Phishing attacks are widespread in this digital world, making them a critical concern for organizations and individuals. Google successfully blocks millions of phishing emails, yet 3.4 billion spam emails are sent to companies daily.
Table of Contents
ToggleSpear phishing is a subset of cybercrimes and a rising cybersecurity concern. To safeguard businesses’ confidential data, let’s examine what helps protect them from it.
What is Spear Phishing?
Spear phishing is a sub-type of phishing that targets a particular organization or even individuals and tries to collect confidential data from them. Attackers first research their target and frame messages that are entirely believable for them.
The mode of communication remains the same as for other types of phishing, such as emails, phone calls, text messages, etc.
Though quite similar to phishing, spear phishing does have some core differences. Phishing is generally quite broad and indiscriminate in nature, with the intention to affect as many victims as possible by acting in the disguise of a legitimate entity through emails or websites. A spear phishing is much more targeted: the email is elaborated, almost-mindedly created in an attempt to deceive certain persons or organizations for the purpose of the disclosure of their confidential data, whereby the fraud here can be high-value fraud or corporate espionage.
The number of victims in spear phishing is less, but the method involved is to collect specific details. Attackers set well-defined targets for more confidential information, such as the organization’s HR team, operations teams, or even C-level executives. They impersonate someone familiar to trick these individuals into revealing sensitive data or granting access to internal systems
Book a Free Demo Call with Our People Security Expert
Enter your details
Growing Attacks of Spear Phishing
If an organization is wondering what size companies were most targeted in spear-phishing attacks, the answer is small and even mid-sized companies.
The number of small organizations in the economy is increasing, and attackers generally target them. Additionally, Forbes states that small businesses have fewer resources and are more vulnerable to spear phishing.
Read more: FBI Warns Against Spear Phishing in the Name of Truist Bank
This is one reason why organizations of all sizes must invest in data cybersecurity. As you can see, it is easy for a threat actor to target an organization.
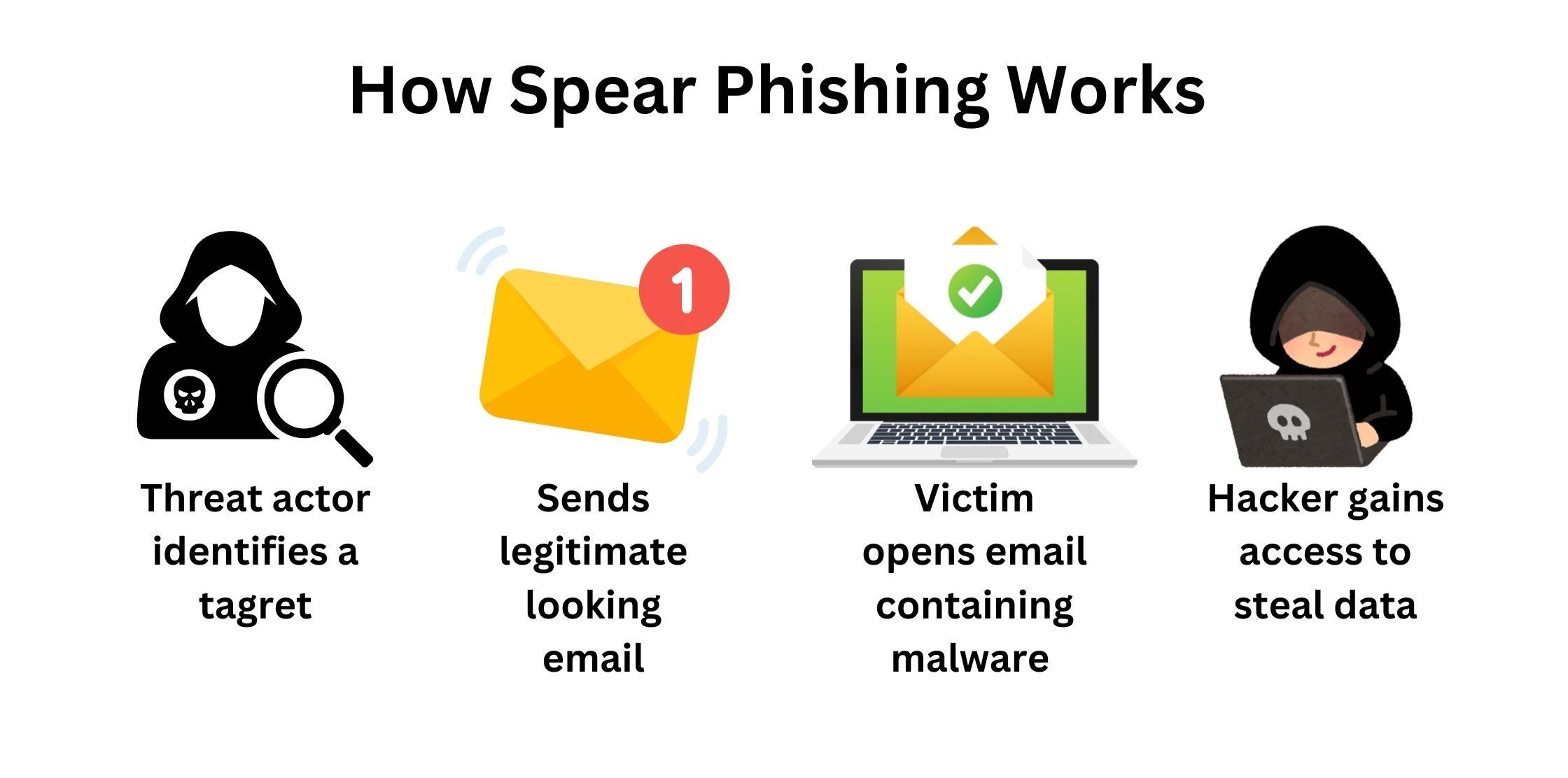
After discussing the problems, let’s look at the bright side and discuss what helps protect from spear phishing.
What Helps Protect From Spear Phishing
- Acknowledging DMARC Technology
DMARC (Domain-based Message Authentication, Reporting & Conformance) is the best way of protecting the domain name for an email organization from compromise since it makes sure that the incoming mails are filtered against the existing list of approved senders, further aiding in security, especially from spear phishing.
Threatcop DMARC (TDMARC) further does this by actively informing the administrators of the unverified attempts so that the administrator can respond quickly to any potential threats and business email communications could be reinforced. It further means that TDMARC is a proactive technology that tries data integrity and domain integrity.
- Regular Awareness Training
Employees are assets and the backbone of every organization. How long the organization rules in the market depends completely on its employees. Therefore, investing in employees gives the highest return.
Threatcop’s Security Awareness Training (TSAT) is an integral part of this education. TSAT employs a best-in-class AI-based solution, emulating real-world cyber-attacks, to enable companies to subject their workforce to unwarranted attacks and verify preparedness against such threats. More than just testing, this is an enlightening, proactive approach for employees. It exposes them to newly modeled vulnerabilities through interactive scenarios of cyber threats, such as phishing, smishing, and WhatsApp.
It identifies where most employees are weak, inculcates in them how to handle suspicious mails, and most importantly, it instills a culture of vigilance in cyberspace. This will make the workforce understand the risks and take part in defending the risks, therefore reducing the risk of falling victim to a successful cyber-attack.
Investing in TSAT is investing in your employees’ ability to protect themselves and, by extension, the entire organization. It transforms them from potential security risks to informed, vigilant participants in your cybersecurity efforts.
- Tools to Identify Suspicious Emails
Spear phishing is performed with utmost research to make sure targets fall for the trap, and data can be stolen. This makes identifying spammy emails difficult as they’re exact imitations of emails from trusted sources. Human error is bound to happen in identification, and therefore, utilizing spear phishing tools just like the phishing incident response tool – Threatcop Phishing Incident Response (TPIR) aids in reporting fraudulent mail in real time and minimizing possible damage.
In response to the sophisticated tactics used in spear phishing, the TPIR tool incorporates a straightforward yet powerful feature—a response button that employees can use to report suspicious emails. This button, conveniently located within the email interface, allows users to flag questionable emails with a single click. Upon activation, the reported email is swiftly forwarded to the security team for further investigation. This rapid response mechanism not only aids in the quick identification and isolation of potential threats but also significantly reduces the chances of data breaches caused by human error in recognizing phishing attempts.
- Software Updates
We use multiple apps and software in our work laptops and phones, which go under update from time to time. If you notice there’s an update pending, make sure to complete it first. Utilizing the latest version of software minimizes the risk of cyberattacks. Switch on the automatically updated software if possible.
Fight Against Spear Phishing
The use of cybersecurity companies and tools is probably the best solution that one can depend upon to ensure the complete negation of spear phishing. It will, in fact, help avoid the chances of losing your data. Stay updated on recognizing these attacks and rely on the latest information.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
