Did you know that targeted emails or spear phishing attacks are used in 91% of successful data breaches and in 95% of network attacks in the enterprise? In a cybersecurity survey, 56% of IT decision-makers stated that spear phishing attacks are major security threats! But what are these “targeted” phishing attacks? Let’s proceed further to find out!
Table of Contents
ToggleThe Infamous Targeted Phishing Attacks
Today, around 91% of cyber-attacks are deployed using a spear phishing email and about 94% of these targeted emails consist of malicious file attachments that are the payload or source of malware. These targeted phishing emails have increasingly become the common way of deploying cyber-attacks to gain the personal information of vulnerable users.
These infamous spear phishing attacks are email scams that are targeted toward any specific individual or organization. The motive is to steal sensitive and financial information of the targeted victim for malicious reasons. This attack is deployed with well-prepared schemes of acquiring the victim’s personal information through available resources or information present online.
Book a Free Demo Call with Our People Security Expert
Enter your details
How Spear Phishing Work -Explained
These cyber attackers target victims who upload their personal information online, especially on social networking sites. By using a fake profile, they trace the targeted victim’s personal email address, geographic location, list of friends, or any recent purchases that they have made.
Once these cyber crooks get all the required information about the victim, they disguise themselves as a trustworthy source or entity to obtain the targeted user’s sensitive information by sending a spoofed email.
On the other hand, expert spear phishing attacks involve phishers impersonating a trustworthy organization or individual in an email address to make it look like a legitimate email. They make a plausible request to have the targeted user fall for the bait with valid email content.
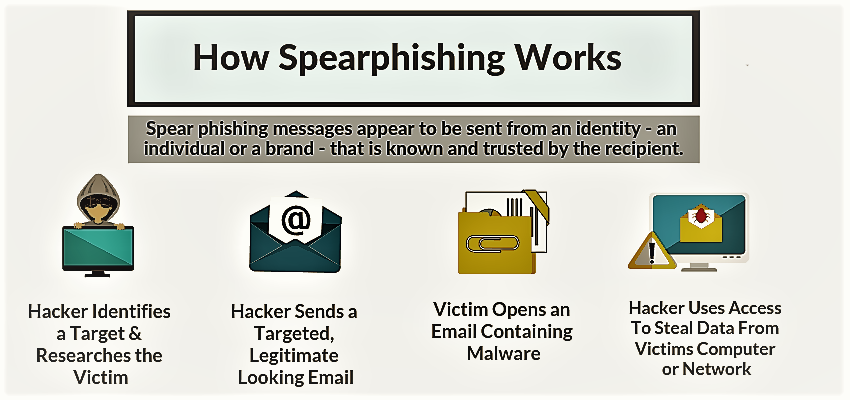
As for the increase in the success rate of spear phishing, the message contains attention-gaining urgent requests, explaining why sensitive information is required. Also, the victims are tricked to click on the malicious email attachments that redirect them to spoofed web pages or sites.
These fraud pages ask victims to provide their login credentials, account numbers, PINs, or access information to unauthorized files. In the aftermath of this process, these cybercriminals misuse passwords or sensitive information to access other websites that hold confidential information such as financial details related to credit cards.
With everything obtained, these cybercriminals become empowered to easily access the victim’s bank account or create a new identity by using all the information of the victim. This spear phishing also tricks targeted users into downloading malicious codes or malware attachments provided in the message.
How to Identify Spear Phishing Emails to Stay Secure?
Spear phishing attacks have become highly sophisticated and complex in nature nowadays. No matter how effective these attacks are, these following ways can help to spot spear phishing emails:
- Spoofed domain and sender’s address:
Spear phishing usually involves domain spoofing and impersonation of the legitimate identity in the email’s sender address.
- Email subject line:
Panic arising email subject lines include words like Request, Follow up, Urgent, Important, Payment Status, etc. that initiates a sense of duty to comply with the message request.
- Email content hygiene:
To spot a spear phishing email, check message content for grammatical errors or spelling mistakes as phishers usually leave complex clues, thinking these hidden clues would go unnoticed.
- Attachment landmines:
Hackers know how email attachments are easy bait for getting victims into clicking on a fake document or link regardless of the expectancy of the attachment.
Tips to Avoid Spear Phishing Attacks
According to cybersecurity researchers, spear phishing attacks are highly dangerous in nature as they are designed with the concept to get around the traditional email security filters. These emails typically do not include malicious attachments. Instead, they use email spoofing techniques along with social engineering tactics that are less likely to be blocked.
But with the advanced cybersecurity tools and solutions, preventing phishing attacks is possible! Here are the best five ways to help you prevent spear phishing emails from landing in your email inbox:
- Implementation of Email Authentication Protocols
What could be better than implementing DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an email authentication protocol to prevent these email-based attacks? The DMARC relies on two main established email authentication standards, SPF (Sender Policy Framework) & DKIM (DomainKeys Identified Mail). This authentication protocol analyses the email against the database to check if any record matches the sender’s email. In case it doesn’t then the email is rejected and the report is submitted to the security administrator. DMARC ensures that no fake or spoofed email reaches end-users.
2. Multi-factor Authentication (MFA)
Using multi-factor authentication for emails can surely help in mitigating the risk of falling to spear phishing attacks. It is an extra layer of security for the data of users. In case if a hacker holds any information, it will need to bypass this layer of security which will lead to two steps of identification. MFA asks for a randomly generated token from the user or a one-time password or an extra login to ensure that the accessing user is a legitimate identity.
3. Risk Assessment
For any organization, it is important to take a cybersecurity risk assessment to find out the level of vulnerability existing in the working environment. A cybersecurity risk assessment is a better way to identify the cyber threat posture of an organization by running phishing simulation attacks on employees. Employees are the most vulnerable resource and the weakest link in the cybersecurity chain of an organization.

In order to turn them into the strongest link and help them in recognizing phishing emails, it is important to provide them with proper cyber security awareness training. There are various leading risk assessment tools that offer to train employees with phishing attack simulations and knowledge imparting spear-phishing awareness and other cyber attack vectors.
4. Verify Suspicious Emails
If you receive an email that looks too good to be legitimate, make sure to get it verified by the IT security team of your organization. Or for a better and easier way, use incident response tools to get all the suspicious-looking emails verified and avoid them from landing in your inbox again. Spear phishing security tools like phishing incident response tools allow users to report emails that look fraudulent in nature in real-time.
5. Don’t Respond Immediately
A lot of email scams use panic-creating email content that raises the sense of urgency within the user to respond to that email. Such emails either ask for sensitive information like account details, passwords, and credit card details, or ask users to click on the malicious email attachments. It is important to read and give a second look at such suspicious emails before falling for them. Be careful in checking for the sender’s email address and verifying the email’s content.
Cybersecurity is a two-way street. In order to keep your organization safe and secure, it is important to implement and follow cybersecurity best practices!
Let us know what are your suggestions on spear phishing in the comments section below.
Thank you for stopping by to read this blog, we hope that you had a good read!
