A ransomware attack disrupted business activities at Swiss-Robotic and automation major, ABB Ltd. The industrial tech behemoth confirmed on May 12, 2023, that they have suffered from an “IT security incident” that has obstructed some of its operations and systems worldwide. However, ABB claimed that most of its “systems and factories are now up and running, and ABB continues to serve its customers securely.”
Table of Contents
ToggleThe company has a variety of customers which consists of the government, Volvo, Hitachi, DS Smith, the City of Nashville, and the City of Zaragoza. ABB’s vast business empire develops SCADA systems for manufacturing and energy suppliers and industrial control systems (ICS). Being a significant part of the manufacturing system, ICS is an easy target for state-sponsored and financially motivated threat actors.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
How ABB Became a Victim of Ransomware Attack?
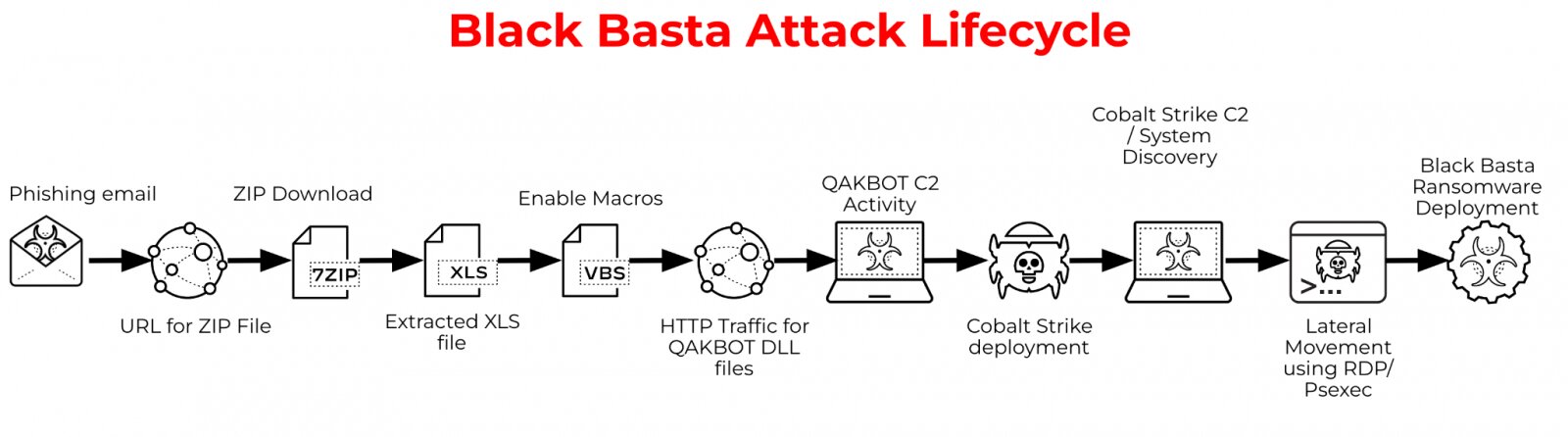
On May 7, 2021, the alleged Black Basta ransomware group conducted a series of phishing campaigns to deceive employees into downloading malware files. Unfortunately, one of the company’s employees fell victim and downloaded the malware file. Once downloaded, the malware executed an XLS file containing VBS macros. These macros established unauthorized access to Cobalt Strike, a remote tool used to execute commands.
Subsequently, the hackers gained access to the system’s database. According to standard reports, this malware attack impacted ABB’s Windows Active Directory, exposing numerous systems across different locations. As a result of this breach, several projects and business operations experienced disruption and delays.
Check out another article on Ransomware as a Service (RaaS) attack
Is Black Basta Behind the Attack?
Bleeping Computers reported that the tech giant has fallen victim to a ransomware attack led by the Russia-linked cybercriminal group Black Basta. Anonymous sources confirmed that the Black Basta ransomware group targeted ABB on May 7, as reported by the news outlet.
The attack impacted multiple devices and Windows Active Directory, but ABB assured that it has terminated VPN connections with its customers to prevent further attacks on other networks. No reports have indicated that Black Basta has demanded a ransom or that any data from ABB has been observed on the dark web.
ABB’s Take on the Attack
According to ET CISO, ABB’s Group Spokesperson, Eike Christian Meuter, acknowledged that the company has implemented and is actively implementing actions to control the incident. These measures have caused some disruption to their operations, but ABB is actively addressing the issue. They are working closely with customers and partners to resolve the situation and minimize the impact of the attack.
Who is Black Basta Ransomware Group?
Alleged to be a Russian-linked cybercriminal group, Black Basta first appeared in 2022. The group has already targeted more than 90 high-profile organizations like Deutsche Windtechnik, American Dental Association, Deutsche Windtechnik, and Capita. The hacker group coerces victims into paying a ransom by using the double extortion method. Employing this technique, cybercriminals frequently expose compromised data in pieces, enticing the victims to buckle under pressure from both internal and external sources.
Ransomware attacks are among the costliest cyber attacks, as the statistics suggest that the cost of a ransomware attack is expected to grow exponentially to 231 Billion dollars by 2031. Organizations need robust cybersecurity measures at the moment. They must protect their systems and networks from potential malware and cyber threats.
Organizations must incorporate sophisticated ransomware simulation and awareness solutions to train their employees to prevent such attacks. Effective awareness training can transform your employees into the strongest defense in the organization, as it empowers them to recognize and resist phishing emails that attempt to lure them into downloading malware files.
This July, we’re in the midst of Ransomware Awareness Month, an international campaign that highlights the dangers of ransomware and educates individuals and organizations on how to defend themselves. The timing of your interest in Black Basta coincides perfectly with this important initiative.
Organizations can significantly improve their security posture by implementing sophisticated ransomware simulations and awareness training for employees. Effective training empowers employees to recognize and resist phishing emails that attempt to lure them into downloading malware, making them the strongest defense against these attacks. Threatcop offers a TSAT solution that provides ransomware simulation to make your employee as first defense.
Book a Free Demo Call with Our People Security Expert
Enter your details
Threatcop’s Threat Simulation and Assessment Tool (TSAT) goes beyond traditional training methods. TSAT simulates real-world ransomware attacks, placing your employees in scenarios they might encounter. This hands-on experience allows them to practice identifying suspicious emails, attachments, and websites.
FAQs: Ransomware Attack on ABB
Ransomware as a Service (RaaS) is a collaborative business model that involves a partnership between ransomware operators and affiliates. In this model, affiliates pay to utilize ransomware attacks developed by operators. Ransomware as a Service can be considered a derivative of the software as a service (SaaS) business model. The most common attack that takes place through this is Phishing emails.
Pay-now-or-get-breached or Double-extortion is a method used by hackers to take ransom from the victims in bits. The threat actor first encrypts the stolen private data and then threatens to publish the information if said amount is not paid to him by the victim. They threaten victims to publish their data in the public domain or sell it to other companies at higher prices if the victim fails to pay the requested ransom.
To prevent ransomware attacks, an organization should focus on strengthening the cyber security level of the systems and train its employees against cyber attacks. Providing regular Ransomware Awareness and Simulation training can turn your employees into cyber attack defenders and create a cyber-secure environment. This helps in equipping them with the knowledge and skills with a real-time ransomware simulation campaign. Humans can be the weakest link in an organization therefore training them regularly to have the skill set to acknowledge any cyber attack can be the best prevention from the social engineering attacks.
