Imagine getting an email from your CEO asking you to urgently wire $100,000 to a vendor. You see their name, the tone feels familiar, and the request seems legitimate. You act fast, only to realize later that it wasn’t your CEO. It was a scam. This is what we call CEO fraud.
Table of Contents
ToggleThis fraud is an extremely targeted, elaborate scam that fools employees, particularly those in finance or HR, into wiring money or sensitive information. It falls under a larger category called business email compromise (BEC) and has resulted in billions of dollars being lost worldwide.
This article breaks down everything you need to know about CEO fraud, how it operates, real-life examples, identifying it, and, above all, how to prevent it.
Let’s get started.
What is CEO Fraud?
So, what is CEO fraud exactly? It’s a form of cybercrime where an intruder pretends to be a company executive, who most likely impersonates a CEO or CFO, and tricks an employee to send money or reveal private information. Criminals usually conduct an in-depth investigation of company hierarchies, business practices, and styles of relationships to make their scams convincing.
A CEO fraud attack usually follows a simple formula:
- Identify the target – The attacker scopes out the organization, often using LinkedIn or the company website.
- Craft the email – Using spoofed or compromised accounts, the attacker creates a believable request.
- Exploit trust and urgency – They manipulate the employee by creating a sense of urgency.
- Execute the fraud – Once the employee complies, the money is gone.
How CEO Fraud Works: Tactics Used
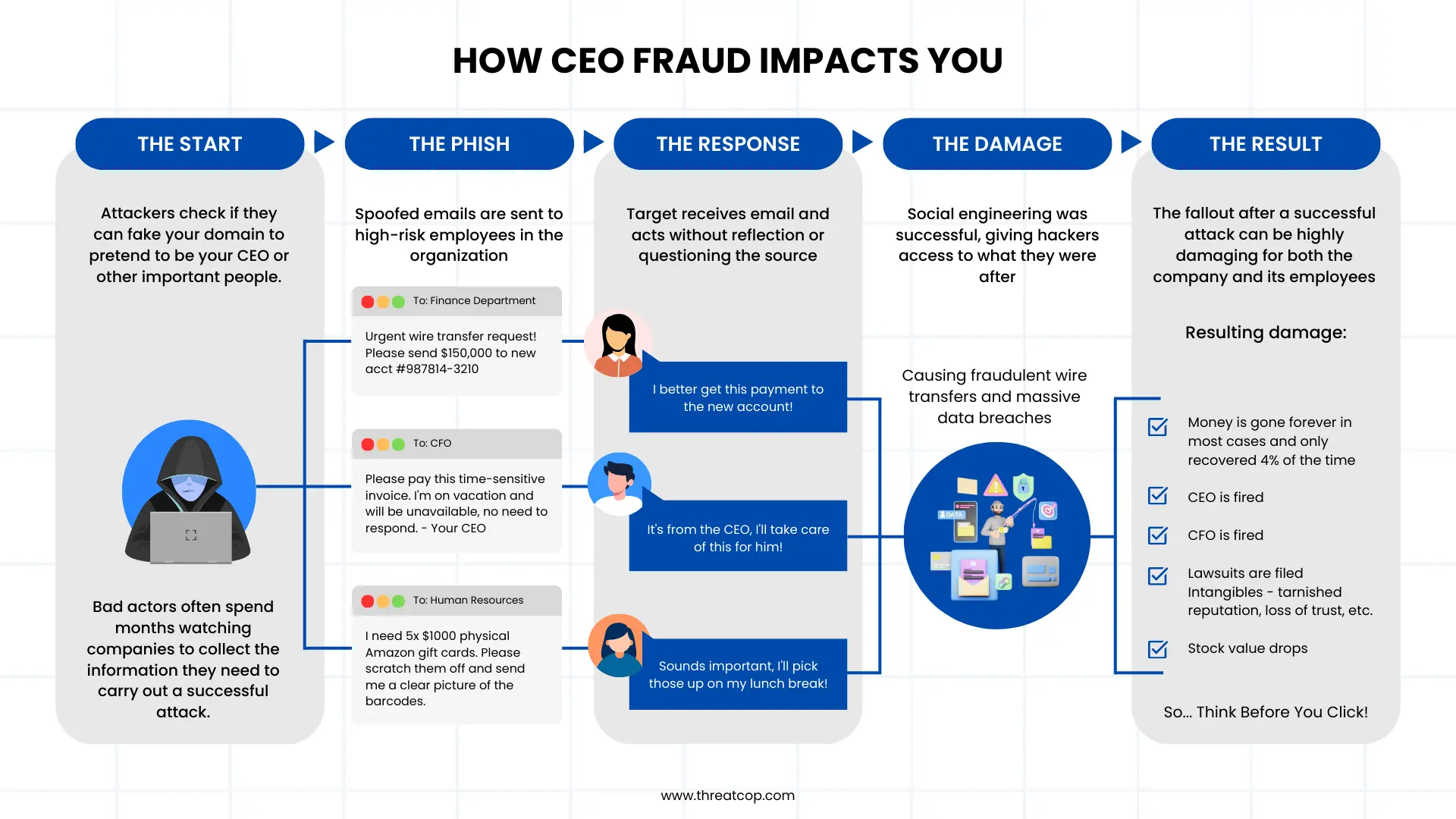
CEO fraud isn’t just about sending fake emails. It often involves a combination of tactics:
- Email Spoofing: The scammer creates an email address that appears to come from an executive (the email address may be hard to spot at first glance).
- Lookalike Domains: Using a domain like @yourcornpany.com instead of @yourcompany.com. A simple typo can trick even sharp eyes.
- Compromised Accounts: In some cases, attackers gain access to the CEO’s real email. This makes the scam much harder to detect.
- Social Engineering: They study employee behavior, company structure, and communication patterns. The more they know, the more convincing the fraud.
In short, it’s psychological manipulation combined with technical deception.
Spotting a CEO Phishing Email
Recognizing a CEO phishing email is the first line of defense. Here’s what to look for:
- Urgent language: Caution should be exercised when dealing with time-sensitive emails, as in the case where an email reads “I need this done ASAP” or “This is very urgent”. Scammers engineer urgency to bypass logical reasoning.
- Unusual requests: If your CEO is suddenly requesting gift cards, wireless transfer, or sensitive employee information via email, it is probably a smart thing to check.
- Poor grammar or unusual tone: If you do not hear a message in your executive tone or if it contains unexpected wording, this is a red flag too!
- Suspicious email addresses: Always verify the email address of the sender. Sometimes it is just one letter off from the real email address.
- Requests for secrecy: Messages that say “keep this confidential” or “don’t discuss with anyone else” raise red flags right off the bat: Scammers want to isolate you.
If something feels off, it probably is. Trust your instincts and verify before acting.
Book a Free Demo Call with Our People Security Expert
Enter your details
Want to Stop This Fraud Before It Starts? Start with These Guidelines
Now that you know the risk, how can you protect your company? Let’s walk through essential CEO fraud prevention measures:
1. Multi-Factor Authentication (MFA)
An email and internal systems should require an MFA. This gives another layer of security, increasing the chance that the scammers will not be able to get in even with your password.
2. Verification Policies
Develop a clear policy that all (most importantly, Wire Transfers) financial requests must be verified by phone or in person, prior to being released for processing.
3. Security Awareness Training
Regularly train employees to recognize CEO fraud phishing attempts. Empower them to question and report suspicious emails without fear.
4. Simulated Phishing Campaigns
Perform phishing simulation attacks in your organization. This aids in the determination of employee awareness and ensures faster reaction when under pressure.
5. Email Filtering and Flagging
Utilize advanced email security systems that employ spam protection and policies to flag suspicious or spoofed emails. A banner to external emails is a quick reminder to stay vigilant.
6. Restricted Access
Keep sensitive systems and data on a strict need-to-know basis. The fewer people with access, the lower your risk of exposure.
7. Audit and Monitor
Conduct regular audits of financial transactions and monitor email traffic patterns. Anomalies like unusually large transfers or requests after business hours should trigger alerts.
Guidelines for Employees: What You Should Do
- Always verify requests: If something feels off, even if it’s coming from a higher-up, pick up the phone and confirm. It’s better to double-check than regret.
- Be cautious with links and attachments: Don’t click on anything else if you are not absolutely sure it is safe. In case of doubt, contact IT.
- Speak up: If your gut instinct is that something isn’t right, then discuss it with your manager or IT team. You aren’t being paranoid, you’re guarding the business.
- Stay updated: Cyber threats evolve every day. Read up on new scams to stay ahead of potential attacks.
Guidelines for Executives and Management
Executives are not just impersonated—they’re also high-value targets. Here’s how leadership can help set the tone:
- Establish Chain-of-Command Protocols: Avoid informal approvals. Build in checks for fund disbursement or data sharing that involve multi-person verification, even at the executive level.
- Create a Security Playbook: Document how to respond to suspicious emails, unexpected financial requests, or security anomalies. Everyone should know the drill before an incident occurs.
- Use Role-Based Access Controls (RBAC): Limit access to sensitive data by function, not title. Only those who truly need access should have it.
- Strengthen Executive Identity Protection: Deploy anti-spoofing technologies and real-time monitoring to secure high-risk personas such as senior leadership.
- Treat Email as a Risk Surface: Implement advanced authentication protocols and email intelligence tools that protect not only the company’s domain but also brand reputation.
The Mechanics Behind the Success of CEO Impersonation Fraud
CEO fraud is successful because it weaponizes trust and urgency. The average employee doesn’t want to question a request from their boss, and scammers count on this hesitation. Combine this with clever email tactics and timing (e.g., Friday afternoons, holidays), and it becomes a dangerous mix.
Also, unlike traditional phishing, CEO fraud attacks are highly personalized. Scammers may spend weeks learning your company’s structure, communication style, and financial workflows before moving.
Impact of CEO Identity Fraud
Beyond financial losses, CEO Identity Fraud can:
- Damage your company’s reputation
- Lead to legal issues or regulatory penalties
- Break internal trust
- Create customer fallout if data is leaked
The stress of scamming employees can also be enormous. Some victims claim they have anxiety, guilt, or even a loss of job to file their cases.
Final Thoughts
CEO fraud is not just an IT problem—it’s a people problem. It uses human emotions, trust, and pressure to succeed. Your organization can be secured with the correct tools, training, and culture.
So, the next time you get your “CEO” email asking for a wire transfer, pause. Think. Verify. Because in the digital age, a moment of caution can save millions.
Frequently Asked Questions
CEO fraud is a targeted scam in which an impostor impersonates the CEO to trick employees into sending money or data. Unlike generic phishing emails, these attacks are personal and include social engineering.
Through multi-factor authentication, employee training, verification protocols, and high-end email filtering systems, the companies can reduce the risk of falling prey to the virus.
Be on the lookout for urgent messages, strange email addresses, grammatical mistakes, and simplicity of any message asking for secrecy. Ensure to check personally prior to doing anything.
