Saudi Arabia is the largest hub of information and communication technology in the whole Middle East and it is continuously evolving. Saudi Arabia is going through vigorous development at both an infrastructural and technological level. In this blog, we will explore how digitization has raised concerns for the country. We will discuss the cyber attacks in Saudi Arabia and how they can be prevented.
Table of Contents
ToggleAs a result of the rising threat, the National Cybersecurity Authority and the Education Ministry of Saudi Arabia signed an agreement to conduct joint training programs for cybersecurity.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Notable Cyber Attacks in Saudi Arabia
According to Arab News, Saudi Arabia became the target of 7 million cyber attacks in the first two months of 2021.
Saudi Aramco Paid $50 Million Ransom After Data Leak
Saudi Arabia’s oil-producing giant Aramco paid a ransom due to a data leak that took place in their organization. The data leak led to an extortion attempt where hackers demanded a $50 million ransom. Saudi Aramco is the world’s most valuable oil producer. The organization told the Associated Press that it discovered a limited amount of data leakage. This data was most likely held by third-party contractors of the company.
The same press reported earlier that threat actors had held onto 1 TB of Saudi Aramco’s data, which was available on the darknet. Later, Aramco decided to make a payment in the form of cryptocurrency to retrieve the data.

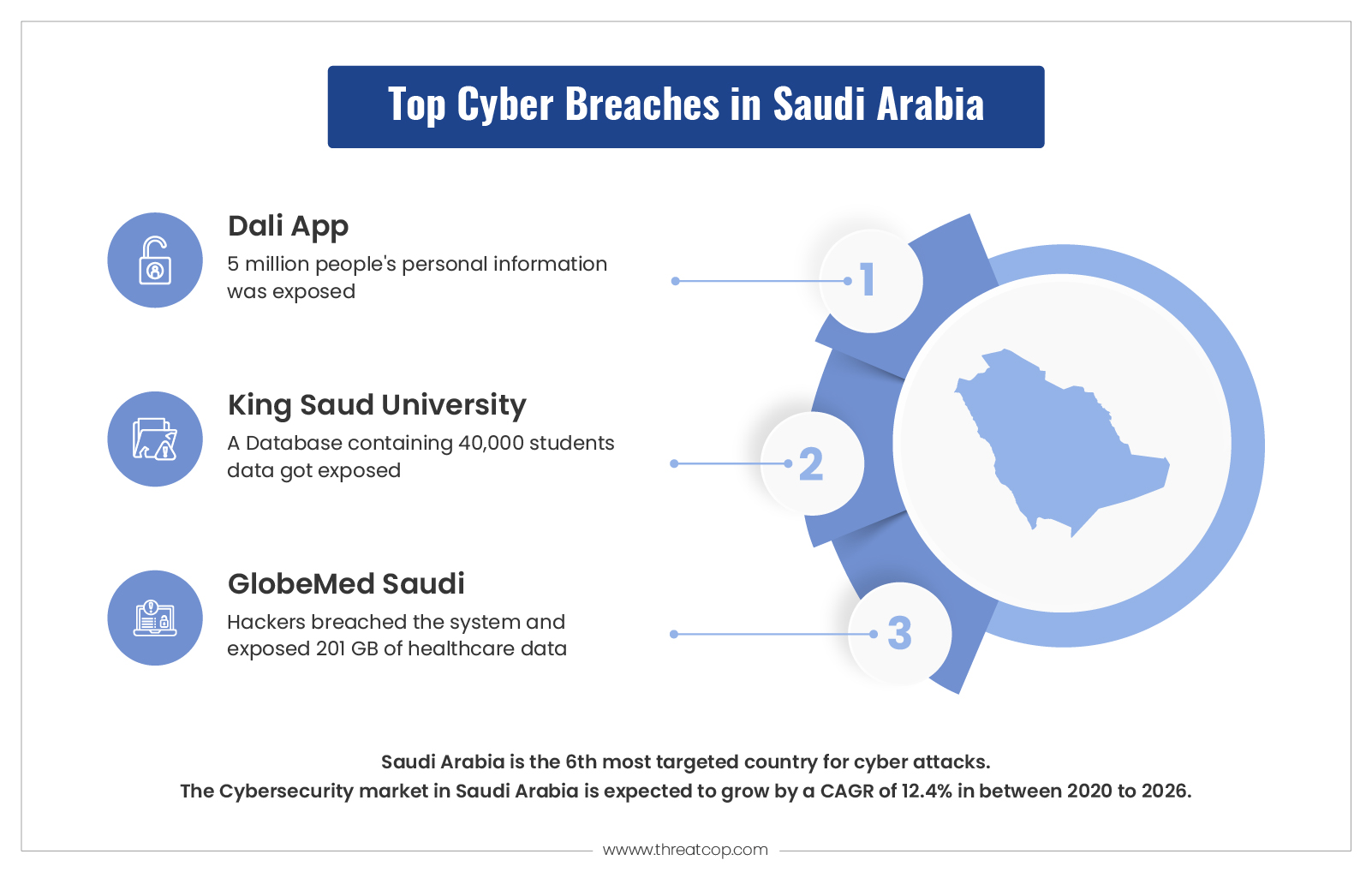
5 million User Data Exposed from Caller ID App Dali
Dali is a famous caller ID application in Saudi Arabia, which is used to find and identify contact numbers. The app is also used for reporting suspicious contact numbers. The application uses a MongoDB database that got misconfigured, leading the data of 5 million users to be publicly available. The total size of the exposed data was 585 GB.
Book a Free Demo Call with Our People Security Expert
Enter your details
King Saud University Database Was Hacked
King Saud is the first university in the country that is home to over 40,000 students and has several notable alumni. A hacker group named Yourikan hacked the database of the university and stole the user data of over 800 people. This data included names, phone numbers, email addresses, and passwords. The hacker later dumped the data but asked students to change their passwords.
Cybercrimes in Saudi Arabia
Cybercrimes in Saudi Arabia have been categorized into three groups.
- Group A includes crimes such as gaining illegal access to the victim’s computers through luring or blackmail. It also includes crimes like defaming a person on social media and breaching the privacy of individuals by either taking pictures or recording their voices over cell phones. A convicted cybercriminal is penalized with a maximum of SAR 500,000.
- Group B cyber crimes include hacking or illegal access to anyone’s social media account. The convicted criminal is charged with a maximum of SAR 3,000,000.
- Group C cybercrimes include storing and publishing anything that is not consistent with morality, religion, public order, or breaches someone’s privacy. It also includes crimes such as publishing pornography and promoting or facilitating narcotic or psychotropic substances. The penalty levied upon the cybercriminal can reach a maximum of SAR 3,000,000.
How to Report Cybercrime in Saudi Arabia?
The victims of cyber attacks can report the crime to the nearest police station. The station transfers the report to the Saudi Bureau of Investigation and Public Prosecution (BIPP) for further investigation. After the confirmation of the crime, the charge sheet is filed and the threat actor is produced in criminal court.
According to Business Wire, the cybersecurity market of Saudi Arabia in 2020 was valued at $3.6 billion, which is expected to grow by a CAGR of 17.98% up to $9.8 billion by 2026.
How Organizations Can Prevent Cyber Attacks in Saudi Arabia?
It is extremely important that organizations in Saudi Arabia seek smart ways to evade threats that compromise their information and operational security. It means they need to take a holistic approach to cybersecurity. A holistic approach would include security awareness, multi-layer protection, incident response tools, and outbound email security, among many others.
According to a news article by Arab News, more than 22.5 million Brute Force Attacks took place on Remote Desktop Protocols (RDPs) in the year 2020.
Cybersecurity Awareness
Traditional and modern methods can both be used to achieve cyber awareness among employees in an organization. Traditional methods consist of the usual cybersecurity workshops and lectures on cybersecurity best practices. But how effective are they? If people don’t experience the sequence of events taking place in a real-life cyber attack, how will they identify it?
That’s why the modern method involves choosing a cybersecurity awareness training solution for employees to impart comprehensive awareness and defense training to their employees. It uses modern methodologies of simulation and analysis for generating awareness and cybersecurity training.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication adds an extra layer of protection to accounts holding sensitive information. Therefore, even if the attacker gets hold of the account credentials, MFA makes sure that the threat actor can’t access the account by cross-verifying the login details with the legitimate owner of the account.
Phishing Incident Response Tools
Phishing incident response tools help employees immensely for quick detection and consequential elimination of cyber threats that manage to enter the organization’s environment through emails. Phishing Incident Response Tools (TPIR) can be used for detecting and removing phishing emails from the office environment after they are reported by a recipient.
Email Security
Email security is very important for both inbound and outbound email security. It incorporates a big part of the cybersecurity framework of the organization. However, the methods and tools used for securing both of them are different. Inbound email security can be ensured by using firewalls to block malicious traffic from entering the system’s environment. This may pose danger to the information and operations of the system.
Outbound email security is a whole different ball game. Email Authentication and Anti-Spoofing tools come in handy to ensure outbound email security. TDMARC is one such tool that helps organizations maintain their email legitimacy and increase their email deliverability and engagement rate.
Prevention of Cyber Attacks Should be The Long Term Goal
Cybersecurity leaders and IT professionals in the organization need to make sure that security policies and solutions are implemented in the organization. The majority of cyber attacks occur due to a lack of cybersecurity awareness, which could be the reason for the high number of successful attacks in Saudi Arabia.
It is a crucial time to consider investing in cybersecurity tools and solutions to stay protected against the different types of cyber attacks. Every CISO, CIO, CXO, and CEO must keep their organizational cybersecurity a priority.
Cybercriminals are relentlessly leveraging the uncertain situation to launch more sophisticated cyber attacks. They are coming up with new attempts to steal and compromise the data of organizations and put their brand reputation at stake. As cybersecurity and email security service providers, we strongly recommend you start implementing essential security measures in your organization.
To mark Cybersecurity Awareness Month, Threatcop collaborated with 31 respected CISOs and CTOs from prominent organizations. Together, we’re working towards a safer digital future.
Explore Here: 31 Cybersecurity Awareness Ideas from Security Leaders
Co-Founder & COO at Threatcop
Department: Operations and Marketing
Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop’s mission to safeguard people’s digital lives.
Co-Founder & COO at Threatcop Department: Operations and Marketing Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop's mission to safeguard people's digital lives.
