Ransomware as a Service (RaaS) is more than just a cybersecurity issue—it’s a lucrative criminal business model. In 2025, RaaS will continue to be one of the major threats affecting businesses, governments, and critical infrastructures. What differentiates Ransomware Service from any other cyber threat is the accessibility of being able to perpetrate an attack without technical expertise. A cybercriminal can simply subscribe to a RaaS platform and attack as a user of the platform.
Table of Contents
ToggleWhat Is Ransomware as a Service (RaaS)?
Ransomware as a service (RaaS) is essentially software-as-a-service (SaaS) for cybercriminals. Instead of having to build their malware, attackers can now buy or subscribe to ready-made ransomware kits that are available online with step-by-step guides and technical support.
Hosted on the dark web, Ransomware services offer a user-facing dashboard, service plans, updates, potential features to be added and user ratings to evaluate the performance of previous users. Such a model eliminates the requirement of coders, making ransomware attacks far more prolific and devastating.
How RaaS Differs from Traditional Ransomware?
Separation of Developer and Attacker: In conventional ransomware, the perpetrator is both the developer and the attacker. In Ransomware as a Service (RaaS), developers (or operators) create the ransomware platform and affiliates (or attackers) do the attacking.
Service-Based Model: RaaS operates similarly, providing a SaaS product with a pre-made kit, user dashboard and customer support.
Scalability: Affiliate capabilities allow them to attack numerous victims through the same platform, allowing RaaS to become enormously scalable as well as broadly distributed.
Specialization: Operators work within the confines of coding and improving the platform. Affiliates focus solely on targeting and infecting victims.
Profit-Focused: RaaS is a fully functioning underground economy where profit is traded, services are marketed and there is innovation and competition.
Book a Free Demo Call with Our People Security Expert
Enter your details
The RaaS Business Model (Explained Simply)
In the RaaS model, developers function like software companies. They create and host ransom kits that come complete with encryption and decryption, affiliate management sites, leaking sites and tech support. Affiliates pay and sign up based on one of several business models.
The RaaS ecosystem has tutorials, SLAs, support channels and even bug bounty programs—very much like legitimate SaaS providers. Cybercrime is now not a prediction, it is the present in the contemporary threat landscape.
Understanding the Business Models of Ransomware-as-a-Service
Ransomware as a Service (RaaS) is also a business. It employs subscription-based and/or tiered services, revenue sharing—in short, developers can monetize their malware, and affiliates can attack with whatever skill and war chest they can muster.
Here are the prevalent models used to build this underground economy:
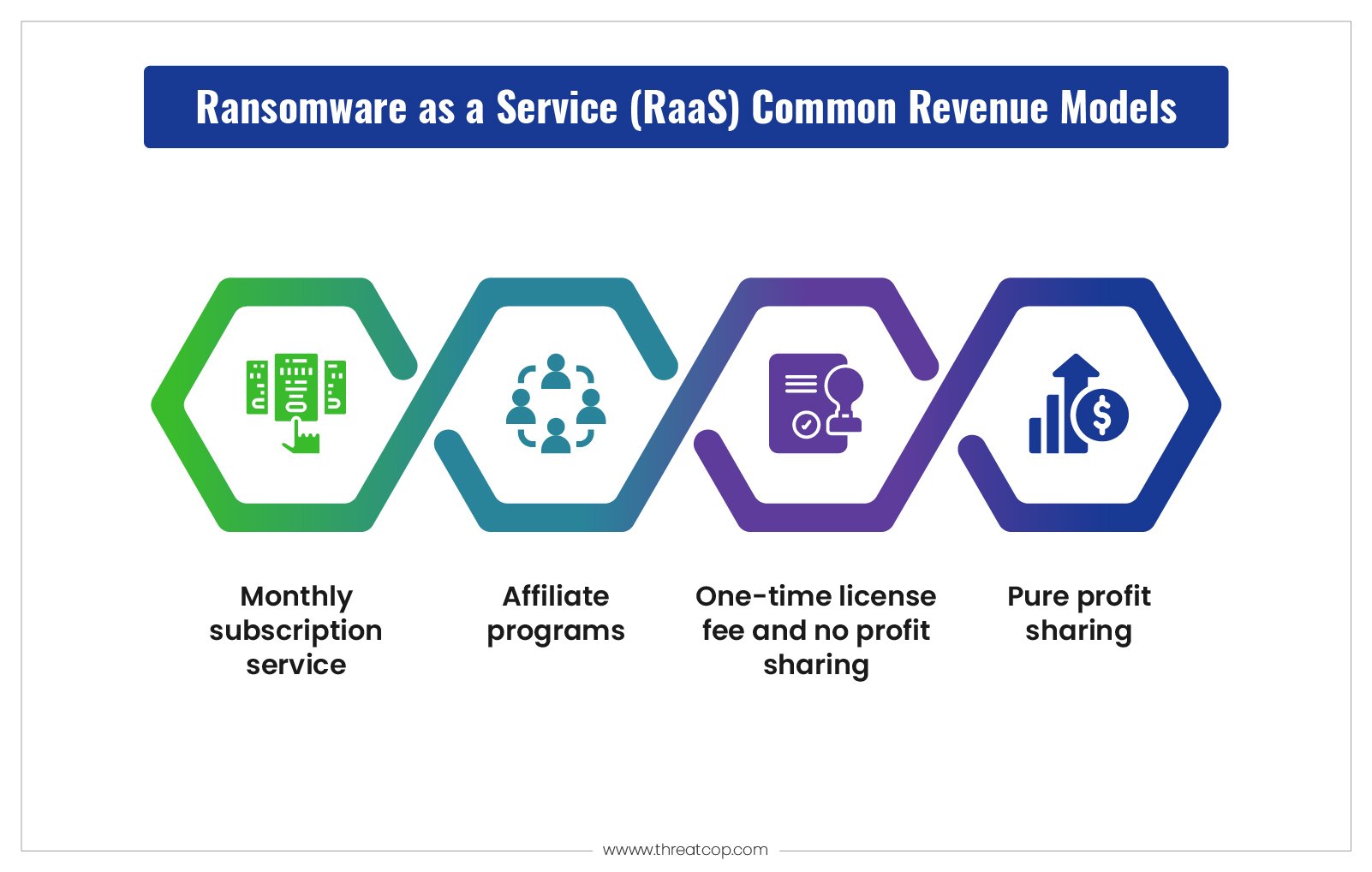
Monthly Subscription Model (SaaS Model)
- How it works: building a community taking constant ($$) monthly payments to access ransomware platforms
- Business model: 24/7 support, tutorials, tech upgrades
- Example: BlackCat/ALPHV offers explosion wizards, support mechanisms and user interfaces.
- Why it is harmful: By making access affordable and scalable for entry-level criminals, it accelerates the pace of attacks on targets.
Affiliate Revenue Share Model
- How it works: Affiliates receive a share of revenue profits from developers (usually 70/30 or 80/20)
- Business model: Dashboards, encryption tools, access to leak sites
- Example: LockBit followed this model and was the most active ransomware group.
- Why it is dangerous: Low entry barriers + easy low-skill profits = more attacks being performed by low-skilled criminals.
One-Time License Model (Pay Once and Use Forever)
- How it works: Pay now to use the ransomware kit for a lifetime (pay once)
- Business model: No revenue share – buyer has complete control over the ransomware
- Example: This method is used for Dharma ransomware often.
- Why it is effective: This option is best suited for advanced criminals or insiders who want full control.
Partnership/Profit Split Model
- How it works: Developers and attackers split profits upon successful attacks.
- Business model: Jointly planned, shared resources, co-led leak sites.
- Example: Conti executed this model as a hybrid RaaS group in 2021/22.
- Why it is effective: Higher quality attacks, better infrastructure and bigger profits.
Real-World Examples of RaaS in Action
These extreme examples help illustrate how RaaS transforms cybercrime into an unintended model for a “repeatable” business process, with global consequences.
- Colonial Pipeline (DarkSide): A national fuel shortage; $4.4 million ransom paid.
- Costa Rica (Conti): Disruption of an entire government; an emergency was declared nationally.
- JBS Foods (REvil): $11 million ransom paid to one of the largest meat suppliers in the world.
- MOVEit (Cl0p): Over 2,000 victims, including the BBC, Shell and various U.S. government agencies.
- Eldorado (2024): A New RaaS group that is utilizing RDP exploits and is under the monitoring of CISA.
These instances illustrate how much movement there is with RaaS attacks and the vast variety of damage that they can incur, from critical infrastructure and food supply chains, right through to national services.
What Are Some Notable Examples of RaaS Attacks?
RaaS affiliates work as a team, from the initial access step that begins with phishing or stolen credentials, to the final step that includes public data leaks, all while applying pressure to the victims.
Let’s look at how many of these attacks would work:
- Initial access – phishing emails, stolen credentials, access broker acquisition through Initial Access Brokers (IABs)
- Speed of encryption – LockBit and BlackCat both outrun defenses by quickly encrypting the data
- Leak tactics – groups like Cl0p apply pressure by directly publishing data leak sites and forcing the victim to decide whether they wish to expose their sensitive data.
How RaaS Attacks Work Step-by-Step?
Ransomware as a Service (RaaS) attacks are scalable and repeatable processes that have been designed for both speed and profitability. Affiliates don’t have to possess highly technical skills, they just need access, a target and a kit for their infrastructure.
Here’s a typical sequence of events for RaaS:
- Access: Affiliate buys RaaS kit and identifies the target.
- Infiltration: Escape identifies access into the system via phishing, compromised accounts, or through IAB.
- Execution: The Affiliate executes the ransomware and the ransomware encrypts the data.
- Exploitation: Victims receive notification through a ransom note, threats include notifying third parties about the aforementioned breach or leaking of data.
- Profit: Victim pays in cryptocurrency; RaaS platform takes a cut.
Notable RaaS Groups in 2024
RaaS groups have grown and developed many organizational structures, different types of attacks and varied attack groups. Each group has its specialization designed to maximize revenue through ransomware attacks. Below are some of the major RaaS groups in 2024, along with the way they conduct their attacks and who they typically target.
Group | Highlights | Techniques |
LockBit | Fast encryption, huge affiliate base | EDR evasion, double extortion |
BlackCat | Rust-based, cross-platform | Leak sites, advanced UI tools |
Cl0p | Exfiltration-first approach | Used in MOVEit, Accellion, and GoAnywhere hacks |
Eldorado | 2024 entrant, targets RDP | Remote admin tools, phishing |
REvil | Legacy group, tactics still copied. | Multi-country attacks, deep negotiation |
Conti | Hybrid RaaS/partnership model | Co-planned targets, extensive infrastructure |
What Measures Can Organizations Take to Protect Against RaaS Attacks?
Detection & Response scenario
- Use EDR (Endpoint Detection and Response) to quickly contain threats.
- Use NDR (Network Detection and Response) to detect and contain lateral movement.
- Together, both EDR + NDR can be merged together to an XDR for full attack context and visibility.
Access & Identity Security scenario
- Use MFA (Multi-Factor Authentication) on all accounts.
- Use PAM (Privileged Access Management) to limit admin exposures.
- Use geofencing to block users from areas of high risk.
Backup & Recovery scenario
- Use offline backups or make sure you use immutable backups to ensure clean recovery.
- Practice backups regularly and have an automated plan for failover.
- Make sure backup systems are not co-located in production environments.
Surface Management scenario
- Patch key software and firmware such as MOVEit and Cirtix.
- Regularly scan your services for exposed services and misconfigured assets.
Employee Readiness scenario
- Conduct phishing simulations quarterly.
- Prepare staff for urgent fake IT alerts and fake IT invoices.
- Test plans with red team and purple team exercises.
Incident Response Planning scenario
- Procure an IR firm ahead of time, as a partner.
- Conduct tabletop drills based on common RaaS model attacks.
- Compile contact lists of legal, compliance, cyber insurance and the FBI.
Legal and Regulatory Implications
Ransom payments may violate OFAC rules if the attackers are sanctioned. The U.S. Department of Justice and FBI recommend reporting groups rather than paying them. The website StopRansomware.gov provides information on real-time alerts and best practices.
- Globally, law enforcement actions have been executed:
- Hive was shut down in 2023.
- Ragnar Locker infrastructure was taken down in 2024.
Conclusion
Ransomware as a Service has turned ransomware into a professionalized cybercrime industry that is globally scalable. It has also grown in sophistication and reactive defenses are no longer sufficient.
The best course of action is a layered approach. Utilize EDR, NDR, and XDR, along with MFA, regular backup and user training. Build and instill a security culture in your organization, stay up to date on threat intelligence and regularly exercise incident response!
Only then will you be able to stay ahead of the next evolution of RaaS.
FAQs: Ransomware as a Service (RaaS)
Ans: No. That’s what makes RaaS so threatening, you don’t need any coding skills or knowledge of cybersecurity to utilize RaaS. RaaS platforms give you fully functional ransomware kits, user guides, RaaS dashboards, and technical support, simultaneously making it easy to attack an organization without coding or a technical background.
Ans: Most RaaS platforms exist on the dark web, which is a hidden part of the internet that requires special software like Tor to navigate and find the RaaS services. RaaS types of services, some would be advertised in underground forums and would typically require some vetting process or an invitation to enter to avoid organizations like law enforcement.
Ans: RaaS attackers target a wide range of organizations, small businesses, large enterprises, health care systems, local and state government agencies, schools, and even critical infrastructure! No target is too small or too big. Their only motivation, a lot of times, is to attack targets that will be most likely to pay quickly, typically hospitals or municipalities with sensitive data.
