PDFs are a staple in our digital world, used for everything from reports to resumes. PDFs are another popular medium through which cybercriminals can deliver malware (and for a good reason). These could be the compromising of personal details, the corruption of your device, or the entire business being stopped in its tracks. This specific security company detected Foxit Reader to be hiding an undisclosed vector, which was until now being used in this friendly file reader.
Table of Contents
ToggleIn this blog, we will easily learn how PDFs can be used to deliver malware and what we can do to protect ourselves. We will take you through two powerful tools, TPIR (Threatcop Phishing Incident Response) and TSAT (Threatcop Security Awareness Training), to protect your organization from these threats.
Subscribe to Our Newsletter On Linkedin
Sign up to Stay Tuned with the Latest Cyber Security News and Updates
How do Attackers Exploit PDFs?
PDFs seem harmless. They might include text, images, and even some interactive elements. But, you can hide hidden code in a PDF file so that when you open the file, this code may be executed. This code can download malware to your device, steal your login credentials, or even send you to a phishing site.
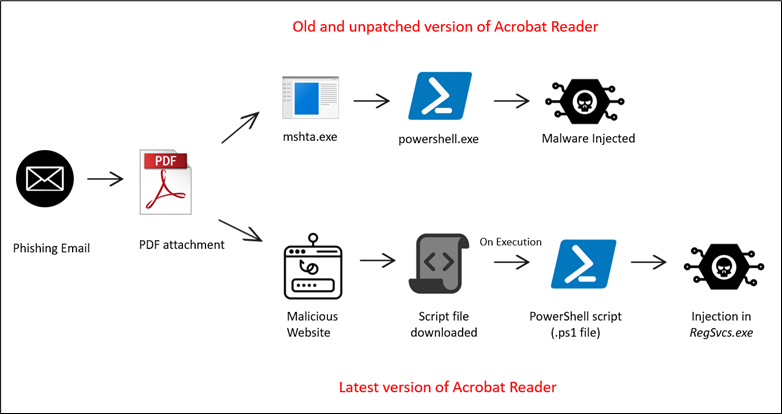
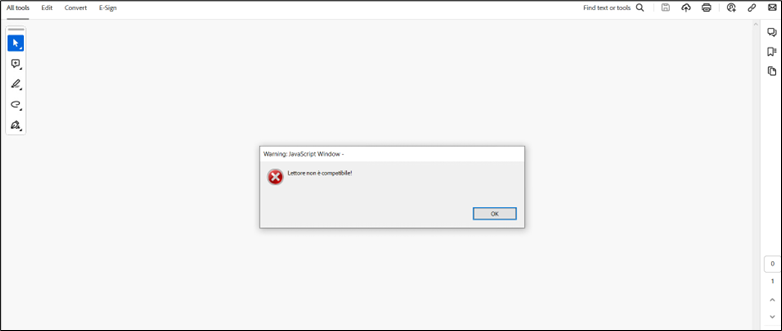
This new research has identified a more nuanced hack. Billion Citizen, which found the technique, reported a pattern of abuse targeting more than 700 million Foxit Reader users everywhere in the world. Most users have opened a PDF only to see a security pop-up, prompting them to enter their password. It may appear real and convince you to take action. Social engineering operates on human psychology. The warning convinces users to click or take action on an otherwise user-initiated action, such as receiving sensitive information or executing harmful programs. It does this by inducing the device to issue apparent security alerts. This is the kind of misleading warning that could get users tricked into doing something that will make them much more insecure.
Book a Free Demo Call with Our People Security Expert
Enter your details
How a Flaw in Foxit Reader Puts Users at Risk?
A popular PDF reader might let attackers run dangerous code, and a scareware scam preys on Google Chrome users. So the fault is of Foxit Reader’s warning messages design.
Here’s the breakdown:
Design Flaw: Foxit Reader’s warning messages have a default option that, unfortunately, can be the most harmful choice.
Double Trouble: When this default is clicked twice by the user without looking for other options, it will trigger the explosion. This downloads and executes malicious code from a remote server, effectively giving intruders a key to the house.
As we mentioned earlier, this explosion is not only a one-trick pony. This technique has been used by both e-crime and espionage-focused cybercriminals. Investigating further, the research team turned up several notable real-world cases:
Espionage Case: There is a suspicion that this exploit would have been used by a group responsible for espionage (APT-C-35 / DoNot Team). This group appears to be able to conduct multi-staged attacks against multiple devices and, as demonstrated, is able to compromise 2FA.
Cybercrime Bonanza: Garden-variety cybercriminals too have been abusing the vulnerability of a variety of malware families, among them digital scourges with names like ImminentRAT and NanoCore RAT.
Researchers found a Social Engineering Twist: Even an incident where the exploit was likely delivered via Facebook, triggering the infection of information stealers and crypto miner downloads.
How Attackers Abused Foxit Reader?
The story doesn’t end with the basic flaw in Foxit Reader. Here’s how attackers made things even trickier:
Double the Deceit: Researchers also discovered a separate campaign where attackers employed two interconnected PDF files. One of them was quite clever and was hosted on a legitimate site as well (Trello.com) to appear trustworthy. This demonstrates the significance of vigilance, even with the links that look kind of safe.
Like a Used Yugo: The group behind these attacks was so bold that they were even selling this exploit as a service, using the ID “@silentkillertv.” This is another area that is making a business around these vulnerabilities.
Building Bad PDFs: The researchers also found tools the attackers used to build their own malicious PDFs and take advantage of this Foxit Reader zero-day. However, most of these PDFs were widely distributed and executed malicious code retrieved from remote servers.
How to Stay Safe from Malicious PDFs?
Be cautious with email: do not open attachments from unknown addresses, even if the email appears to come from a legitimate source. Beware of emails with urgent language, poor grammar,
Check the sender: Confirm the email address of the sender. Attackers frequently spoof email addresses.
Avoid clicking any and all suspicious links: A link inside a PDF is as dangerous as a link given out in the open. Do not click any link unless you are 100% sure it is real.
Update the software: Make sure to update your PDF reader and your OS such that the software includes the latest patches available

Empowering Your Organization with Threatcop
Threatcop Phishing Incident Response (TPIR): TPIR allows your employees to report suspicious emails in one click. This protects against phishing and gets the message to your security team, who is best trained to identify and respond to them without unnecessary damage. TPIR reviews the emails submitted, identifies attachments and URLs indicative of malicious emails and instantly emails out the disposition of reviewed threats.
Highlights of TPIR
- Malware Analysis: Each reported email is analyzed for malicious attachments using Advanced Malware Analysis techniques.
- Heightened Attachment Security: scans attachments against a global threat database and checks the reputation of the sender.
- User-Reported Analytics: Provides insights into user behavior and identifies employees most susceptible to phishing attacks.
Threatcop Security Awareness Training (TSAT) trains your employees to recognize and avoid phishing activities such as those delivered in PDF format. TSAT uses computerized models that are AI-powered to create a realistic copy of phishing scenarios posing as real-world attacks enabling your coworkers to rehearse while in a secure space.
Highlights of TSAT
AI-Powered Simulation: Generates phishing simulation templates driven by artificial intelligence, which can be tailored to any organization.
Multiple Attack Vectors: Helps identify fake emails across different platforms like email, QR codes, and WhatsApp.
Employee Vulnerability Score: It shows who is the most vulnerable against phishing attacks and explains how they should be trained.
After understanding the risk involved with malicious PDFs, and putting in place the right security measures, organizations can significantly reduce their chances of falling prey to cyber-attacks. To empower your company with the tools and training needed to stay safe in the ever-changing threat landscape of today’s businesses, consider TPIR and TSAT by Threatcop.

Technical Content Writer at Threatcop
Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
Technical Content Writer at Threatcop Ritu Yadav is a seasoned Technical Content Writer at Threatcop, leveraging her extensive experience as a former journalist with leading media organizations. Her expertise bridges the worlds of in-depth research on cybersecurity, delivering informative and engaging content.
