If you have already secured your domain with DMARC, you still have to make sure all the SPF, DKIM, and DMARC records are properly configured and the right DMARC policy has been enforced. While Reject is the strictest DMARC policy when it comes to security, it isn’t always the most suitable choice for your domain. In this blog, we’ll talk about when is the right time to switch to the Reject policy and what is the best way to do it.
Table of Contents
ToggleBut before we dive into that, let’s review the basics first.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What are the 3 DMARC Policies?
There are 3 DMARC policies available for you to choose from according to your email domain security needs.
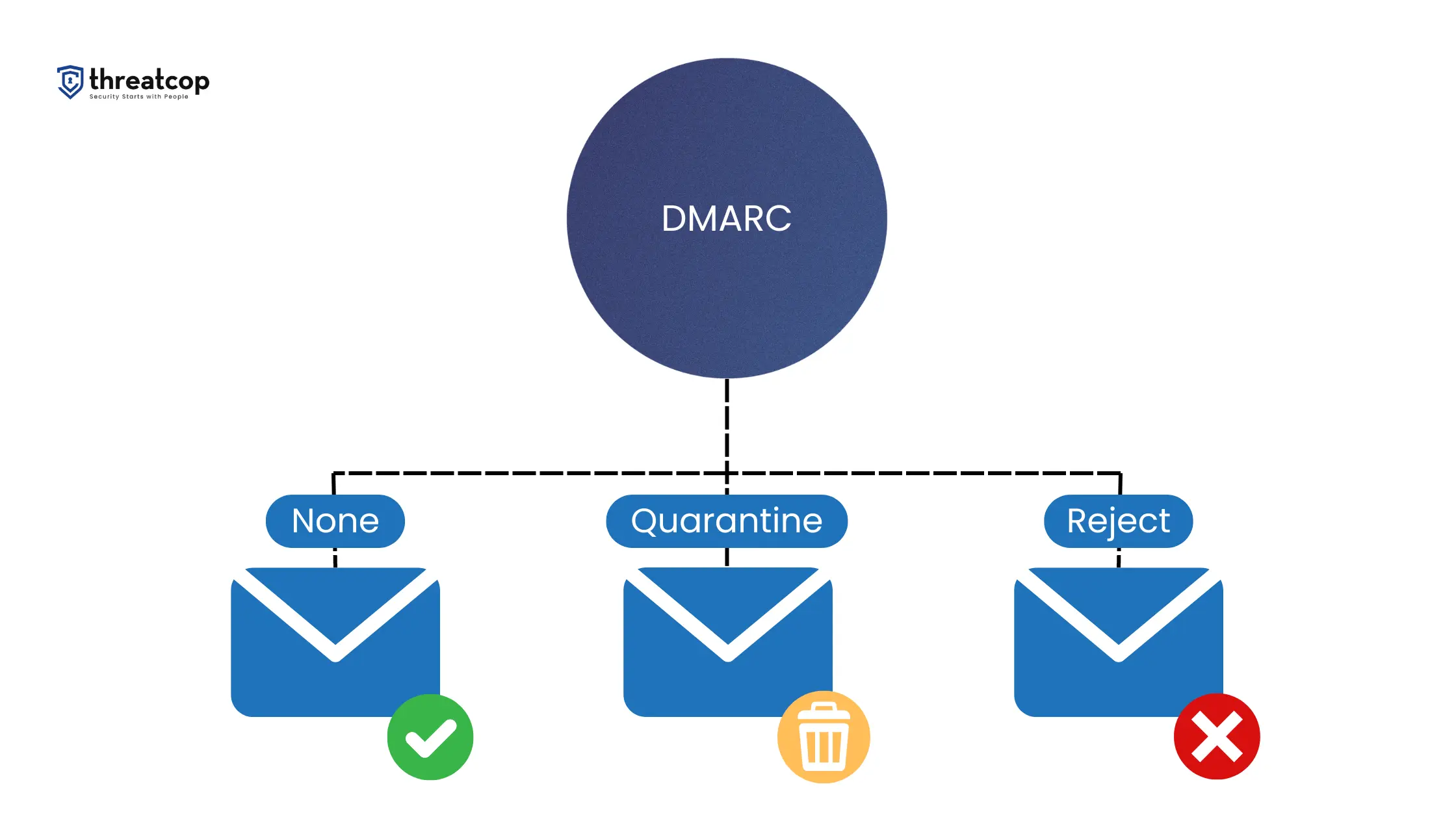
DMARC None Policy (p=n)
Also known as a Monitoring Only policy, it instructs the ISPs to send the reports to the email address published in the RUA or RUF tag of your domain’s DMARC record. Helping you gain deep insights into your email channel, this policy doesn’t affect email deliverability at all. It allows all emails to reach the recipient’s inbox, regardless of whether or not they are DMARC-compliant.
DMARC Quarantine Policy (p=q)
In addition to sending reports, this policy instructs the ISPs to redirect all the emails that fail DMARC authentication to the intended recipient’s spam folder. Emails that successfully pass DMARC authentication are delivered to the recipient’s primary inbox. While this policy helps in limiting the impact of email spoofing, it still allows spoofed emails to reach the receiver.
DMARC Reject Policy (p=r)
Apart from sending reports, this policy instructs the ISPs to completely prevent any email failing DMARC authentication from being delivered. Emails that successfully pass DMARC authentication are delivered to the recipient’s primary inbox. It effectively mitigates the impact of email spoofing by preventing all spoofed emails from reaching the recipient’s inbox.
When to Set DMARC Policy to Reject?
Before you decide to set your DMARC policy to either reject or quarantine, it is essential to have insights into your email channel. Enforcing the DMARC None policy is the best way to gain the necessary insights. For this reason, it is highly advisable to start your DMARC deployment process with the ‘none’ policy. This will allow you to work on correctly authenticating all the sources that are authorized to send emails on behalf of your organization.
Once all the authorized sources have been properly authenticated and their DMARC compliance has reached around 100%, you can enforce the reject policy. This will help in preventing low deliverability rates for legitimate emails. It is recommended to switch your DMARC policy to reject in small steps by using the percentage tag (pct) in the DMARC record. This will minimize the risk of reduced email deliverability and maximize the chances of successful delivery of legitimate emails.
Book a Free Demo Call with Our People Security Expert
Enter your details
How to Set DMARC Policy to Reject?
If you feel you have reached the stage where your domain is ready for the reject policy, here is a step-by-step guide to help you switch your DMARC policy to reject.
Step 1: Start DMARC Monitoring
First, start monitoring your domain by deploying DMARC. Once you have implemented DMARC, ISPs send DMARC reports to the email address published in your DMARC record every day.
Two Types of DMARC Reports
There are two types of DMARC reports sent by the ISPs- Aggregate (RUA) and Forensic (RUF). Here is some information about these reports.
Aggregate Reports (RUA)
Aggregate reports are sent to your email address every day for providing a detailed overview of your domain’s email traffic. These reports include a list of all the IP addresses that have attempted to send emails using your domain name.
Forensic Reports (RUF)
Forensic reports send you real-time alerts in case emails sent from your domain fail to deliver. These reports always include original message headers and may include original messages.
While monitoring your domain with DMARC in the initial stages, make sure to set your DMARC policy to None. This ensures that you receive DMARC reports without any effect on your mail flow.
Step 2: Continue the Analysis of DMARC Reports
Stay on None policy for a while and use that time to configure your domain’s SPF and DKIM records. In the meantime, keep an eye on all the DMARC reports you receive. These reports will inform you about which DKIM selectors are used and which senders are sending emails from your domain. They also show how many of your emails are passing and failing DMARC authentication.
Make sure your SPF record includes all of your legitimate senders and nothing extra or unnecessary. Don’t forget the importance of SPF flattening and make sure the number of DNS lookups doesn’t exceed 10. Use a different DKIM selector for each sender and only include selectors that are in use. Make sure your DKIM keys are secure and periodically changed.
Step 3: Switch Your DMARC Policy to Quarantine
Once your SPF and DKIM records are configured properly, you can consider changing your policy to Quarantine. This policy causes all of your unauthenticated emails to be redirected to the recipient’s spam. While deciding whether or not you are ready for the Quarantine policy, take into account the type and number of emails that would be affected by the change.
For instance, if a large number of emails being sent to customers and partners are failing DMARC authentication, it might not be the right time for you to switch to quarantine. Whereas, if only a small number of promotional emails are failing authentication, you might be ready for the switch. Depending on your priorities and mail flow, the readiness to enforce the quarantine policy can vary from domain to domain.
As mentioned before, it is highly advisable to set the policy in small steps by adjusting the percentage of emails for which the ISPs enforce the quarantine. For example, you can begin by setting the pct tag in your DMARC record to 5%. This means that only 5% of the unauthenticated emails will be redirected to spam. You can then slowly increase the percentage to 20% after making the required changes in the SPF and DKIM configurations. Doing this will allow you to ease into the quarantine policy without any major loss of legitimate mail flow.
Step 4: Switch to Reject Policy
Once you are sure that your transition to quarantine has been completed and that very few of your emails are landing in spam, it’s the right time to switch to the Reject policy. When enforced correctly, the Reject policy should not affect your email flow. Just keep in mind that this policy completely blocks out the unauthenticated emails.
If any of your emails are still landing in the recipients’ spam, you shouldn’t switch your DMARC policy to Reject. It is recommended to switch to reject in small steps using the percentage tag, just like with quarantine. Once you are sure that most of your important emails are reaching the recipients’ primary inbox, you can switch the DMARC policy to full reject.
Is Reject Policy Always the Right Choice?
Regardless of how accurately and carefully you authenticate your valid sources, it is very rare for an organization to achieve 100% DMARC compliance on all the valid sources. Very often, a small percentage of the emails sent from valid sources fail DMARC authentication. This means that at least a few of the legitimate emails sent from your domain will be blocked when you switch the DMARC policy to full reject.
While switching to a full reject policy might result in the loss of a few legitimate emails, it is also very important for organizations to fully secure their email domain against impersonation and abuse. The adverse impact caused by the failure of delivery of a legitimate email is still much lower than the effect caused by a malicious email being delivered successfully.
However, this is not the case for every organization. There are certain companies that need to prioritize deliverability over security. In these cases, it is recommended to at least set your DMARC policy to a full quarantine. Doing this will not only lessen the impact of a malicious email slipping through but also make sure that all your legitimate emails are reaching the recipient, even if they sometimes land in spam.

In a Nutshell
If the security of your email domain is a priority for you, it is a good idea to enforce the Reject policy. Before taking any action, ensure that your SPF and DKIM configurations are at a point where the policy will not affect your deliverability. Make sure you follow all the steps given above carefully to ensure maximum email deliverability as well as strong security.
You can implement a DMARC deployment tool like TDMARC to make the entire process much easier and hassle-free. Packed with an array of dynamic features like Smart SPF, Smart DMARC, Smart BIMI, and Automatic SPF Flattening, TDMARC can help you easily configure your domain’s SPF, DKIM and DMARC records.
To mark Cybersecurity Awareness Month, Threatcop collaborated with 31 respected CISOs and CTOs from prominent organizations. Together, we’re working towards a safer digital future.

Explore Here: 31 Cybersecurity Awareness Ideas from Security Leaders
Co-Founder & COO at Threatcop
Department: Operations and Marketing
Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop’s mission to safeguard people’s digital lives.
Co-Founder & COO at Threatcop Department: Operations and Marketing Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop's mission to safeguard people's digital lives.
