Progress Software Corporation, an American public company, issued an alert on May 31, 2023, regarding a critical SQL injection vulnerability discovered in their MOVEit Transfer solution. Following this disclosure, numerous organizations like BBC, and British Airways have come forward to reveal that they have fallen victim to cyber-attacks stemming from a zero-day vulnerability (CVE-2023-34362) in the file transfer product. According to reports, the cybercriminal gang known as Clop, believed to be of Russian origin, is responsible for the attack. The group appears to specifically target organizations in North America and the UK, indicating they have gained full control over a MOVEit installation.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
On June 6, 2023, several notable organizations including the BBC, Boots, and British Airways (BA) confirmed their exposure to a vulnerability. The BBC has informed its staff that personal information such as ID numbers, dates of birth, home addresses, and National Insurance numbers have been compromised in the attack. BA employees have also been notified of the potential theft of their banking details. The attack has affected companies that use Zellis as their payroll service and human resource department, which is the UK’s leading payroll provider.
What is MOVEit and Why is it important?
MOVEit is a file transfer software owned by software solution provider, Progress Software Corporation. It encrypts files and implements secure transfer protocols to transfer data between organizations and customers. With its extensive user base spanning various industries, including healthcare, Progress Software Corporation’s MOVEit is widely recognized as a premier Managed File Transfer (MFT) software. However, there have been reports of a zero-day vulnerability in the software that has been exploited by hackers. The vulnerability is a SQL injection vulnerability that could allow a hacker to gain unauthorized access to the database of MOVEit.
How It All Began: Uncovering the MOVEit Transfer Vulnerability
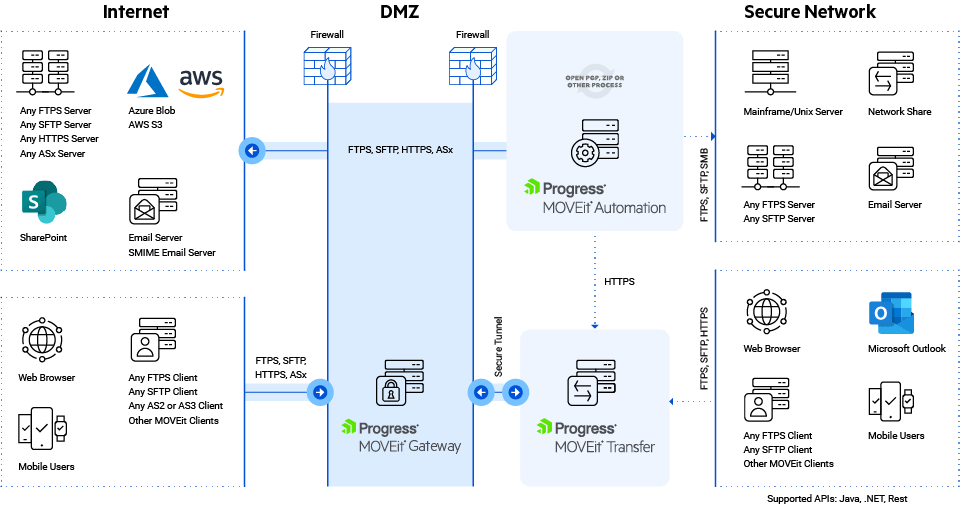 Architecture of MOVEit transfer
Architecture of MOVEit transfer
Alerting its users, Progress Software Corporation on May 30, 2023, informed that it has found a vulnerability dubbed CVE-2023-34362 in MOVEit Transfer and related MOVEit Cloud products. The American company published an advisory when it discovered the zero-day SQL injection vulnerability. The advisory highlights that the extent of the vulnerability’s impact varies depending on the specific database engine employed, such as Azure SQL, MySQL, and Microsoft SQL Server. Both the HTTP and HTTPS protocols can be used to exploit unpatched systems, giving attackers access to sensitive database data as well as the ability to execute SQL commands for changing or deleting database items.
Read More: Zero-Day Attack: Protect Your Organization from the Unforeseen
Whereas, public reports broke the news on May 27, 2023, claiming that the attacks against this vulnerability were true zero-day attacks. They started around this time when the American company wasn’t even knowing about it or no patch was available. Reports asserted that attacks have focused on creating web shells on vulnerable systems and utilizing the credentials to steal data from compromised systems.
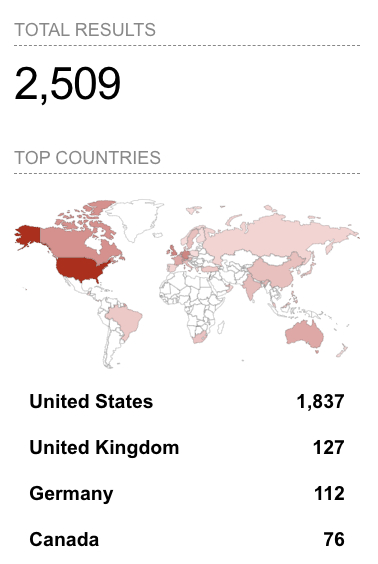
As of May 31, it was discovered that some 2,500 instances of MOVEit Transfer were visible on the public internet, with the majority of them appearing to be based in the United States, according to recent data. A Shodan search for exposed MOVEit Transfer instances returned over 2,500 results, the majority of which belonged to US customers. Previous analyses conducted by cybersecurity experts have highlighted similar vulnerabilities, where SQL injection flaws could lead to remote code execution (RCE) and serve as an initial access point for threat actors to infiltrate corporate networks.
Book a Free Demo Call with Our People Security Expert
Enter your details
In recent times, file transfer solutions have increasingly become a prime target for cyber attackers, including ransomware groups. Later on June 2, the vulnerability was officially assigned the identifier CVE-2023-34362 in the updated advisory by Progress Software. Prior to the security advisory, threat actors had already exploited the vulnerability for at least four days. In light of this, Progress Software urges MOVEit customers to examine their systems for any signs of unauthorized access spanning “at least the past 30 days.”
You can read more about- Ransomware Statistics For 2022
Who is Behind the Attack?
On June 4, 2023, a ransomware actor group known as “Lace Tempest or Clop Group” was attributed to the attacks by Microsoft Threat Intelligence. This group has gained notoriety for its involvement in ransomware operations and running the Clop extortion site. They are also recognized in the industry by alternative names such as FIN11, DEV-0950, and TA505. In a communication posted on their leak site on June 6, the Clop ransomware gang asked victims to contact them before June 14 to negotiate extortion fees for the deletion of stolen data.
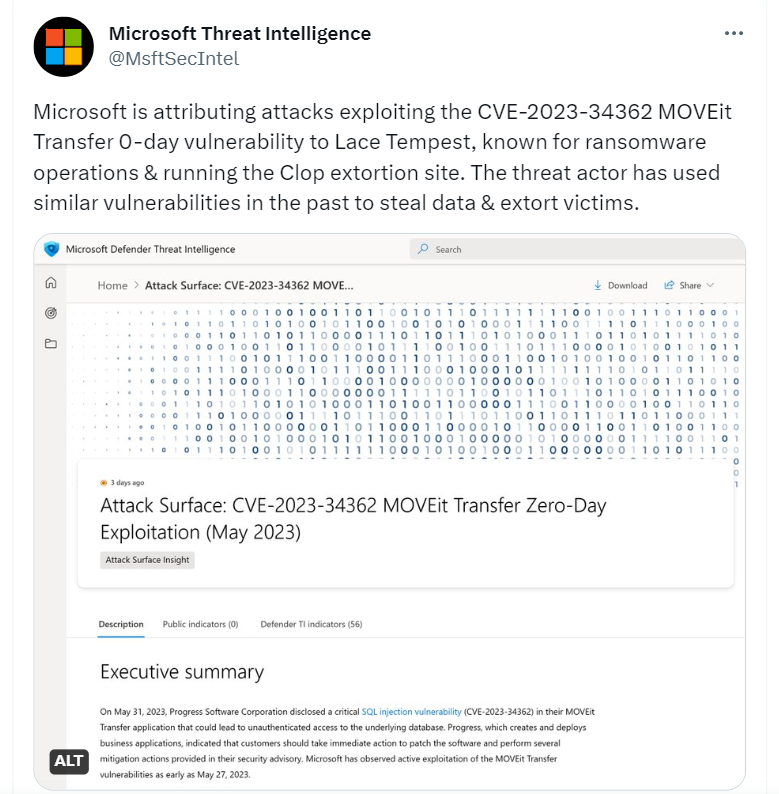
Threat intelligence organizations captured screenshots of the threat group’s demands. Google-owned Mandiant, tracking the activity under UNC4857 and identifying the web shell as LEMURLOOT, has found significant tactical connections with FIN11. Notably, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) put the flaw to its list of “Known Exploited Vulnerabilities” (KEV) and cautioned government agencies to fix the issue before June 23, 2023 by using the vendor’s patches. Notably, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, advising federal agencies to apply the patches provided by the vendor before June 23, 2023.
This development follows the similar zero-day mass exploitation of Accellion FTA servers in December 2020 and GoAnywhere MFT in January 2023. Therefore, it is crucial for users to promptly apply the provided patches to protect against potential risks and secure their systems. The cybersecurity firms have identified the same web shell name as exposed to the public internet in multiple customer environments, It directs automated exploitation.
The web shell code within the exploited MOVEit Transfer instances follows a specific pattern. It initially checks if an incoming request contains a header named X-siLock-Comment. If this header does not have a particular password-like value, the web shell responds with a 404 “Not Found” error. A top cybersecurity company has confirmed the presence of a web shell, specifically the file human2.aspx located in the www root folder of the MOVEit install directory, serves as a key indicator of successful post-exploitation.
Read More: How Employee Unawareness Led to Coinbase Data Breach?
It is important to note that the original aspx file used by MOVEit for the web interface is named human. aspx. This pattern has been consistently observed in all instances of MOVEit Transfer exploitation recorded as of June 1, 2023. The accompanying image demonstrates an attack and subsequent web shell traffic as documented in the IIS logs. If an inbound request has a header called X-siLock-Comment, the web shell code can first check to see if it contains that information. If it does not, it delivers a 404 “Not Found” error.
A cybersecurity organization confirmed that a critical indicator of successful post-exploitation is the presence of a web shell: c:\MOVEit Transfer\wwwroot\human2.aspx. Above, in the image, is an example of an attack and the follow-on web shell traffic as recorded in the IIS logs. A human2.aspx file must be present in the wwwroot folder of the MOVEit install directory in order for MOVEit Transfer to be exploited as of June 1, 2023 (human.aspx is the native aspx file used by MOVEit for the web interface).
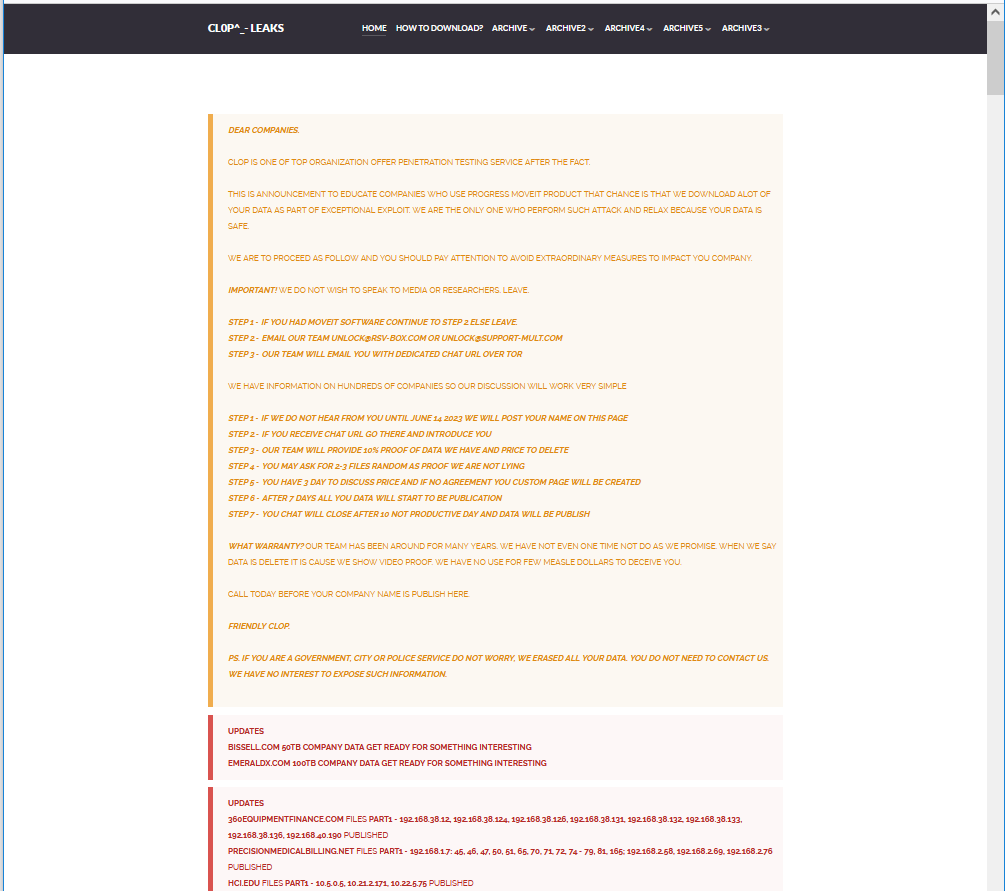
Clop has posted a notice on the dark web, warning affected firms of the MOVEit hack to contact them before June 14th to prevent the publication of stolen data. The group claims to have downloaded significant data through an exploit. In an unusual move, Clop is requesting that victim organizations initiate contact with them through email to negotiate on their darknet portal.
This tactic suggests that the group may be overwhelmed by the scale of the hack and the amount of data they have acquired. Cybersecurity researchers have been monitoring Clop since February 2019, and it is estimated that the group has targeted over 230 companies across different sectors. They maintain a presence on the Dark Web, regularly uploading data dumps from their breached victims.
Big Companies Affected
Just after the attack was registered by Progress Software, organizations including Aer Lingus, BBC, Boots, and British Airways (BA) confirmed that they have been impacted. The BBC informed personnel that the incident resulted in the compromising of ID numbers, dates of birth, residential addresses, and National Insurance numbers. Although it employs roughly 22,000 people worldwide, BBC guaranteed that it was investigating the breach’s scope in conjunction with UK payroll service Zellis.
Payroll data may have been stolen, the BBC, British Airways, and Boots have informed more than 100,000 employees. Also informed that their banking information may have been stolen is the BA crew. The Zellis systems, which BA and others utilise for IT services for the payroll and human resources departments, are where the incident started for them. Following these claims, a Zellis spokeswoman also stated that a “small number” of the company’s clients have been affected.
One more big name that has been added to the victims’ list which is attacked by the Clop ransomware group is the UK media watchdog firm Ofcom. Ofcom has confirmed that it has fallen victim to a cyberattack conducted by hackers associated with a well-known Russian ransomware group. The attack resulted in the unauthorized download of confidential data pertaining to certain companies regulated by Ofcom, as well as personal information belonging to 412 Ofcom employees.
Upon discovering the attack, Ofcom took immediate action by promptly notifying the affected companies it regulates and referring the matter to the Information Commissioner’s Office (ICO), the authority responsible for data protection and privacy in the UK. Additionally, Ofcom swiftly implemented recommended security measures, including discontinuing the use of the compromised MOVEit service, and continues to provide support and assistance to the affected individuals and organizations.
Are You a MOVEit User? Here is what you need to know
To mitigate the impact of the vulnerability in MOVEit Transfer, experts, and Progress Software recommend the following steps:
Turn off all HTTP and HTTP traffic going to your MOVEit Transfer environment
Firewall rules should be modified to prevent any HTTP or HTTPS traffic from reaching the MOVEit Transfer environment on ports 80 and 443. Access to the REST, Java,.NET, and native host for MOVEit Automation tasks, as well as the MOVEit Transfer add-in for Outlook, will be restricted as a result of this action. The SFTP and FTP/s protocols, however, will continue to operate correctly. Administrators can access MOVEit Transfer by connecting to the Windows PC using a remote desktop and going to “https://localhost/” on their browser.
Conduct a Comprehensive Security Audit- Review, Delete, and Reset
- Thoroughly review the system for unauthorized files and user accounts. Remove any instances of the “human2.aspx” and “.cmdline” script files. Additionally, check for new files created in the “C:\MOVEitTransfer\wwwroot” directory and the “C:\Windows\TEMP[random]” directory with a “.cmdline” file extension.
- Monitor logs for any unexpected downloads from unknown IP addresses or a significant number of file downloads.
- Reset the credentials for the service accounts associated with affected systems and the MOVEit Service Account. This will help ensure that unauthorized access using compromised credentials is mitigated.
Apply the Patch
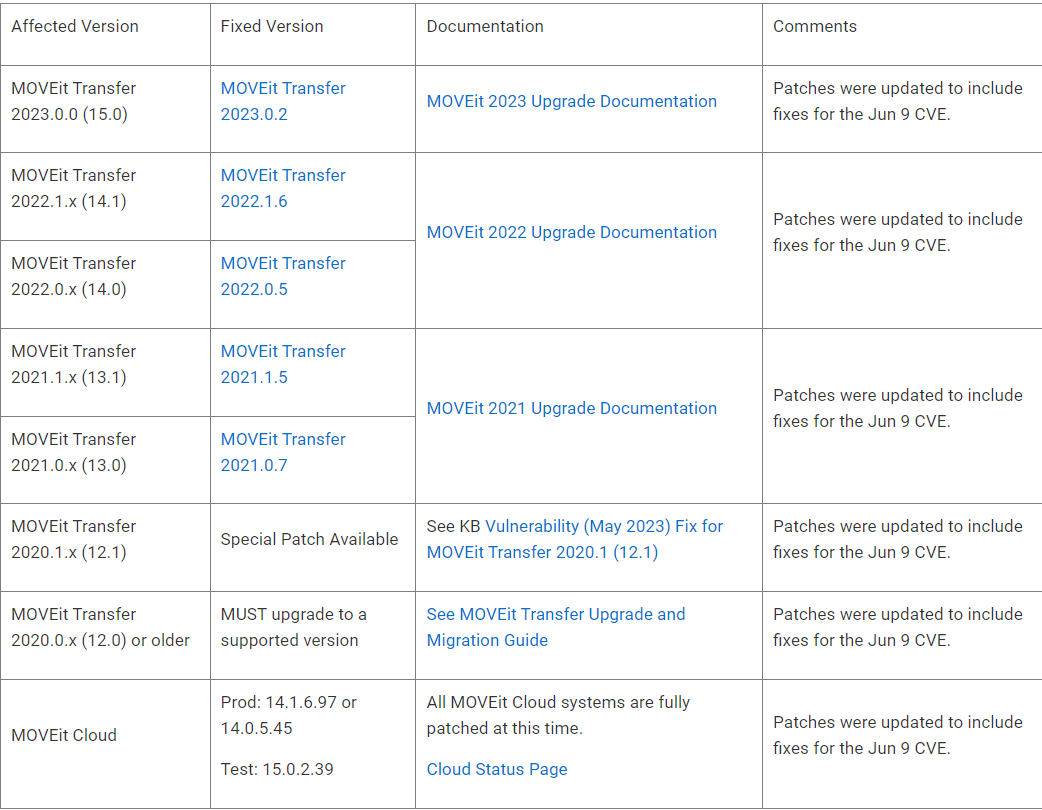
Progress Software provided patches for all supported versions of MOVEit Transfer. Please note that when applying the patch, there is no need to modify the license file. Simply follow the instructions provided with the patch to ensure a successful update. It is crucial to keep MOVEit Transfer up to date with the latest patches to enhance security and protect against vulnerabilities.
Enable Web Traffic, Verify, and Monitor
Enabling all HTTP and HTTPs traffic to your MOVEit Transfer environment is advised to ensure MOVEit Transfer runs without a hitch. By changing the firewall rules to permit HTTP and HTTPS traffic on ports 80 and 443, this can be accomplished. You should re-set the service account credentials if you discover any signs of intrusion.
While they wait for the required security updates to be installed, organisations can reduce the risk and potential effects of the MOVEit Transfer vulnerability by taking the procedures outlined in this mitigation guide.
FAQs: MOVEit Zero-day Vulnerability Attack
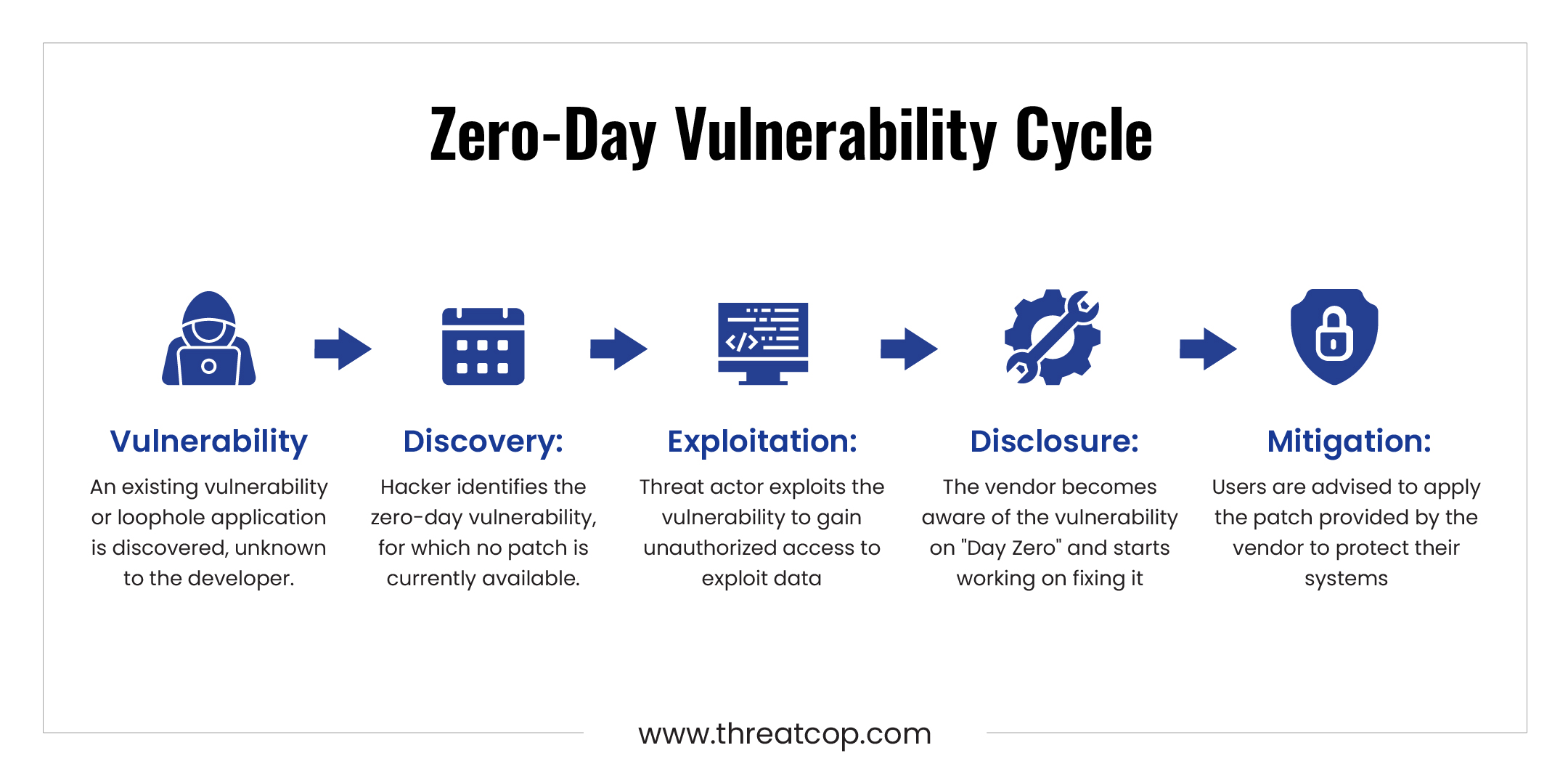
A zero-day vulnerability refers to a security flaw or weakness in software or hardware that is unknown to the developer. It is called “zero-day” because the vulnerability exists before the affected party becomes aware of it or has had a chance to fix it. As happened in the case of Progress Software, where the vulnerability in its MOVEit File Transfer was not known by the developers which was later exploited by the Russian-linked ransomware hackers Clop group. The hackers take advantage of the vulnerability to gain unauthorized access, compromise data, or perform malicious activities. Zero-day vulnerabilities are considered highly valuable to attackers as they offer an advantage due to the lack of available patches or security measures.
MOVEit is a file transfer software developed by Standard Networks which was later acquired by Ipswitch,Inc & Progress Software in 2008. It provides secure encryption and utilizes reliable File Transfer Protocols for the seamless transfer of data. MOVEit offers advanced features like automation, analytics, and failover options. Companies across the world use this software to transfer their data securely. It is used by various sectors, including healthcare with clients like Rochester Hospital and Medibank. Additionally, MOVEit is widely adopted by IT departments in financial services, high technology, and government organizations.
The hacking group behind the attacks on MOVEit Transfer is known as Clop. Clop group is a well-known cybercriminal gang believed to be of Russian origin. They have gained notoriety for their involvement in ransomware operations and running the Clop extortion site. They are also recognized in the industry by alternative names such as FIN11, DEV-0950, and TA505. Clop has specifically targeted organizations in North America and the UK, and they have been actively exploiting the zero-day vulnerability in MOVEit Transfer to gain control over affected systems.
American Software Company, Progress Software is a provider of different software tools and solutions for application development, integration, data connectivity, and digital experience. Its services helps companies to build and deploy applications, integrate systems and data, and enhance customer experiences.
SQL injection is nothing but an attack technique taking advantage of the vulnerability in the web application database that allows submitting arbitrary SQL code in the database query without proper sanitation. During the attack, the hacker exploits these vulnerabilities by inserting malicious SQL code into the application’s input fields and the application process it without any check. This lead to the execution of malicious SQL in the database server which gives unauthorized access, data manipulation, or even the complete compromise of the application and its underlying database.
