Email is one of the forms of online communication which is used due to its relevance and reliability. With evolving technology, email has become the most popular point of attack for hackers and cybercriminals. Hackers are using phishing, spam and spoofing techniques to infect your emails and misuse them for online fraud and data breaches. To increase email security there is a need to apply various security and filtering solutions to reduce the chances of unwanted mail and prevent phishing emails. To stop attacks like email phishing and spam, there is a need to properly understand how they work and apply prevention strategies to reduce the chances of cyber threats. Let’s understand working and prevention strategies for Phishing and Spam.
Table of Contents
ToggleUnderstanding Phishing and Spam
Cybercriminals are using baiting strategies to convince users to download malicious files and open suspicious links or attachments in the mail which can request access to private data and infect your devices. To stop the misuse of private data there is a need to recognize phishing attacks and report them to stop their widespread and maintain confidentiality. Recognizing is an important step for identifying suspicious links and avoiding clicking on fake email IDs. People should resist clicking on untrusted links or attachments and report phishing attempts using the mail as a “report spam” feature.
An Example of Phishing Email
Dear User,
Your account has been compromised. Please click here to verify your identity: [maliciouslink.com]
Spam emails are irrelevant emails which are sent with the motive of advertising and promotions. It can be used for phishing and malware attacks by hackers. These emails are sent in the form of bulk emails. Hackers can also use spam emails to gain unauthorized access to your devices. To block spam emails, we need to see the security and filtering techniques in the type of email which is being used. Different email providers like- Gmail, Yahoo, Outlook, etc., have common techniques like “unsubscribe” to prevent unwanted adware and promotional emails. You can also implement techniques like “blocking” and “reporting” to stop spam emails.
An Example of Spam Email
‘’Congratulations! You’ve been selected for a FREE iPhone 16″. Click on the link to claim now:
[spamlink.com]
Let’s discover various techniques which will help to prevent phishing emails and spams.
Book a Free Demo Call with Our People Security Expert
Enter your details
Techniques to Prevent Phishing and Spam Emails
1. Unsubscribing to spam and promotional emails
- In your Gmail search bar, type “unsubscribe” to get the list of spam and promotional emails to which you have subscribed.
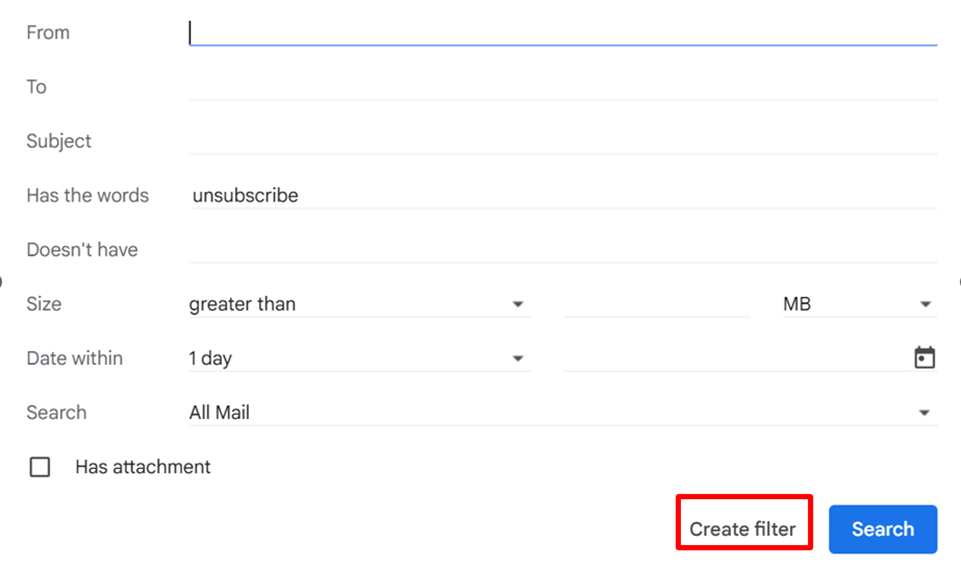
- Now, click on “Show search options” and click on the “Create filter” option to get various options.
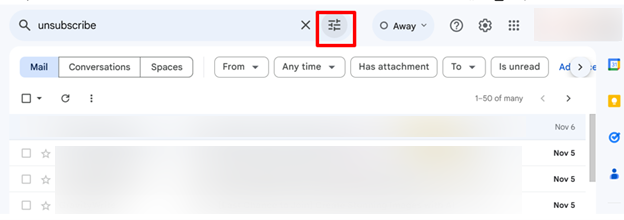
- In the various filter options, select the “archive it” option.
Note
- Exclude bank-related emails by entering the name of the bank.
2. Identification of spoofed emails
- There is a need to identify the spoofed emails which appear to be legitimate but intended to scam people.
- These spoofed emails can be identified by seeing misspellings or unusual domains.
An Example of spoofed email.
From:
[email protected] (Spoofed – Actual domain might be something like “[email protected]”)
To:
Subject:
[Urgent] Actoin Required: Confirm Your Filpkart Order for ₹17,000 Gift Voucher.
3. Reporting Spam and Phishing Attempts
- Select the mail which you find suspicious and click on more options to report it as spam or phishing.
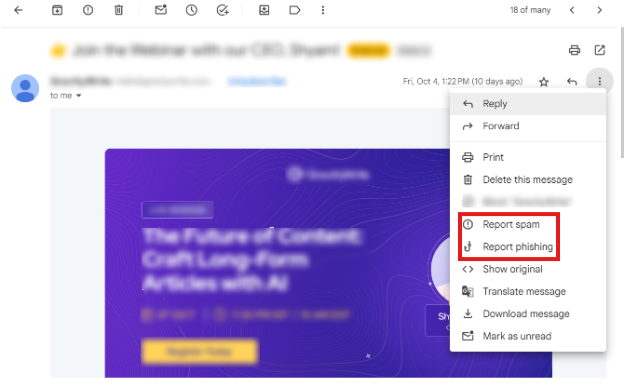
- By using Threatcop’s TPIR (Threatcop Phishing Incident Response) solution, it will help organizations in making email threat checking process convenient .
- With the help of TPIR, detection and reporting of suspicious emails becomes easier resulting in reducing modern cyberthreats.
4. Employees Awareness Training
- Organizations need to train employees to deal with spam and phishing attempts.
- Run dummy simulations to highlight various email threats.
5. Enforcing Email Authentication Solutions
- For an all-in-one email authentication security solution – DMARC, SPF and DKIM can be enforced for better security.
6. Use of Strong Passwords
- To enhance email security there is a need to use strong passwords and change them frequently.
- Don’t use common and weak passwords, it might become the cause of email security breaches.
7. Using 2FA or MFA
- Using an added layer of security for login and verification is an essential step which can help to prevent unauthorized access.
- 2-Factor Authentication or Multi Factor Authentication can help to verify the legitimacy of the person trying to gain access to the email-related details.
- This process helps to reduce the chances of data breaches.
8. Beware of Suspicious Email Attachments
- There is a need to pay proper attention to email attachments and verify the senders as these attachments may be malware or other forms of computer virus.
- Look for file extensions to verify the type of email attachments.
- For example – File ending with .exe,.src, and .bat extensions are the form of programs or code that can be used to harm the computer. Some other extensions to be varied include file extensions such as .xls,.zip,.wsh,.com, and .js.
9. Avoid Clicking or Replying to Spam Emails
- If you receive any spam email, avoid interacting with it. It’s advisable to simply delete or mark spam through your email client interface.
10. Use of Encryption and Decryption Methodology
- To ensure only authorized people can access and read the mail content, encryption and decryption methodologies are implemented for secure mail communications.
- In this methodology, content is converted into unreadable formats and uses encryption and decryption processes for sending and receiving purposes securely.
Book a Free Demo Call with Our People Security Expert
Enter your details
Conclusion
Email Protection has become an important aspect of digital platforms to stay safe from spam, spoofing, and phishing attacks. Important filtering, security settings, and email authentication solutions need to be implemented to enhance the overall security of email. By using important security techniques and training the employees it will help organizations to safeguard sensitive data and maintain trust in email communication. By using these modern techniques, it helps to be future-ready and establish a culture of safe and secure email communication.

Technical Content Writer at Threatcop
Milind Udbhav is a cybersecurity researcher and technology enthusiast. As a Technical Content Writer at Threatcop, he uses his research experience to create informative content which helps audience to understand core concepts easily.
Technical Content Writer at Threatcop Milind Udbhav is a cybersecurity researcher and technology enthusiast. As a Technical Content Writer at Threatcop, he uses his research experience to create informative content which helps audience to understand core concepts easily.
