Cybercriminals can exploit the Domain Name System (DNS), a trustworthy and frequently used system on the internet. However, threat actors use it as a weapon and it is called DNS tunneling. DNS tunneling allows hackers to carry out their attacks through the DNS. Without it, we would never have been able to find websites on the Internet. It simply translates human-friendly URLs to IP addresses.
Table of Contents
ToggleDNS tunneling allows attackers to collect sensitive data from the website. Let’s first discuss what is DNS tunneling and how it operates.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is DNS?
The Domain Name System, or DNS, is an internet protocol that translates URLs to IP addresses. These IP addresses are machine-friendly, so you can access the websites you want. It is a global naming database. We would still be accessing websites using IP addresses with several dots in between if there were no DNS.
DNS allows you to find websites without remembering long number strings. Presently, we use smartphones to save simple 10-digit numbers, which our parents might memorize in a go. If we cannot remember these small numbers, IP addresses are way too confusing for a human brain.
Book a Free Demo Call with Our People Security Expert
Enter your details
DNS helps us convert these number strings into words we can remember, called domains. Therefore, companies also rely on and trust DNS traffic more than other protocols. One of the reasons is that the company wants its employees to reach external domains and external users to find their domains. Therefore, it is crucial for the company to allow this traffic through its firewalls.
However, once the traffic enters the firewall without any filtering, the process of DNS tunneling starts.
What is DNS Tunneling?
Even though DNS is a more reliable protocol, you cannot rule out the possibility of using it as a weapon. This reliability has itself given birth to the phenomenon called DNS tunneling. What does DNS tunneling do? It implements a command-and-control channel using DNS requests.
Once this command-and-control channel is established, it becomes easy for the attacker. It is no different than a friend taking advantage of your trust. Since you trust this person, you tell them everything, and then you realize that your “friend” is spilling the beans all over the place.
These command-and-control channels are set up to monitor your traffic so the threat computer can start extracting data and carrying commands from inbound traffic to the threat system. Data exfiltration is a process in which a malware or threat computer starts an unauthorized data transfer.
Now, DNS is a very flexible protocol. There are hardly any limitations to what kind of data can be sent since it is designed for finding website domain names. These requests go to the attacker’s DNS servers, which then respond with the corresponding DNS replies.
These DNS queries’ hostnames are prepended with payload data. with the help of the RDATA field of different DNS RR (Resource Record) types. The most commonly used DNS tunneling records are NULL, CNAME, and TXT records.
DNS Tunnelling History
The topic of DNS tunneling was originally brought up in the late 1990s, and by 2004. Ozyma DNS, one of the earliest tools for DNS tunneling, was created by Kaminsky. Since then, many more have been produced, but the fundamental approach has mostly not changed.
Now that you know what DNS tunneling is, let’s understand how it works.
How Does DNS Tunneling Work?
DNS tunneling exploits the DNS protocol by attaching malicious payloads to DNS responses. All the implementations are done through the client-server model. If you are looking forward to understanding how DNS tunneling works, keep reading.
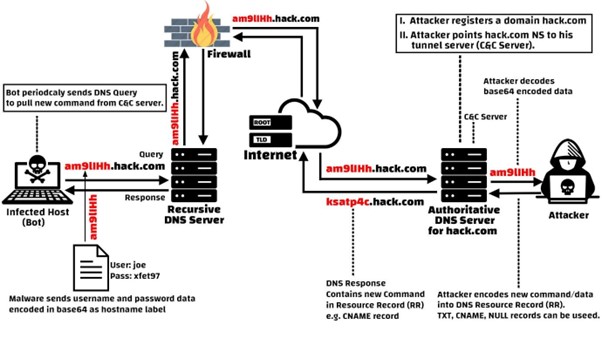
- The attacker first registers a domain like “abc.com.” This domain name is pointed toward the attacker’s server. On this server, malware/malware software is installed. This malware program is a tunneling malware that will do the job for the attacker.
- Once the systems are ready to carry out the attack, the attacker infects a system that is protected by firewalls. The malware affects the system and starts its work. As we mentioned earlier, DNS traffic is more reliable, firewalls allow such traffic to move inside the system and outside of it.
- This DNS query is sent to a DNS resolver that further relays the requests to root and top-level domain servers.
- Once the query is shot, the resolver will resolve the query and send the resolution to the attacker’s server. On this server, the tunneling malware is installed. Like a client-server model, a connection is established between the victim’s computer and the attacker.
- The tunneling software creates a tunnel through which all the information is either exfiltrated or malicious programs are supplied.
Recent Example
DNS Tunneling uses Morto and Feederbot Malware. The most recent example of DNS tunneling is an attack on government entities in the Middle East in 2018 from the DarkHydrus threat group.
SolarWinds was the victim of a highly sneaky cyber attack in 2021 that employed DNS tunneling to go unnoticed for 8 months. With this incident, SolarWind is currently expecting damages of over $90 million.
How to Prevent DNS Tunneling Attacks?
DNS tunneling is one of the most critical attacks in cybersecurity. This is because it leverages the reliability of DNS traffic to exfiltrate data from victim computers. Therefore, it is important to take a few preventive steps, so your data is safe, and you do not become a victim of DNS tunneling. Here are a few things you can do to prevent DNS tunneling.
Employee Awareness
One of the very first steps you need to take as a business entity is to educate and spread awareness. Cybersecurity is a critical subject, but awareness of these attacks is very low. Try and explain to your employees, clients, and other stakeholders its importance. Tell them what to expect and how they can make better decisions to prevent DNS tunneling attacks. Employee security awareness training is the first line of defense against cyber threats.
The more efforts are taken to create an aware environment, the more will be the chances of preventing DNS attacks.
Add Layers of Security
You might have assembled one of the best security teams for handling cyber attacks, but sometimes human error does play a role. Therefore, it is better to have an extra set of eyes through third-party tools. These tools are purposefully made to help you track and detect attacks that are sometimes invisible to the human eye. This is where the reliability factor can be eliminated since the machine treats all traffic the same, as a suspect.
DNS Filtering
Education is one thing; putting it into practice is another. DNS is a reliable protocol. We are repeating this because it is important to understand that DNS tunneling leverages the reliability factor of the DNS protocol. Due to this, the DNS traffic easily enters the firewall. It is, therefore, recommended that you use DNS filtering to ensure that only trusted traffic enters your network.
Here are a few things a good DNS filtering system should have:
- Ability to detect phishing attacks
- Filter traffic by comparing the domains to the list of malicious domains
- Detect and inform unusual DNS traffic patterns.
DNS filtering will also help you understand the traffic that is reliable or unreliable as it enters your network. Once you have the data and know the patterns, we can take the next step.
Behavioral analytics
One of the ways we distinguish between normal and abnormal human behavior is by figuring out a pattern. That’s how we know if someone is suspicious of us when they are sick or if they are having a heart attack. You can put this into play for your systems too. This is called behavioral analytics. You can use machine learning techniques and human monitoring in tandem to understand DNS traffic patterns.
If you do not know how normal DNS traffic looks, you will never be able to differentiate between unusual DNS requests.
Taking care of underlying scenarios
Once a connection is established between the victim’s computer and the attacker’s computer, DNS tunneling uses malware to hack a system and exfiltrate data. So, the first big step to preventing DNS tunneling is to take care of small things like installing anti-malware software, antivirus software, and firewall technology. So, it is best to invest in a DNS-specific firewall.
Once this is done, you can quickly identify illegitimate traffic and stop DNS tunneling from happening.
Final Thoughts: DNS Tunneling
DNS tunneling is a serious online security risk. It might have really detrimental effects. This is due to the cybercriminal’s usage of the tunnel for nefarious purposes like data exfiltration. In addition, there isn’t any direct connection between the target and the hacker. As a result, it makes it challenging to spot the hacker’s attempt.
Well, this is a lot to digest if you are someone who has never heard of DNS tunneling. But think about it. If you have someone or something that can take care of DNS attacks like a pro, that will make for an amazing teammate. DNS attacks are critical, and businesses should have a mechanism in place to tackle them. Not only that, but an aware environment can also help you keep your information safe and secure your IT assets from DNS attacks.
FAQs: DNS Tunneling
Data exfiltration and other illegal activities can be accomplished with DNS tunneling. It is more difficult to detect because there is no direct link between the target and the hacker.
DNS tunnels can be found by looking at a single DNS payload or by looking at traffic statistics like request count and frequency. Using a single request, malicious activity can be found via payload analysis.
Threat actors can gain remote access to a targeted server by compromising network connectivity with DNS tunneling techniques, for example. Threat actors may utilize further DNS attacks to bring down systems, steal information, direct visitors to phony websites, and launch DDoS operations.
