Understanding People Security Management (PSM)
People Security Management (PSM) is an essential aspect of comprehensive cybersecurity and risk management strategies in modern organizations. It addresses the human component of security risks, focusing on minimizing vulnerabilities arising from employee actions and susceptibility to social engineering attacks. By integrating PSM into their cybersecurity framework, organizations can effectively reduce the likelihood of breaches caused by human error.
Table of Contents
ToggleThe Rising Importance of PSM
In the evolving landscape of digital threats, the human factor has become increasingly significant. With a majority of security breaches traced back to human errors or manipulations, it’s clear that robust cybersecurity measures must go beyond technical solutions to include a strong focus on People Security. This shift towards a people-centric approach in cybersecurity highlights the need for effective PSM practices, particularly in training and awareness programs.
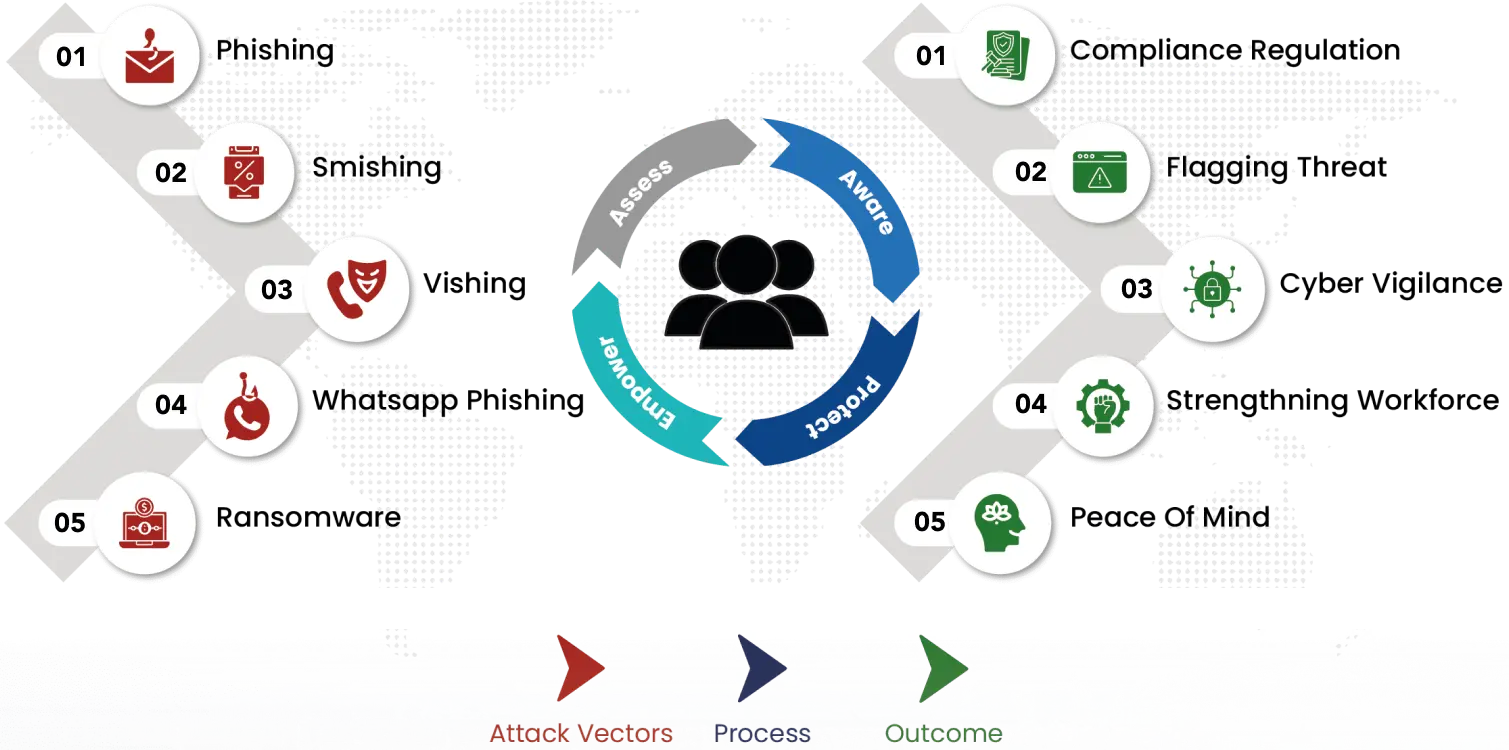
Best Practices in PSM for Employee Training
Assess: Identifying Vulnerabilities for People Security
Conduct Risk Assessments:
Begin by evaluating your organization’s cybersecurity risk posture. This involves a comprehensive analysis of potential vulnerabilities that could be exploited by cyber attackers.
Simulate Attacks with TSAT: Utilize TSAT for simulating cyberattacks. Its AI template generation feature tailors simulations to specific industries, making the scenarios highly relevant and effective.
Real-Time Vulnerability Tracking: TSAT offers real-time insights into employee vulnerabilities, significantly enhancing the organization’s risk management capabilities. By identifying who is most susceptible to social engineering attacks, companies can tailor their training to address these specific weaknesses.
Book a Free Demo Call with Our People Security Expert
Enter your details
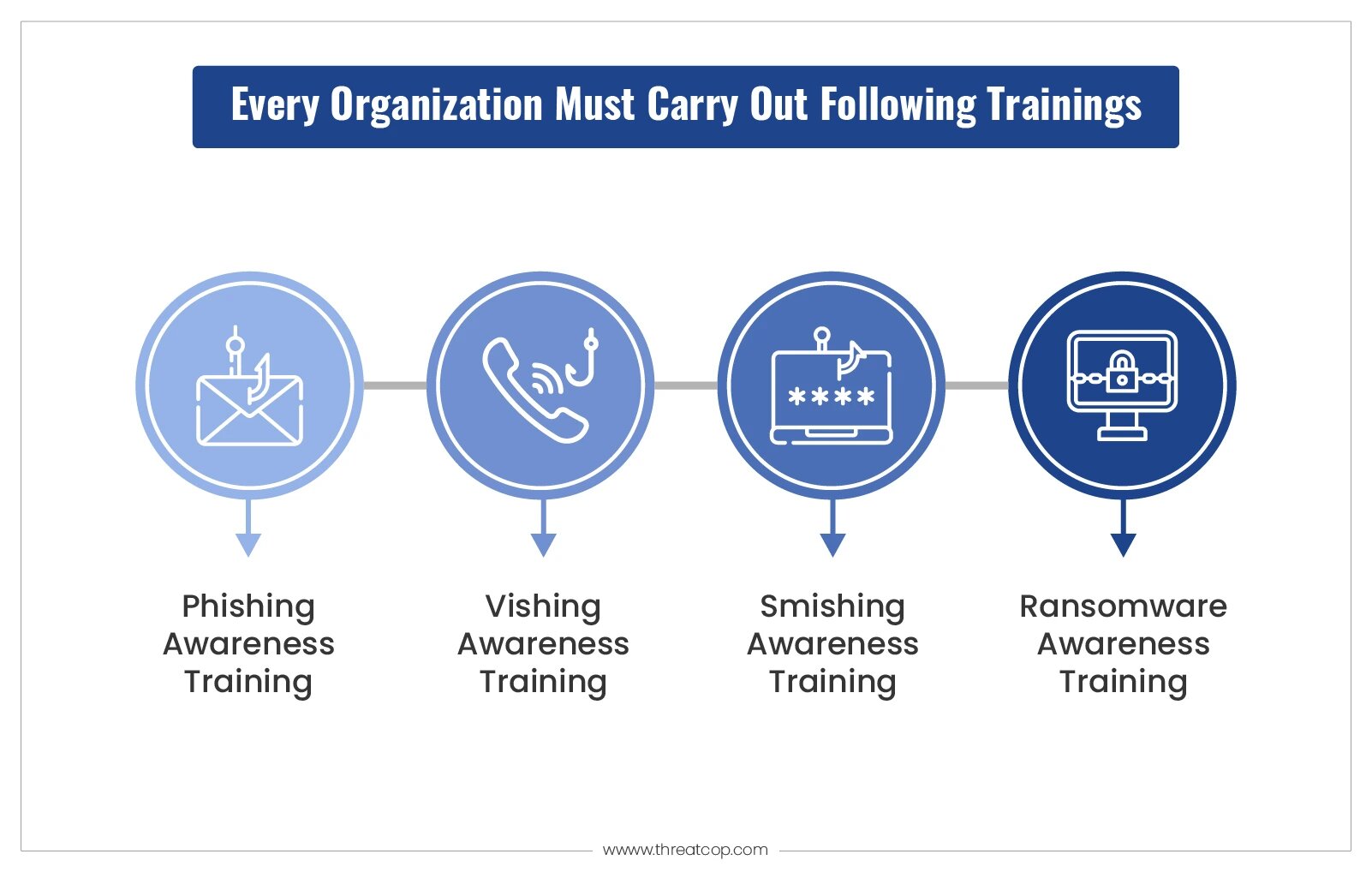
2. Aware: Raising Cybersecurity Awareness
Comprehensive Training Modules: Develop and implement training modules that cover the spectrum of cybersecurity threats. These modules should be designed to be accessible and understandable for all employees, regardless of their technical background.
Interactive Workshops with TLMS: Engage employees with interactive learning experiences using TLMS. Its updated content and diverse categories ensure that training remains engaging and relevant.
Regular Cybersecurity Updates: Continuously update the training content to reflect the latest cybersecurity trends and threat information, ensuring that employees are always aware of emerging risks.
3. Protect: Implementing Robust People Security Measures
Encourage Daily Security Practices: Cultivate a workplace culture where integrating security protocols into daily activities becomes second nature for employees. This can involve simple steps like regular password changes, using secure communication channels, and being vigilant about email attachments and links.
Routine Security Checks: Implement regular checks and reminders for software updates, data backups, and adherence to security policies. These routine checks can significantly reduce vulnerabilities.
Engagement in Security Discussions: Encourage employees to participate in discussions about security protocols, providing feedback, and sharing experiences. This promotes a sense of ownership and responsibility towards maintaining cybersecurity.
TDMARC for Reputation Protection: Implement Threatcop Domain-based Message Authentication, Reporting & Conformance (TDMARC) to protect the company’s and domain’s reputation from email-based threats.
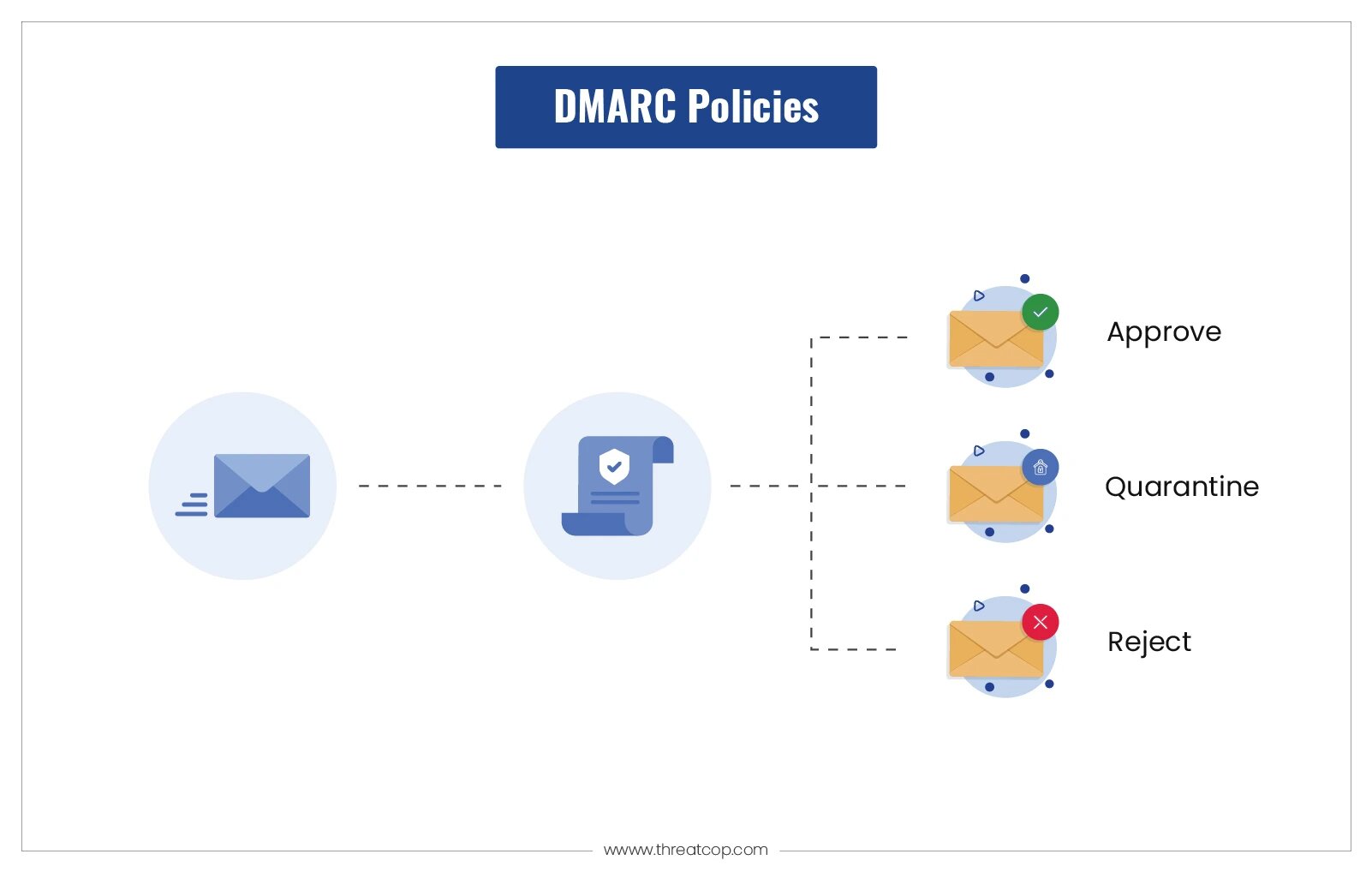
Conclusion
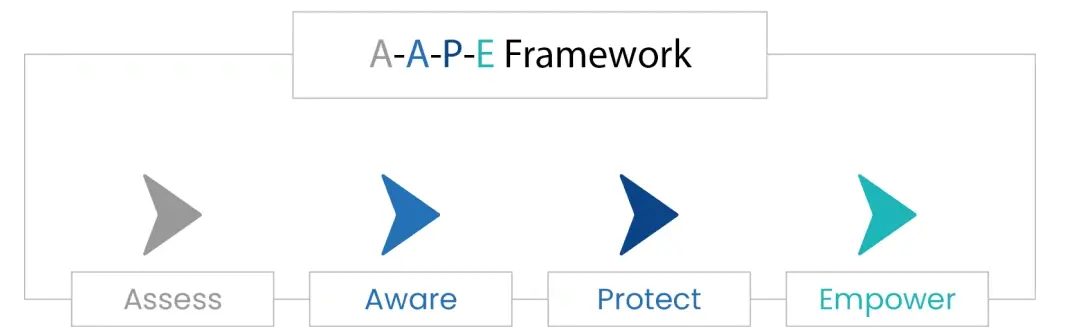
Implementing these practices of people security management for employee training is essential in developing a robust cybersecurity posture. By focusing on Assess, Aware, Protect, and Empower, organizations can transform their employees into knowledgeable, proactive participants in their cybersecurity framework, significantly reducing the risk of breaches and enhancing overall security.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
