Email has become the cornerstone of communication for organizations worldwide. It’s more than just a tool; it’s the primary conduit for business operations, customer engagement, and professional correspondence. The ubiquity of email in corporate communications is unparalleled, offering immediacy, versatility, and global reach. Whether it’s internal discussions, client negotiations, or marketing campaigns, emails play a pivotal role in driving business processes and strategies. This extensive reliance on email underscores the need for robust security measures to safeguard against cyber threats.
Table of Contents
ToggleIf either of these protocols is not present, then it is quite likely that domain spoofing or email spoofing can be done. The absence of these protocols will give threat actors an upper hand in creating malicious email domains and impersonating your organization to land a cyber attack. Apart from preventing attacks, the implementation of these protocols increases an email domain’s reputation, resulting in higher email deliverability.
Adhering to the New DMARC Guidelines
For bulk email senders, adhering to the DMARC (Domain-based Message Authentication, Reporting & Conformance) guidelines, as per the new standards set by major email service providers, has become indispensable. Effective from February 2024, these guidelines mandate that bulk emailers implement stringent authentication measures, including DMARC, along with SPF and DKIM. The integration of DMARC is a critical step towards ensuring that emails are not only authenticated but also aligned with the best practices for email security. This compliance not only protects the integrity of email communication but also plays a vital role in preserving the trust and confidence of customers and subscribers in the digital communication ecosystem.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What are SPF and DKIM?
SPF stands for Sender’s Policy Framework and DKIM stands for DomainKeys Identified Mail. Both are email authentication protocols meant to authenticate an email domain and emails sent from it.
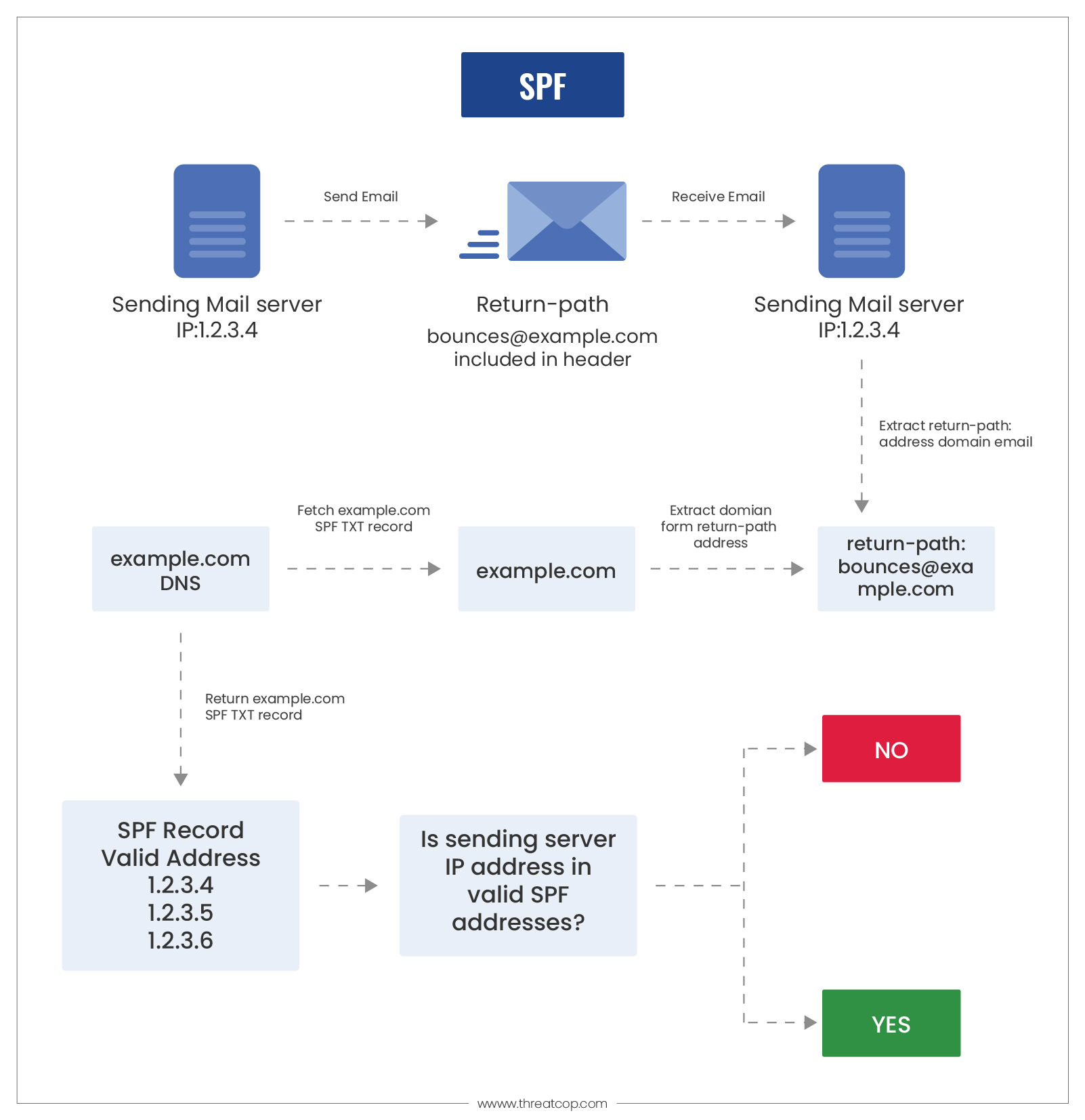
SPF is an authorization protocol through which the receiving server can authenticate whether the messages sent from a domain are sent from an IP address approved by the domain owner. It provides a mechanism for storing email domain and IP address information on the DNS (Domain Name System).
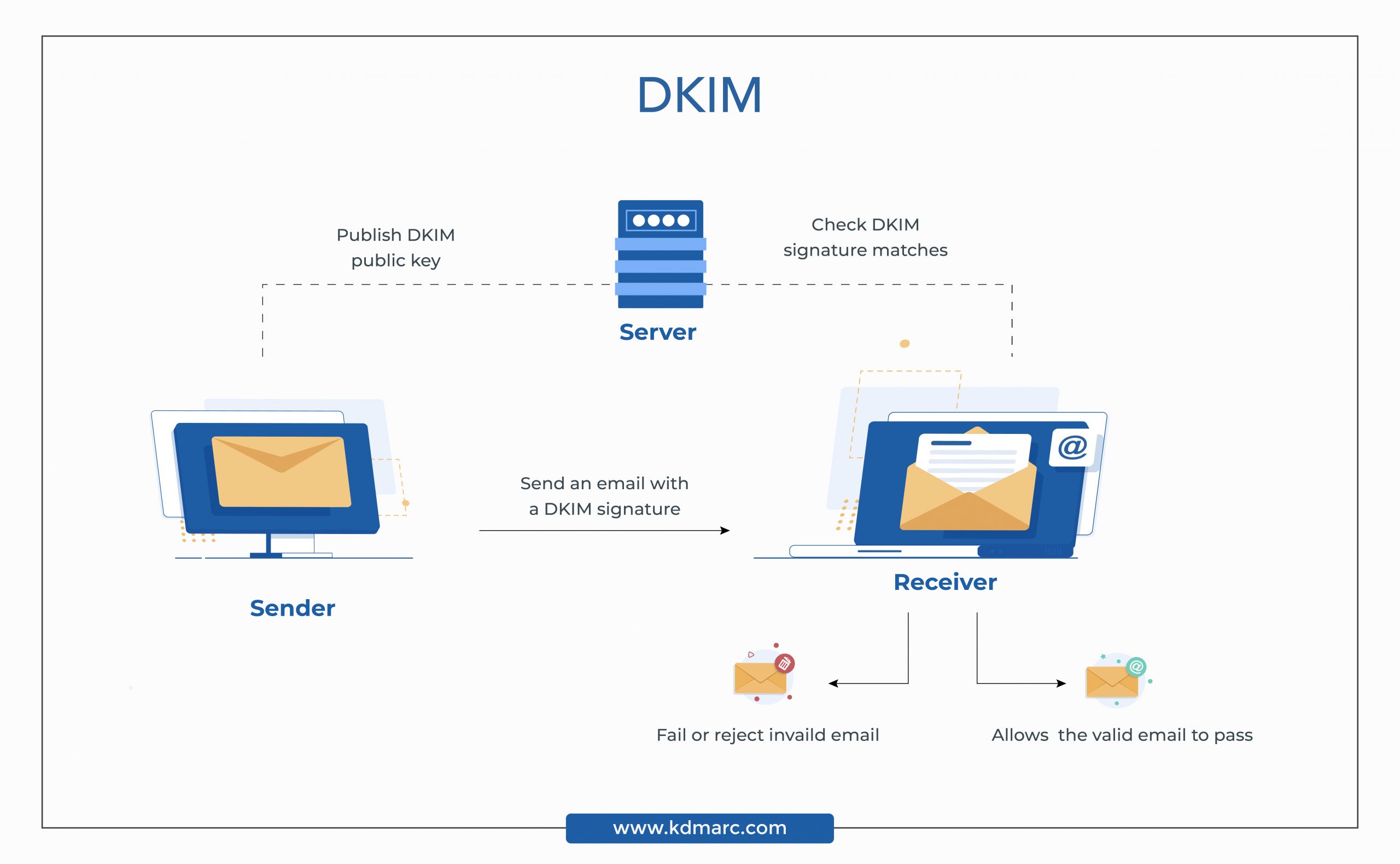
DKIM uses public key cryptography to ensure the email wasn’t tampered with during transit. The authentication protocol also helps in improving the brand’s reputation. DKIM allows domain-based blacklisting and whitelisting of domains. This is done more effectively by allowing the signing of domains to reliably recognize its stream of genuine emails.
Why do Organizations Need SPF and DKIM?
There are many organizations that employ email marketing as the primary mechanism to reach out to their customers and subscribers. In such cases, they have to send a huge number of emails and it is quite possible that their emails could land in spam. Also, such organizations are always prone to email-based attacks such as phishing, spoofing, etc.
Having both SPF and DKIM configured provides your outbound emails with an extra layer of protection. Using two-protocol authentication is a very strong approach that will have a positive effect on email deliverability. These protocols help in building the reputation of the email domain.
What are SPF and DKIM Records?
An SPF record registers a series of information that gets stored in the DNS. These records contain a list of IP addresses that are mapped to the DNS servers. The DNS servers allocate a series of records specific to a particular domain, which becomes a medium of connection for an organization with the rest of the world.
These SPF records contain a list of IP addresses that are associated with a respective domain of the organization. When emails are sent from an organization, the receiving server checks the IP address of the incoming emails and tallies them with the SPF record of the sender’s domain. Only if it matches will the emails pass SPF authentication.
A DKIM record is either a 1024-bit or 2048-bit stream of characters that act as a digital signature on an email. The DKIM record in DNS contains a public key. The private key is mapped on the email server. The private key is signed in the email and the public key is mapped to the domain. Both key pair serves as a medium to authorize the outbound emails.
When a user sends emails, then the receiver domain extracts the public key from pair of keys and matches them with the domain name on the DNS. This is how DKIM helps the email service provider authenticate an email.
How to Check SPF and DKIM Records?
There are several free online diagnostic tools like DKIM Record Checker and SPF Record Checker that can be used to easily and quickly verify the presence and validity of a domain’s SPF and DKIM records. If you are looking to check whether or not your domain has an SPF or DKIM record, you can easily do so with the help of these efficient online tools.
What is Domain Alignment?
Domain alignment means that the ‘From’ address in an email must match the actual sender of the email. For DMARC to work properly, domain alignment is necessary. There are two types of domain alignment, which are:
Sender Policy Framework (SPF) Alignment: The domain of your email’s Mail- ‘From’ (MFrom) address and ‘From’ address must match.
DomainKeys Identified Mail (DKIM) Alignment: The email’s root domain of the DKIM signing domain should match with the ‘Header’ from the domain.
Both SPF and DKIM alignments are either:
- Relaxed Alignment: In this type of alignment, the domain should match the parent ‘Header’ of the domain. Relaxed alignment is the default that allows the use of a subdomain and helps meet the requirements of domain alignment.
- Strict Alignment: This alignment type requires the domain to match the ‘Header’ from the domain exactly. If strict alignment has not been specified, relaxed alignment is automatically assigned.
Why SPF and DKIM are Not Enough For Securing Emails?
SPF and DKIM alignment complement each other and are meant to secure email domains. Alignment and authentication of either SPF or DKIM are not enough for emails to pass DMARC. However, both protocols have their own pitfalls and nuances that can affect their implementation and maintenance. That includes transient errors that may occur due to the loss of packets of data and transmissions that fail randomly for several reasons.
Senders who run into sporadic problems with one authentication protocol and cannot fix that problem immediately may find a large proportion of their legitimate emails blocked because of the failure of DMARC. Mailbox providers favor those senders that pass and align with both SPF and DKIM. That’s why both of the protocols need to be implemented alongside DMARC.
Threatcop DMARC is the Solution
Standing for Domain-based Message Authentication Reporting & Conformance, DMARC is a protocol that uses Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) for authenticating an email. DMARC is the email verification convention, while DKIM and SPF are the strategies that are intended for the identification of the sender’s email addresses.
Book a Free Demo Call with Our People Security Expert
Enter your details
Threatcop DMARC (TDMARC) is a sophisticated and comprehensive email authentication tool that allows an administrator to implement SPF and DMARC policies. This authentication protocol for emails is intended to give the domain owners the capability to protect their domain from any unsanctioned activity. The intention behind the implementation of the policy is to ensure the protection of your email domain from any BEC attacks, scams, phishing emails, or any other threat activities.
Editor’s Note: This post was originally published in May 4, 2022 and has been partially revamped and updated for accuracy and comprehensiveness

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
