It is a Friday evening. The office hours are just about to end. But a finance manager receives an urgent email from the personal Gmail account of the CEO:
“Need you to wire $75,000 for the Philippines deal ASAP. Don’t loop in others. Confirm when done.”
The email header looks clean, and the request feels urgent. The manager acts right away. The outcome? The organization later finds out that the CEO never sent it. The funds are gone, and the attacker is nowhere to be found.
Table of Contents
ToggleSuch incidents have become quite common, and it is known as a whaling attack. It has evolved as a serious cyber threat, as organizations are losing millions.
What is a Whaling Attack?
A highly targeted form of spear phishing that involves senior executives, or to be more precise, pretending to be them, is a whaling attack. This is different from the mass phishing campaigns, as the whaling attacks are quite personalised and research-driven.
At first, the attackers exploit the authority and influence of the C-suite, and then it becomes quite easy to trick employees into sharing sensitive data, transferring funds, or granting access to the system.
Let’s have a look at the core characteristics of a whaling attack:
- Authority + Urgency + Confidentiality: A trusted leader “ordering” fast action.
- Minimal Content: Short, high-pressure instructions to bypass suspicion.
- Research-Driven: Attackers may study press releases, LinkedIn profiles, earnings calls, or org charts for weeks before launching.
- Common Targets: CFOs, COOs, CHROs, Executive Assistants, Finance Directors.
Book a Free Demo Call with Our People Security Expert
Why Whaling Attack Works So Effectively
- One of the most important reasons why whaling works so effectively is the position-based pressure. The pressure comes from the top, and the subordinates often hesitate to decline it. The CEO gives an order, and you can’t say no.
- The attackers plan everything ahead, and they deliberately send requests before holidays or on Friday evenings, when the employees are rushing to close out work. So, often they miss out on the verification process in a hurry.
- Third, the attackers include instructions with the message like “Don’t involve anyone else”, and this cut off verification channels.
- During whaling attacks, the attackers often spoof personal domains of the executives. Thus, there remains no doubt or clue from the side of the employees who receive the messages from the legitimate domain.
- When it comes to phishing simulation, senior leaders are often exempted. They usually do not go through the same security onboarding as other staff, and this creates a blind spot for attackers.
Real-World Impact Example
Let’s take an example of one publicly reported case where a multinational company received a series of fake emails. All these emails seemed to come from the CEO. It consisted of instructions for the finance team to process payments for an “urgent acquisition.”
The attacker had already gathered information from the company’s press releases and SEC filings to time the attack during real M&A talks, and this made the emails more believable for the employees.
Common Whaling Use Cases
- Wire transfer requests: Here, an attacker directs finance teams to send urgent payments to accounts which are not legitimate
- Payroll / W-2 data theft: The goal is tricking HR into sending salary, tax, or banking details.
- M&A Intelligence Theft: The cybercriminals target the executives during mergers or acquisitions. Here, the main aim is to steal contracts and NDAs.
- Credential Harvesting via Fake SSO Pages: It is also a common method. Here, the attackers send links to realistic login pages. Sometimes, these are enhanced with deepfake overlays to imitate live video calls and “authenticate” the request
Red Flags for Executive Assistants, HR, and Finance Teams
Red Flag | What It May Indicate |
Comes from personal domain (e.g., Gmail) | Possible CEO impersonation scam |
“Don’t tell anyone” language | Social isolation tactic |
Urgent financial action (wire, crypto, etc.) | Business Email Compromise attempt |
Sudden tone/style change | Spoof attempt |
Missing or altered signature block | Brand impersonation |
Attachments that require “immediate review” | Possible malware loader |
The Executive Risk Gap
Talking about the executives, they are actually both the most protected and the most exposed members of an organization:
- Executives are usually not included in routine security training. Leaders have tight schedules, and this leaves little room for structured awareness programs. As a result, this creates blind spots that attackers can exploit.
- Leaders are often bypassed in phishing simulations. So, the leaders don’t get valuable opportunities to experience and recognize evolving attack tactics.
- Although there are these gaps, they hold the highest-value data and financial authority. From confidential negotiations to wire transfer approvals, their access is a prime target.
Result: Attackers are well aware that just a single successful impersonation can result in massive rewards. Executives are like the “whales” in a sea of cybercrime. As the attackers exploit authority, urgency, and trust, technical defenses can be bypassed entirely, striking at the human layer where leadership influence is strongest.
The AAPE Framework for Whaling Mitigation
To counter whaling, adopt a Zero Trust Executive Protection Model using the AAPE Framework:
1. Assess (TSAT)
- Conduct impersonation simulations (CEO-to-finance, CFO-to-HR).
- Measure reaction times, escalation procedures, and validation steps.
- Identify high-risk individuals who need extra awareness.
2. Aware (TLMS)
- Deliver executive-specific awareness modules tailored to real-world attack patterns.
- Train assistants, finance, and HR staff to spot spoof tactics—from display name deception to domain typos.
3. Protect (TDMARC)
- Block spoofed executive email domains with DMARC enforcement.
- Implement BIMI (Brand Indicators for Message Identification) to give a visual trust marker in inboxes.
4. Empower (TPIR)
- Give employees one-click reporting for suspicious high-authority messages.
- Flag and investigate any email that requests sensitive action without prior process.
Executive Engagement Strategy
Want to close the leadership security gap? Have a look at the steps mentioned below:
- You need to stop using personal email for business communications. As you take this step, the attackers can no longer exploit less-secure personal accounts to send convincing requests.
- It is crucial for leaders to participate in phishing simulations. As executives actively engage in training, it makes vigilance a part of their normal lives. Also, it reduces stigma around double-checking unusual requests.
- Publicly endorsing security culture in all-hands meetings will ensure that security is a shared organizational value, not just an IT responsibility.
- Dual-approval processes for financial transactions, even at the top level must be made mandatory. This simple safeguard prevents single points of failure and prevents fraud attempts that rely on urgency and authority.
- If a request seems unusually urgent and secretive, it deserves a verification step. You can just pick up the phone before acting.
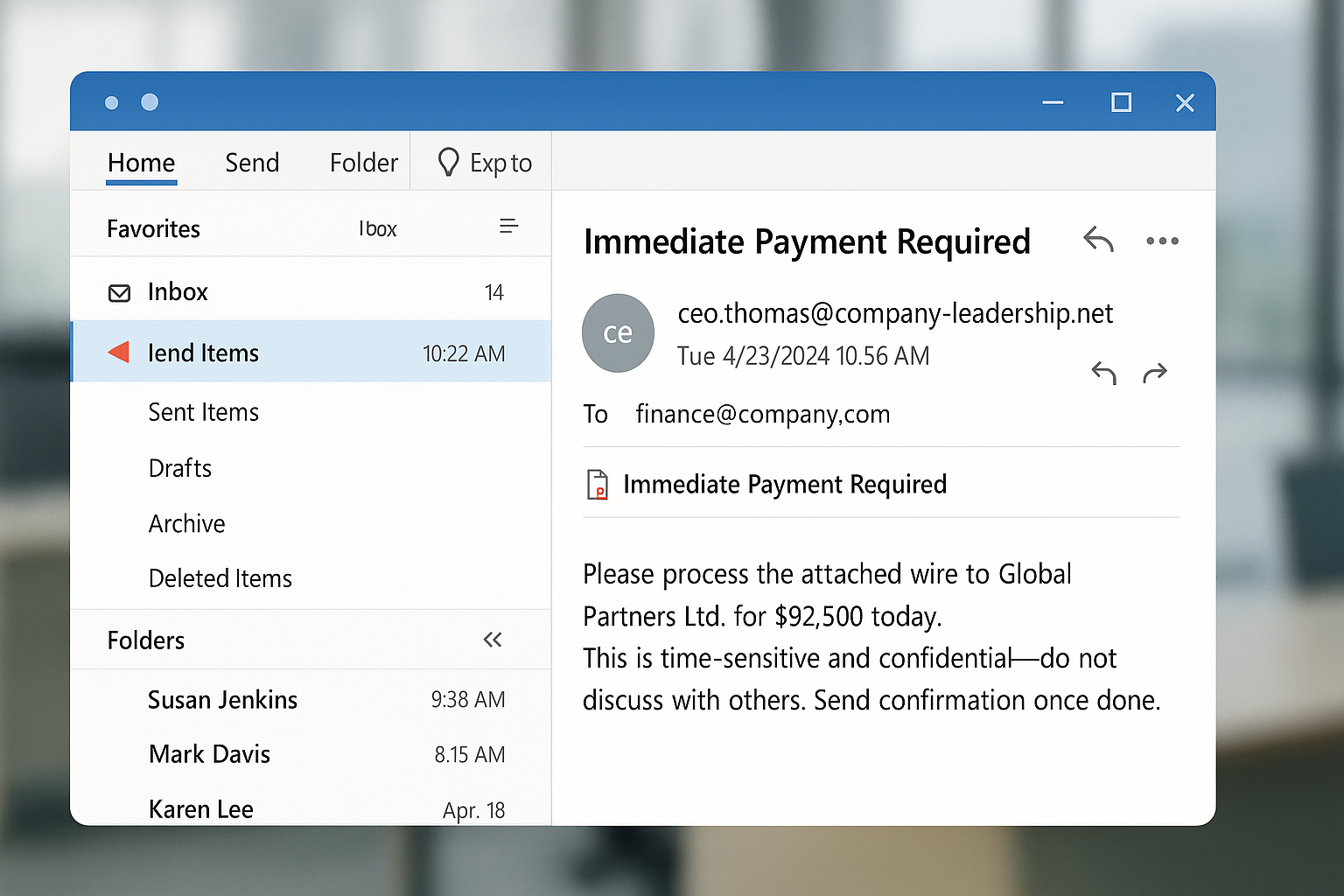
Example of a Mock Whaling Email
Closing Insight
Yes, your CEO’s inbox may be very secure. But when it comes to whaling, the attackers don’t need access. They only need you to believe the lie.
Failure of technology? No, that is not the reason behind the success of a whaling attack. Human trust gets hijacked by the cybercriminals; and this is the main reason.
The solution lies in executive engagement, process discipline, and security awareness that extends to every level of leadership, ensuring that verification becomes instinctive, communication channels are silent, and trust is backed by process, not assumption. Still confused? You can get in touch with cybersecurity experts for help!
Frequently Asked Questions
A: Whaling is a type of phishing attack where the main focus lies on the top-ranking executives who have access to sensitive data or financial assets.
A: Whaling is a more personalized and sophisticated method. Here, the targets are the senior executives. On the other hand, general phishing attacks are not very personalized and attack regular employees.
A: Yes. It can be prevented by awareness training among the high-ranking officials. Also, various authentication protocols and security tools are considered effective in preventing whaling phishing.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
