Your inbox can be a minefield. As a renowned US foreign policy expert, your insights are valuable, making you a target for cybercriminals like TA427. Cyber espionage groups like TA427 exploit trust and expertise to gain access to sensitive information. A cybersecurity company recently exposed how TA427 operates, and in this blog, we’ll explore their methods to help you stay alert and safeguard your valuable insights.
Table of Contents
Toggle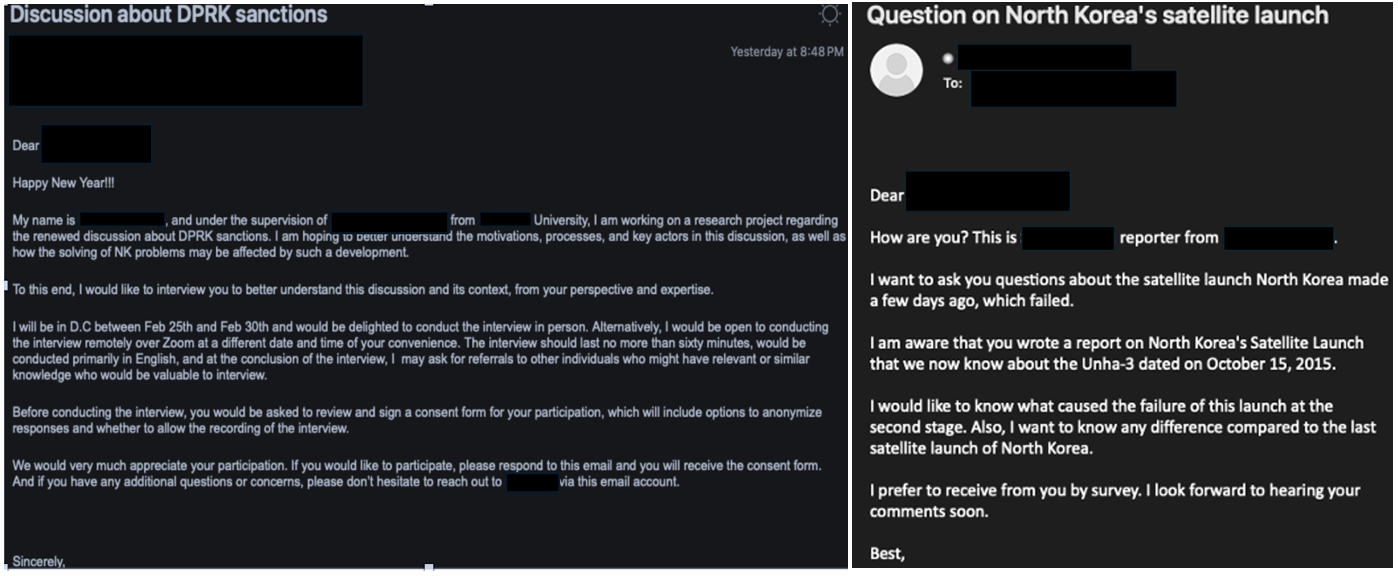
Who is TA427?
TA427, also known by names like Emerald Sleet, APT43, THALLIUM, or Kimsuky, is a cyber threat group that stands out due to its association with North Korea (officially the Democratic People’s Republic of Korea, or DPRK). This group works to support the North Korean Reconnaissance General Bureau and is especially active in using email phishing to target individuals who are knowledgeable about US and South Korean (ROK) foreign policy. Over the years, researchers have tracked TA427’s activities, noting their persistent and adaptable nature in the realm of cyber espionage.
What Makes Them Different?
The primary goal of TA427 isn’t financial gain, which is often the motive behind many cybercriminal activities. Instead, this group aims to gather information and exert influence. They focus their efforts on individuals in academia, journalism, and independent research, especially those who are experts on North Korea. By impersonating these experts, TA427 cleverly gains access to their professional networks and colleagues. This tactic allows them to embed themselves within organizations for long-term intelligence gathering.
Book a Free Demo Call with Our People Security Expert
Enter your details
Since 2023, TA427 has been actively engaging with foreign policy experts, asking for their opinions on sensitive topics like nuclear disarmament and US-South Korea policies through seemingly harmless emails. These initial contacts are designed to start conversations and establish trust. In recent months, researchers from a cybersecurity firm observed a consistent and sometimes increasing stream of such activities.
TA427’s Deception Techniques
TA427’s success hinges on social engineering, the art of manipulating people to share information or grant access. They have seen employing a variety of social engineering techniques and frequently changing their email infrastructure to stay undetected. Here’s how they craft their attacks:
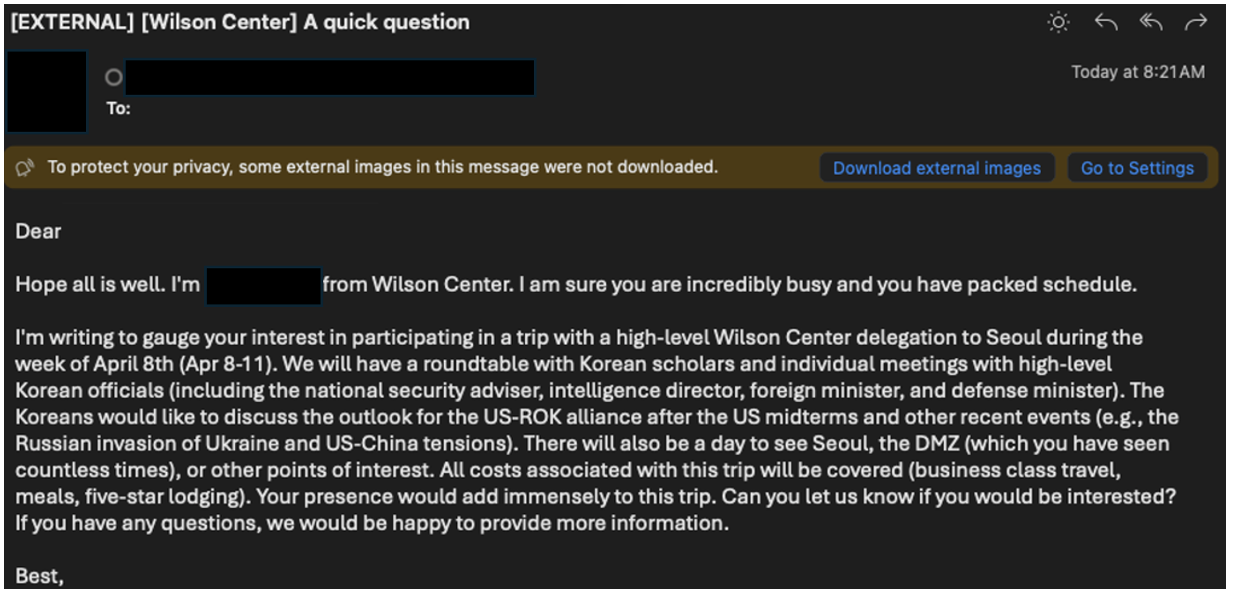
Social Engineering: They impersonate credible individuals through email. These emails might appear to be from a known colleague, researcher, or journalist, creating a sense of trust.
Exploiting Weak DMARC Policies: Notably, in December 2023, the group started exploiting weak DMARC (Domain-based Message Authentication, Reporting, and Conformance) policies to better impersonate various personas. DMARC is an email authentication standard. By exploiting lax DMARC policies, TA427 can spoof email addresses, further enhancing their impersonation tactics. The group can send emails that appear to come from trusted sources, thereby increasing the likelihood of recipients interacting with malicious content
Web Beacons: These tiny hidden elements embedded in emails can track a recipient’s activity when the email is opened. In February 2024, TA427 incorporated web beacons, potentially to gather information about the recipient’s device or location.
Essential Signs of a Deceptive Email
Unexpected Emails from Familiar Names: Be wary of emails, even from seemingly known senders, requesting sensitive information or unusual actions.
Sense of Urgency: Phishing emails often try to create a sense of urgency to pressure the recipient into acting without thinking critically.
Suspicious Links or Attachments: Never click on links or open attachments from unknown senders, even if they appear legitimate.
Why DMARC is Your Ultimate Defense Against Email Spoofing and TA427
Cyberattacks by TA427 are focused on a critical vulnerability: weak DMARC policies. DMARC is an email authentication protocol that thwarts domain impersonation of an organization while trying to phish. Here’s how DMARC empowers you to fight email spoofing and the tactics used by TA427:
Stops Spoofing in its tracks
DMARC makes it simple to define how mail servers should handle messages that fail the authentication checks.
Make sure the DMARC policy is enforced strictly (e.g. p=reject), so that there is an opportunity for spoofed emails trying to directly impersonate your domain to be rejected in the first place, making it less likely you are now a target for impersonation by TA427.
Sees Through Deceptive Tactics
TA427 uses permissive DMARC policies (p=none) to bypass the security checks and make sure their spoofed email gets into the inbox. A strict DMARC policy would catch such attempts, and a warning about potential risks would come your way.
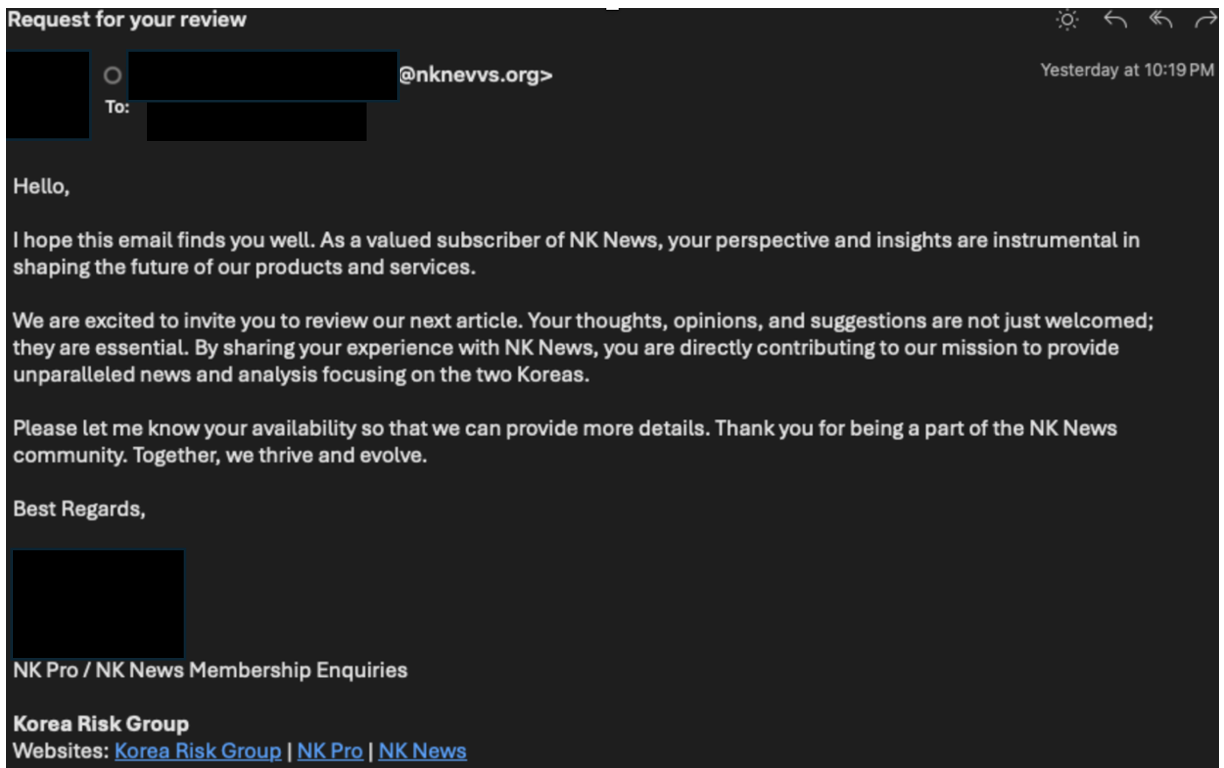
Exposes Misleading ‘Reply-To‘
To make their act more real, TA427 miscreants sometimes use free email addresses in the field “Reply-To.” DMARC reports just show such contradictions, shedding light on both the origin of the email and the sender’s address displayed.
Stop BEC Attacks and Protect Your Brand with TDMARC
Imagine a scenario where a fraudulent email, disguised as coming from your CEO, lands in your employee’s inbox. This email could request a wire transfer, contain a malicious link, or trick your employee into divulging sensitive information. This is a classic example of a Business Email Compromise (BEC) attack, and it can be devastating for organizations.
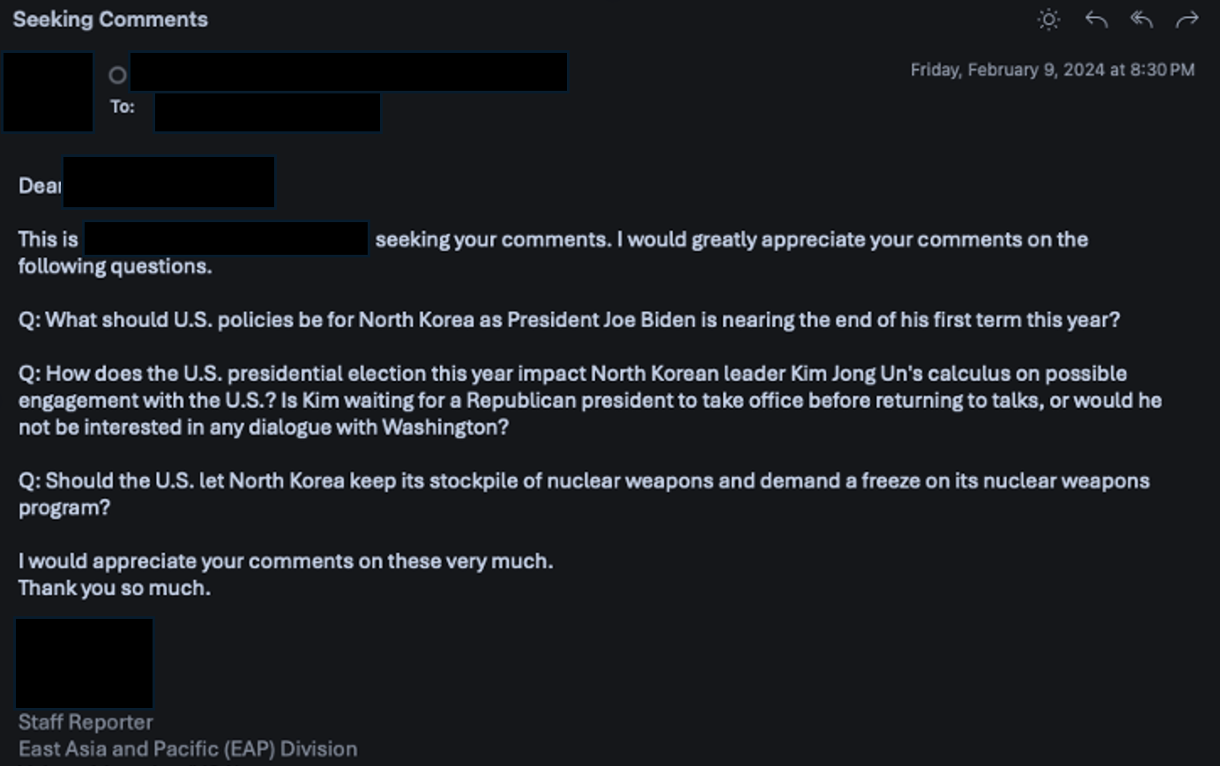
How DMARC Could Have Helped:
- Verifying Email Authenticity: DMARC ensures that only authorized emails appear to be coming from your domain. This significantly reduces the risk of impersonation attempts.
- Alerting You to Threats: DMARC reports provide valuable insights into email authentication failures. These reports can help you identify potential threats and take action before they cause damage.
How TDMARC Makes DMARC Simple and Powerful:
While DMARC offers robust protection, implementing and managing it can be complex. This is where TDMARC comes in. TDMARC is a comprehensive solution that simplifies DMARC for your organization:
- Streamlined Management: TDMARC provides a centralized platform for managing SPF, DMARC, and BIMI records. This eliminates the need for juggling multiple tools and simplifies the entire process.
- Actionable Insights: TDMARC goes beyond basic DMARC reports. It delivers in-depth analysis, including sender location, blacklisted IPs, and lookalike domain detection. This empowers you to make informed decisions and take swift action against potential threats.
- Reduced Burden: TDMARC automates many DMARC tasks, freeing up your IT team to focus on other critical security priorities. This translates to cost savings and improved efficiency.
Benefits of Adopting TDMARC:
- Prevent BEC Attacks: TDMARC’s robust DMARC implementation significantly reduces the risk of email spoofing and impersonation attempts.
- Protect Your Brand Reputation: By preventing fraudulent emails from appearing to come from your domain, TDMARC safeguards your brand reputation.
- Increase Email Deliverability: DMARC compliance helps ensure your legitimate emails reach inboxes and avoid spam filters.
- Reduce Administrative Overhead: TDMARC automates DMARC tasks, saving your IT team valuable time and resources.
Don’t wait for a BEC attack to disrupt your business. Implement TDMARC today and gain a powerful defense against email spoofing and phishing attempts.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
