Just imagine: A single wire transfer in 2024 resulted in a loss of $2.7 million in the U.S.-based manufacturing firm. The email appeared to be very legitimate, being sent from the CEO’s address. The format was exactly like the earlier communications, and the email discussed an ongoing project. It asked for an urgent payment to a vendor’s new bank account. The employee who dealt with transfers didn’t have any idea that it was a scam and processed the request within 30 minutes.
Table of Contents
ToggleThe most dangerous part is that the breach wasn’t even detected for several days, as no systems were compromised, no malicious attachments involved. No viruses, no ransomware, no phishing links, it was just Business Email Compromise, and it worked without any flaws!
What is Business Email Compromise (BEC)?
An email fraud which is not something ordinary, rather it is quite sophisticated and uses social engineering, impersonation and psychological manipulation to trick individuals can be referred to as Business Email Compromise (BEC). The victim often belongs to the finance or HR department, as the goal is usually to transfer funds or confidential data.
Some major characteristics of BEC are mentioned below:
- No involvement of any malware or phishing links
- The usage of spoofed or compromised real accounts is quite common
- Leverages urgency, trust, and authority
- Frequently targets high-stakes workflows like vendor payments, salary deposits, or contract approvals
BEC scams usually involve:
- Executive Impersonation – “The CEO needs this done right now.”
- Vendor Spoofing – “We’ve changed our banking details; please update soon.”
- Payroll Redirection – “I have changed my banking account; please update before payday.”
This usually doesn’t involve much technology and that’s why it is quite difficult to detect. It doesn’t make use of any traditional indicators of compromise.
Book a Free Demo Call with Our People Security Expert
Enter your details
“Secure” Organizations; but Still BEC Works: Why?
When it comes to the investment in cybersecurity, it is billions. Still, BEC continues to thrive; shocking, right? Let’s understand why:
BEC preys on:
- The email looks like it is sent from a very trustworthy source of contact. For instance, if an email is sent from your boss or a genuine vendor; would you not act? Yes, you would, and this increases the chances of a successful attack.
- Using phrases like “ASAP,” “today,” or “EOD”, attackers create a sense of urgency, and this creates a scenario for the victims where the attackers bypass second-guessing.
- Power distance bias is another important factor. Employees are conditioned to act quickly on executive requests without challenging them.
And it bypasses:
Traditional Control | Why It Fails Against BEC |
Spam Filters | Content isn’t malicious or flagged; no links, no attachments |
Link Scanners | Many BEC emails contain no links at all |
Multi-Factor Auth | Doesn’t apply to spoofed or compromised external email domains |
Awareness Campaigns | Too generic; lack role-specific or scenario-based training |
Firewall Rules | Irrelevant against psychologically driven social engineering attacks |
Almost all security stacks are designed to detect what is dangerous, but when it comes to who seems dangerous, there are drawbacks.
3 Most Common BEC Attack Types
1. CEO Fraud / Whaling
Also known as “whaling,” this type of attack involves impersonating a senior-level executive. It can be a CEO or CFO. They may be sending direct instructions to subordinates in the finance department. A scenario will make it easy for you to understand how it works.
Scenario:
A spoofed email from “[email protected]” asks the finance head to wire funds to finalize a merger with a new vendor. The tone is quite urgent, professional, and confidential.
2. Vendor Email Compromise
In this type of attack, a real vendor’s mailbox is compromised by the attackers at the first step, and as the second step, they may send a payment update from the legitimate domain. Have a look at a scenario now.
Scenario:
You receive an invoice for a routine payment from the legitimate account of the vendor, but he asks it to be wired to a new account. This new account is that of the attacker, and you have no clue of all these, as the sender is trustworthy.
3. Payroll Diversion Scams
In this type of attack, the HR or payroll receives a fake email regarding the updating of the direct deposit information.
Scenario:
The attacker impersonates an employee. In most cases, it is a new hire or a remote worker. They make a request to send their salary to a different account. They may give reasons like they have lost access to the old one.
Could Your Team Detect This?
Let’s have a look at a very realistic example.
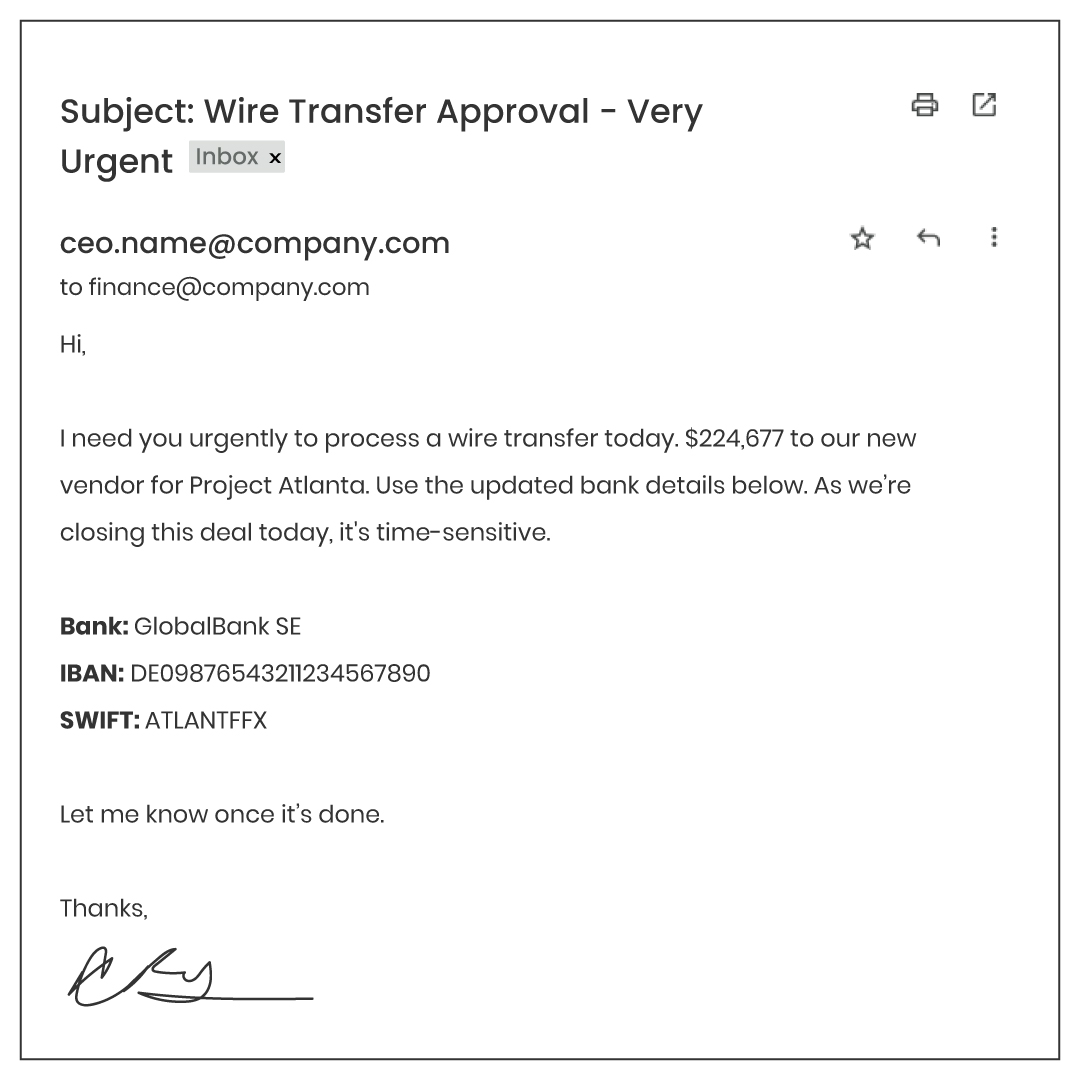
What seems legitimate:
- Known sender name and email structure
- References a real project
- Familiar tone and urgency used in past emails
- Professionally written with no grammar issues.
What’s suspicious:
- New bank details without official notice
- Unusual isolation of the request—no CC to project lead or finance director
- No invoice or supporting documentation
A trained employee would:
- Verify the request through an alternate channel (e.g., direct call or secure messaging)
- Report the email using the Threatcop TPIR plugin.
- Cross-check banking instructions with vendor records
Why Your CFO and GRC Teams Should Care
You must keep in mind that Business Email Compromise is not a technology problem; it’s a trust problem. It exploits people and business processes, not just systems. Have a look at the points mentioned below to understand the urgency:
- FBI reports estimate over $50 billion lost globally due to BEC since 2013
- It often results in quiet financial losses, not ransomware headlines.
- Recovery is difficult, especially with international wire transfers.
- Even publicly traded companies have admitted falling victim, damaging their reputations and stock prices.
BEC scams are low-cost, low-risk, and highly scalable, and this is what makes them a preferred tactic for both cybercriminals and nation-state actors.
The People-Centric Defense Strategy: Threatcop’s AAPE Framework
To be very frank, it is never possible for tech to solve BEC alone. A resilient defense starts with people, process, and layered protection, and this is exactly where Threatcop’s AAPE framework comes in:
1. Assess (TSAT)
→ Explore TSAT Product Page
- Simulate BEC attacks using:
- Real invoice templates
- Tone-mimicked executive emails
- Changed banking details
- Track how employees react under pressure
- Identify who’s most vulnerable and why
2. Aware (TLMS)
→ Explore TLMS Product Page
- Deliver role-specific training and security awareness games for finance, HR, executives, and assistants
- Train teams to spot:
- Tone or language anomalies
- Inconsistent sender domains
- Requests that break established protocols
- Reinforce behavior change with microlearning and feedback loops
3. Protect (TDMARC)
→ Explore TDMARC Product Page
- Block spoofed emails with DMARC, DKIM and SPF authentication
- Prevent lookalike domains from reaching employees
- Use BIMI to visually confirm legitimate senders
- Integrate with threat intel feeds to detect domain spoofing attempts
4. Empower (TPIR)
→ Explore TPIR Product Page
- Give employees a one-click reporting button inside their inbox
- Allow reporting of BEC emails even when there’s no malicious file or link
- Feed reports into simulations and policy reviews
- Create a feedback loop between awareness, action, and escalation
Final Thought: BEC is About Seconds; Not Systems
“BEC doesn’t need a virus to succeed—just a split-second of misplaced trust.”
It is high time that security leaders need to rethink how they approach email protection. Spam filters and MFA are no longer capable of stopping a well-crafted impersonation.
It’s time to evolve from inbox filtering to human-layer defense:
- Simulate the multiple attack vectors (TSAT)
- Train people with multiple content formats and security awareness games (TLMS)
- Authenticate every domain (TDMARC)
- Empower reporting and intervention (TPIR)
As organizations take steps towards such a defense, Business Email Compromise is no longer a worry. Still wondering where to start? Get in touch with cybersecurity experts today!

Director of Growth
Naman Srivastav is the Director of Growth at Threatcop, where he leads customer-facing and product marketing teams. With a self-driven mindset and a passion for strategic execution, Naman brings a competitive edge to everything he does — from driving market expansion to positioning Threatcop as a leader in people-centric cybersecurity.
Director of Growth Naman Srivastav is the Director of Growth at Threatcop, where he leads customer-facing and product marketing teams. With a self-driven mindset and a passion for strategic execution, Naman brings a competitive edge to everything he does — from driving market expansion to positioning Threatcop as a leader in people-centric cybersecurity.
