According to Global DMARC Adoption Report of 2019, 79.7% of the companies have left their consumer data vulnerable by not implementing email domain security protocols.
(Source: Business Wire)
Email is one of the most standard and official forms of communication for exchanging messages everywhere in the world. But have you ever wondered whether the emails you receive always come from authentic sources?
Table of Contents
ToggleSuppose you get an email from your Finance Department asking for a transaction or sensitive information about your account. How can you be sure that this email came from a credible source?
Email security is a matter of concern for every organization today. In fact, according to IC3, there were 19,369 BEC (Business Email Compromise) complaints in 2020 that incurred a loss of over $1.8 billion to organizations.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Back in 2012, big organizations like Google, Microsoft, Paypal, and Yahoo developed a protocol to place alongside SMTP (Simple Mail Transfer Protocol) for email authentication. This protocol is known as DMARC (Domain-based Message Authentication, Reporting, and Conformance).
But as per an article published by Tech Crunch in 2018, only half of the Fortune 500 deployed DMARC for email security. Moreover, according to the article CIO insight in 2021, 67% of Fortune 500 companies don’t have a DMARC implemented in their corporate domain!

So what is this DMARC and how can it save organizations from billions of losses?
What is DMARC?
DMARC is an effective email validation protocol that protects your organization’s email domain from email-based attacks. Threat actors can carry out malicious activities like email spoofing and phishing scams.
In common terms, it provides domain owners with insights into who is sending emails from their domain, giving them detailed information about their outbound email channel. This email authentication protocol offers the framework to ensure that your customers or clients will only receive emails sent by authorized sources. This protocol improves the delivery rate and enhances domain reputation.
Book a Free Demo Call with Our People Security Expert
Enter your details
It is an email authentication standard that secures senders and receivers from email-based attacks like spamming, email domain spoofing, etc. It is also used to reduce and prevent attacks like BEC (Business Email Compromise) attacks, phishing, etc.
This protocol is implemented on a technical level, which allows an organization to authenticate its emails by setting either of the three main policies:
- None
- Quarantine
- Reject
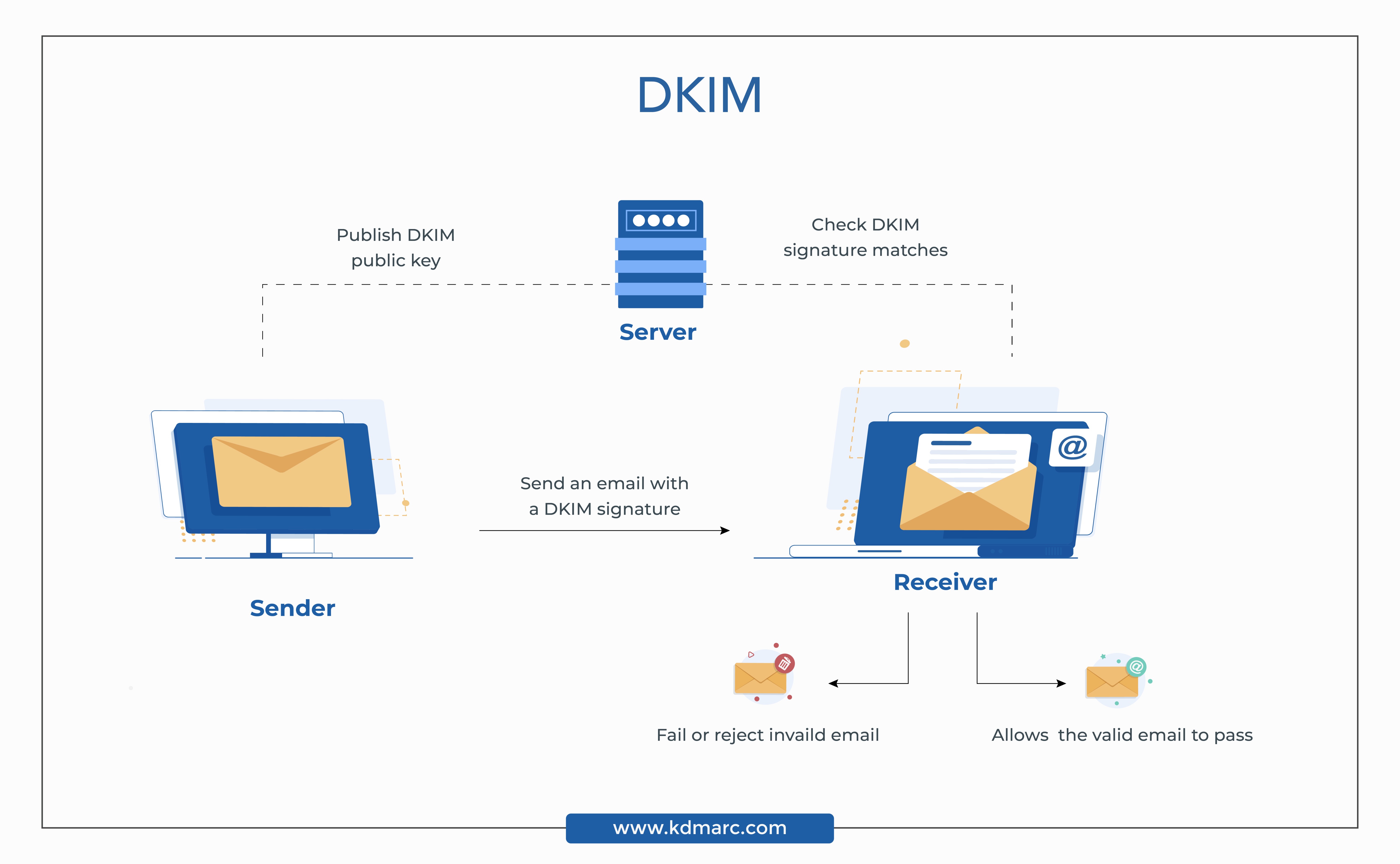
It is aligned with SPF (Sender Policy Framework) and DKIM (Domain Key Identified Mail) standards. DMARC facilitates a set of email authentication rules to either reject or quarantine emails from unauthorized resources.
The DNS (Domain Name Server) holds DMARC entries. These entries are checked by the company’s exchange server policies. The policies are set by the company, based on how the email is authenticated on the receivers’ end. Once the email is authenticated, it is monitored, rejected, or quarantined based on the configured policy.
It empowers ISPs (Internet Service Providers) like Gmail, Outlook, Yahoo, etc., to protect the organization’s email services and the recipient’s personal information from phishing. However, it is not an email authentication protocol that enforces itself. It empowers domain owners to take defined actions against emails that fail authentication checks.
Why DMARC is Important?
According to a spam report by ENISA (European Network and Information Security Agency), 95% of all emails sent over the internet end up in the spam box. Most of these spam emails are sent using spoofed addresses. A cybercriminal can use your organization’s domain name to send emails to your customers, tricking them into giving their credentials or sensitive information.
If your email domain is impersonated, it can disrupt your relationship with your clients and impact your organization’s reputation. It can also affect your domain’s email deliverability and engagement rates. Once your domain’s reputation starts deteriorating, even legitimate outbound emails will be redirected to spam or fail to deliver.
Securing your domain with DMARC can prevent impersonators from forging your domain name and sending fraudulent emails on your behalf. It also gives you insights into your outbound email channel. Moreover, it helps in boosting your domain’s engagement and deliverability rates.
What is the Purpose of DMARC?
The primary function is to detect and stop email spoofing. For instance, a phishing scammer is impersonating the domain of a bank and sending out emails to its customers stating that their accounts have been frozen and prompting them to click on a link to unfreeze them.
Customers assume that the email is legitimate and click on the embedded link that leads them to a fraudulent website. When the customers log in, cybercriminals will get access to their credentials.
It is used to fully secure your email domain. Email authentication techniques like SPF and DKIM are designed to protect your domains from such scams. However, cybercriminals have evolved their tactics and can easily bypass these security measures.
This is why, it is deployed to establish a link between DKIM and SPF. Once you have implemented them, ISPs send Forensic (RUF) and Aggregate (RUA) reports to the email address that is published in your DMARC record every day.
Here is some information about the two types of reports available:
- Aggregate Reports (RUA)
Aggregate reports are sent to your email address every day to provide a detailed overview of your domain’s email traffic. These reports include a list of all the IP addresses that have attempted to send emails using your domain name.
- Forensic Reports (RUF)
Forensic reports send you real-time alerts in case emails sent from your domain fail to deliver. These reports always include the original message headers and may include original messages.
The purpose of securing email domain servers is fulfilled using the policies that are placed in the DMARC record.
What is a DMARC Record?
It is an important element of DMARC implementation. It contains a set of rules and information to define a record. This record informs email recipients whether the domain is set for DMARC or not. If it is set, then the domain owner uses the policy that is present in the record itself.
The DMARC record is made up of host names and tag-value pairs. It also includes the DNS database of an organization. It is a version of a specifically formatted standard DNS TXT record with a particle name, i.e., “_dmarc.mydomain.com“. The tag-value pairs are something like “p=“, which is explained later in this blog.
What is the Importance of the DMARC Record?
The DMARC record plays a particularly significant role in the validation of an email. It helps the sender and receiver sides match the records at their respective ends, which provides a basis for the authentication of the emails. If it is not available, then it will not be possible to match the signatures and policy framework on both ends.
Example of DMARC Record
Here is an example of the record:
v=DMARC1; p=reject; rua=mailto:[email protected]; ruf=mailto:[email protected]m; fo=1;
The above example has five tag-value pairs.
In the above DMARC record:
- “v=DMARC1” indicates the version of DMARC
- “p=reject” indicates the applied DMARC policy
- “rua=mailto:[email protected]” is the tag that allows mailbox providers to know where the aggregate reports are to be sent
- “ruf=mailto:[email protected];” tag allows the mailbox providers to know where forensic reports are to be sent
- “fo=1” tag helps mailbox provider to know about the samples of emails that have SPF and DKIM checks or any of the two checks
Note: The domain owner can use other available configuration options for setting up the DMARC policy record.
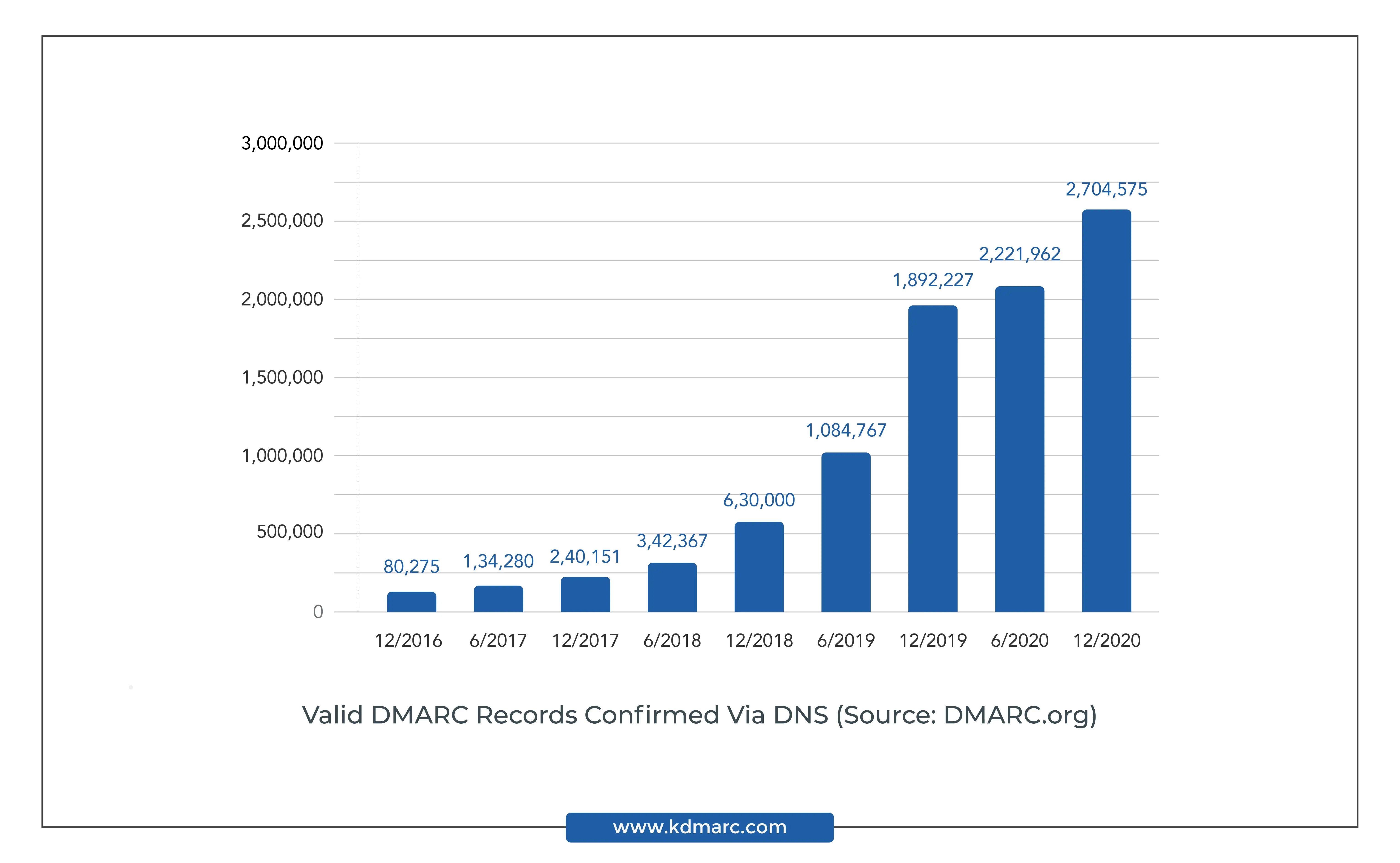
Number of Valid DMARC Records Confirmed via DNS (Source: DMARC.org)
What are DMARC Policies?
An organization can set a specific policy that determines its email authentication standard. A policy instructs the receiving mail servers, such as Gmail, Outlook, Live, etc., about the rules to follow. It enforces the respective policy in accordance with the DMARC check.
There are three types of policies that you can choose from for handling unauthorized emails. These emails are either sent or received on your behalf by instituting one of the following policies in the DMARC record:
-
None Policy
“p=none”
This policy monitors your email traffic and does not take any specific action for emails that fail the DMARC check. You can use this policy to gather DMARC reports and analyze the data in those reports.
The “none” policy instructs the ISPs to send the reports to the email address published in the RUF or RUA tag of your domain’s DMARC record. This is also known as a ‘Monitoring Only Policy’ as it helps one to get a deep insight into their email channel. This policy will not affect email deliverability and will allow all emails to reach the recipient’s inbox irrespective of their DMARC authentication.
-
Quarantine Policy
“p=quarantine”
According to this policy, unauthorized emails are sent to the spam folder. It allows email receivers to send DMARC-failed emails in quarantine, i.e., to the junk/spam folder.
The “quarantine” policy instructs the ISPs to redirect emails failing the DMARC authentication to the recipient’s spam folder. The emails that pass the DMARC authentication will be successfully delivered to the recipient’s primary inbox. Even though this policy mitigates the impact of spoofing, the spoof emails might still be able to reach the receiver.
-
Reject Policy
“p=reject”
The Reject policy is the most recommended policy as it secures all your emails. It ensures that any email that fails the DMARC check is not delivered to the receiver at all.
The “reject” policy instructs the ISPs to not deliver emails that fail the DMARC authentication at all. Emails that pass the DMARC authentication will be successfully delivered to the recipient’s primary inbox. Since this policy prevents all spoofed emails from landing in the recipient’s inbox, it mitigates the impact of spoofing.
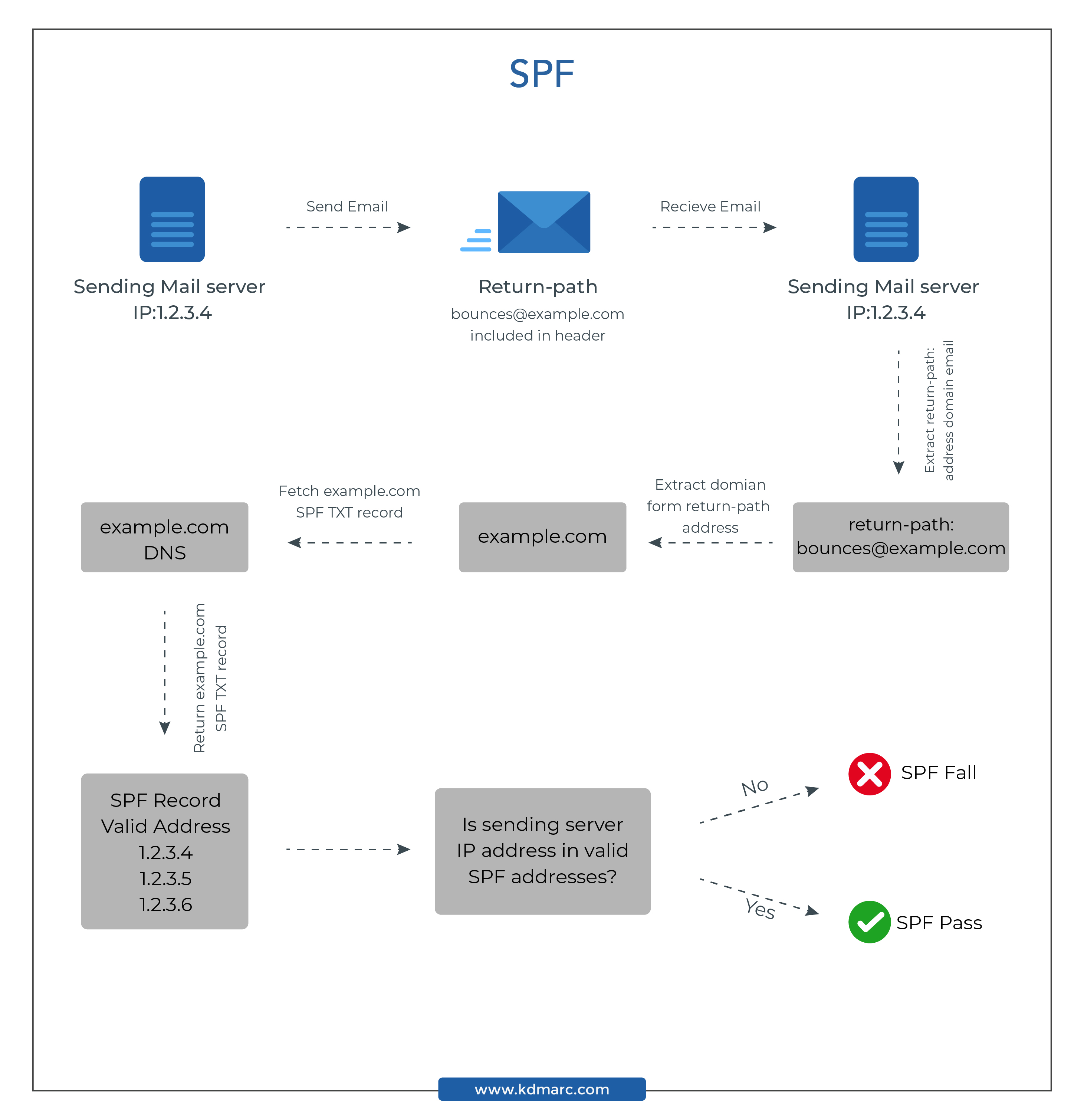
How does DMARC Work?
DMARC is used in combination with SPF and DKIM to authenticate an email and determine what to do if the email is from an unauthorized source. The email sender’s DMARC record instructs the email recipient on how to deal with the unauthorized email (for eg. spoofed email) according to the specific enforced policy.
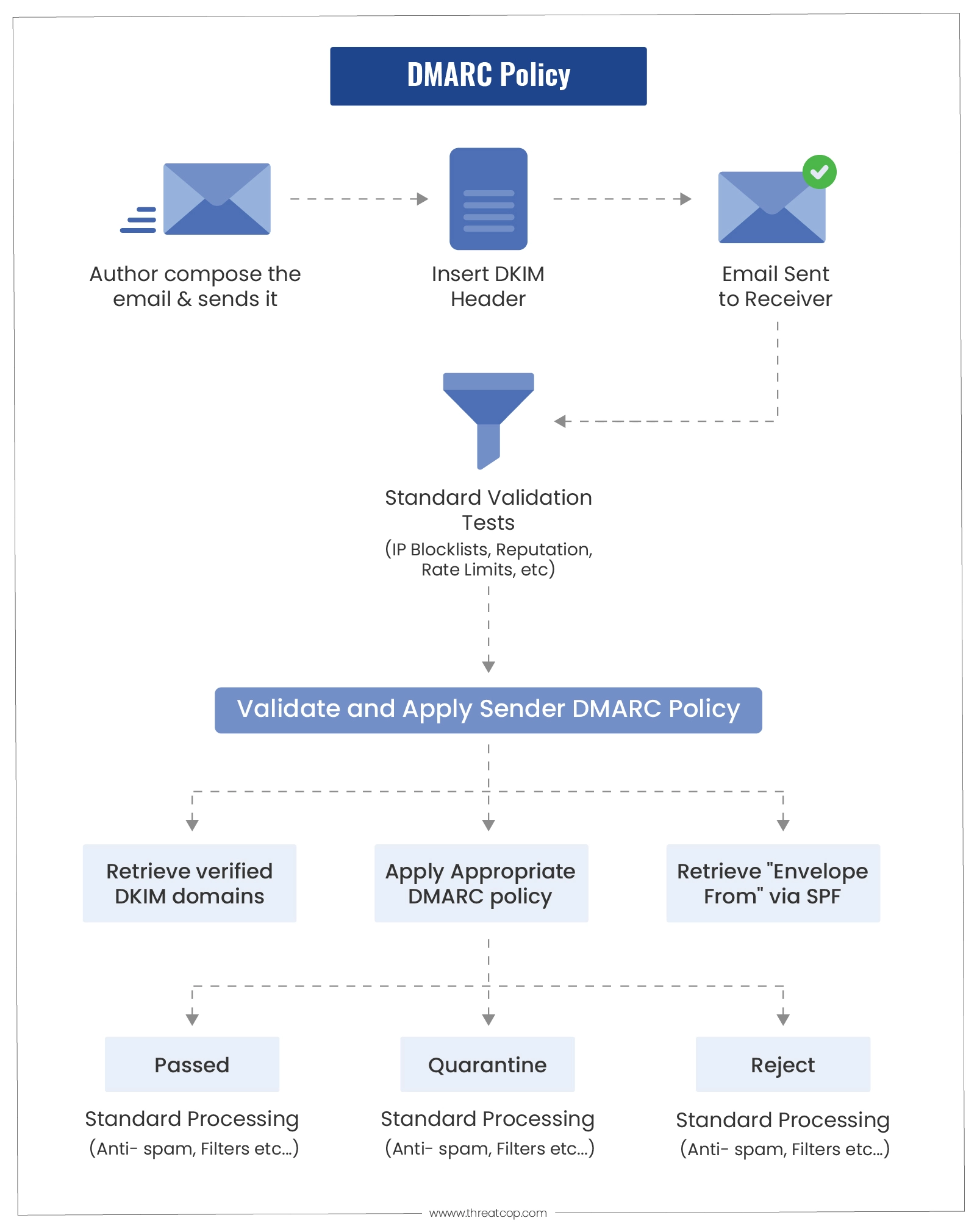
This is the stepwise procedure of how DMARC works:
- The email domain owner publishes a DMARC DNS record.
- When an email is sent from the sender’s domain or the sender’s spoofed domain, the receiving mail server checks for the domain’s DMARC record.
- The receiving mail server then checks for DKIM and SPF authentication and alignment to verify whether the sender’s domain is legitimate by looking for:
- Validated DKIM signature
- Sender’s IP address matches with the senders in the SPF record
- Sender’s domain alignment test to verify the message headers
During the verification of DKIM and SPF, the receiving mail server applies the sender domain owner’s policy (None, Quarantine, or Reject), based on the verification results.
Later, the receiving email server sends a report to the sender’s email server. The report contains a verification analysis of the email received on behalf of the sender’s domain.
These reports are called the DMARC Aggregate Reports and are sent to the specified email address or addresses in the domain’s DMARC record. DMARC allows the organizations to determine the procedure for emails that failed the DMARC checks. They can define a policy in their domain’s DMARC record.
Once all these details have been checked, the ISP determines whether an email is DMARC failed or DMARC compliant.
Notably, email receivers aren’t obligated to follow the policy set by you. Sometimes, they can override DMARC policies with a local policy in case they have reason to doubt the legitimacy of an email. So, an email that has failed the DMARC authentication can still land in the recipient’s primary inbox even if you have enforced the reject policy.
Email Authentication Standards
Email authentication is a technical methodology that is implemented with SMTP to make sure that email is not forged. It provides a layered approach to verifying the genuineness of emails. The purpose of the authentication standard is to block and prevent malicious or fraudulent emails that could possibly lead to BEC attacks or phishing attacks.
The most popular and widely used email authentication standards are Sender Policy Framework (SPF), Domain Keys Identified Mail (DKIM), and DMARC.
Statistics on Email Attacks and DMARC
All the statistics presented below are sourced from ‘Global DMARC Adoption Report, 2019 on the 250ok platform, and the “DMARC Industry Report” by Kratikal.
- Only 113 out of Fortune 500 (23%) companies have implemented DMARC, irrespective of whether they are the highest revenue companies.
- The most unsecured segment in the travel industry, where 1% of domains have a reject policy and 86% of domains have no policy.
- 81.5% of all the domains of the executive branch of government have enforced a reject policy.
- The most significant progress was found among law firms, where DMARC implementation increased by 19% from 2018 to 2019.
- On a global level, 70% of all emails are suspicious.
- BEC Scams target over 400 businesses every day.
- On average, only 3% of the phishing mail is reported by employees in organizations.
- Employees in organizations report only 3% of phishing emails on average.
- Organizations incur losses of over $500 million after getting a victim of phishing attacks every year.
- During the end of 2018,
- According to a survey conducted by ENISA, 70% of respondents believe that spam is extremely significant from the perspective of security.
- In the same report, it was stated that 13% of data breaches between January 2019 and April 2020 were caused by malicious spam.
- ENISA also found that 58.3% of email accounts were spammed in the mining industry.
TDMARC is the Solution
From Statistics, it can be seen that organizations are most vulnerable if they haven’t implemented DMARC solutions for their email domains. Thus, DMARC provides additional security to email servers along with SPF and DKIM.
Though the concept of DMARC is well and clear from the blog, the concerns for organizations still persist regarding how to implement and configure DMARC rightly. This is where TDMARC helps. TDMARC is designed and developed to help organizations in deploying and configuring DMARC, DKIM, and SPF rightly.
TDMARC is a SaaS-based email authentication tool that helps organizations secure their outbound email flow and prevent the misuse of their email domain.
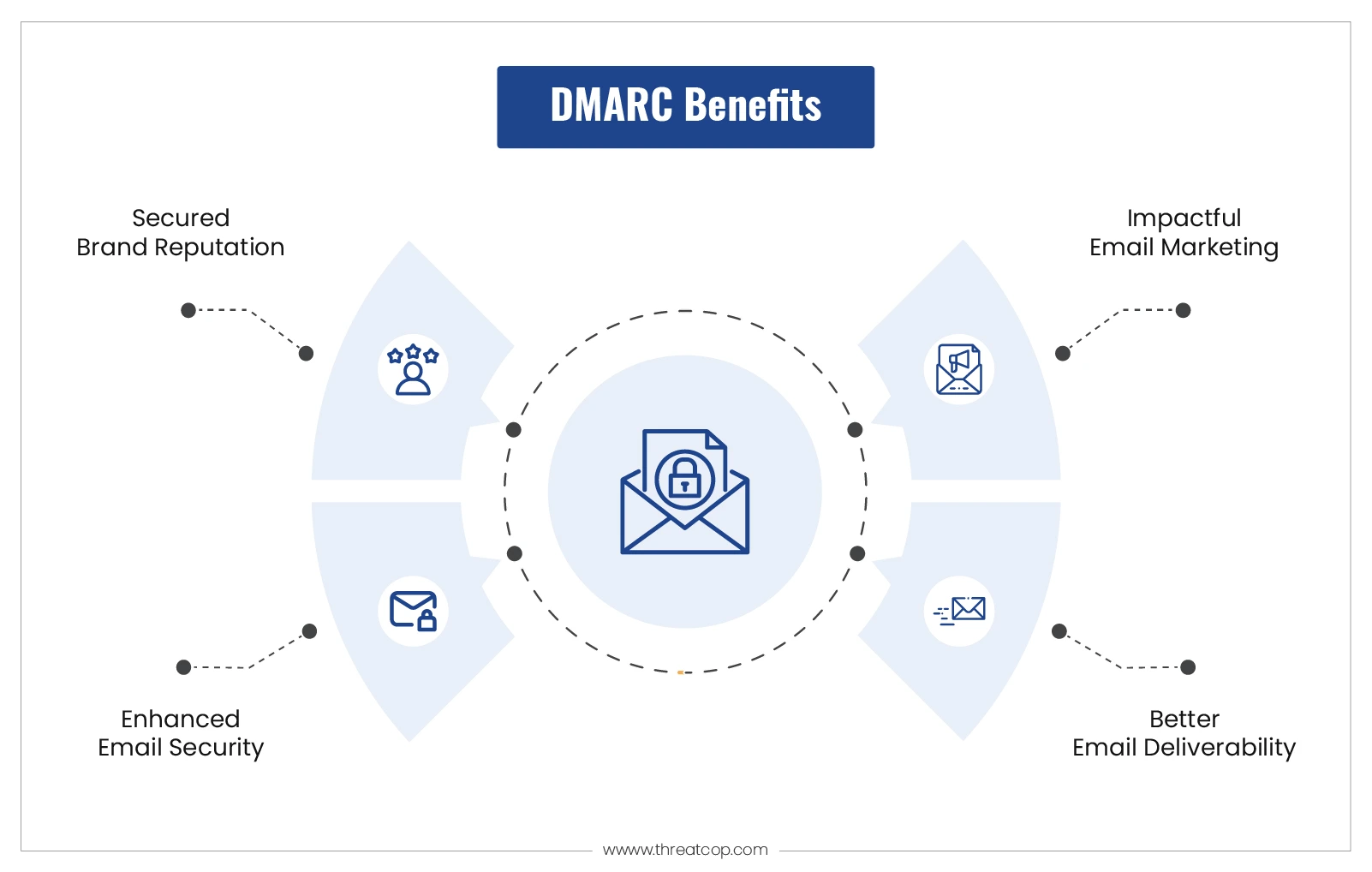
Not only this, TDMARC ensures that:
- Prevents email-based attacks
- Preserves brand reputation
- Improves email deliverability
- Boosts email engagement rates

Senior Writer
Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
Senior Writer Shantanu is an accomplished content strategist and technology enthusiast at Threatcop Inc. With a knack for translating technical intricacies into reader-friendly narratives, Shantanu contributes to making cybersecurity insights both informative and enjoyable for tech enthusiasts and general audiences alike.
