The whole world was highly affected by the pandemic, and one of the key elements that evolved during that time was digitization. As the world was forced to stay indoors, its dependence on technology increased exponentially. The increase in online shopping during the pandemic gave cybercriminals a perfect chance to come up with new ways to target and deceive people on the internet. In fact, the Economic Times reported that amidst the rising number of digital devices, there has been an increase in cyber attacks by 151%.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
The Middle Eastern countries were the most affected region. During the pandemic, Saudi Arabia and UAE witnessed a 168% and 230% rise in phishing attacks respectively. Recently, another hacker group has come to light, which has used similar tactics to target the Middle East population. One such threat operator, the PostalFurious gang, impersonated postal brands and toll operators in the UAE to carry out phishing campaigns. The hacker group used phishing texts and iMessages in the UAE, tricking victims into entering personal and payment data on fake payment pages.
The threat actor, first identified by Group-IB in April 2023, has been impersonating toll operators and postal brands to target customers in the Asia-Pacific region. Scam communications from numerous organizations, including government agencies and well-known brands like DHL, Central Bank, Salik, Emirates Post, and more have been making the rounds in the nation.
Tactics Behind the Sophisticated Smishing Campaign
Group IB can now vouch for the fact that the organization has expanded its reach into the Middle East. Local officials issued a warning about a scam campaign in which threat actors pretended to be road toll operators at the beginning of May 2023. The Digital Crime Resistance Centre of Group-IB in Dubai was able to link PostalFurious to this campaign and another recent fraud operation that pretended to be a postal service and targeted people in the Middle East. The cybersecurity group has also found that 270 domains are impersonating renowned postal service brands.
Book a Free Demo Call with Our People Security Expert
Enter your details
The phishing websites could only be accessed from IP addresses in the UAE and employed access-control measures to circumvent automatic detection. Based on shared infrastructure and code seen in earlier APAC activities, Group-IB connected these campaigns to PostalFurious. It is possible that skilled phishing actors were involved given the usage of Laravel as an administration panel and remarks in simplified Chinese in the phishing code.
Here is the Breakdown of the Smishing Attack in the UAE
- The hacker group pretended to be toll operators and postal companies asking target customers to make payment of a vehicle toll to avoid fines.
- To hide the actual phishing address, a shortened URL is used in the SMS phishing campaign.
- When a user opens the link, they are taken to a bogus payment page with a phoney brand name.
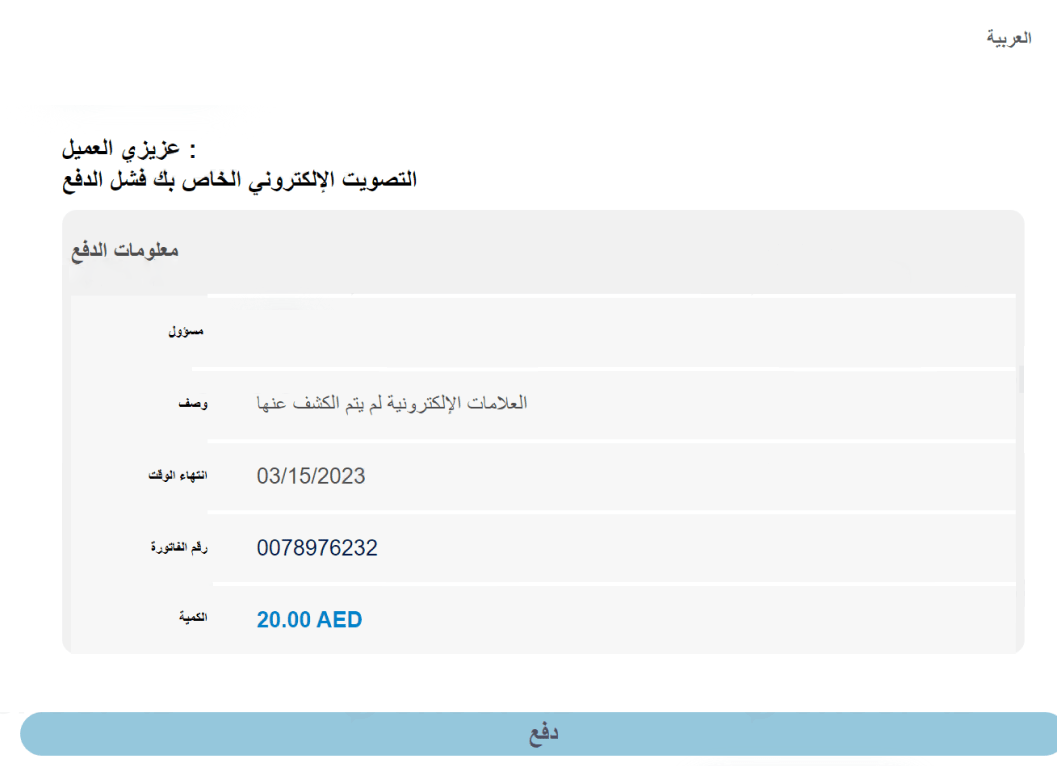
- Threat actors asked for personal information such as name, address, and card details.
- They used the official branding and logo of the impersonated postal services provider.
- The numbers from which messages were sent to many telecom company customers were registered in Thailand and Malaysia.
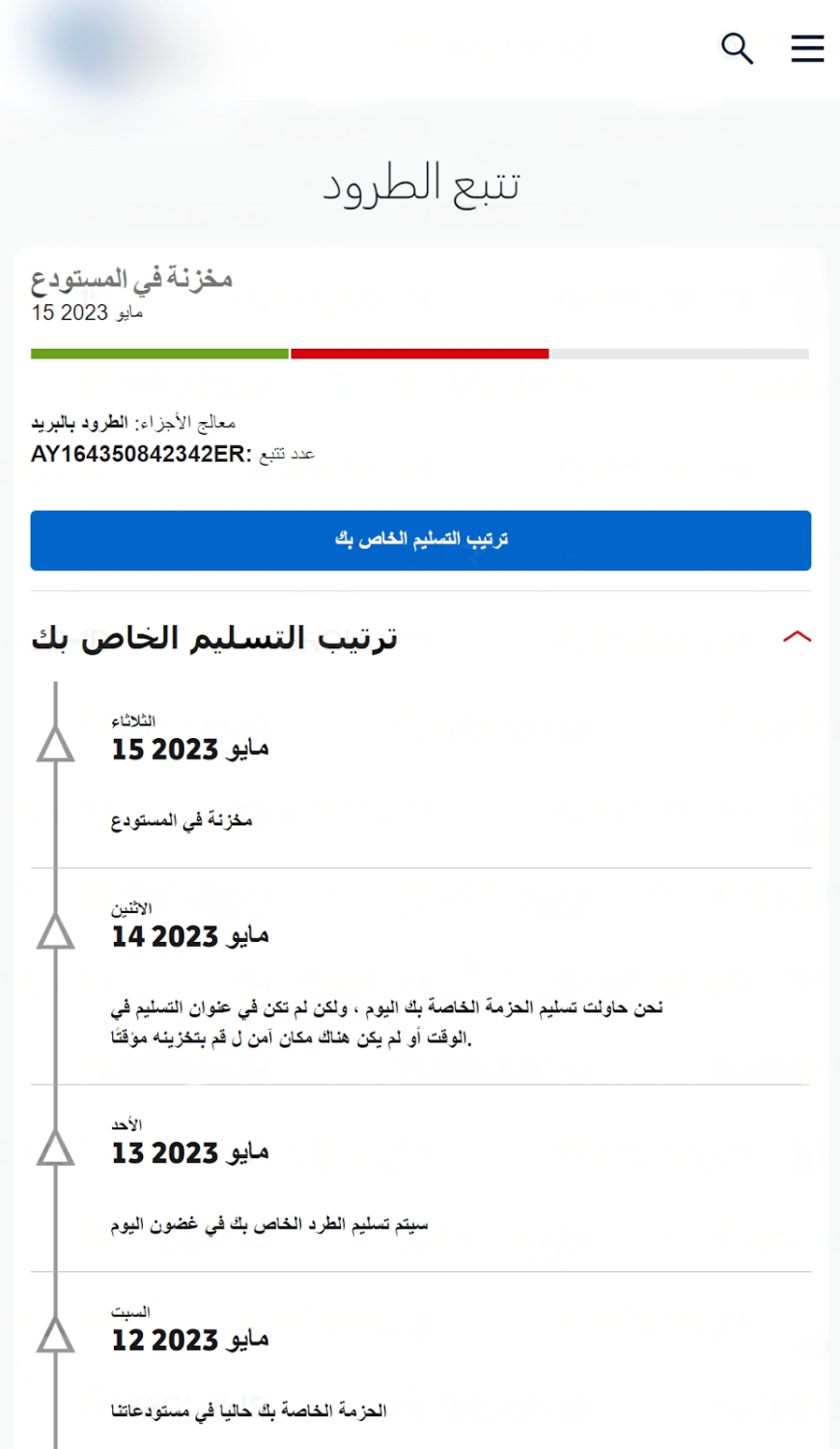
- The exact impact and scale of the attack is unknown but hackers also sent messages through email addresses via Apple iMessage.
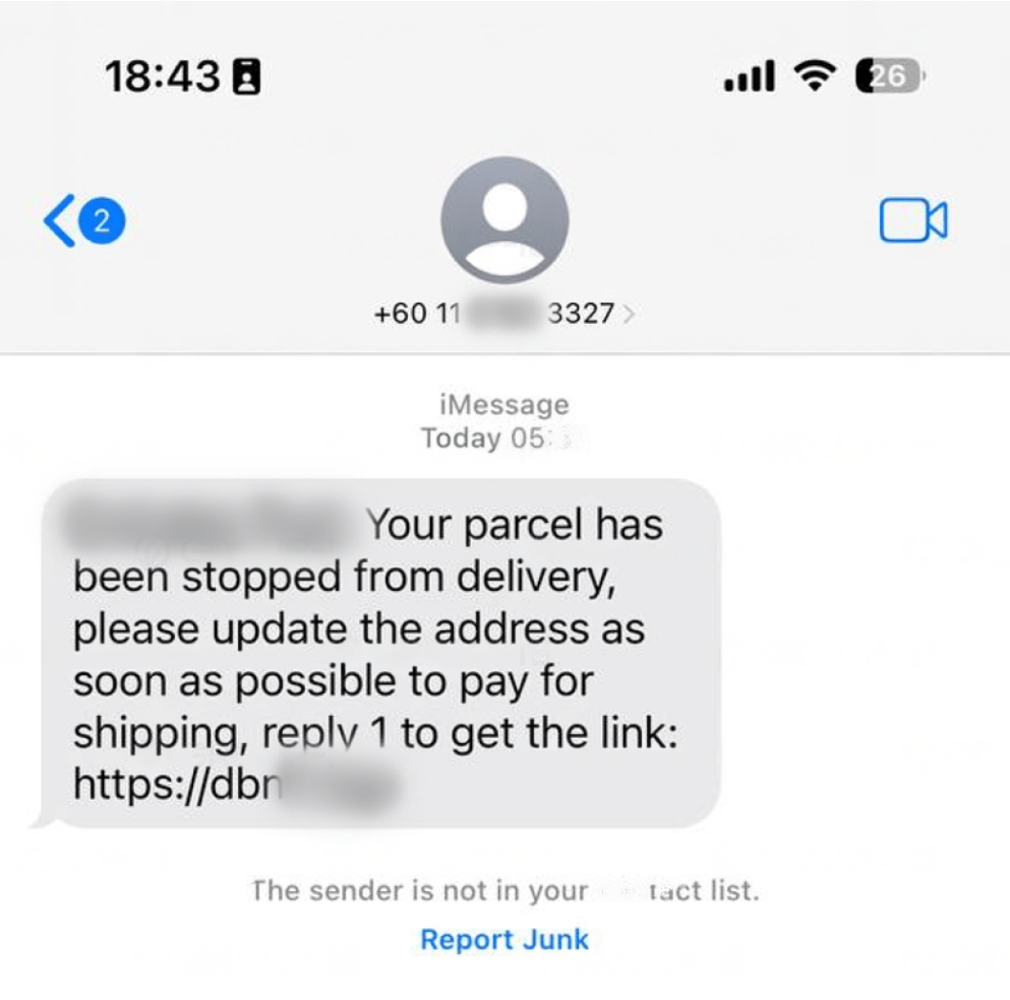
- To increase their reach, threat actors constantly register new phishing domains.
- Both phishing efforts used the same web servers to host their phishing resources and used the same layout for their fake payment pages.
- These campaigns’ architecture and code are similar to earlier PostalFurious campaigns in the Asia-Pacific area.
- Attacks on the Middle Eastern and Asia-Pacific markets use the Laravel administration panel.
- The phishing websites’ source code includes remarks written in simplified Chinese.
- The Group-IB did not disclose the name of the organizations who were impersonated by PostalFurious but Dubai’s road toll system operator Salik issued a warning on Twitter regarding the circulation of false messages.
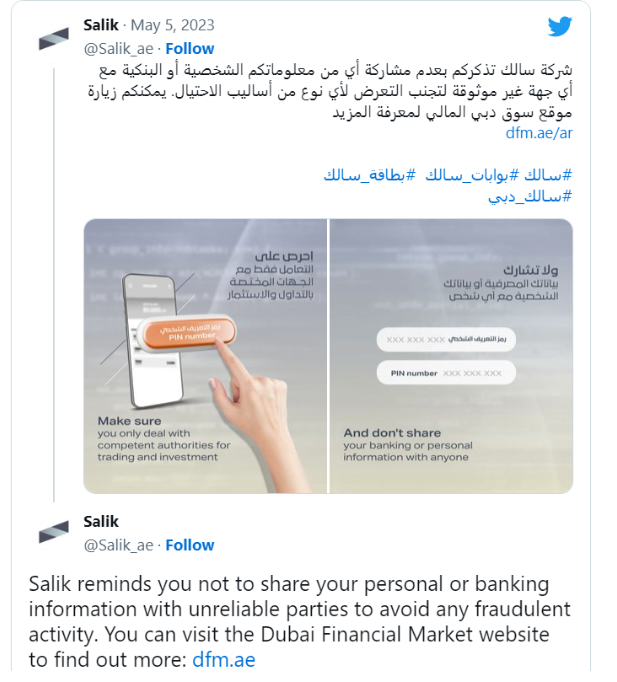
According to information provided by Group-IB, the fraud has been active at least since April 15, 2023, with the aim of compromising victims’ financial information. On April 29, the same scam was reintroduced, and the con artists used the same servers to host a new network of phishing websites. This time, Emirates Post was the impostor company. The Chinese-speaking community known as PostalFurious has purportedly existed since 2021. The gang’s choice to imitate postal brands and its ability to establish sizable network infrastructures that are often updated to prevent detection led to the naming of the organization.
Also Read: A Brief Guide to Types of Social Engineering Attacks

The bogus payment pages shared a similar layout to the Salik and Emirates Post scam schemes, which were both hosted on the same web servers. Both forgeries used the identical components and codes that the cybersecurity company had previously noted in their infrastructure.
Read More: Types and Techniques of Phishing Attacks & How to Identify
People Security Management Can Help Your Organization
Phishing continues to pose a significant threat to cybersecurity, and its effectiveness can largely be attributed to human error. Despite advancements in technology and security measures, cybercriminals consistently exploit the vulnerabilities of human behavior to carry out successful phishing attacks. They craft deceptive emails and messages that trick unsuspecting individuals into revealing sensitive information, such as login credentials, financial details, or personal data. We have read about such cases where the unawareness of employees has led to a major cyber breach.
Human error plays a crucial role in phishing attacks. Employees may unknowingly click on malicious links or download infected attachments, providing hackers with access to corporate networks. In other cases, individuals may fall victim to social engineering tactics, such as impersonation or urgency tactics, leading them to disclose confidential information or execute unauthorized transactions. These mistakes can have severe consequences, leading to data breaches, financial loss, reputational damage, and compromised network security.
You can also read: Top 5 Cyber Attacks and Security Breaches Due to Human Error
To combat phishing effectively, organizations need to prioritize People Security management. This involves educating and training employees on recognizing and responding to phishing attempts. To empower employees through the AAPE Model, we assess the weakest links, raise awareness, provide robust protection, and empower employees to defend against cyber threats. By making employees aware of the various techniques used by cybercriminals, individuals can become more vigilant and cautious when interacting with suspicious emails, messages, or websites.
No matter how many firewalls and security tools you put in place, some phishing emails will still find their way into your employees’ inboxes and that’s where the TPIR (Threatcop Phishing Incident Response) tool empowers your employees to identify and report suspicious emails with a click. TSAT (Threatcop Security Awareness and Training) helps in simulating five different kinds of cyber-attacks including phishing, vishing, smishing, and ransomware. An additional feature of this tool is that you can customize the campaign templates to launch highly realistic dummy cyber attacks for maximum impact.
These solutions provide employees with the knowledge, skills, and tools necessary to identify and report phishing attempts, thus strengthening the overall cybersecurity posture of the organization.
Read More: How the Middle East Can Defend Social Engineering Attacks
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
FAQs: PostalFurious Strikes in UAE
Smishing is a form of phishing that involves sending deceptive text messages or SMS (Short Message Service) to trick individuals into revealing sensitive information or performing certain actions.
In smishing attacks, cybercriminals send fraudulent text messages pretending to be legitimate entities, such as toll operators or postal services. They include links or instructions that lead recipients to fake websites, where they are prompted to enter personal and payment information.
PostalFurious is a threat group known for carrying out phishing campaigns by impersonating toll operators and postal brands. They have targeted customers in the UAE and Asia-Pacific region.
To protect against smishing attacks, individuals should be cautious of messages from unknown or untrusted senders, avoid clicking on suspicious links, never provide personal or financial information in response to unsolicited messages, and regularly update their devices with security patches. Phishing incident response tools like TPIR can help in the quick detection of malicious emails and their elimination from the inboxes of employees. It empowers employees to identify and report suspicious emails immediately.
People Security management focuses on educating and training individuals to be more aware of cybersecurity risks and to make informed security decisions. It aims to empower employees to defend against cyber threats by raising awareness and implementing robust security measures.
This solution follows the Assess, Aware, Protect, Empower (AAPE) model. They assess the weakest links in an organization’s security posture and raise awareness about phishing techniques and best practices through comprehensive training programs. And empower employees to defend against cyber threats by equipping them with the knowledge, skills, and tools necessary to identify and respond to phishing attempts.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
