In this rapidly evolving digital age, the hacker’s focus on exploiting the most vulnerable link in the security chain – humans – is becoming more pronounced. This emerging tactic is exemplified by a Chinese-linked hacker’s use of HTML Smuggling, a novel technique that recently targeted European government entities, revealing the cunning ways hackers navigate beyond conventional cybersecurity measures.
Table of Contents
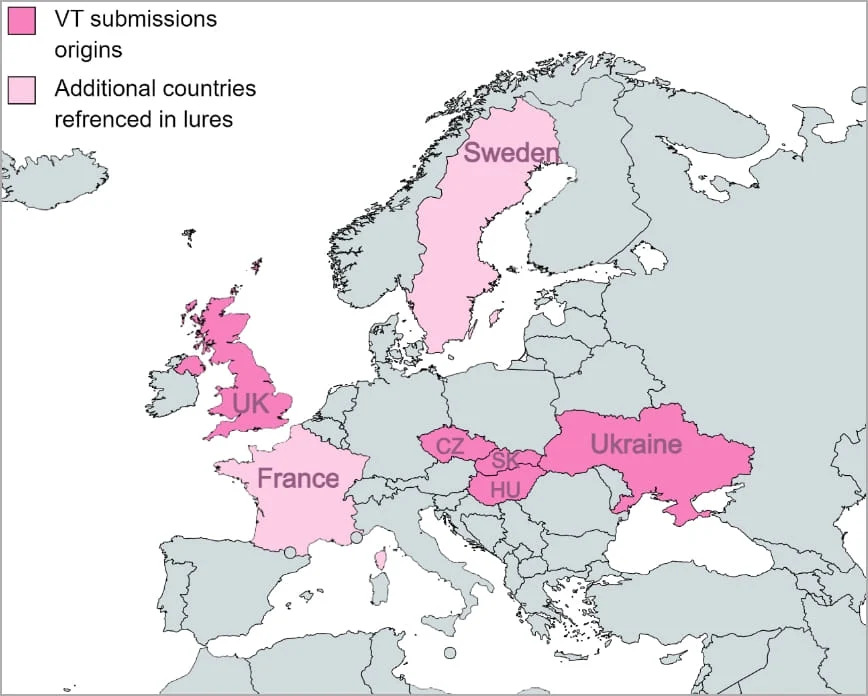
ToggleA Chinese-linked hacker has been targeting several government entities across Europe, employing HTML Smuggling since December 2022. A phishing campaign dubbed SmugX targeted foreign affairs ministries and embassies in France, Sweden, the UK, Ukraine, the Czech Republic, and Slovakia. It was surprising; to see attackers’ effectiveness in surpassing conventional security measures by exploiting web browser vulnerabilities. Though technology at the place could be highly useful it always possesses certain challenges, which hackers consistently seek to exploit.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
A recent news report by Bleeping Computers says that researchers at a top cybersecurity company examined the attacks and found similarities to activity previously linked to advanced persistent threat (APT) organizations such as Mustang Panda and RedDelta. Due to the unique attack mechanism used in the SMUGX campaign, it is regarded as quite hazardous for organizations’ data security.
What is SMUGX Phishing Campaign?
In SMUGX phishing campaigns, the users are targeted and lured to open phishing emails and download infected attachments. In those attachments, they hide malicious code within HTML files and this is known as the HTML smuggling technique. The objective of malicious HTML is to successfully evade network security systems and deceive web browsers into executing the code as if it were a legitimate part of the webpage. This method provides attackers with unauthorized access to sensitive data, enabling them to extract valuable information or take control of compromised systems.
You can Read Our Article on Phishing Attacks: Biggest Menace for Organizations Globally
Crucial Insights on SmugX Phishing Campaign from Research Report
- The news report by Bleeping Computers stated that Chinese hackers are employing innovative delivery methods, including HTML Smuggling, a new variant of PlugX. Chinese hackers are quite infamous for their usage of the PlugX technique to target users.
- While the malware payload has similarities to earlier versions of PlugX, the ongoing campaign’s unique delivery techniques have contributed to its ability to evade detection and operate covertly until recently.
- Following a complex infection chain involving either archives or MSI files, the attacks deploy PlugX. A powerful remote access Trojan (RAT), PlugX is also known as “Korplug” or “Sogu.” It has been connected to Chinese advanced persistent threat (APT) groups. It is a potent malware that gives attackers total control over affected systems. The attackers use the PlugX implant after the initial infection, which often happens through complex infection chains using either malicious archives or MSI files, to create a backdoor into the intended system.
- As Chinese APT actors RedDelta and Mustang Panda correlate to some extent with Camaro Dragon, there is insufficient evidence to link the SmugX campaign to the Camaro Dragon group.
- Upon examining the evidence, the researchers observed a recurring theme centered on European domestic and foreign policies.
Tactics Used in the SmugX Phishing Campaign
The manipulation techniques, which were employed primarily to target government ministries in Eastern Europe, are focused mainly on European domestic and foreign affairs. The majority of the documents discovered contained content related to diplomatic matters, with some directly linked to China. Various documents uploaded to VirusTotal were identified, including-
- A letter originating from the Serbian embassy in Budapest.
- A document outlining the priorities of the Swedish Presidency of the Council of the European Union.
- An invitation to a diplomatic conference issued by Hungary’s Ministry of Foreign Affairs.
- An article highlighting the sentencing of two Chinese human rights lawyers to lengthy prison terms.
Moreover, the names of the archived files strongly indicate that the intended targets were diplomats and government entities. Examples of these file names include:
- Draft Prague Process Action Plan_SOM_EN
- 2262_3_PrepCom_Proposal_next_meeting_26_April
- Comments FRANCE – EU-CELAC Summit – May 4
- 202305 Indicative Planning RELEX
- China jails two human rights lawyers for Subversion
Read More: Types and Techniques of Phishing Attacks & How to Identify

How HTML Smuggling is a New Way to Deliver Malware?
HTML Smuggling is a new trend followed widely by cybercriminals and state-sponsored actors. It involves hiding malicious files within HTML documents, allowing them to bypass detection methods that rely on network analysis. In the SmugX campaign, HTML Smuggling is employed to trigger the download of either a JavaScript or ZIP file. When users open these compromised HTML documents, the following steps occur:
- The encoded payload within the code is decoded and saved as a JavaScript blob, specifying the file type, such as application/zip.
- Instead of using the standard HTML <a> element, the JavaScript code dynamically creates it.
- A URL object is generated from the blob using the createObjectURL function.
- The desired filename is set for the download attribute.
- Finally, the code simulates a user’s click by invoking the click action, initiating the file download.
- In older browser versions, the code utilizes msSaveOrOpenBlob to save the blob with the specified filename.
Leveraging HTML Smuggling, the SmugX campaign cleverly tricks users into unknowingly downloading malicious files, exploiting the inherent trust placed in HTML documents.
Also Read: Impersonation Attacks Led By Email Phishing and Spoofing
Decoding the SMUGX Phishing Attack Chain
The HTML smuggling technique is used in both SmugX attacks, according to the above-mentioned news report, to conceal malicious payloads in encoded strings of HTML pages that are attached to the bait message.
One campaign variant distributes a ZIP archive that contains a malicious LNK file that, when started, executes PowerShell to extract an archive and save it to the Windows temporary directory.
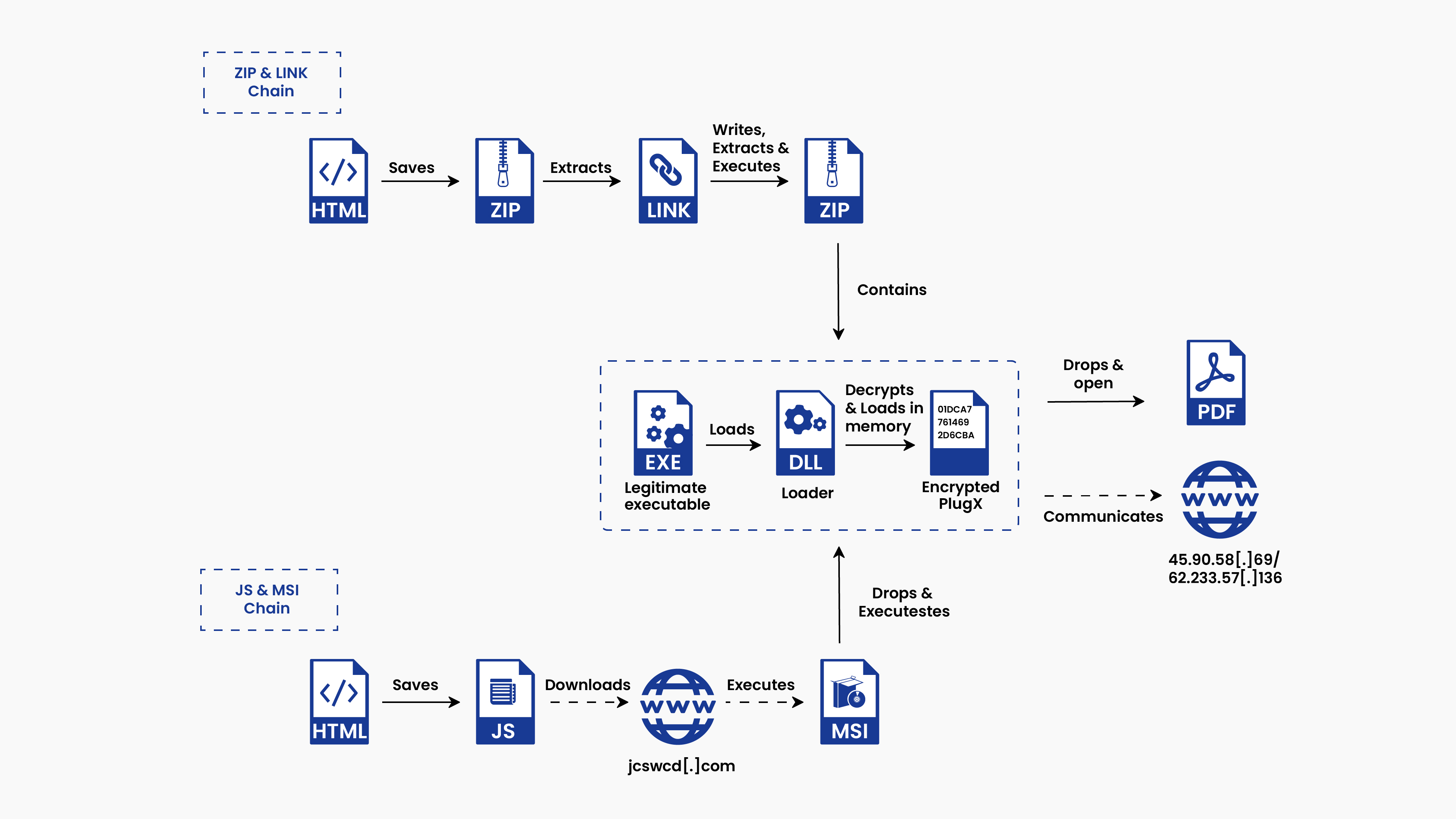
- In the first scenario, the HTML file hides a ZIP archive that carries a malicious LNK file. When the LNK file is executed, it triggers PowerShell to run.
- PowerShell then extracts a compressed archive that is embedded within the LNK file and saves it in the %temp% directory.
- The extracted archive, typically named tmp.zip or tmp<random_number>.zip, contains three distinct files:
- A legitimate executable, either robotaskbaricon.exe or passwordgenerator.exe, is utilized to sideload the payload.
- The malicious sideloaded DLL file is named RoboForm.dll.
- The payload data.dat, which contains the PlugX payload.
The “robotaskbaricon.exe” or “passwordgenerator.exe,” comes from an older version of the RoboForm password manager. In that version, there was a vulnerability that allowed the loading of DLL files unrelated to the application. This technique is known as DLL sideloading.
The other two files consist of a malicious DLL file called Roboform.dll, which is sideloaded using one of the legitimate executable mentioned earlier. The third file is named data.dat and contains the PlugX remote access trojan (RAT). When executed through PowerShell, this RAT enables unauthorized access to the compromised system.
- In the second variant of the attack chain, HTML smuggling is used to download a JavaScript file.
- This JavaScript file then downloads an MSI (Microsoft Installer) file from the attacker’s command and control (C2) server.
- Once downloaded, the MSI file creates a new folder within the “%appdata%\Local” directory.
- Within this folder, three files are stored. A legitimate executable file that has been hijacked, a loader DLL file, and an encrypted PlugX payload named “data.dat.
In this process, the legitimate program is run, allowing the PlugX malware to be loaded into the computer’s memory using DLL sideloading. This method is employed to evade detection by security measures. To maintain persistence on the infected system, the malware creates a hidden directory where it stores both the legitimate executable and the malicious DLL files.
- It also adds the program to the system’s ‘Run’ registry key, ensuring that it runs every time the computer starts up.
- Once the PlugX malware is successfully installed and operational on the victim’s machine, it may display a deceptive PDF file to divert the victim’s attention and lower their suspicion while it carries out its malicious activities.
PlugX is a RAT that has been utilized by various Chinese APT groups since 2008. It is a highly versatile malware with a wide range of capabilities, including stealing files, capturing screenshots, logging keystrokes, and executing commands on the compromised system.
Based on the findings, cybersecurity researchers suggest that the SmugX campaign indicates a growing interest of Chinese threat groups in targeting European entities, likely driven by espionage motives.
Read about the Reasons Behind Successful Phishing Attacks
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Mitigating the SmugX and PlugX Attack Chain
To effectively address this emerging threat at the very initial level, organizations should adopt a multi-layered approach to cybersecurity. Organizations often implement security tools and firewalls to protect their process and technology, but they ignore the most vulnerable link in cybersecurity, which is people. Organizations should focus on incorporating best security practices by regularly monitoring and assessing their employees’ vulnerability through simulated attacks. Organizations should look forward to ensuring that their employees are able to identify such threats and report them, which will additionally empower them to defend against cyber attacks.
Book a Free Demo Call with Our People Security Expert
Enter your details
The notion of people-centric security is attributed to the assessment, awareness, and empowerment of people, which is completely facilitated by the Threatcop Security Awareness Training (TSAT) Solution. The solution allows organizations to reduce their cybersecurity spending by running regular simulated phishing and ransomware attacks. The ransomware simulation and awareness training will allow the employees to identify ransomware attacks such as SmugX and help your organization to meet compliance standards.
As the SMUGX campaign continues to evolve and create havoc, cybersecurity leaders worldwide remain vigilant and actively develop countermeasures to detect and prevent HTML smuggling attacks. This incident serves as a clear reminder of the dynamic nature of cyber threats, emphasizing the significance of maintaining constant vigilance and adaptability to effectively combat ever-changing attack techniques.
Also Read: Prevent Phishing Attacks to Secure Your Organization
FAQs: SmugX Phishing Campaign and HTML Smuggling
The SmugX Phishing Campaign is a cyber attack targeting government entities across Europe, utilizing HTML Smuggling to exploit web browser vulnerabilities.
HTML Smuggling hides malicious files within HTML documents, bypassing network analysis to deceive users into downloading malware.
PlugX is a powerful remote access Trojan (RAT) commonly used by Chinese threat actors. It is deployed in the SmugX campaign to establish a backdoor entry on compromised systems.
Organizations can adopt a multi-layered cybersecurity approach and prioritize people-centric security through employee awareness training and simulated phishing exercises. Threatcop solutions like TSAT and TPIR completely facilitate awareness training and improve the decision-making of the employees. The solution allows organizations to reduce their cybersecurity spending by running regular simulated phishing and ransomware attacks.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
