The banking, information, and healthcare industries account for the majority of worldwide cyber warfare, and there is a lot more to the story. Cyber warfare cases are increasing day by day. Considering the same, the government is taking equivalent actions.
Table of Contents
ToggleLet’s explore in-depth cyber warfare here in this article. Read further to learn more in detail about the same.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is Cyber Warfare?
Cyber Warfare refers to the war between countries in terms of cyber attacks. When there is significant use of cyber attacks against a particular region, individual, organization, or country. There are varying degrees of what can cause cyber warfare and the damage it can cause. In some unfortunate cases, it can range from financial loss to the loss of lives. There is no clear cyber warfare definition because different countries have different policies on tackling these attempts at digital terrorism. Yes, cyber warfare can, in some cases, be taken as an act of terrorism. This depends on the severity of the crime, its origin, and the purposes behind it.
Even if it is not an act of terrorism, cyber warfare is a punishable crime. Several techniques, like phishing and hacking, for the theft of sensitive and confidential data, are some of the most common ways cyber warfare can begin. The term “warfare” has been given because these acts usually attack a nation or country. It is with the intent of gathering intelligence on a country. This information is then used in further phases of cyber war.
The simple purpose of cyber war is to penetrate security systems and institutionally attack a nation. All information is online or data-driven now. Therefore, cyber warfare is the new face of terrorism in many forms.
History of Cyber Warfare
Cyber warfare suggests the medium of conflict is through a network that is accessible to people quickly. These attacks will hamper essential services and breach security networks. Since all global information is being digitized, cyber warfare incidents have been rising. Since 2010, nations have been engaged in cyber warfare. This is how cyber warfare takes place every year between nations.
- Stuxnet, 2010, was the first actual cyberweapon meant to cause physical harm. It is said to have destroyed over a quarter of Iran’s nuclear centrifuges.
- The March 2014 Russian DDoS attack on Ukraine is allegedly the second time that Russia has combined military and cyber attacks. When pro-Russian separatists took control of Crimea, a DDoS attack in Ukraine disrupted the internet 32 times greater than any recorded attack before.
- The information of 21.5 million US federal workers and rejected applicants were stolen from the US Office of Personnel Management. According to US official sources, the hacker was the Chinese government.
- It is believed that Russian hackers lurked in a power supplier’s network for six months before shutting down the electricity. The power outage cost nearly a sixth of Kiev’s electricity usage that night. This incident occurred almost exactly one year after the December 2016 cyber strike that knocked off electricity to 225,000 people in western Ukraine.
- In May 2017, a ransomware cryptoworm WannaCry attacked more than 200,000 computers in around 150 countries. WannaCry was a ransomware cryptoworm that targeted Microsoft Windows PCs.
- NotPetya was the first notable incidence of weaponized ransomware in June 2017. The NotPetya software masqueraded as ransomware, but its true purpose was to delete data. While the attack began in Ukraine, it swiftly spread over the world. It is unclear how much damage was done during this attack, although it is thought that the overall damage was more than $10 billion USD.
What are the Different Types of Cyber Warfare?
Unfortunately, there are many different ways in which cybersecurity warfare can be conducted. Some of the popular ways in which cyber security threats have been created in the past are mentioned below:
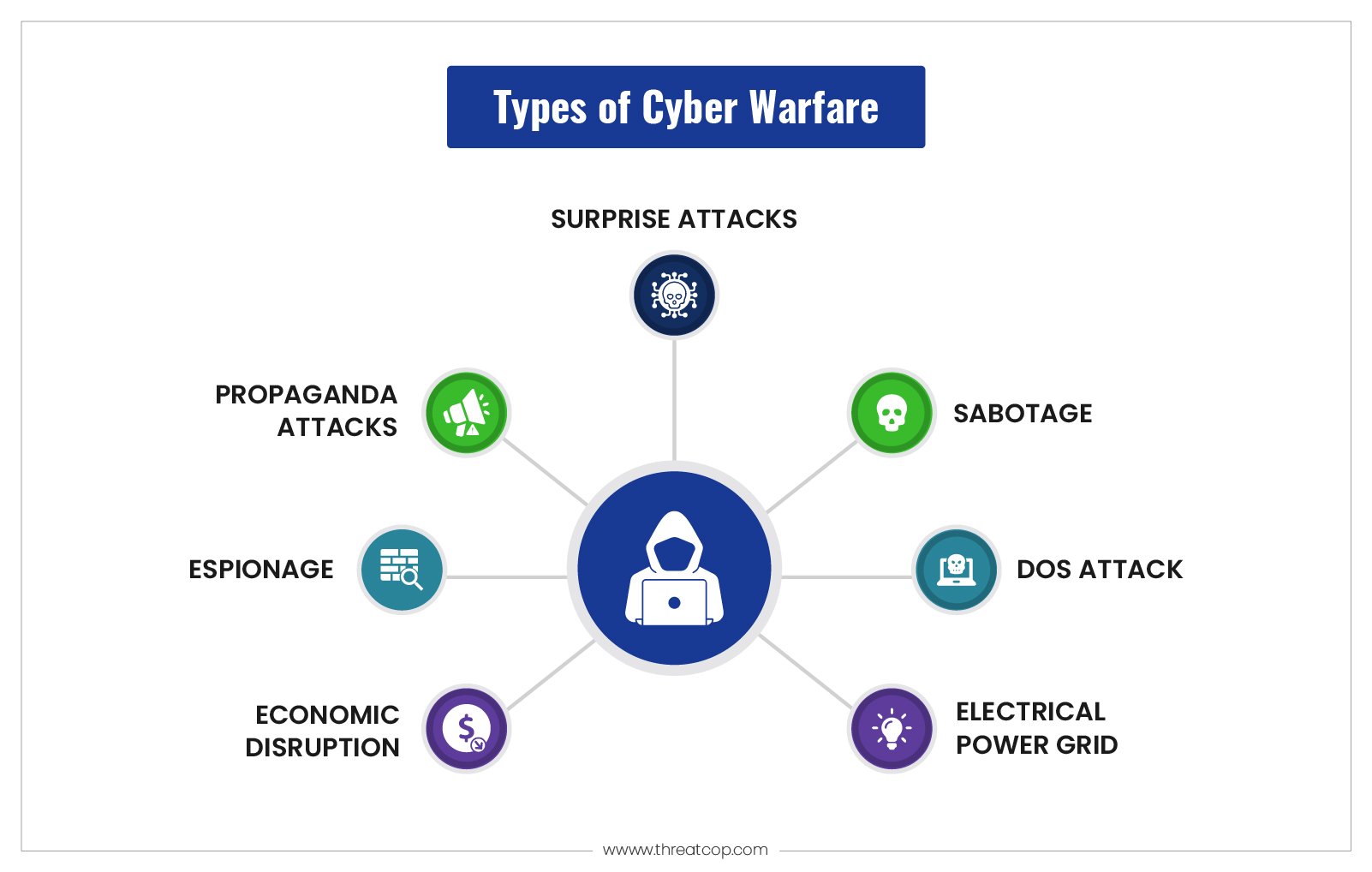
Sabotage
Government agencies must identify sensitive information and the dangers associated with its compromise. Information may be stolen, destroyed, or exploited by hostile governments or terrorists using insider threats such as dissatisfied employees or government employees affiliated with the attacking nation.
DoS Attacks
DoS attacks stop legitimate users from using a website by bombarding it with fictitious requests and making it respond to them. These attacks have been used to disrupt vital operations and block access to websites.
Electrical Power Grid
Targeting the electricity grid gives attackers the ability to disable necessary systems, damage infrastructure, and possibly cause bodily harm. Power grid attacks can also interfere with communications, making it impossible to use services like text messaging and communications.
Propaganda Attacks
Attempt to influence people who are residing in or supporting a target country in their thoughts and behavior. Propaganda attacks can be bemused to reveal embarrassing facts,
Efforts to exert influence over the spread of falsehoods to undermine public confidence in a government, or support one’s adversaries.
Espionage
Espionage means using a country’s vital information to steal, duplicate, or forge incorrect information that would lead to extracting information. Regardless of whether the country is aware of it or not, this may happen. There have been cases where the attacked country found a leak in its system. In terms of cyber warfare, this can entail compromising delicate computer systems using spear phishing or botnet attacks before leaking sensitive data.
Economic Disruption
Computers are used in the majority of the current economic systems. Attackers can attack networks of economic institutions such as stock exchanges, payment systems, and banks to steal money or prevent individuals from obtaining the funds they need.
Surprise Attacks
These are the modern-day equivalents of the 9/11 and Pearl Harbor attacks. The goal is to launch a large-scale attack that the adversary is unprepared for, which will weaken their defenses. When hybrid warfare is used, this can be done to set the stage for a physical assault.
There are many other forms of cybersecurity warfare. However, these are the most commonly applied. Even though they are familiar, these still pose a threat to countries across the world. This is why this topic is a source of so much debate all the time. It takes one strong virus to disrupt a country’s information.
Recent Cyber Warfare
- While the Finnish parliament was in session in August 2022, the website suffered a DDoS attack. This denial-of-service assault might be part of a concerted attempt by Russian state-sponsored hackers to impair the websites of the Finnish government in retribution for the application to join NATO. A DDoS attack momentarily disables access to a website but does not permanently destroy it.
- South Staffordshire Water Company reported an assault in August 2022 that caused a network interruption and data loss in their internal business network. A cybercriminal ransomware organization threatened to interfere with the company’s water supply. This claim was denied by the corporation. The crooks sought to cash in exchange for not releasing important material and explaining how the network hack occurred.
- In April 2022, a DDoS assault knocked off various Estonian government websites for many hours. The president’s website, the Ministry of Foreign Affairs, the Police and Border Guard, the identity card homepage, and the state services digital portal were all attacked. Because of Estonia’s disapproval of Russia’s assault on Ukraine, the country has become a target for Russian hackers.
Is Cyber Warfare a Threat?
Cyber warfare is a threat because, globally, countries are moving to access information more efficiently, which can only happen through online portals. These attempts at digitizing our files put us all at risk of cyber warfare attacks. However, there are many ways in which countries have managed to protect themselves from such attacks.
More importantly, the global community has come together on many avenues to assist each other in protecting ourselves from such threats. While it is ironic how security threats bring the global community together, it has been an effective tactic. Sharing technology and information has recently helped bridge many gaps between nations. These are the possible ways in which we can hope to win against any cyber warfare.
Protection Against Cyber Warfare
Cybersecurity Policies in Industries
To address today’s cyber dangers, organizations must rethink the way they inculcate their cyber strategies. Given how readily predators exploit an ecosystem, hunting for a single link in the chain is ineffective. Organizations must look for weak spots along the chain, from one end to the other. The proper solution is to collaborate across industries as an ecosystem.
Cyber Attack Simulation
Cyber attack simulation (phishing awareness and simulation) is by far the most effective technique for each and every sector to protect itself from various cyber attacks. You may replicate circumstances by performing activities to identify where you fall short and where you excel. This provides a comprehensive grasp of what has to be incorporated into your resiliency and cyber approach.
Employ Threat Intelligence
Cybersecurity concerns have grown into a more comprehensive strategy. However, this has greatly improved communication and security cooperation. It is not only about technology but also about procedures and people. Cybersecurity analysts may quickly change their attention from cyber controls and technology to knowing the business and conversing with its consumer’s thanks to communication and intelligence gathering.
Multi-Layer Defense
Companies must employ multi-layered protection rather than depending largely on perimeter security. Recognizing this sooner rather than later is essential since cyber threats ultimately infiltrate, and when they do, detecting and responding to them effectively with a multi-layered defense is becoming more of a requirement these days.
Employee Security Awareness Training
Aside from cybersecurity rules, you must also prioritize personnel training for your employees. They must be able to recognize and efficiently deal with dangers. To do this, make security awareness training mandatory for all employees. This training will help your employees be cyber vigilant.
Final Thought
As a global community, we are all under the threat of cyber warfare. However, as we have been dealing with these problems for a few decades now, their solutions and protection for the future have still been achievable tasks. Information protection and the ease of using digital platforms have been the focus of all countries for quite some time. There will be glitches on the way, but there are many ways to identify and protect ourselves from them. This is only because of the constant efforts and achievements of security personnel.
FAQs
What is Cyber Warfare?
Cyber warfare is an act of terrorism conducted by any country or terrorist organization against another. The primary aim is to destabilize a country or to create a general atmosphere of chaos and panic. Digital information is an essential tool for such terror attacks today.
How many types of cyber warfare are there?
There are no fixed ways of conducting cyber warfare. This is what makes the definition of cyber warfare so flexible and challenging. The future is uncertain. This is why active steps are constantly being taken to ensure that proper protection is given to everybody.
How long has the threat of cyber warfare been around?
The term itself implies that this is a digital war. This means that it has not been around for a very long time. Unfortunately, this does make this warfare tactic a little unpredictable for all parties. It is also easy to understand where these attacks are happening because it is easy to pin down a location online today.
What is the best solution to cybersecurity warfare threats?
The best solution to cybersecurity warfare threats is employee security awareness training. They are the most important, as well as most vulnerable, assets for any organization, so they should be trained properly.
