation is done, it’s time to review and analyze the results. All the trends and patterns of employees in the campaign must be tracked to understand the level of vulnerability in the organization.
Step 4: Plan the Training Schedule
Once you’re sorted with the list of employees who need training, it’s time to plan for follow-up training to address the problem; for better results, take the aid of professional learning systems like TLMS – Threatcop Learning Management System.
With fun and engaging awareness content like cyber-comics, posters, and graphs, TLMS makes the training part fun and exciting for the employees to spread as much awareness as possible.
Preventive Steps Against WhatsApp Scam Messages
Employees and the general public can safeguard their data from such crimes with little patience and presence of mind.
- In case you receive messages with panic and urgent situations, make sure to call to confirm before sharing any information or transferring the amount.
- In case of doubt about suspicious activity, make sure to report the WhatsApp scam numbers so that other people don’t get scammed.
- Do confirm your two-factor authentication is switched on. No other user can log in to your account without a verification code sent to your phone number. This adds a security layer to your account, and no WhatsApp scam numbers can take over your data.

Security Awareness Training
78% of employees are aware of the risks of suspicious links in emails but click on them anyway.
This shows how crucial it is to prevent your employees from falling for phishing, Vishing, ransomware, WhatsApp phishing, and more such cyber threats. Employing Threatcop Security Awareness Training (TSAT) can aid in training your team members with the right skills. With the correct form of content, TSAT and WhatsApp phishing awareness provide information on the rest of the cyber threats. Chief information security officers now get the best tool for performing simulations and improving company security awareness.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
