Cyber attacks are already the biggest threat to organizations in the modern world. Of these, ransomware attacks are the most dangerous and devastating ones, especially in terms of damage inflicted. This infamous form of cyber attacks is based on the concept of the double extortion model.
Table of Contents
ToggleRansomware attacks could incur huge damage to the organizations financially and reputationally. These attacks can lead to data breaches and exploit system vulnerabilities. The number of ransomware attacks has reportedly increased in the last few years.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is a Ransomware Attack?
Ransomware is malicious software that is developed and injected into a system to block its access to users and encrypt the existing data. The main motive of encrypting the data is to make victims pay the demanded ransom in exchange for the decryption key or data. Once the attackers get into a system, they encrypt all its data and then freeze the screen with the message of the attack and ransom demands.
In some cases, during encryption, the index of data on a system is encrypted into gibberish, which can only be restored using a decryption key. In other cases, screen lockers simply block user access to the system by freezing the screen, declaring that the system is encrypted.
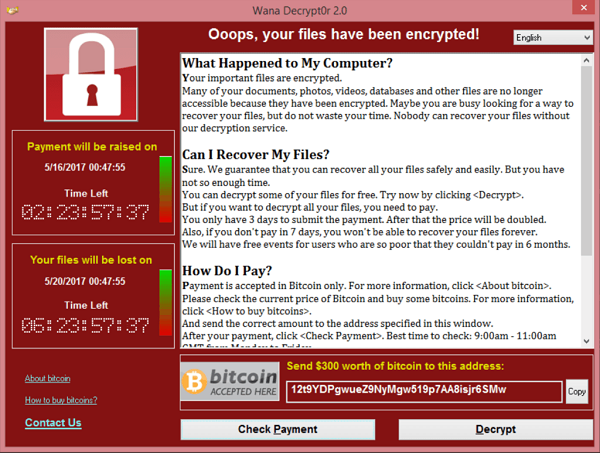
Several notable companies all across the globe have fallen victim to this vindictive attack. Cybercriminals spare no one and can attack any institution or business across all industries. Various government and security agencies advise people against paying the ransom as this increases the occurrence of these attacks.
Book a Free Demo Call with Our People Security Expert
Enter your details
How Does a Ransomware Attack Work?
Ransomware is a type of cyber attack where threat actors use various attack vectors to infect the systems of target users with malware or virus-embedded software. Once the system is infected with malware, it provides cyber attackers with access to its data. They can then track the system’s functioning and explore the data at will.
Once the threat actors gain access to the system, they can download all the data and extort the organization for ransom. They can also encrypt the data and freeze the system, disrupting the activities of the whole organization. In this way, they not only exploit the target’s data but also leverage it for ransom. Also, they can demand money for decrypting data or providing some solution to secure organizations from future malware attacks. That’s why ransomware attacks are believed to be based on a double extortion mechanism.
In most cases, the demanded ransom from the victim comes with a deadline. If the victim fails to pay within the provided timeline, the data might get lost forever, or exposed to the public, or sold to competitors. Ransomware attacks are very common these days and have impacted organizations globally.

Notable Ransomware Attacks Worldwide
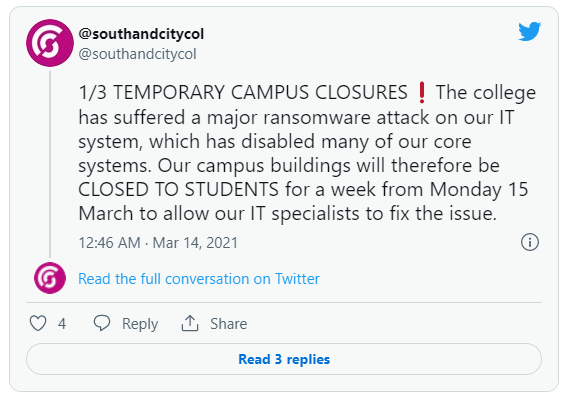
Birmingham College Hack
According to an article, Birmingham College fell victim to a ransomware attack which led the institution to ask their 20,000 students to stay at home for a week.
The threat actor behind Birmingham ransomware attack was never identified and the information about the attack was relayed through a series of tweets. The same tweets notified the students about the classes to be resumed online, meanwhile the experts were striving to recover the exploited system.
Acer Loses $50 Million in a Ransomware Attack
Acer became a victim of the infamous ransomware group REvil that caused a financial damage of $50 million. An article by PCMag reported that REvil gave a deadline to Acer for paying the demanded ransom, after which the stolen data would be exposed to the public. During the analysis, it was found that REvil exploited the Microsoft Exchange vulnerability to carry out this attack.
Microsoft released the patch later in 2021 to contain the vulnerability. The vulnerability was named ‘Hafnium’. The ransomware group announced the breach on their data leak website with some images as proof. REvil was also found guilty of carrying out a ransomware attack on Travelex, incurring financial damage of $6 million on the London-based foreign exchange company.
“Acer routinely monitors its IT systems, and most cyberattacks are well defended. Companies like us are constantly under attack, and we have reported recent abnormal situations observed to the relevant law enforcement and data protection authorities in multiple countries.”
“We have been continuously enhancing our cybersecurity infrastructure to protect business continuity and our information integrity. We urge all companies and organizations to adhere to cyber security disciplines and best practices and be vigilant to any network activity abnormalities.”
Statement made by Acer
Lapsu$ targeted Nvidia
Nvidia is a US-based largest microchip manufacturer who became victim of a ransomware attack on 28th February, 2022. They were attacked by a ransomware gang known as Lapsu$. The group threatened the company to expose their 1TB data by 4th March, if the ransom isn’t paid. However, Nvidia had backup of their data due to which they haven’t paid any ransom yet and are still in the process of analyzing the compromised data.
The breach occurred on the systems of Nvidia, revealing the company’s proprietary data and employees credentials along with source codes of some important applications and softwares. In response to the attack, the company went offline for two days.

Colonial Pipeline under Ransomware Attack
Colonial pipeline is a 5,500 mile-long gas pipeline, which is the largest in the United States. They became victims of a ransomware attack, leading to a 5-day shutdown and disrupting gas services at 10,000 gas stations across the country. The gang responsible for this attack was Darkside ransomware, which demanded a ransom of $4.4 million.
The Colonial Pipeline paid the ransom in the form of cryptocurrency and received a decrypting tool in exchange to restore their computer network. However, the decrypting tool was found to be very slow and the company utilized the alternative of restoring their data from backups. The FBI traced a significant amount of transfer being made but the ledger was password protected.
Chemical Distributor Brenntag Paid $4.4 Million Ransom
In another attack, Darkside ransomware group targeted the chemical distributor company, Brenntag. The ransomware group claimed to have stolen over 150GB of their data and they showcased a page of leaked private data as a proof. Darkside demanded the ransom of $7.5 million but after the negotiations, they were paid $4.4 million by the company. Darkside ransomware carried out this attack through their affiliate, who were able to steal credentials.
Most Infamous Ransomware Groups
Darkside Ransomware Group
The Darkside ransomware group is based on Ransomware as a Service (RaaS) model. This means, their hackers have partnership with third-party affiliates, who delegate RaaS attacks on the target organization. Through this method, Darkside is able to earn about 20% to 30% of the acquired ransom, while the rest goes to the affiliate.
Dharma Ransomware Group
Dharma ransomware group is another group of threat actors who are known for their complicated decryption tool. The average demanded ransom by the group is $66,688 and the average duration of the complete attack is 14 days, which is much lower than the other ransomware groups. This ransomware group is believed to use 83% times remote desktop protocol as an attack vector, while 17% times phishing emails. Dharma ransomware group is also known as CrySis as they target Windows XP and exploit user’s files in the directory.
Conti Ransomware Group
This group mostly targets mid- and large-sized organizations and their average ransom is $480,333, while the average duration of the ransomware attack is 15 days. The group provides quite a straightforward and simple decryption tool and their data recovery rate is pretty high. The attack vectors of Conti ransomware group are 33% remote desktop protocol, 34% phishing emails, and 33% software & hardware vulnerabilities. Conti is known for exploiting various vulnerabilities in Microsoft products.
REvil Ransomware Group
This ransomware group is regarded to be among the most ruthless gang. They employ RaaS affiliate to carry out the attack. In one of their attacking spree in the first six months of 2021, they carried out 25% of all the ransomware attacks. The group has targeted some of the crucial companies like Acer, JBS, Kaseya, and Quanta Computer Inc.
How to Mitigate the Risk of Ransomware Attacks?
Ransomware attacks are a menace to the cyber world, and the greed of money often attracts more ransomware groups into the field. However, organizations can simply employ some practices to mitigate the risk associated with ransomware attacks. They are listed below.
Backup Data at Multiple Locations
Every organization must make at least two copies of their data; that is, they must back up data to an external source. The data backup allows the company to restore their data in case the existing data is encrypted or lost. In the above-mentioned several attacks, organizations have started restoring their data from backup even before they retrieved the decrypting tool.
Use Multi-factor Authentication
The MFA provides an additional layer of security over passwords or account credentials. The MFA is used as a double authentication technique, where one is static and the other is in real-time like an OTP on a registered contact number. So, the benefit of MFA is that even if the credentials have been compromised, the threat actor cannot access the data because they won’t have the real-time generated password.
Email Security
Every organization must employ email security tools to make sure that their communication media is secure. The email security tools not only protect the email domain but also improve email deliverability. Organizations must use DMARC, an email authentication protocol, and a phishing incident response tool to empower employees to report malicious emails.
Cybersecurity Awareness
The biggest cyber attacks are usually due to employee negligence and unawareness. They often get lured by the threat actors and lose credentials or data. The cybersecurity awareness training for employees is meant to educate them about various kinds of attack vectors and how to prevent them.
Proactive Practices and Security Awareness are the Solutions
Ransomware attacks are mostly carried out by ransomware groups who commonly use the dark web as a platform for marketing and commercializing the stolen data and credentials. Various organizations across the globe have suffered from ransomware attacks and lost millions of dollars. However, organizations can prevent ransomware attacks by being proactive and incorporating security practices. Along with that the organizations can employ tools of security awareness to train employees through simulation and learning management systems to make them the strongest line of defense.

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
