A hacker group, OilAlpha, which appears to support Houthis in Yemen has targeted humanitarian and international organizations in the Arabian Peninsula via using phishing techniques on WhatsApp. Allegedly, the threat actors are targeting organizations connected to media, non-governmental activities, international humanitarian efforts, and development sectors. It is nearly certain that the targeted entities had common interests in Yemen, security, humanitarian aid, and reconstruction initiatives. A cybersecurity firm that had been tracking OilAlpha’s ongoing hacking campaign since May 2022 reported the attack.
Table of Contents
ToggleSubscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Recorded Future’s threat research division, Insikt Group, which has been tracking OilAlpha’s activities, claims that OilAlpha has targeted people who are pro-Saudi Arabian government-led negotiations. OilAlpha is using spoofed Android applications. The spoofed applications impersonate organizations working with the UAE humanitarian entity, the Saudi Arabian government, and others OilAlpha is suspected to be pro-Houthis because it targeted only individuals the Houthis wanted to engage with directly.
You can also read – WhatsApp Phishing: Rising Threat Via Instant Messaging App
How did OilAlpha Carry Out Phishing Attacks Through WhatsApp?
OilAlpha sent malicious Android files to political representatives and Journalists on WhatsApp. OilAlpha suspected of pro-Houthi ties after phishing attacks targeted Houthis’ targets. The hacking group target Android phones which people in the region widely use. Let us see how they sent the malicious files.
- OilAlpha used the Public Telecommunications Corporation (PTC), a Yemeni government infrastructure under the direct control of the Houthi authorities.
- The phishers group launched a phishing campaign through WhatsApp which is an encrypted chat messenger.
- The phishing campaign was carried out using URL shorteners in the messages on Android devices and the victims were Arabic-language speakers.
- The messages contain long Arabic messages and a WhatsApp documents file that had a malicious link along with an image of a government document.
Here is a free tool to check any suspicious link : Phishing URL Checker
Whatsapp Messages from the Hackers
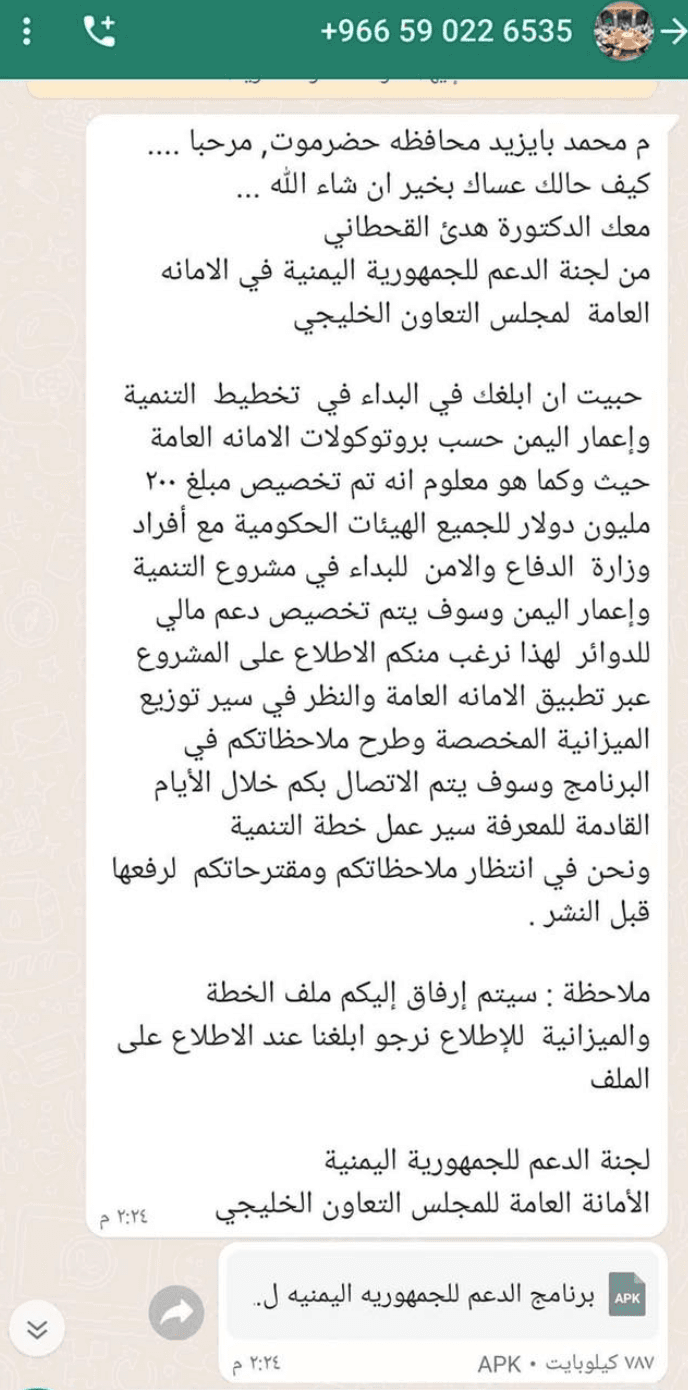
It has been claimed that the njRAT samples are in touch with C2s associated with this group which indicates that it may continue using other malware for operating attacks. It seems that the attackers may target individuals and entities supporting Yemen’s political and security developments along with other non-governmental organizations operating in the country.
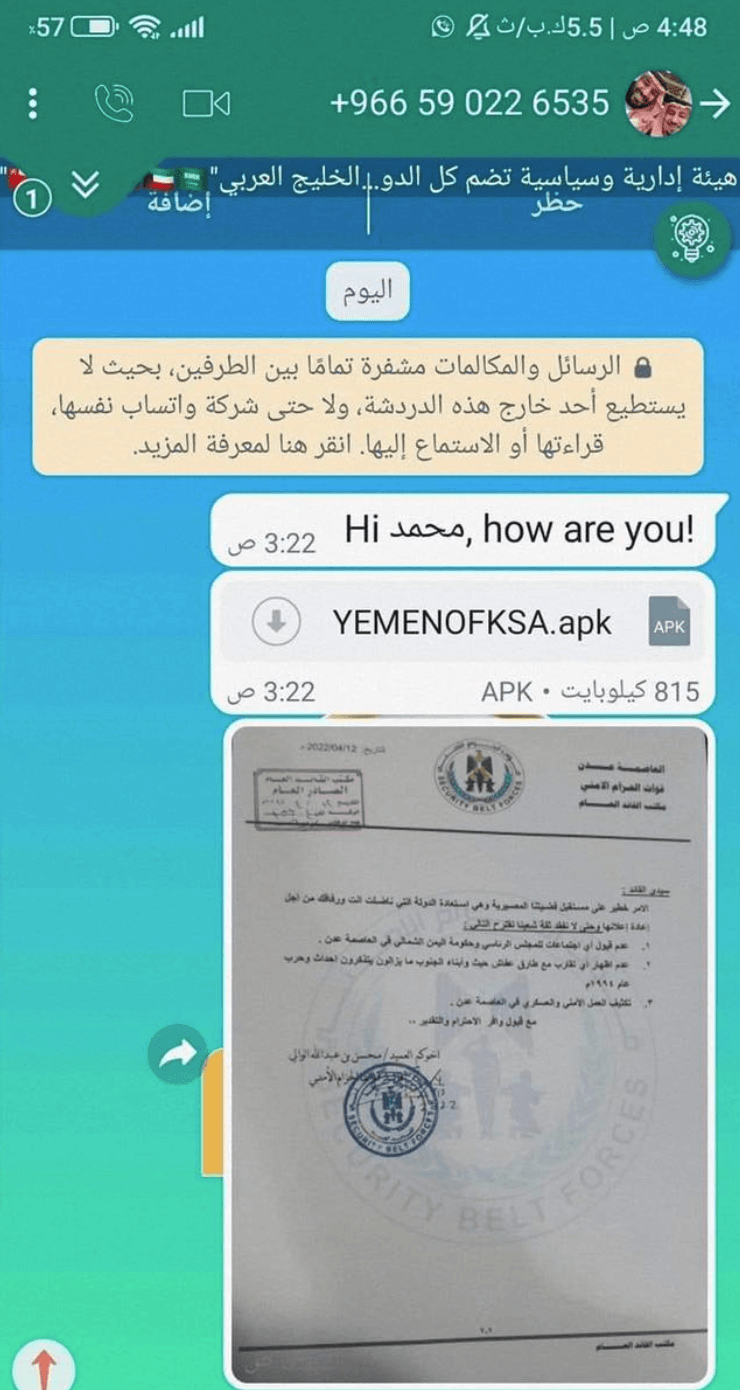
OilAlpha was more likely planning espionage activities as they used Remote Access Tools (RATs) like SpyMax and SpyNote to execute this phishing attack. Both the RATs SpyNote and SpyMax can be very harmful as they have the ability to access the device’s camera and audio, SMS data, call logs, network information, contact information, and GPS location data.
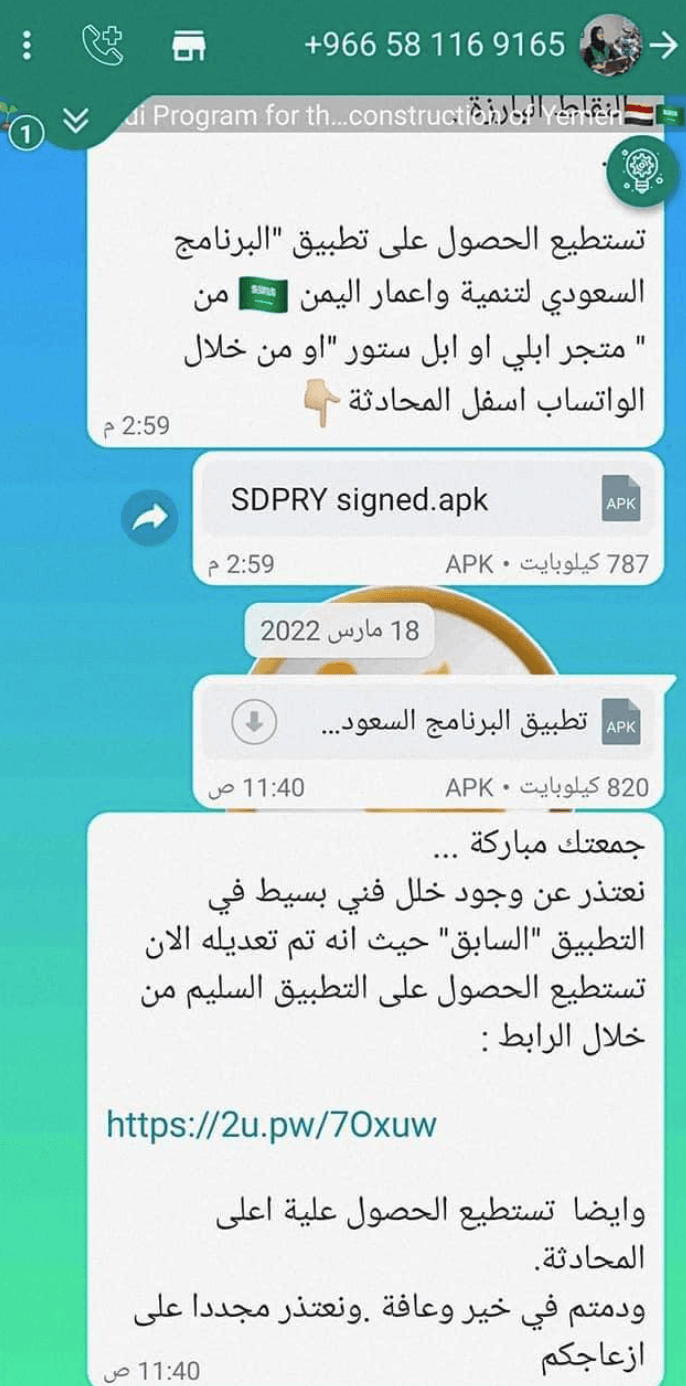
Not just the journalist and political representatives, the hackers’ group have also targeted non-governmental organizations that conduct or coordinated disaster response and human work in Yemen. OilAlpha has spoofed applications of organizations such as the Norwegian Refugee Council, the United Nations Children’s Emergency Fund, and the Red Crescent Society. However, the group appears to have purposely didn’t give any effort to hide its infrastructure. The group’s exclusive use of dynamic DNS further provides a significant clue for attribution purposes.
Did OilAlpha Succeed in its Operations?
There is no such representation of how successful OilAlpha got in the ongoing campaign but it has been alleged that the hacker group has also spoofed other Saudi Arabian firms after noticing the icons of entities in the malware. The organizations include King Salman Humanitarian Aid, King Khalid Foundation, Relief Centre, and Project MASAM.
The applications of organizations that manage disaster and humanitarian work in Yemen were also attacked by the OilAlpha such as Norwegian Refugee Council, Red Crescent Society, and the United Nations Children’s Emergency Fund.
The report mentioned that there is still a lot more to find out to back up that back Yemeni operatives are behind the ongoing phishing campaign by OilAlpha. John Condra, Director of Strategic and Persistent Threats at Insikt Group said, “Uncertainly, it is difficult to determine if there has been any compromise of those assets and consequently, it is possible that foreign threat actors are utilizing them.”
He further stated that it is not clear yet that they are selling their infrastructure to other attackers and may be using it to target individuals of their interest. Outsiders like Iraqi Hezbollah, and Iranian and Lebanese hackers are favoring Islamic Revolutionary Guard Corps as they have a vested interest in the outcome of the civil war, which resulted in this threat.
How can Organizations Prevent WhatsApp Phishing Attacks?
To prevent phishing attacks through WhatsApp, organizations should prioritize employee awareness and training, educating them about the risks associated with WhatsApp phishing and providing guidance on identifying and handling suspicious messages. Organizations must employ WhatsApp phishing simulation and awareness training solutions to transform their employees into the strongest defense against such attacks.
Book a Free Demo Call with Our People Security Expert
Enter your details
Implementing strong security policies, including the use of strong passwords and discouraging the sharing of sensitive information, is crucial. Enabling two-factor authentication (2FA) adds an extra layer of security to WhatsApp accounts. Additionally, employees should verify the authenticity of senders before responding to messages, using alternative communication channels to confirm their identity when dealing with requests for sensitive information or financial transactions. These measures collectively enhance protection against phishing attacks on WhatsApp.
FAQs: WhatsApp phishing attack on Yemen-Related Entities
Hackers deploy malware using attack vectors, and then execute it to gain access to a system or server. OilAlpha employed one of the most common social engineering techniques phishing through WhatsApp. The hacker sent messages containing long Arabic messages and a documents file that had a malicious link.
There is not much information available about the OilAlpha hacker group. The Insikt Group alleges that OilAlpha has targeted individuals who support Saudi Arabian government-led negotiations. It appears to support Houthis in Yemen and has targeted humanitarian and international organizations in the Arabian Peninsula via using phishing techniques on WhatsApp.
The hacker group has also spoofed other Saudi Arabian firms after noticing the icons of entities in the malware. The organizations include King Salman Humanitarian Aid, King Khalid Foundation, Relief Centre, and Project MASAM. OilAlpha also attacked the applications of organizations that manage disaster and humanitarian work in Yemen, such as the Norwegian Refugee Council, the Red Crescent Society, and the United Nations Children’s Emergency Fund. It has also spoofed applications of organizations such as the Norwegian Refugee Council, the United Nations Children’s Emergency Fund, and the Red Crescent Society.
Train employees to recognize phishing messages. Phishing messages manipulate you into taking action by using unexpected content and employing social engineering techniques. Employees should be aware of these methods. WhatsApp Phishing Simulation and Awareness Training can be the only way to protect your organization from WhatsApp phishing.
