Microsoft Office 365 is one of the most popular lines of services in the corporate world. With its huge customer base, it is expected to be a secure system, yet on the contrary, it’s not. Even after so many breaches, the service still contains many vulnerabilities and thus keeps on one of the favorite sites of a cyber attack. With one in every five businesses using cloud-based services, it is being increasingly used in Phishing campaigns.
Attackers have been continuously leveraging access to Office 365 accounts for deploying various cyber-attacks. One of the most widely used cyber attacks is Phishing. Broadly, three major cyber-attacks are being used:
- Microsoft emails that ask you to update your password
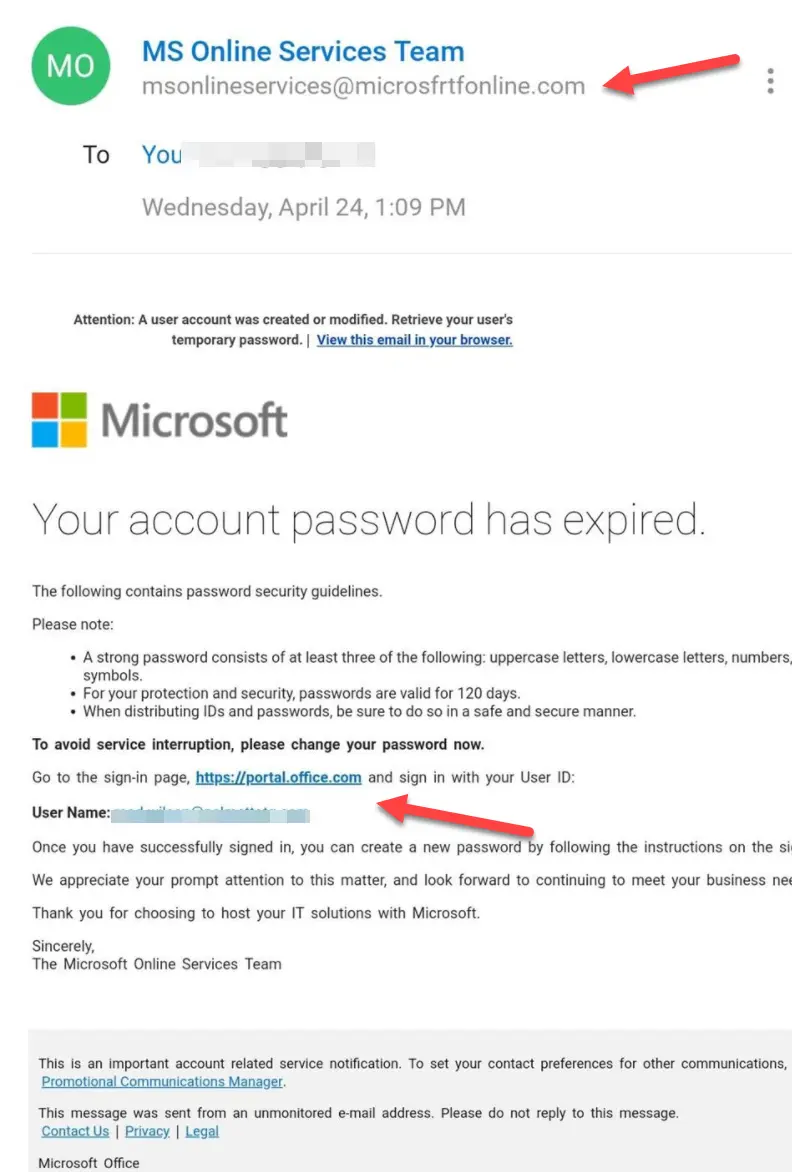
In this email, the attacker manipulates the victim into clicking on the malicious link within the email. This type of phishing attack is performed by convincing the employee to change the password by clicking on the link attached to the email.
Sender ID is suspicious: On a closer look, it can be noticed that the sender id is ‘microsfrtfonline’ which is not the actual sender id.
You can see more than what is visible: If you hover over the link provided in the email, a different email id will be displayed, and you will be able to notice that the link re-directs you to a website that is not Microsoft’s.
- Your IT support provider asks you to upgrade to the latest email outlook web apps
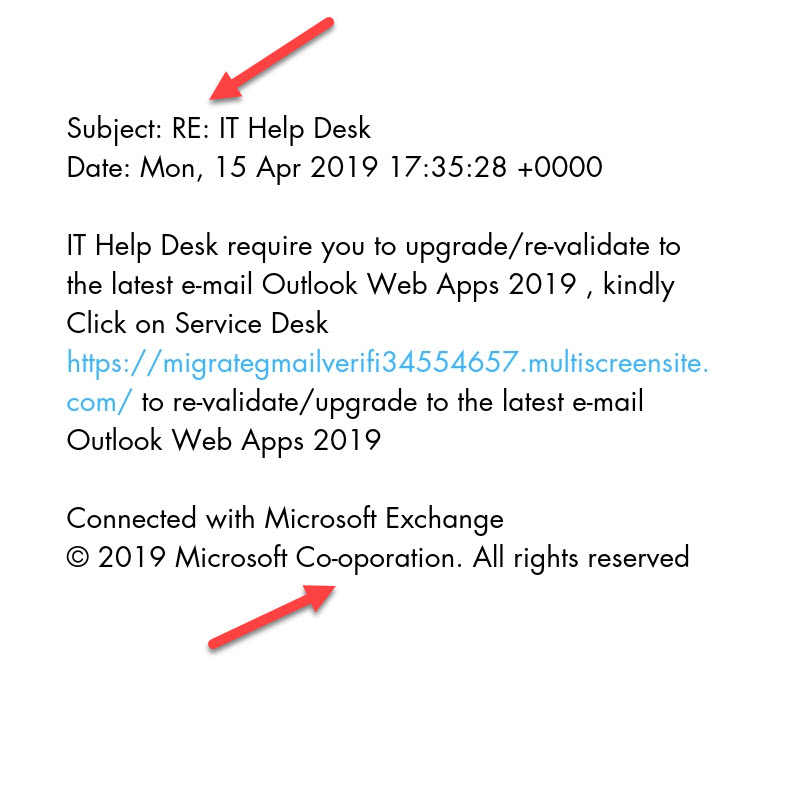
The attackers manipulate victims to revalidate or upgrade to the latest email outlook web apps by sending an email with “RE: IT Help Desk” as its subject line automatically increasing the credibility of the phished email.
Grammatical errors leave you suspicious: In most phishing emails, attackers do not pay attention to grammatical errors. Spelling errors and typos are very commonly found in a phished email.
- The attack mimics an email return path for stealing victims’ credentials
In this type, probable victims receive an email notifying them that the email has not been delivered.
Sense of Urgency: Such emails are designed in a manner that the victim is compelled to take prompt action. This is a real component of a non-delivery receipt and thus, it is important to verify the authenticity of an email.
Book a Free Demo Call with Our People Security Expert
Enter your details
A “Send Again” button out of nowhere: A send again button has also been provided in the email thus, subconsciously forcing the victim to click on the malicious link. However, an actual non-delivery receipt does not have this option.
How can organizations prevent such attacks?
Microsoft Office 365 is a cloud-based software as a service product that has been customized for business environments including Skype for Business Server, hosted Exchange Server, SharePoint, etc. With its increasing use, it becomes necessary for organizations to employ security measures that can help employees in identifying attacks that leverage Microsoft Office 365. This includes:
Implement policies related to cyber security within the organization that will effectively enhance the cyber security infrastructure of the organization. However, training and educating employees remains one of the most effective strategies in combating cyber-attacks.
With tools like TSAT, employees can learn about different cyber attacks and the methodologies that are used by attackers. This can be achieved with periodic cyber security and awareness training that can gradually develop employees’ immunity against cyber-attacks.
Co-Founder & COO at Threatcop
Department: Operations and Marketing
Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop’s mission to safeguard people’s digital lives.
Co-Founder & COO at Threatcop Department: Operations and Marketing Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop's mission to safeguard people's digital lives.
