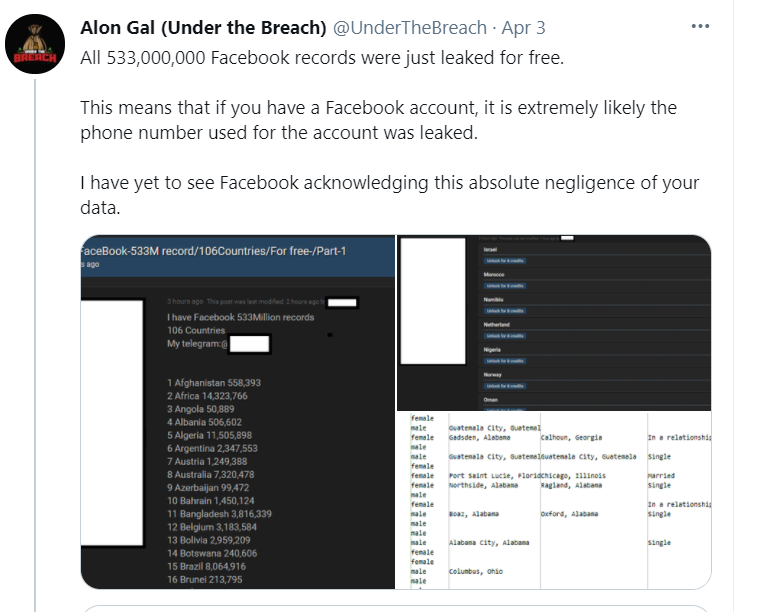
On April 3, 2021, the personal data of more than 500 million Facebook users globally was published on a low-level hacking forum for free. The leaked data includes full names, phone numbers, email addresses, birth dates, locations, and biographical information.
Table of Contents
ToggleThis data breach affected more than 533 million Facebook users from 106 countries across the globe, including over 32 million records of US users, 11 million users in the UK, and 6 million users in India. Reportedly, all the data is neatly divided into separate download packages by country.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What Did Onavo Protect Do?
Similarly, in 2018, Facebook was hit hard in the gut when it was forced to take down its mobile web analytics application, Onavo Protect, from the iOS App Store. Onavo, a Facebook-owned-Israeli-application, was not only found guilty of developing and using spyware that monitors users’ activities and also works as a data collection tool for recording data of the usage of other applications.

The app was found guilty of a data breach. it was capable of confirming whether a smartphone’s screen was on or off, the usage of cellular data in bytes and if Wi-Fi was being used or not. Onavo Protect was taken down from the iOS app store since it violated the iOS’ stringent guidelines that discourage the collection of data while using other apps. Onavo is still available on the play store and has been installed more than 10 million times.
What Does the Onavo Application Do?
The research application, christened ‘Project Atlas’ (in some of the documentation, helped Facebook in a data breach. It extracted personal data (over 30 attributes) by tracking smartphone users’ activities on multiple applications in order to comprehend users’ attitudes towards the third-party applications.
The application has also been placed in the bad books because of its invasive nature as it reads users’ messages in social media apps, non-e2e messages, web searches, as well as activities. It can pinpoint the user’s location as well. The application is so capable that, in many instances, data can even be collected from apps that use encryption.
Why was Facebook Blamed?
The confirmation of the attack came from Facebook, and they cited that ‘old data’ was leaked in the attack. And the vulnerability of this leak has already been patched in 2019. The exposed data was exploited by threat actors to carry out an array of cybercrimes, including identity theft, impersonation scams, SMS spam, and extortion attempts.
“A database of that size containing the private information such as phone numbers of a lot of Facebook’s users would certainly lead to bad actors taking advantage of the data to perform social engineering attacks [or] hacking attempts”
– Alon Gal, CTO of a cybercrime intelligence firm
Notably, this isn’t the first time that the personal information of Facebook users has been exposed online. The vulnerability uncovered in 2019 led to the exposure of phone numbers of millions of users from Facebook’s servers. Also, during the 2016 election, Cambridge Analytica scraped 80 million users’ data to target voters with political ads.
The National Privacy Commission (NPC) is currently investigating the large-scale data leak that has affected around half a billion social media users globally. Cybersecurity experts worldwide are urging Facebook users to secure their social media accounts immediately. All users are being advised to change their passwords and enable multi-factor authentication right away.
Read more about How to Keep Your Password Safe From Hackers?
Practices to Prevent Data Breaches
Data breaches cost organizations huge data and financial loss, which also causes damage to reputation. That’s why organizations need to follow some practices to ensure the prevention of data breaches.
Book a Free Demo Call with Our People Security Expert
Enter your details
Keep the Software and Hardware Updated
Cybercriminals can exploit and gain access to valuable data due to vulnerabilities created due to outdated devices or software. Keeping your systems and software up-to-date with the latest security patches and updates is essential to eliminating any exploitable vulnerabilities in your organization’s cyber security infrastructure.
Conduct Periodic VAPT
VAPT stands for vulnerability and penetration testing. Every organization should conduct VAPT on a regular basis to evaluate the level of vulnerability in their organization. Technology is advancing with each passing day, and with that, cyber threats will continue to rise. That’s why it is important for organizations to seek exploitable vulnerabilities. This allows the organization to patch the vulnerability and strengthen the security infrastructure.
Generate Cyber Security Awareness
According to the report by IBM, 24% of the data breaches occurred due to human error.
If the employees of your organization are not vigilant and cyber aware, then they can cause serious and unintentional mistakes, which could lead to data breaches and cyber attacks. The cybersecurity awareness training for employees could be highly effective and beneficial for not only educating them but also defending against different kinds of cyber threats.
Enable Multi-factor Authentication
Multi-factor authentication has become more prominent these days for account security. It is applicable and must be implemented across all the endpoints across the organization. It can prevent major breaches and unauthorized access to compromised accounts.
According to a report by Microsoft, enabling MFA blocks over 99.9% of automated account compromise attacks.
Enforce Strong Password Policy
Weak passwords allow cybercriminals to exploit the system and gain illegal access to the victim’s account. Organizations should ensure that their employees must put strong passwords on their accounts. The organization should inculcate it as a practice or a part of security policy. They must provide the necessary guidelines for password security, such as using a password that consists of a combination of upper and lower case letters, numbers, and special characters. Also, advise them to change their passwords every 90 days. Make sure they understand the risks of password sharing and using the same password across multiple platforms.

Facebook Response to the Attack and Voice of Experts
Mike Clarke from Facebook responded to the situation through a blog post where he showed an old dataset from 2019 that was leaked. He blamed advertising companies for using scraping methodology to intentionally break into the platform and scrape internet services. He also notified that this issue has been fixed and scraping data is no longer allowed.
Further, it was notified that a lot of data is stored with social media companies. One must be careful about the data they give out to these platforms. Also, the organization must be very cautious about different attack vectors that could lead to data breaches.
