According to statistics by Sophos, 54 % of companies say that their IT departments are not sophisticated enough to handle modern cyber threats. The continuous increase in cyberattacks demands a proper risk identification system to tackle modern threats. Organizations need to adopt the approach of information security risk management to handle risks related to information technology properly.
Table of Contents
ToggleTo empower employees against modern threats, it also requires security awareness training to minimize human errors and fix flaws and vulnerabilities present in the IT infrastructure. By using ISRM approach companies can strengthen security postures and be future-ready against upcoming cyberattacks.
In this blog, we will be understanding about ISRM and its importance for strengthening the security posture of the organization.
What is Information Security Risk Management?
ISRM stands for Information Security Risk Management. It involves the process of handling risks which are associated with information technology. It aims to protect the confidentiality, integrity and availability of the assets of the organization. Its key components involve risk identification, assessment and applying mitigation strategies to prevent data breaches.
The process involved in ISRM includes identification, assessment and treating risk in such a way that it aligns with the risk tolerance factor of the organization. It helps to ensure business continuity by preventing data breaches and ensuring compliance rules and regulations are followed properly.
Book a Free Demo Call with Our People Security Expert
Enter your details
Risks Involved in Information Systems Attackers Can Exploit
Risk becomes a major factor which is responsible for limiting or affecting the organization to work at full potential.
Following are the risks involved in information systems which hackers can take advantage for infecting organization’s IT infrastructure:
- Unauthorized Access: Hackers can gain access to the IT systems unauthorized using spam mail and spam messages.
- Loss of confidentiality: Disclosure of confidential company details can lead to data breaches and unauthorized access.
- Loss of integrity: Making unnecessary and unauthorized modification or deletion of data can compromise its reliability as well as accuracy.
- Loss of Availability: Businesses can be badly affected in scenarios of access issues in the system or data halt situations.
4 Stages of Information Security Risk Management
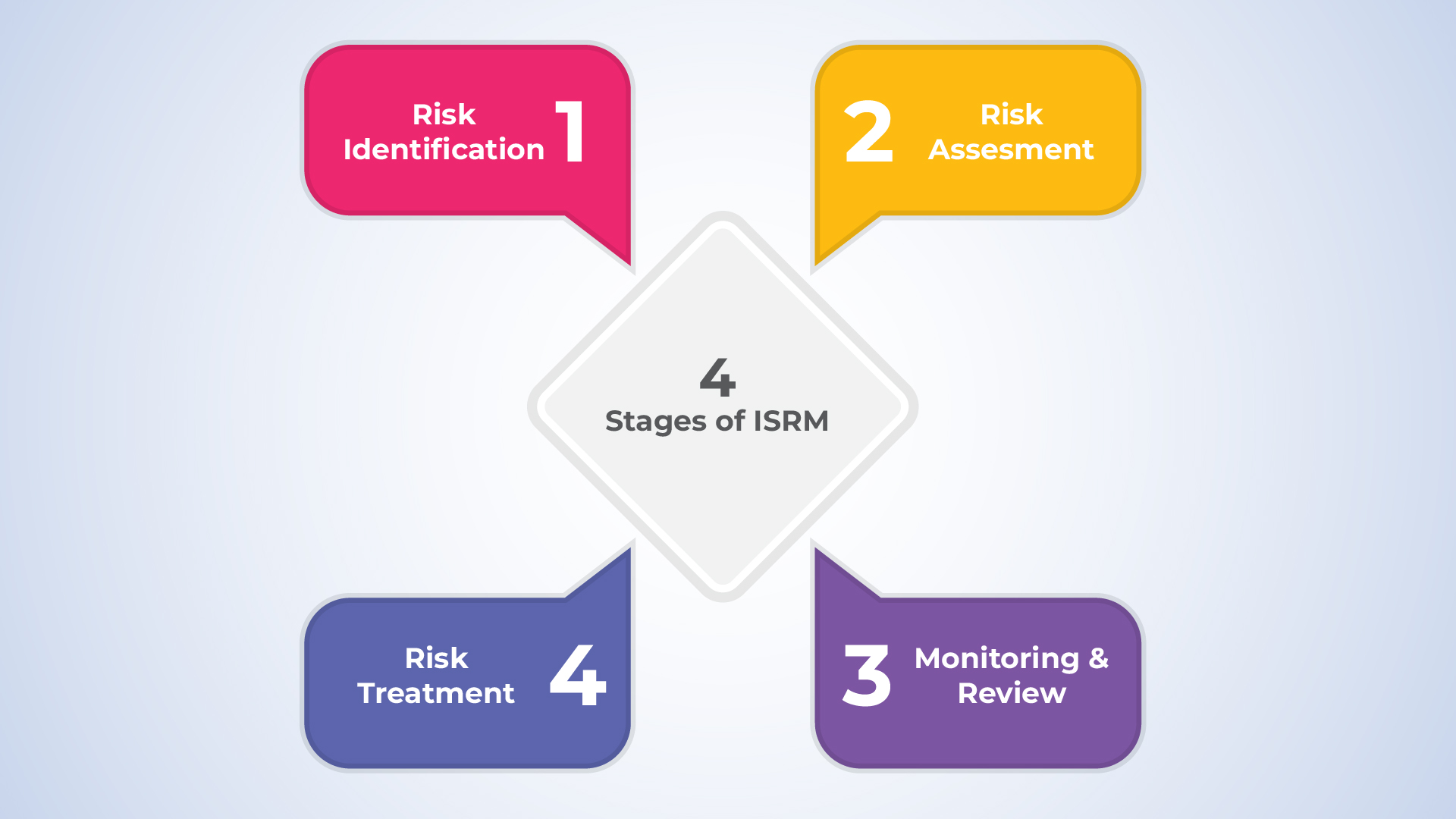
ISRM helps organizations in the identification, assessment, and mitigation of risks which are related to their IT assets as it involves stages to simplify the whole process.
The following are the stages of ISRM :
Risk Identification
Risk identification in information security involves identifying assets, vulnerabilities and threats which can be a factor for compromise of confidentiality, integrity or availability of the information.
Key Takeaways
- Involves identification and documenting potential risks, threats, and vulnerabilities.
- The main focus involves assets, business processes and identification of external threats.
- Techniques like threat modeling, audits and historical data analysis are used.
Risk Assessment
Risk assessment involves evaluating the likelihood and impact of identified risks.
Key Takeaways
- Evaluating risks based on likelihood and potential impact takes place.
- Categorization of risks such as Low, Medium and High for prioritizing the mitigation strategy.
- Frameworks like NIST, ISO 27005 and FAIR for proper assessment.
Risk Treatment
In risk treatment, it involves developing and implementing strategies to mitigate or accept risks.
Key Takeaways
- Works on deciding strategies for risk response such as avoiding, mitigating or accepting.
- Focuses on implementing security controls like encryption, IAM and incident response plans.
- Help in ensuring compliance with regulatory requirements and necessary security frameworks and policies.
Monitoring and Review
This process involves continuously monitoring and reviewing the risk environment.
Key Takeaways
- Tracking and updating risk levels based on new threats becomes easy.
- Emphasizes regular audits, penetration tests, and risk assessments.
- Promotes implementation of security measures to meet business needs and tackle upcoming cyber threats.
Importance of Information Security Risk Management
ISRM plays a major role in strengthening the security posture of an organization. Whether it’s identification of anomalies or protecting from cyberattacks. Following are the point which highlights the importance of ISRM:-
- Protection: It helps safeguarding confidential data from unauthorized access, data theft and corruption.
- Reputation: Protection of an organization’s confidential details from data breaches helps to maintain brand reputation and help in building trust.
- Vulnerability Identification: The vulnerability identification process of an organization’s information system becomes easy through implementing ISRM.
- Compliance: By complying with standardized compliance rules and regulations like GDPR and HIPAA, organizations can avoid legal penalties.
- Prioritization: Prioritizing risks based on the probability and its impact helps in efficient resource allocation.
- Business Continuity: ISRM helps prepare organizations to respond and recover from cyberattacks, which ensures to maintenance of business continuity.
Conclusion
ISRM plays a crucial role in protecting confidential data, ensuring business continuity and maintaining important compliance standards of an organization. Proper identification, assessment and mitigating risks can help to reduce financial losses and strengthen security posture.
Implementing a strong ISRM framework helps to establish a culture of security awareness in the organization and also helps to align cybersecurity efforts with business goals. Real-time monitoring and adapting to modern cyber threats play a major role in making organizations ready and evolve according to future needs and stay secure.
FAQs
ISRM stands for Information Security Risk Management (ISRM).
ISRM involves the process of identifying, assessing, and mitigating risks that could impact the confidentiality, integrity, and availability of an organization’s confidential information and IT assets.
The four stages of ISRM are: Risk Identification, Risk Assessment, Risk Treatment, Monitoring, and review.
Risk Assessment helps in determining the likelihood and impact of identified risks.
Risk in information systems which hackers can exploit includes:- Unauthorized Access, Loss of confidentiality, Loss of integrity, and Loss of Availability.

Technical Content Writer at Threatcop
Milind Udbhav is a cybersecurity researcher and technology enthusiast. As a Technical Content Writer at Threatcop, he uses his research experience to create informative content which helps audience to understand core concepts easily.
Technical Content Writer at Threatcop Milind Udbhav is a cybersecurity researcher and technology enthusiast. As a Technical Content Writer at Threatcop, he uses his research experience to create informative content which helps audience to understand core concepts easily.
