Remote code execution is a cyber attack in which an attacker can remotely execute commands on a system or network. RCEs are typically caused by harmful malware downloaded by the host and can occur regardless of the device’s geographic location.
Table of Contents
ToggleA broad category of cyber assault tactics is remote control execution. It enables a threat actor to execute remote code on a target machine over the internet, a vast area network (WAN), or a local area network (LAN). For example, a threat actor in Ukraine could surreptitiously install malicious code on a targeted device in the United States.
Furthermore, RCE allows a threat actor to take control of a machine or server by executing malicious software. RCE can result in the entire takeover of a susceptible program.
Read and follow the article further to know and understand the remote code execution in detail.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
What is RCE (Remote Code Execution)?
A security flaw known as remote code execution (RCE) enables attackers to connect to a remote system via public or private networks and execute arbitrary code on it. It is regarded as a component of a larger class of flaws called arbitrary code execution (ACE). Perhaps the most serious type of ACE is because it can be used by an attacker even if they have never had access to the system or device before.
RCE is identical to a complete compromise of the system or network. It can result in serious data loss, service turmoil, or the deployment of ransomware or malware.
How Does a Remote Code Execution (RCE) Attack Work?
The execution of an RCE attack sequence is relatively simple. First, the threat actor searches systems across the internet for known vulnerabilities that could be used to launch a successful assault. Once a specific vulnerability has been found, the threat actor will use the exploit to get access. Now that they’re in, they can use the malicious code to accomplish their objectives, which include data exfiltration, fund diverting, detailed surveillance, and service disruption.
Book a Free Demo Call with Our People Security Expert
Enter your details
The language of the targeted application is frequently used to inject code. The server-side interpreter will then run it in that language. Python, Java, Perl, Ruby, and PHP are common programming languages. Code injection is used in applications that immediately analyze unvalidated input. Indeed, threat actors frequently attack public online apps.
Malicious code is usually executed via terminal commands or Bash scripts. A Bash script is a text file that contains commands that are normally typed on the command line. Bash scripts ensure that the provided commands work normally. They are usually followed by a “.sh,” but this is unnecessary. After wrapping a Bash script, the threat actor loads the code into a vulnerable application and executes it. Alternatively, the application could call the kernel to execute it.
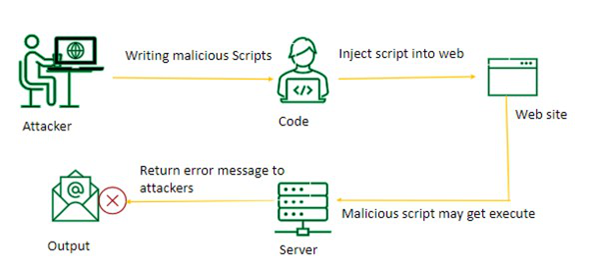
Types of RCE Attacks (Remote Code Execution)
The use of arbitrary code execution on a remote device allowed attackers to exploit RCE vulnerabilities. RCE can be attained by attackers in different ways, such as:
Injection Attacks
Use user-provided data as input to commands in a wide variety of applications, including SQL queries. In injection attacks, the threat actor purposely provides input that is deformed, so, that part of the input can be interpreted as part of the command. This allows attackers to shape the commands to execute on the vulnerable system or execute arbitrary codes in it.
Deserialization Attacks
Applications often use serialization to combine multiple pieces of data into one string to facilitate data transmission and communication. The deserialization attack can interpret specially formatted user input contained in the serialized data as executable code.
Out-of-Bound Write
Applications frequently allot fixed-size memory to store data, including data supplied by users. If the memory allocation is performed incorrectly, threat actors might be able to create input that writes beyond the allocated buffer. Since the executable code is also stored in memory, the application may execute user-provided data if it is written in the appropriate location.
Remote Code Execution (RCE) Vulnerability Techniques
To execute remote code execution (RCE attack), there are two primary techniques.
Execution of Dynamic Code
- The most prevalent attack vector leading to RCE is dynamic code execution. Most programming languages allow you to produce code and execute it in real-time. This is a compelling concept that aids in the resolution of many complex problems. A malevolent third party, on the other hand, can easily exploit it to get RCE capabilities.
- The code written at runtime is frequently reliant on user input. The code almost always incorporates that input in some tone. Knowing that dynamic code creation will employ a specific input, a malicious actor may submit genuine code as an input to exploit your program. The code will be executed on the target system if user input is not validated.
- In general, dynamic code execution generates two types of RCE vulnerabilities: direct and indirect.
- Direct: The malicious actor is aware that their input will be used in code generation in the event of direct dynamic code execution.
- Indirect: An indirect case involves dynamic code generation with user inputs. However, user input is routed through one or more layers. Some layers may even change the input before it is used to generate dynamic code. Furthermore, dynamic code generation may be a byproduct rather than the primary purpose of the input. As a result, the user giving the input is unaware that the input would be used as a building block of a code snippet to be run on a remote system.
Memory Safety
Memory safety is another source of RCE vulnerabilities. It refers to preventing code from accessing memory areas it did not initialize or receive as input. Intuitively, you could expect illegal data access from a lack of memory safety. On the other hand, the operating system and underlying hardware require memory to store actual executable code. Memory also stores metadata regarding code execution. Obtaining access to this memory could lead to ACE and possibly RCE. So, the primary causes of memory safety issues are:
- Imperfections in software design: Software design faults are memory safety issue that occurs when an underlying component is misdesigned. Typically, this would be a compiler, interpreter, or virtual machine; it may also be the operating system kernel or libraries. This category includes a wide range of defects.
- Flaws in hardware design: Flaws in equipment configuration can also be the cause of memory safety violations. They are much more difficult to spot and less common than programming attacks. However, the framework is severely impacted by this kind of attack.
The Effects of Remote Code Execution Attacks
RCE vulnerabilities can have severe consequences for a system or application, including:
- Penetration: Attackers can leverage RCE vulnerabilities as their first point of entry into a network or environment.
- Privilege escalation: In many circumstances, servers have internal vulnerabilities that only people with inside access can see. RCE enables attackers to identify and exploit vulnerabilities, escalating privileges and accessing connected computers.
- Exposed sensitive data: By installing data-stealing malware or simply executing commands, RCE can be used to exfiltrate data from vulnerable systems. This can range from basic unencrypted data copying to memory-scraping malware that searches for credentials in system memory.
- Denial of Service (DoS): An RCE vulnerability allows an attacker to execute code on a machine. This code can be used to deplete system resources and crash the system, or it can be used to execute DoS against third parties.
- Crypto mining: A popular next step after exploiting RCE is to execute crypto mining or cryptojacking malware, which leverages an infected device’s CPU capabilities to implement a cryptocurrency attack for the attacker’s financial profit.
- Ransomware: The most dangerous side effect of RCE is that attackers can install ransomware on the compromised application or server and propagate it over the network, preventing users’ access to their files until they pay a ransom.
Some examples of REC
- CVE-2021-1844 is a vulnerability in Apple iOS, macOS, watchOS, and Safari operating system components. When a victim accesses an attacker-controlled URL using a vulnerable device, the operating system executes a malicious payload on that device.
- CVE-2020-17051 is a vulnerability in the Microsoft Windows communication protocol NFS v3. An attacker can use it to connect to a susceptible NFS server and transmit a payload to the target endpoint.
- CVE-2019-8942—a WordPress 5.0.0 vulnerability that allows attackers to execute arbitrary code in WordPress by uploading a specially crafted image file with PHP code in its Exif metadata.
How to Prevent RCE Attack (Remote Code Execution)?
Because the mode of entry is not fixed, remote code execution assaults are complicated. RCE attacks are a type of attack with a playbook rather than a specific attack. Every day, new vulnerabilities and exploits emerge. As a result, protecting against RCE attacks is a bit of a cat-and-mouse game.
However, there are two steps that every business should take to improve its chances of averting RCE assaults.
Sanitize Input
Deserialization and injection flaws are frequently used by attackers to exploit RCE vulnerabilities. It will help prevent many types of RCE attacks if user-supplied input is validated and sanitized before being used by the application.
Manage Memory Securely
Hackers can exploit issues with memory management as buffer overflows. To find buffer overflows and memory-related vulnerabilities and fix problems before a hacker can perform an RCE attack, it is crucial to undergo vulnerability scanning.
Inspect Traffic
RCE attacks involve hackers manipulating network traffic to gain access to a corporate system by taking advantage of code flaws. Businesses ought to put in place a network security system that can spot attempts to remotely access and control their systems and stop them from being exploited.
Control Access
An attacker can expand their access and execute more damaging attacks using RCE to gain a foothold in the target network. An organization can prevent an attacker from exploiting its initial access to corporate systems by implementing network segmentation, access management, and a zero-trust security strategy.
Final Thoughts: Remote Code Execution
RCE has been on the rise recently. Before hackers affect the system, they must ultimately locate their malware and stop the malicious code. In contrast to a virus, which only attempts to copy and encrypt files, this type of action is performed with malicious intent in addition to just trying to gain access to a system.
Therefore, preventive measures are essential for the creation of secure cybersecurity. In the majority of dangerous circumstances, it becomes challenging for an attacker to enter without setting off alarms.
So securing your workforce is a must. With TSAT from Threatcop, you can educate your employees about the increased risk of cybercrime.
FAQs: Remote Code Execution
An attacker can execute malicious code on a computer via remote code execution (RCE) attacks. An RCE vulnerability can result in malware execution or an attacker acquiring complete control of a vulnerable system.
The attacker must first obtain executable code from your website. Vulnerabilities on your website, such as those that allow file inclusion, allow them to accomplish this. They then run it remotely on your wine server.
Software vulnerabilities, such as remote code execution (RCE), are security flaws. Malicious actors can exploit RCE vulnerabilities to execute code on a remote system over LAN, WAN, or the internet. A vulnerability resulting in arbitrary code execution (ACE) is called remote code execution (RCE).
At its most basic, it enables an agent to execute arbitrary code operations on the target machine/device. With the capacity to run arbitrary code on the target computer, the execution can assume the same privileges as the parent executor of that code, potentially giving access to essential systems, and they are interconnected.
Co-Founder & COO at Threatcop
Department: Operations and Marketing
Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop’s mission to safeguard people’s digital lives.
Co-Founder & COO at Threatcop Department: Operations and Marketing Dip Jung Thapa, Chief Operating Officer (COO) of Threatcop, a leading cybersecurity company dedicated to enhancing people security management for businesses. With a profound understanding of cybersecurity issues, Dip plays a pivotal role in driving Threatcop's mission to safeguard people's digital lives.
