An email-based malware distribution campaign has tried to disguise spam as an email chain and launch a spoofing attack. TA551, also known as Shathak, the infamous group that spreads malware like Ursnif and Valak, is behind this operation. To carry out the operation, the group uses real messages. These messages have been stolen from previously infected hosts.
Table of Contents
ToggleThis campaign often targets English speakers to spread Ursnif, Valak, and other information-stealing malware. However, since mid-July 2020, this campaign has exclusively been spreading IcedID, another info-stealer malware. And as of now, the campaign has also started targeting German, Italian, and Japanese speakers.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
How does TA551 Malspam Work?
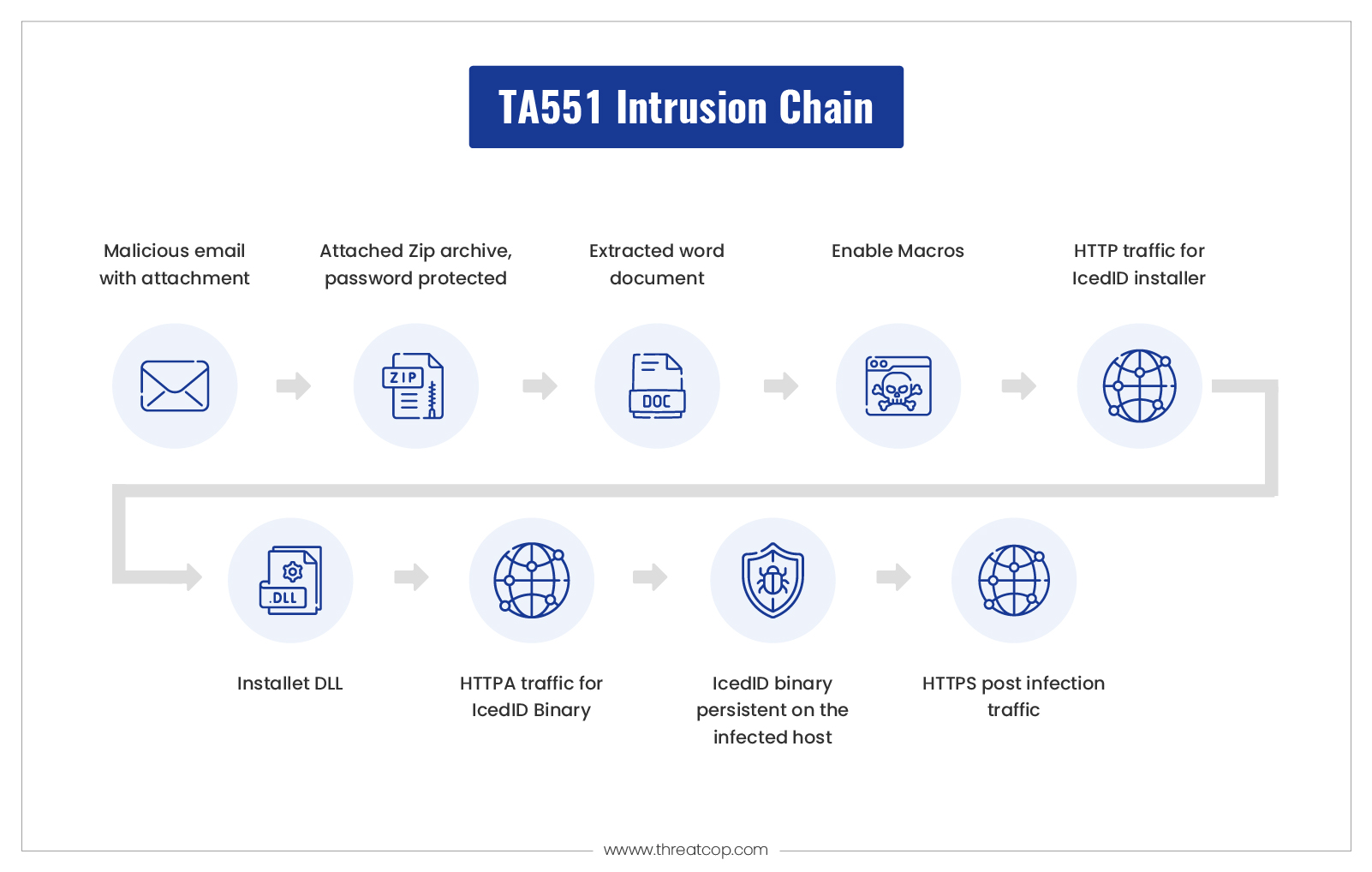
The group sends emails with an attached, password-protected ZIP archive containing a Microsoft Word document. The message informs the user of a password to open the attachment. On opening the Zip archive and entering the password, the user finds a Microsoft Word document with macros. When the victim enables macros on an exposed Windows computer, the victim’s host downloads an installer DLL for IcedID malware. However, recently they put a few changes in their attack pattern.
Book a Free Demo Call with Our People Security Expert
Enter your details
The TA551 group spread TrickBot and BazarBackdoor via malicious documents, in Microsoft Word document format. They store the infected documents in a password-protected archive file. After then they attach those infected documents to the phishing emails.
When you need to repeat a task, you can use a macro to automate the process. These specific infected documents have a macro, that a user run by opening the document and allowing macro execution.
The macro executes a file using the mshta.exe Windows utility after dropping a Microsoft Hypertext Markup Language (HTML) Applications (HTA) document on the file system. A malicious actor is able to execute malicious HTA files by using mshta.exe and bypass applications that don’t account for its use.
TA551 Recent Modifications
So far, TA551 has been following specific traffic patterns. However, it has changed as of now since October 2020. The URLs generated by Word Macros follow a noticeable pattern, such as:
- “php?l=” in the URL path
- URLs end with “.cab”
But since November 2020, experts have noticed some changes in the pattern of generating the URLs by TA551 during IceID infection. The possible reason for the changes from the campaign could be an attempt to evade detection. At the very least, they can baffle the user conducting forensic analysis on an infected host.
Recent TA551 attack using stealers
In a recent study by Cyware Social, TA551 (aka Shathak) has been targeting English-speaking victims with this malware distribution campaign. Multiple malware families, including Ursnif and Valak, have been distributed by TA551 since the beginning of 2022.
- An ElectroRAT stealer for macOS, Windows, and Linux was recently uncovered after being undiscovered for nearly a year.
- Furthermore, a PyMicropsia stealer associated with AridViper (a hacker team) was discovered operating in the Middle East.
How to Stop the TA551 Malspam Campaign Spoofed Email?
When it comes to email spoofing, it can take many of the following forms:
Sender’s name spoofing
Hackers impersonate the identity or the sender’s name that the recipient might trust in order to trick the recipient. As a result, the recipient ends up providing sensitive information or credentials.
Sender’s domain spoofing
Malicious actors fake the sender’s email address or the domain name that is legitimate and trusted by the recipient.
Look-alike spoofing
In this case, the malicious actors copy the sender’s name or domain, which looks alike but differs in a character. The goal these domains have is to impersonate someone and make money or steal data.
As an organization, you should implement certain cybersecurity protocols to protect your domain against cyber criminals. If your organization neglects to implement the protocols, there is no check on the sender’s authentication and it is highly susceptible to spoofing attacks.
Effective and Reliable Protection from the TA551 Group
There are several cybersecurity measures to protect your organization’s email domain and prevent malicious actors from misusing the domain. An organization must embrace certain protocols to control attacks. Also, to prevent your email domain from being used in spam and spreading malicious links or attachments, your organization should adopt the following approaches:
- Sender Policy Framework (SPF): An SPF record is added to the DNS records so that the recipient’s mail server can verify if the sender’s IP address matches and if it is authorized to send emails on behalf of the sender’s email domain.
- Domain Key Identified Mail (DKIM): Every email sent from your email domain includes a digital signature in the header field. The receiving server verifies the unique signature to authenticate the email.
- Domain-based Authentication Reporting and Conformance (DMARC): Implementing DMARC provides you with the ability to know how many emails are sent out from your email domain and who sent the emails. It also gives you information about the emails that failed to deliver and the reason for the failure.
To secure your domain, the smart and easy solution for email spoofing is to implement DMARC. Our tool, TDMARC from Threatcop, ensures that your email domain is safe against domain forgery.
TDMARC is a GCA-certified email authentication protocol that monitors DMARC, SPF and DKIM to give your organization a compliance report. The report gives you detailed insights into the organization’s outbound emails.
It provides information on how many emails are flowing through the domain and how many are landing in the receiver’s inbox. And good news for a non-technical person, it is user-friendly and easy to understand the report because it gives you a clear picture with a graph.
The tool lets you determine whether your domain’s outbound emails that fail DMARC authentication reach the recipient’s inbox, are redirected to spam, or are bounced back. Hence, it also boosts email engagement rates since your organization’s legitimate emails will end up in the receiver’s inbox every time an email is sent.
Malicious actors Impersonating your email domain not only brings you loss in terms of money but also abuses your brand and harms the customer’s trust in relying on your service. Therefore, an organization must secure the email domain and protect the brand and trust it has to build.
