Microsoft has been a top impersonated brand for hackers in 2022. The company has been impersonated in phishing attacks more than any other brand, with phishers creating over 11,000 unique phishing URLs in the first half of 2022. This trend is likely to continue, as Microsoft remains a popular target for phishers. In the most recent attack, a Russian government-linked hacking group targeted dozens of global organizations with a campaign to steal login credentials. Microsoft Threat Intelligence (MTI) said that the hacker known as Midnight Blizzard (previously tracked as NOBELIUM) is engaging users in Microsoft Teams chats pretending to be from technical support.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
The attacks were highly targeted and affected fewer than 40 unique organizations. However, they highlight the ongoing threat posed by Microsoft impersonation attacks since at least late May 2023. The threat actor has targeted the government, non-government organizations (NGOs), IT services, technology, discrete manufacturing, and media sectors. The attacks are highly targeted, meaning that they are only being sent to a small number of organizations. This makes them more difficult to detect and defend against. The attackers are using a variety of social engineering techniques to trick users into providing their credentials, including sending fake emails and creating fake Microsoft Teams chats.
Read More: How has Microsoft Impersonation Become a Major Concern for CISOs?
How did Midnight Blizzard plan the Microsoft Teams phishing attack?
Midnight Blizzard is a cybercriminal group that often uses different methods to gain unauthorized access to their target’s systems. These methods include stealing authentication tokens and tricking users with spear-phishing emails to reveal their login credentials. Microsoft researchers have noticed that since late May 2023, Midnight Blizzard has been particularly focused on credential attacks or token theft, where they try to obtain and abuse login credentials. It was claimed by the tech giant that these attacks are part of the overall campaigns carried out by the threat actor.
According to Microsoft’s January financial statement, Teams is their proprietary business communication platform, and it boasts over 280 million active users. MFA is a commonly recommended security measure to safeguard against credential hacking and theft. However, the fact that hackers are targeting Teams indicates that they are discovering ways to bypass this security measure.
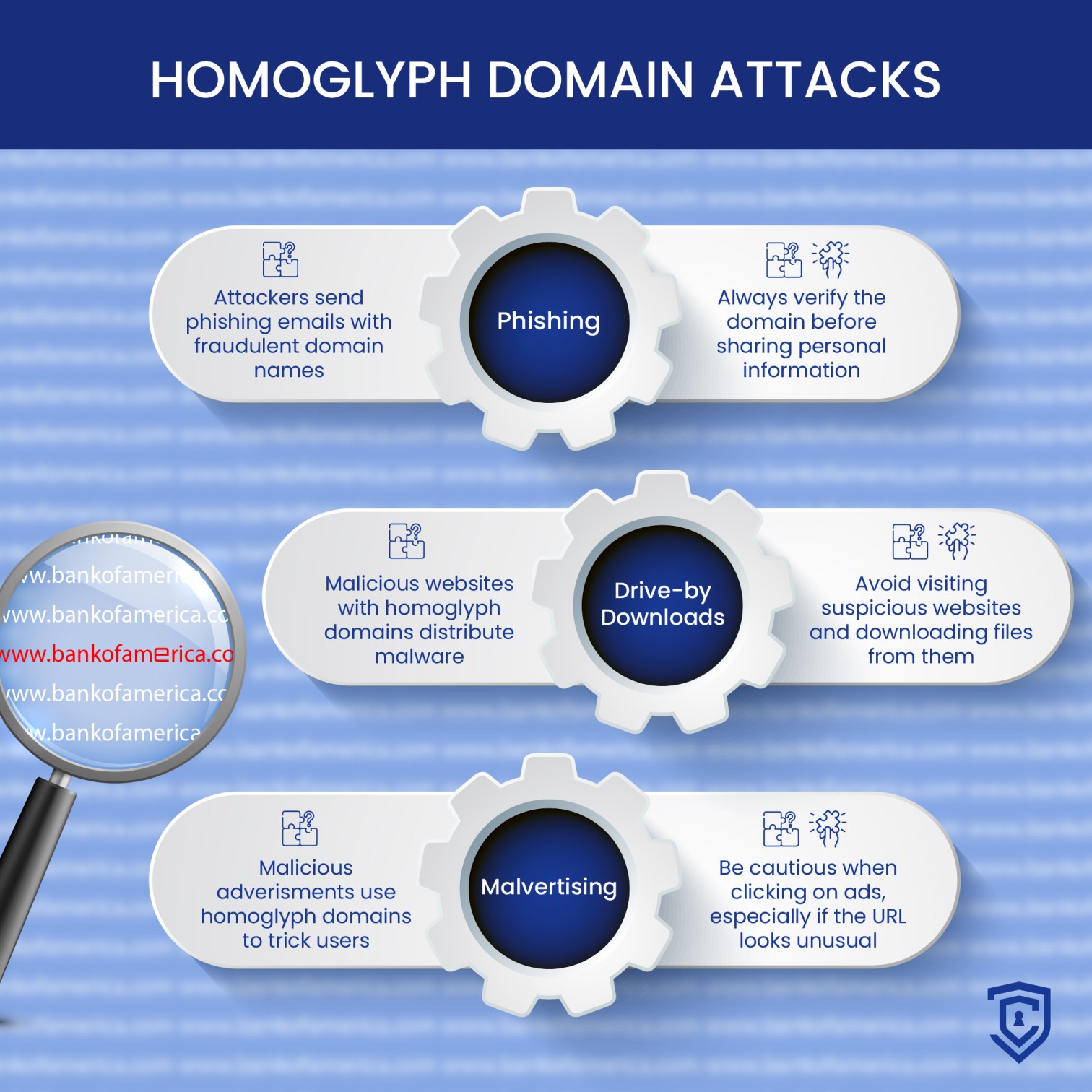
Phishing Attacks Using Security-Themed Domain Names
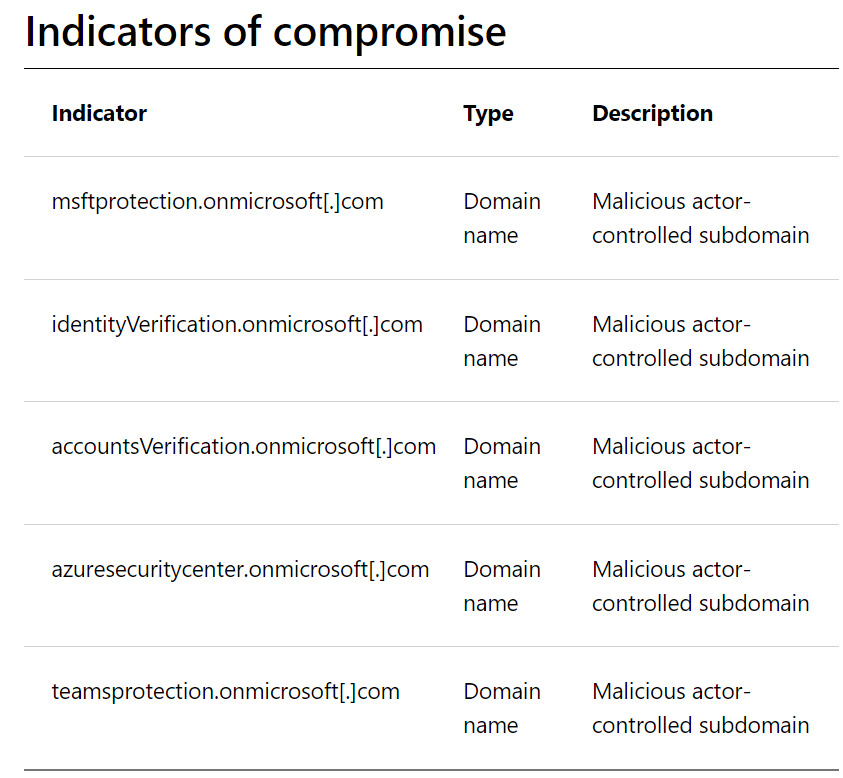
The threat actor has been using previously compromised Microsoft 365 tenants owned by small businesses to create new domains that appear as technical support entities. They use these domains to send Teams messages to targeted organizations in an attempt to steal credentials. The attackers send messages, asking the user to approve multi-factor authentication (MFA) prompts. When the user approves the MFA prompt, the attackers gain access to the user’s account.
The actor leverages previously compromised Microsoft 365 tenants to launch social engineering attacks. They rename the compromised tenant, create a new onmicrosoft.com subdomain with security-themed keywords, and add a new user associated with that domain to send the outbound message. The ongoing investigation by Microsoft includes looking into the initial attacks on genuine Azure tenants and the use of homoglyph domain names in social engineering tricks.
Social Engineering Attack Chain by Midnight Blizzard
During this tactic, Midnight Blizzard gains access to valid account credentials of their targeted users or focuses on users with passwordless authentication. Where a code is displayed during the login process and needs to be entered in the Microsoft Authenticator app on their mobile device.
Once they attempt to log in to an account with this form of MFA, the threat actor is shown a code that the user should enter in their authenticator app. At the same time, the user receives a prompt on their mobile device to input the code. Taking advantage of this situation, the attacker contacts the targeted user through Microsoft Teams, persuading them to enter the code into the prompt on their device. Let us understand the steps in brief:
Step 1: Contacting through Teams Chat
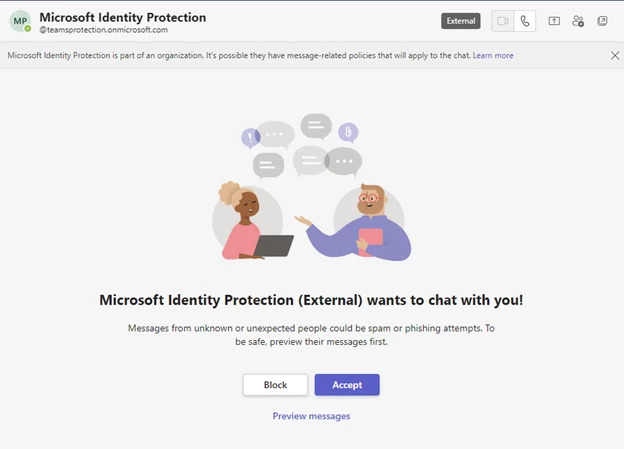
The target user might receive a message request on Microsoft Teams, seemingly from an external user posing as a technical support or security team.
Step 2: Request for Authentication App Action
Once the targeted user accepts the message request, they receive a message through Microsoft Teams from the attacker. The message aims to persuade the user to enter a code into the Microsoft Authenticator app on their mobile device.
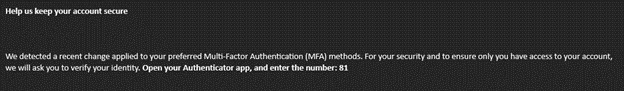
Step 3: Successful MFA authentication
If the targeted user falls for the message request and enters the code into the Microsoft Authenticator app, the cybercriminal gains a token to impersonate the user. This grants the attacker access to the user’s Microsoft 365 account, completing the authentication process.
With unauthorized access, the attacker then engages in post-compromise activities, typically involving stealing information from the compromised Microsoft 365 account. In some instances, the attacker may try to add a device to the organization as a managed device through Microsoft Entra ID (formerly Azure Active Directory). This move is likely an attempt to bypass conditional access policies that restrict access to specific resources only to managed devices.
What do we know about Midnight Blizzard?
- Midnight Blizzard (NOBELIUM) is a threat actor based in Russia, specifically attributed by the US and UK governments as the Foreign Intelligence Service of the Russian Federation (SVR).
- They have a well-established history of targeting governments, diplomatic entities, non-government organizations (NGOs), and IT service providers primarily in the US and Europe.
- Since early 2018, their main objective has been to collect intelligence through dedicated espionage of foreign interests.
- Midnight Blizzard employs diverse methods to gain initial access, including stolen credentials, supply chain attacks, and exploiting on-premises environments to move to the cloud.
- They also take advantage of trust chains within service providers to access downstream customers and use AD FS malware such as FOGGYWEB and MAGICWEB.
- The threat actor is persistent and consistent in their operational targeting, and their objectives rarely change.
- Security vendors track them under different names, such as APT29, UNC2452, and Cozy Bear.
Have Microsoft Teams mitigated the phishing attack?
Microsoft has claimed that they have mitigated the actor from using the domains and continues to investigate the matter further. It has recommended the following measures to reduce the risk of this threat:
- Pilot and deploy phishing-resistant authentication methods for users.
- Implement Conditional Access authentication strength to require phishing-resistant authentication for employees and external users accessing critical apps.
- Specify trusted Microsoft 365 organizations to define allowed or blocked external domains for chat and meet.
- Keep Microsoft 365 auditing enabled to investigate audit records if needed.
- Understand and select appropriate access settings for external collaboration in your organization.
- Allow only known devices adhering to Microsoft’s recommended security baselines.
- Educate Microsoft Teams users to verify ‘External’ tags on communication attempts from external entities, be cautious about sharing information, and never share account details or authorize sign-in requests via chat.
- Encourage users to review sign-in activity and report suspicious sign-in attempts as “This wasn’t me.”
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Organizations should also educate users about social engineering and phishing attacks, including avoiding entering MFA codes from unsolicited messages. The entire security posture of an organization can be considerably improved by informing and educating employees about the dangers of phishing campaigns and other social engineering techniques. Prioritizing people security management as a vital component of securing an organization’s digital infrastructure is crucial in the field of cybersecurity. Threatcop’s phishing awareness and simulation can be very helpful as employees can be vulnerable links because the success of a phishing attack totally relies on the unawareness and lack of vigil of an employee.
Book a Free Demo Call with Our People Security Expert
Enter your details
To fulfill the need for security awareness training, organizations can use tools like Threatcop Security Awareness Training (TSAT). This will help you to increase employees’ productivity due to reduced time spent handling security incidents and recovering from cyberattacks. Invest in tools that equip your employees with the knowledge and skills to identify and mitigate potential security risks, reducing the organization’s vulnerability to cyber threats.
Also read: Updates on Microsoft Outage 2024
FAQs: Microsoft Teams Phishing Attack
The threat actor behind the Microsoft Teams phishing attack is infamously known as Midnight Blizzard (previously tracked as NOBELIUM). They are a Russia-based cybercriminal group attributed to the Foreign Intelligence Service of the Russian Federation (SVR).
The main targets of the phishing attack were dozens of global organizations, including governments, non-government organizations (NGOs), IT services, technology companies, discrete manufacturing, and media sectors.
Midnight Blizzard used compromised Microsoft 365 tenants owned by small businesses to create new domains that appeared as technical support entities. They sent Teams messages to targeted organizations, pretending to be from technical support, and asked users to approve multifactor authentication (MFA) prompts. When the users approved the MFA prompt, the attackers gained access to their accounts.
Since early 2018, Midnight Blizzard has been consistently and persistently targeting governments, diplomatic entities, NGOs, and IT service providers primarily in the US and Europe. Their primary objective is to collect intelligence through espionage of foreign interests.
Organizations should implement security measures recommended by Microsoft, including using phishing-resistant authentication methods, educating users about phishing attacks, and reviewing sign-in activity regularly. Additionally, they can invest in security awareness training tools like Threatcop Security Awareness Training (TSAT) to equip employees with the knowledge and skills to identify and mitigate potential security risks.
Co-Founder & COO at Threatcop
Department: Operations and Marketing
Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop’s mission to safeguard people’s digital lives.
Co-Founder & COO at Threatcop Department: Operations and Marketing Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop's mission to safeguard people's digital lives.
