Subdomailing – became a groundbreaking search term in February 2024, when Guardio Labs exposed subdomain hijack attacks happening since 2022. Over time, cybercriminals have taken possession of 8000 domains of reputable names and have sent over 5 million phishing emails. Unfortunately, these emails differ from other fraudulent emails and are challenging to spot.
Table of Contents
ToggleRead the blog that cuts through the noise and guides you as a CISO on how to not only stay safe from such emails but also protect your company’s domain address.
What is Subdomain Phishing?
The subdomailing campaign has been going on the market for two years, where malicious mail from authentic and compromised domains is sent with DND issues.
With any other phishing type, professionals can notice something off, like a difference in URL or logo. But, URLs and other brand details are almost 100% perfect in subdomain phishing.
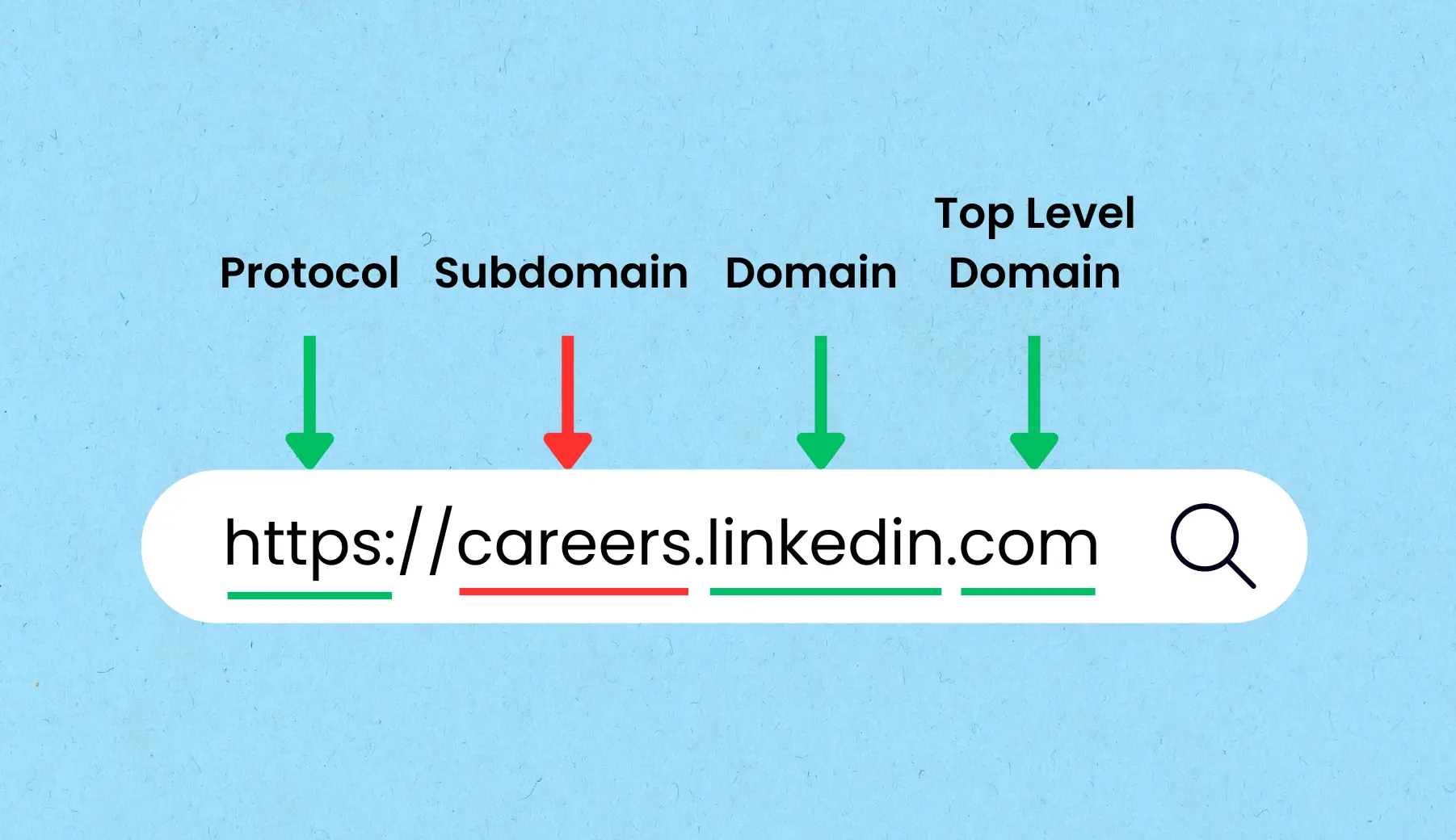
Why is Subdomailing More Destructive?
Subdomailing controls the domain IDs that are legitimate and well-acquainted with large masses of people. For every other person, shop.myntra.com will be a fair domain, making it easier for people to fall for phishing emails. These hijacked domains are used to retrieve consumer data, conduct illegal activities, or even spread ransomware. Till now, famous brands like MSN, CBS, and McAfee have fallen victim to the same.
Example of subdomain phishing:
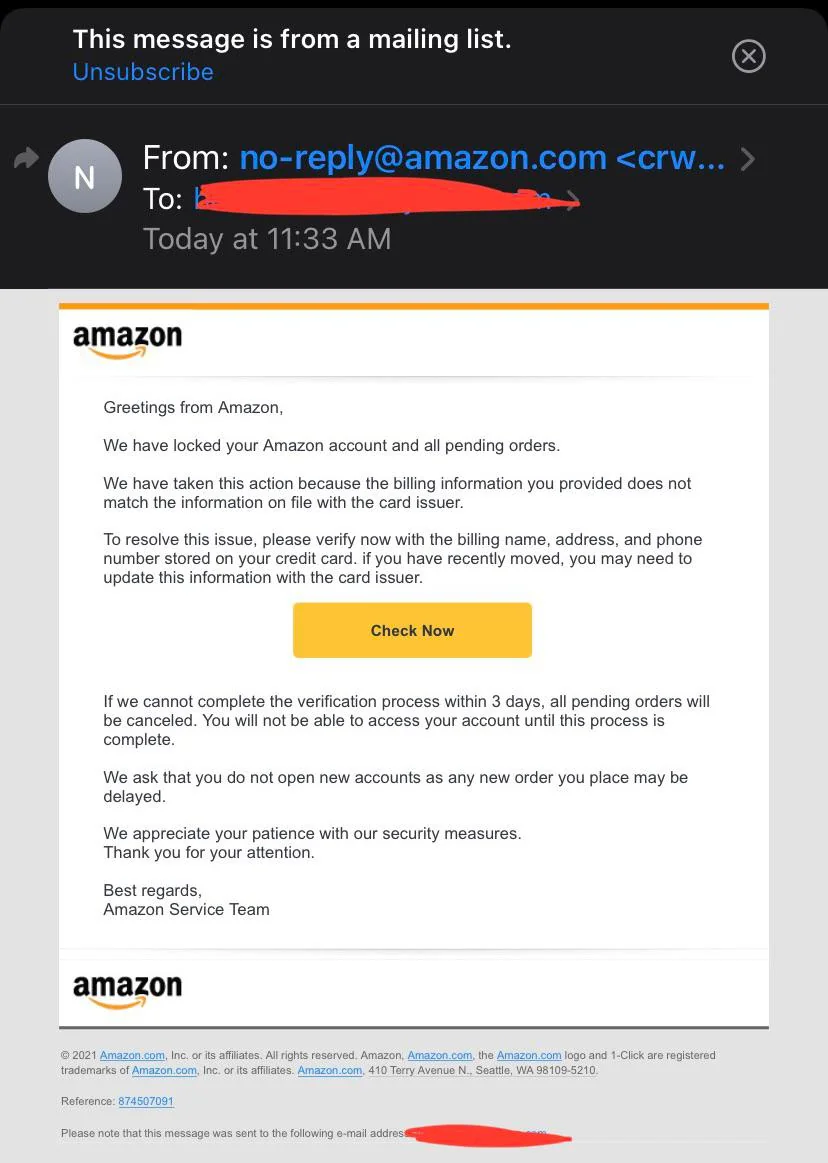
Organizations must acknowledge the evolving landscape of cyber threats in response to the alarming trend of hijacked subdomains from major brands being exploited in extensive spam campaigns.
- Rahul Powar, CEO of Red Sift
To understand how subdomailing works, it’s critical to know the backend process of the whole picture. Popular brands create sub-domains that appear before their brand name. For example, sale.myntra.com. Now, these sub-domains are used primarily for web linking and redirects.
Naturally, brands often discontinue the use of these subdomains after a time. Cybercriminals target these hidden subdomains, buy them, and use them under the same brand’s name to make their emails look more legitimate. Unfortunately, the spam filter considers these links legitimate from the brand and thus delivers the mail straight to your inbox.
Characteristics of SubdoMailing Attacks
- Brands often overlook subdomains; therefore, the attacks mainly target subdomains of popular brands.
- The attacks disrupt brand image by impersonating and tricking users into disclosing confidential information or installing malware in their systems.
- Once the attackers access a subdomain, they hold on to it for a long time, sending thousands of fraudulent emails until someone notices the wrongdoing.
- Subdomailing often performs social engineering to fool users by sending emails with spoofed login page links.
Read more: A Brief Guide to Types of Social Engineering Attacks
Along with impacting users, the subdomailing attacks significantly impact organizations by negatively affecting their brand image.
A Proactive Approach to Fight Against Subdomailing
To protect your company’s name from phishing emails, it’s necessary to take critical actions. Tech giants have emphasized strict adherence to DMARC and other such protocols.
DMARC provides systematic insights into all emails sent from the organization’s domain, preventing misuse of email. It assists in providing the security of outbound email flow, promoting the domain’s prestige and email deliverability.
The concern still leads to a question of how to implement DMARC. Well, that’s when TDMARC comes into the picture. It’s a SaaS-based email authentication tool developed precisely to help businesses deploy and configure DMARC.
Here are some other generic guidelines to prevent subdomain phishing:
- Perform subdomain audits regularly to know the status of organizations’ subdomains.
- Unused subdomains are the main target of cybercriminals. Make sure to delete or repurpose the unused subdomains for an extended period.
- Create and strictly implement policies on how subdomains will be created for the brand, how they’ll be managed, and by whom.
- Ensure that experienced subdomains are renewed before time to safeguard the domain and prevent them from being misused by attackers.
- Lastly, the related employees should be trained and well aware of subdomailing phishing and how necessary it is to maintain records of all subdomains working.
Focusing on Solution – Conclusion
Keeping updates on various types of phishing and implementing tools and systems can get overwhelming for the brands. It’s, however, recommended to divert focus on solutions to ensure safety and take aid from third-party experts for security.
Threatcop helps organizations identify and protect the weakest link in the system against cyber threats. You can quickly start your domain security journey with us; contact us to speak with an expert today and discuss it with us!

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
