The introduction of the internet has been immensely beneficial for businesses and individuals alike. We are all engaged through the internet in the form of social media, emails, and many other communication apps and software. Information exchange has become easier through this medium. As much as we love to surf the Internet and use it for formal and informal communication, we often miss out on discussing the possibilities of theft and misuse of the information being accessed through unseen channels.
Table of Contents
ToggleIn this article, we will discuss one such threat called spear phishing. We will first understand phishing and then what spear phishing. How are these two different? Since businesses are more prone to such attacks due to a lack of awareness among their employees, we will also try and share some tips to help you prevent spear phishing attacks.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is Phishing?
Before we move to spear phishing, it is important to understand what is a phishing attack. Phishing is a set of practices in which the attacker poses as a reputable institute and connects with the victim through emails or messages. The end goal can be anything like stealing personal information or sensitive business data using malware. This is a common social engineering attack using code injection, malware, and other network attacks.
What is Spear Phishing?
Spear phishing, as the name suggests, is a type of phishing attack that involves sending highly customized emails to employees inside an organization. The idea stays the same where the attacker poses as an influential individual or reputed organization to lure the reader into submitting important personal or business information. This type of phishing attack increases the likelihood that the victim will perform all necessary actions.
You might have gotten emails from unknown sources that look real, and they promise you some false information. All this is a form of scam and also a spear-phishing technique.

How Does Spear Phishing Work?
Spear phishing is a type of social engineering attack that can steal sensitive information and personal details on a network if you do not take proper steps to curb it. To eliminate the risk, you need to understand how it works and how a threat actor capitalizes on these methods.
Spear phishing is a sophisticated and more complex, yet targeted form of phishing. Threat actors can pose as your friend, organization, or family member and ask for credentials, credit card PIN, etc., through malicious links. These links you will receive in your inbox or messaging apps. Once you click on these, you will be shown a text box where you can enter the corresponding information.
Book a Free Demo Call with Our People Security Expert
Enter your details
Well, the modus operandi is not limited to malicious links, but also malware apps, ransomware, and so on. If you click on any of it without taking the right training and getting it confirmed by the right person, you are in for a big goof-up. These attacks are most likely to happen in an organization where employee security awareness training is lacking. Therefore, the first step toward preventing such attacks is to educate your employees.
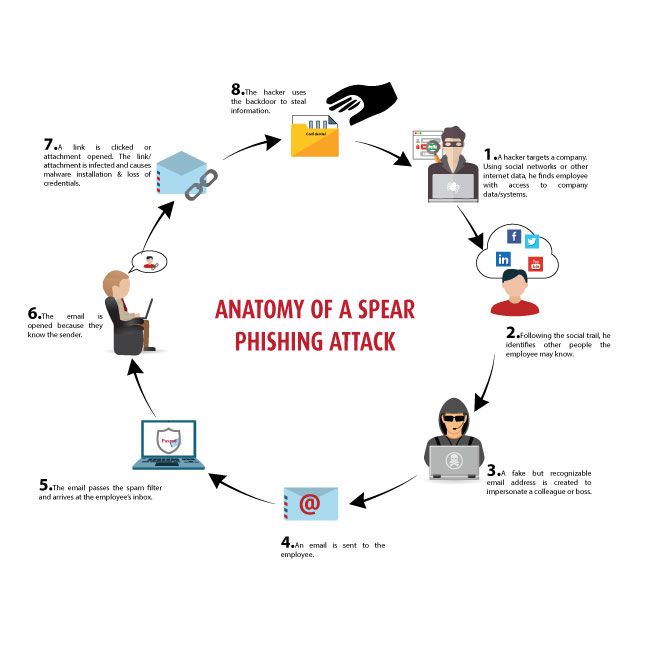
Why is Spear Phishing Attack Dangerous?
Most of us love socializing and want to get to know more people around us. Some of them become friends, and others become the best ones. You start hanging out with them and sharing personal life experiences and emotions with them. Think that this person is trustworthy, and one day you ask him to pay the bill using your credit card. You share the PIN with him.
The next day, your “best friend” disappears with your credit card and PIN. He also starts transacting at bigger shops, buying stuff with his money. You brought this whole problem upon yourself. This is more dangerous now since you shared it of your own will.
This is exactly how spear phishing attacks look on the web. They gain your trust by posing as friends, bosses, and so on, and lure you into sharing sensitive information. So now, as a CEO, it is your responsibility to provide cybersecurity practices to avoid spear phishing attacks.
How to Prevent Spear Phishing Attacks?
Preventing an attack can be much easier than controlling them after you fall for them. In order to prevent spear phishing attacks within any organization, here are a few simple steps to follow
Security Awareness Training
First and foremost, you need to educate your employees about cybercrime. Spear phishing is just one of the various cyber attacks your employees could fall prey to. Your organization needs to reach out to a cybersecurity firm like Threatcop, which offers a security awareness training tool named TSAT. This tool will help your organization properly train your employees about the risks of the cyber world.
Multi-Factor Authentication
Using multi-factor authentication is like using a dual locking system at your home. That means you would need two keys to open that locker. It also works like that, where first you need to put in your username and password, then an OTP will come for a second verification. After both steps, you get access. Now, if someone tries to access your email, you will get a message asking for a second authentication.
Strict password policies
Passwords are an important credential for any system online. If you don’t set good, strong passwords, you are bound to lose out on a lot of information because there are systems much more powerful that can help crack simple passwords. To keep your password safe, don’t include your name, birth date, lucky number, or anything else in your password. Here are a few things you should include in your password policies.
- Prohibiting password sharing
- Minimum password length guidelines and password complexity
- No password repetition. Use unique passwords only.
- Password age setting
Use DMARC technology
One of the ways to validate if the sender is a trusted entity is by creating a database of all the senders and then validating the emails against this database. If a sender does not align with the database, the security team will get notified about this activity. This whole process is known as Domain-based Message Authentication, Reporting & Conformance technology. So getting a DMARC tool like TDMARC by Threatcop will help your organization secure data.
Phishing Incident Response
We all know that human error is a real thing, and sometimes your employees might miss out on catching malicious mail. To eliminate that, your organization needs a phishing incident response tool. That will help your organization to find phishing emails with just a click.
Spear Phishing attacks seem like an easy-to-catch, but trust us, these campaigns are so accurate and convincing that you can fall prey to one of them. We discussed only a few ways to keep yourself safe from such attacks. There is a lot more. But you can start with these small things. Rome was not built in a day. Start slow, start right, and secure your data from such attacks.
Final Thought
No one is safe from being a target of cyber thieves, neither are they nor their organizations. Your organization could become a victim of this and other sophisticated cyber attacks if your information is stored online. The best defense against becoming a victim is to always be vigilant. To ensure that business assets are similarly protected, keep information private and never trust outside sources.
The goal of spear phishing emails is to deceive users into sending credentials, money, or other personal information by purposefully pretending to be someone they trust. Unfortunately, the sophistication of these particular types of social engineering attacks makes it easier for them to go unnoticed by most people.
FAQs: Spear Phishing Attack
Spear phishing is another typical method of a cyber attack against businesses. The most dangerous kind of phishing attack is probably spear phishing because it is so specific to its targets.
Spear phishing is more likely to be started by criminals looking for money, trade secrets, or military information than by ransom hackers. The unfocused efforts of phishing emails are far less effective than spear phishing attacks.
A suspicious attachment is a common sign of a phishing attempt. These attachments are frequently sent via phishing emails by hackers because they are aware that many recipients are curious enough to open them and click on any links or buttons they may contain. These attachments could be, for instance, a Word document or a zip file.
Spear phishing emails are more tailored to the target recipients. They are made to gain the victim’s trust. Basically, typographical or grammatical errors solicit private information. Links that do not match the domain are present, consisting of unsolicited attachments.
Typically, spear phishing is a targeted attack technique to access a person’s data. Their main targets are mostly high-ranking officials or those engaged in sensitive operations.
