A cryptocurrency is a form of digital currency widely regarded as the future of the international exchange of currencies. The most popular types of cryptocurrencies include Bitcoin, Ripple, and Cardano. In recent years, threat actors often demand ransom or wire digital transfers in the form of cryptocurrencies during cyber attacks or, more specifically, ransomware attacks. The purpose of demanding a ransom in the form of this digital currency is to try to keep the transaction anonymous as it is not easy to decrypt the blockchain element and get the information of who received the transaction. And these blockchains can be hacked, it is called a cryptocurrency attack.
Table of Contents
ToggleNotably, many developments have taken place in the crypto world, such as NFT and Metaverse. Now, digital artists are creating NFT, and many people are getting robbed online through them. In this blog, we will discuss all the aspects of cryptocurrency attacks that are wreaking havoc on the digital world. But before that, let us understand more about cryptocurrency.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is Cryptocurrency?
Cryptocurrency emerged as an alternative form of currency that would revolutionize the global economy. The concept of cryptocurrency was to create a decentralized means of conducting currency transactions that could not be controlled by the government. Over the years, cryptocurrencies and other forms of digital currency have developed and evolved based on a modern technology called a blockchain. The concept of a blockchain is to create an encrypted node of online storage that can contain some digital information, and each of these blocks has a certain value based on the meaning it has or the entity it represents.
Book a Free Demo Call with Our People Security Expert
Enter your details
What is Cryptocurrency Attack?
A currency unit that is represented by an encrypted information string is known as a cryptocurrency. So, a peer-to-peer network monitors and organizes those cryptocurrencies, known as the blockchain. In addition to transactions, blockchain acts as a secure ledger for buying, selling, and transferring assets.
Cryptocurrencies are Decentralized Finance (DeFi) that are not issued by any financial institutions or governments. Cryptographic algorithms are used to create and secure cryptocurrencies, and this process is known as mining. Here the transactions are processed and validated by a computer network or other specialized network, like application-specific integrated circuits (ASICs). The procedure incentivizes the cryptocurrency miners who power the network.
Nowadays, cryptocurrencies have become a huge target for hackers. It can be a little tricky to initially identify a cryptocurrency cyber attack. So organizations should know how hackers employ the attack.
How Does a Cryptocurrency Attack Work?
Hackers primarily use one of two techniques to steal cryptocurrency: either they steal it outright or trick users into giving it to them. When individuals or organizations would like to invest in cryptocurrencies, they often use a blockchain exchange.
The blockchain exchange procedure entails opening an account and funding it with money that has been converted into the desired digital currency. The exchange is the only one with exposure to the private keys that are used to regulate and store the cryptocurrency in a custodial wallet. Custodial wallet services hold onto the private key, so they are responsible for safeguarding the funds.
Traditional banks hold a limited amount of cash. However, blockchain exchange networks only maintain adequate crypto in the hot wallets to help with transactions. Hot wallets are made to store cryptocurrency online, while cold wallets purchase the private keys that are required to access cryptocurrency offline.
The government today lacks the financial protocols necessary to protect cryptocurrency deposits if an exchange is closed, unlike centralized banks. When cybercriminals target an exchange, crypto users usually lose their digital investments. Due to the nature of blockchain networks, it is almost always impossible to recover stolen money.
A Notable Cryptocurrency Attack (2022)
According to a new Federal Trade Commission report, a cryptocurrency attack stole over $1 billion from 46,000 people in 2021.
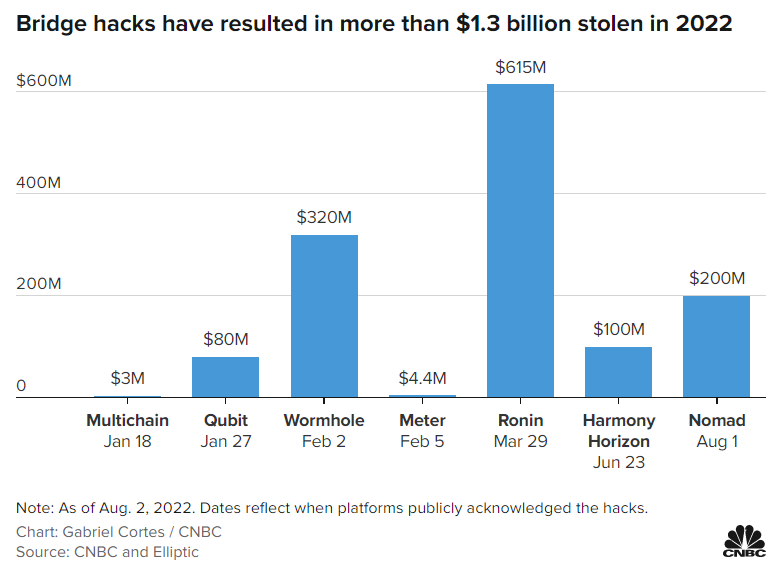
According to reports, hackers have stolen about $3 million from Multichain in a cryptocurrency attack. Lorenzo Franceschi-Bicchierai, a reporter for Vice magazine, tweeted that “the hack against Multichain users keeps getting worse.”
A decentralized finance (DeFi) platform, “Qubit Finance,” also became a victim of a cryptocurrency cyber attack. They stole $80 million worth of cryptocurrency. Qubit Finance acknowledged the hack through a report published on Medium and a tweet. The hack allegedly took place on the evening of January 27 at around 5 p.m. ET.
The Wormhole, one of the most well-known bridges connecting the Ethereum and Solana blockchains, experienced the theft of cryptocurrencies valued at over $320 million on February 2, 2022. After some time, Wormhole stated that “all funds have been restored,” and they offered $10 million (a bug bounty) to the hackers.
Meter, a blockchain network, reported a cryptocurrency attack for $4.4 million on the network. They tweeted about the attack.
The popular blockchain Axie Infinity’s Ronin network posted a blog about a cryptocurrency attack for $615 million. The breach was confirmed on Ronin’s official Discord channel and Twitter account.
A blockchain network, Harmony has reported a cryptocurrency attack for $100 million. Researchers are linking the attack to the infamous Lazarus Group. Harmony offered a $1 million bounty to the attackers.
One more organization becomes the victim of a cryptocurrency attack, Nomad. They lost nearly $200 million in the attack. Nomad promised not to file legal complaints against parties that returned at least 90% of the money and said it would pay up to 10% of the money that hackers had stolen in digital form.
How Can One Prevent Cryptocurrency Attacks?
Cryptocurrency attacks are challenging to detect. Since the majority of cryptocurrency mining operations are frequently covered by legitimate processes, it is also challenging to identify the source of excessive CPU utilization. Therefore, safeguarding against malware and dangerous scripts is the best strategy to stop cryptocurrency attacks.
Organizations should follow some practices to protect their data and assets from cyber attacks, based on the principle that prevention is better than cure.
Use Two-Factor Authentication for your Exchange
Two of the simplest defenses against these attacks are to make sure your cryptocurrency is purchased securely first, and then to enable two-factor authentication (2FA) for withdrawals. Every time you withdraw cryptocurrency, 2FA makes you enter a code from your phone. When you want to withdraw money, it can be inconvenient if your phone’s battery is dead or you have to get it from another room. However, it could also prevent you from losing your cryptocurrency if an attacker gains access to your account.
Withdraw Your Crypto
When you initially buy a cryptocurrency, it is typically purchased through an exchange account. If an attacker gains access to the exchange account, they can withdraw your cryptocurrency to a wallet address that they own. One way to protect yourself from a cryptocurrency attack is by simply withdrawing your cryptocurrency first from the exchange. You can withdraw through your wallet and set it up on your PC as well. Then command your exchange to transfer your crypto to a new Walleye address.
Don’t Enter Your Seed Words on a Website
If it’s your first time buying cryptocurrency, then you should know what seed words mean. It is a string of letters and numbers from which you can cryptographically deduce all of your account keys. If your device crashes, you can recover your crypto wallet using these words. It is also known as the “master key” or “secret recovery phrase.” So keep in mind that you need to keep this phrase safe. Don’t enter this on any website to keep yourself safe from a cryptocurrency attack.
Use a Strong Password for your Crypto
The very first step to keep your password safe is to ensure it is strong, complex, and difficult to guess. When an attacker is deploying a cryptocurrency attack, they know that they can steal millions of dollars. So, they know the password is going to be pretty complex. Take your time while creating the password and change it within a 90 day.
Check the URL and Fake Applications
When deploying a cryptocurrency attack, the most common way for attackers to succeed is to convince the victims to download fake wallets or fake applications. Scammers use fake versions of popular wallets for the attack. The best way to prevent it is to get your wallets and applications directly from the developer’s websites.
Beware of Email Files
Email threats are a very common threat in cyber attacks. To not fall into the attacker’s trap, proper email security techniques need to be applied in your organization. Get your organization’s email authentication protocol or phishing incident response tools. It will help to keep track of which emails are authentic and which are malicious.
Role of Security Awareness in Improving Vigilance
One can easily comprehend from the complete reading that cybersecurity practices are the best defense available. No matter what equipment you have at your disposal, the biggest target of cybercriminals is humans. And several statistical reports have shown similar data that suggests that threat actors are carrying out huge numbers of cyber attack attempts targeting humans employing social engineering attacks.
Organizations should explore various mechanisms to make sure their employees are well-trained. We have already comprehended from multiple perspectives that there are multiple benefits and purposes of security awareness training tools in the organization.
TSAT from Threatcop provides a complete learning management system for security awareness training for employees. The tool provides a platform for creating attack templates that allow the trainer to make a customized attack. This tool is used to simulate dummy attacks on the employees to give them a real-time experience of cyber attacks. This tool provides a complete cybersecurity knowledge base and defense learning for employees.
