The FBI has released a warning that threat actors have started impersonating Trusit, one of the largest US bank holding companies. According to the investigative agency, threat actors are using this spear-phishing campaign to infect the victims with Remote Access Trojan (RAT) malware.
A Bleeping Computer article mentions that according to the FBI, threat actors have also designed a phishing campaign. In that malicious campaign, they spoof this financial organization with registered domains, email subjects, and an application. This makes it look as if the emails came through the above-mentioned legitimate financial institution.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
The Instance
- In February 2021, a renewable energy company was targeted. In this attack, the phishing emails asked the user to download a malicious Windows app that imitated the legitimate Truist Financial SecureBank App. The email faked the last step needed by the company to complete the process behind a $62 million loan.
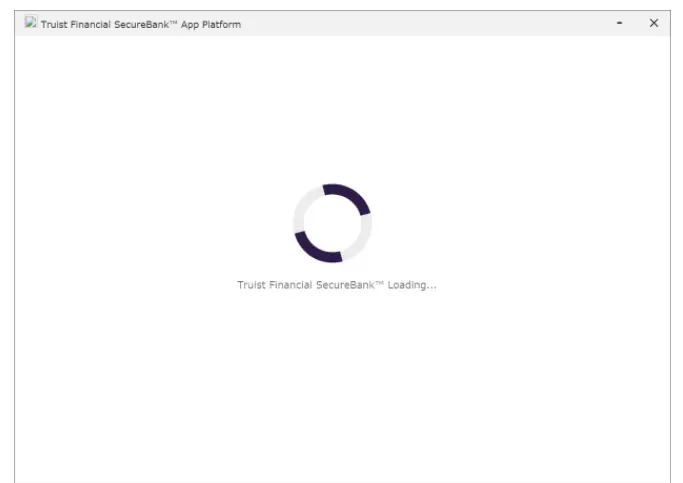
- The FBI added that the fraudulent loan amount was in line with the energy company’s business requirements. Further, the FBI stated that the phishing email also contained a link for downloading the application, a username, and a password for access.
- The phishing email appeared to have originated from a UK-based financial institution, stating that Truist’s loan to the victim was confirmed and it can be accessed through an application that appeared to belong to the Trusit.
- The malicious actors hosted this fake Windows app on a fraudulent domain registered that impersonated Truist.
- Some other financial institutions like MayBank, FNB America, and Cumberland Private also seem to have been impersonated by this spear-phishing campaign.
- It has been found that the malware gets deployed after users download and install the executable file in the spear phishing emails that they receive. It then connects them to secureportal(.)online domain.
- The FBI has informed through their warning that attackers are using this malware to log keystrokes and take screenshots of the users’ screens.
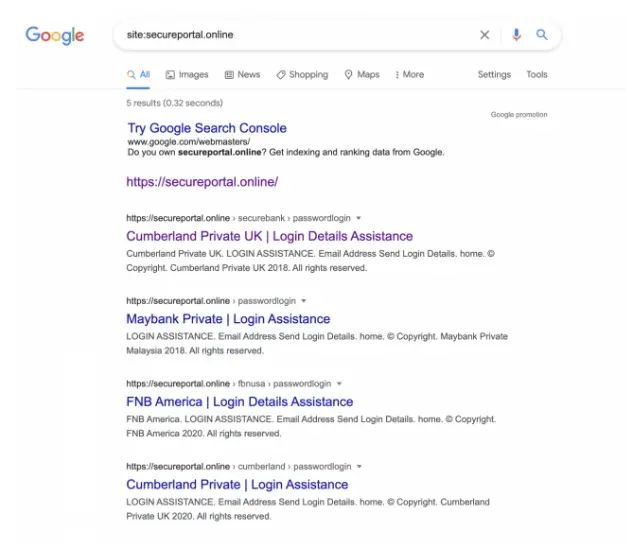
It has been seen that this spear phishing campaign has also been successful in impersonating other financial institutions in the US and UK.
Book a Free Demo Call with Our People Security Expert
Enter your details
It is noteworthy that the attackers can use the login credentials of the user to access very sensitive information of the organization which can potentially harm their business interests. Moreover, fake applications can be used to camouflage background malicious activities running in the background.
Read more about Understanding the Difference between Spear Phishing and Phishing

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
