Lack of security awareness and training among employees is one of the major causes due to which organizations become victims of modern cyberattacks. One such attack is QR code scams which involve directing users to malicious websites to collect their private details or infect their devices with malware and trojans.
Scanning fraudulent QR codes can lead to heavy financial losses, the loss of confidential data, and also install malware which can infect work devices. To solve these problems, it is necessary to understand how these scams work and provide proper cybersecurity awareness training to employees to prepare them to identify and recognize fraudulent QR codes.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
Table of Contents
ToggleWhat is QR code Scam?
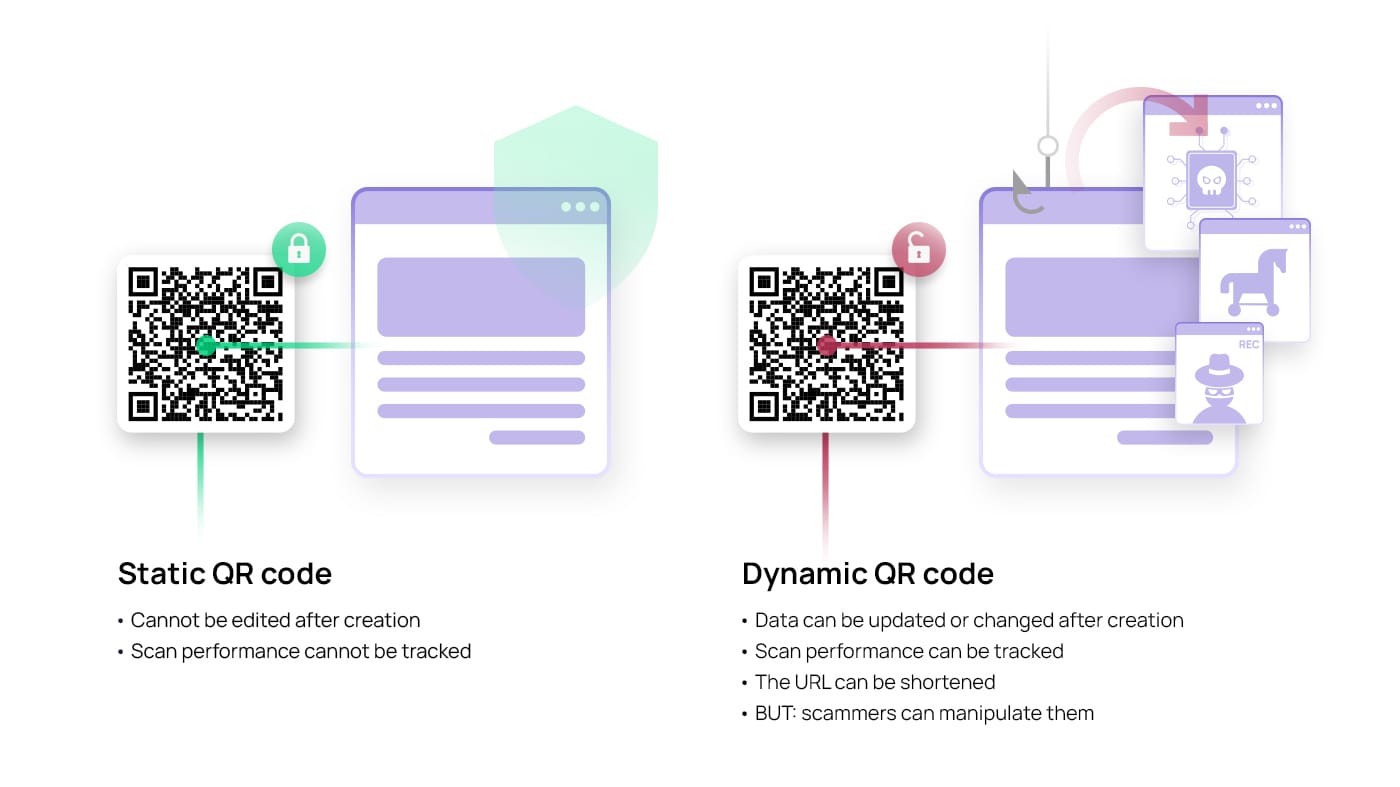
It is a type of scam which uses fraudulent QR codes and redirects users to fake websites or intends to steal user’s private data. These scams are rapidly increasing with the growth of digital payments. Scammers use this to trick users into sending money or revealing confidential details by appearing as legitimate entities.
To avoid such scams user, need to verify the URLs linked to QR codes, avoid scanning codes from unknown sources and ensure secure connections (https://). This attack is also known as Quishing as it is a combination of “QR” and “phishing”, which signifies that it is a type of phishing attack where the user on scanning the QR code is redirected to fake or malicious websites.
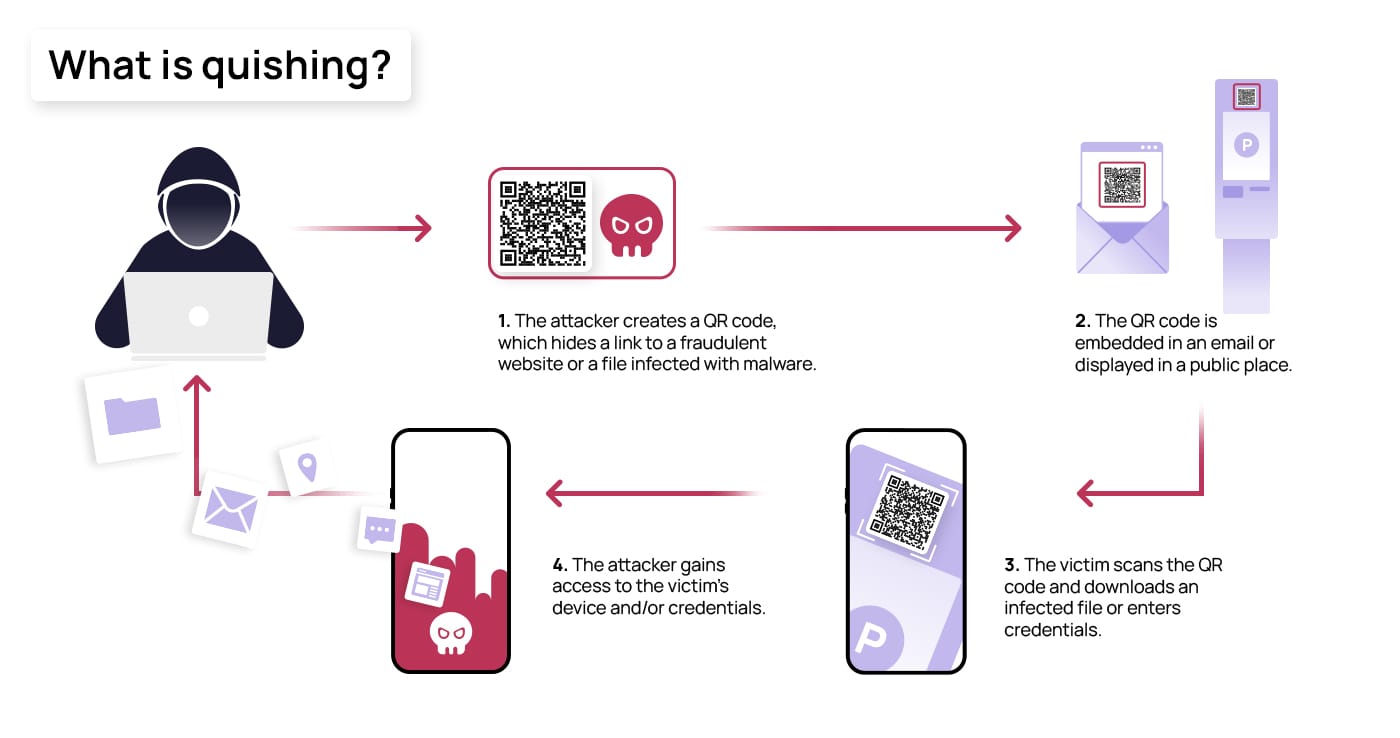
How Quishing Works?
Following are the steps which highlights the working of quishing attacks:-
- Quishing involves sending QR codes on emails and mimics legitimate sources.
- Scanning these fake QR codes results in redirecting users to fake websites.
- These websites appear as legitimate and trusted sites but aim to trick users into entering personal details.
- Usually, users scan these QR codes with mobile devices which might be vulnerable and lack robust security.
- QR codes are basically in the form of images which makes the detection and filtering process difficult.
Example of Real Life Incidents of QR Code Scams
Fake Covid-19 Test Results (2021)
Location: United Kingdom
This QR code scam happened in the UK during the COVID-19 pandemic where attackers sent text messages containing fraudulent QR codes, claiming its recipients needed to scan them to receive their test results. These QR codes are directed to phishing websites that steal user’s personal data and payment details.
Reference: GOV.UK
Fake QR code Scam for Job Application Fees (2022)
Location: Bengaluru, India
Scammers used fake QR codes for an application fee in the name of fake job postings on social media handles. After scanning these fake QR codes victims were directed to a malicious and fraudulent payment gateway where they unknowingly paid money to the scammers without any guarantee of getting the job.
Reference: Times of India
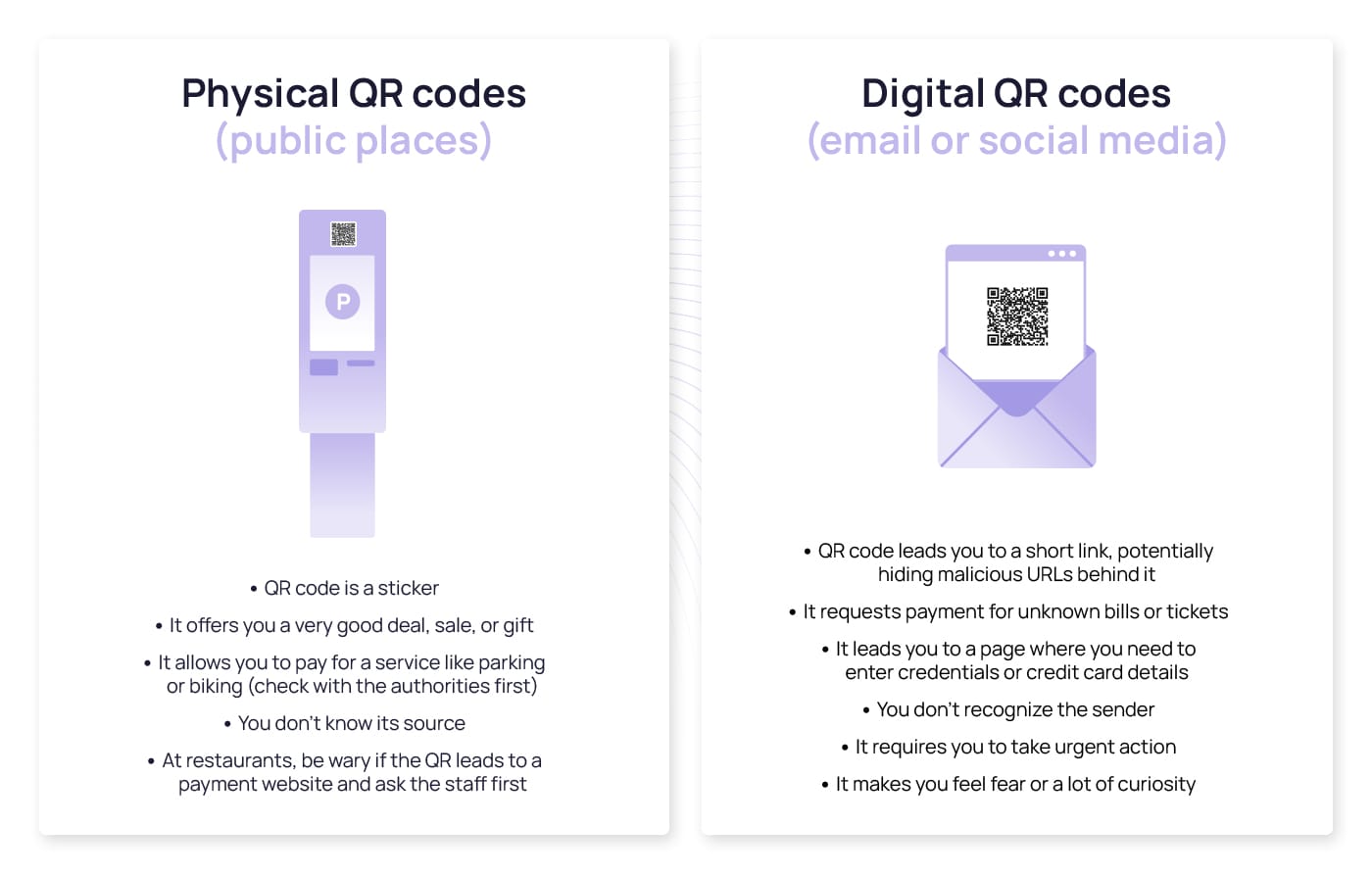
Consequences and Risks Involved in QR Code Scams
- Scanning these fake QR codes can result in installing malware on the devices.
- Phishing sites are a major cause of data theft and aim to capture sensitive details and login credentials.
- The victim needs to suffer financial losses due to unauthorized transactions.
- Attackers can use victim’s data for identity theft.
- Organizations need to face heavy risks and damages if employees scan fraudulent QR codes on work devices.
- Entering employees or customer details on fake or malicious websites can lead to data breaches and compromises.
Book a Free Demo Call with Our People Security Expert
Enter your details
Preventive Strategies to Tackle Quishing Attacks
Following are the preventive strategies to tackle quishing attacks:-
- Organizations need to provide proper security awareness training to employees so that they can identify and recognize phishing attempts through QR code scams.
- Users need to always verify the source of the QR code before scanning to stop getting redirected to unknown websites.
- To identify the chances of QR code scams, check signs of tampering, misalignment, or overlays to identify fraudulent activities.
- Always use reliable QR code scanner applications to avoid the installation of malware in your devices.
- If you’re suspicious of any QR code, try to enter URLs manually.
- Implementing a monitoring and control system can help organizations for tracking unauthorized attempts and suspicious activities.
- There is a need to be cautious when you receive QR codes through messages or unsolicited emails. It might redirect you to fake or untrusted websites.
- Never enter your personal information on unfamiliar or untrusted websites.
- Don’t get fooled by similar-looking email addresses or sender names. It might contain malicious links, grammatical errors, inconsistency, and generic greetings like “Dear Customers” which shows the signs of fraudulent attempts.
- Regularly install and update software on the device to fix vulnerabilities and reduce the chances of malware attacks.
Threatcop’s Methodology to Tackle QR Code Scams
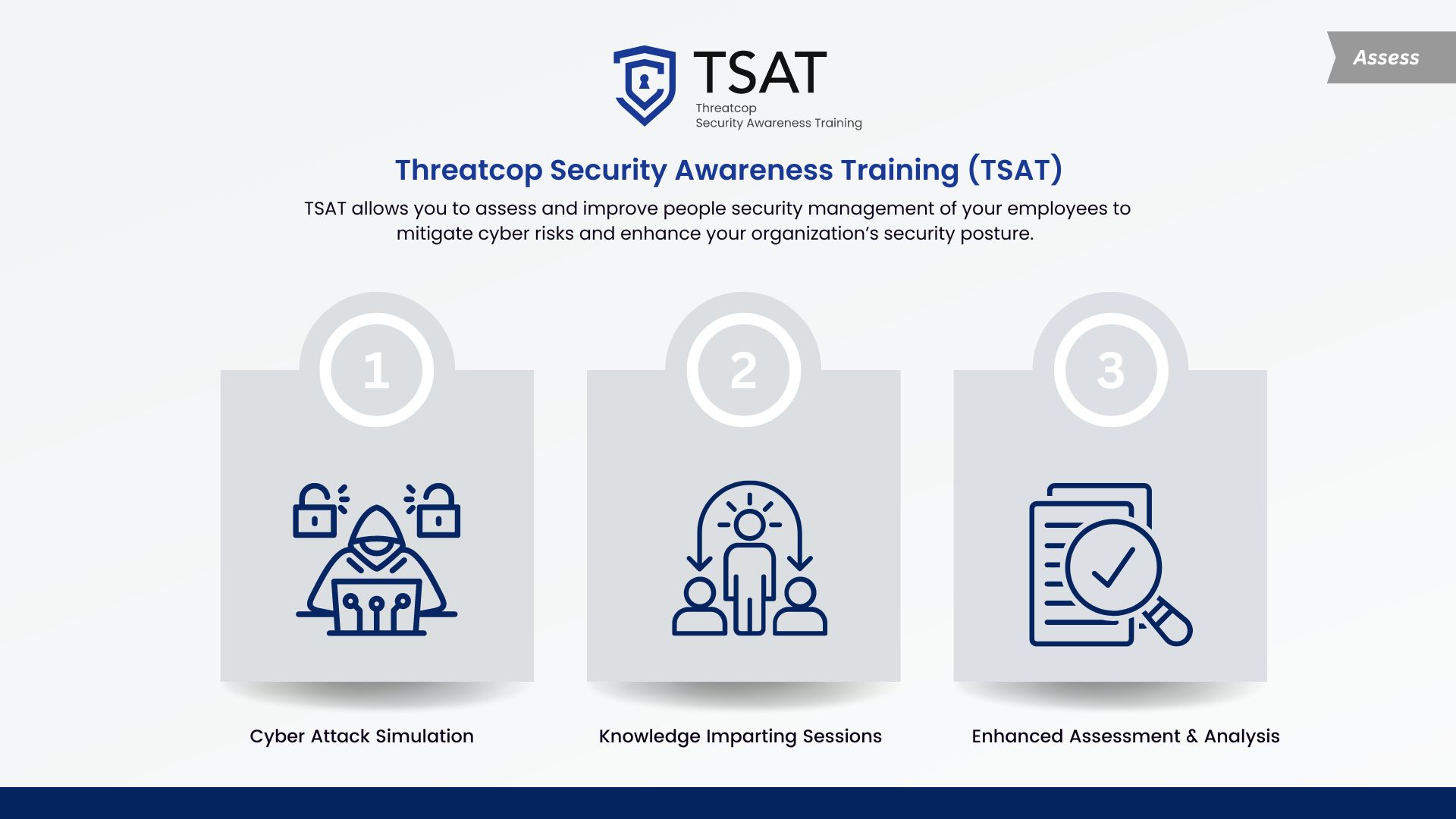
Threatcop’s TSAT provides simulations of multiple attack vectors to mimic real-world scenarios. Organization can train employees on various simulations and make them ready to identify and respond against various cyberattacks. It helps employees to deal with malicious QR codes that comes through ads, posters, or from unknown email sources.
This type of training helps organizations to make employees ready to identify phishing attempts through fake QR codes. Through TSAT it shows employees how to scan QR codes safely, like using a trusted and authorized QR code scanning app that lets them preview the destination link before visiting it.
Features of TSAT
- Provides simulations of multiple attack vectors such as phishing, smishing, vishing, ransomware attacks, QR code scams, Attachment-based attacks, and WhatsApp Phishing.
- Offers predesigned templates and landing pages to fulfill department-specific needs.
- It can run unlimited simulated campaigns.
- Provides multi-language support for dashboards.
- Organizations can track hack history to detect which employees are vulnerable to cyberattacks.
- To deliver better customization it offers AI Template generation.
- For flexibility purposes, it has the feature of campaign scheduling.
- Through category-wise templates, helps to meet various training needs.
- By using real-time dashboards, detailed reports, breach and attack details can be accessed.
Conclusion
Organizations need to implement proper security posture and ensure proper training awareness programs are held to educate employees about modern QR code scams. By using Threatcop’s SAT platform, employees can be trained over a multi-attack vector simulation platform and be future-ready against evolving cyber threats. Using TSAT’s AI-powered phishing simulations can help to streamline security awareness training. Also, empower employees to manage the ongoing threats with extensive customization mimicking the real-world scenarios. Implementing security solutions and applying preventive measures can help to reduce the chances of becoming a victim of quishing attacks.

Technical Content Writer at Threatcop
Milind Udbhav is a cybersecurity researcher and technology enthusiast. As a Technical Content Writer at Threatcop, he uses his research experience to create informative content which helps audience to understand core concepts easily.
Technical Content Writer at Threatcop Milind Udbhav is a cybersecurity researcher and technology enthusiast. As a Technical Content Writer at Threatcop, he uses his research experience to create informative content which helps audience to understand core concepts easily.
